Shadow Access in Your Cloud
Blog Article Published: 03/16/2023
By Venkat Raghavan, Stack Identity
Shadow Access is unauthorised, invisible, unsafe and generally over permissioned access that has grown along with cloud identities, apps and data. Today, identities, human and nonhuman are automatically created, along with access pathways to cloud data. Current tools are blind to many cloud identities and access pathways, creating vulnerabilities that are exploited to breach cloud data.
Shadow access breaks cloud and data security, audit, compliance and governance. IAM operations in the cloud must be instrumented for this new age of access and data security.
Expanding Cloud Access Surface
This may be new for some, but everything you spin up in the Cloud has an identity with access to a critical cloud service, supply chain or data. Weaponization of access, therefore, is a big problem in the cloud. The most recent Verizon DBIR report highlights that 80% of breaches were related to identity and access. As data is pouring into cloud platforms, exabytes of data are stored in cloud platforms which drives a massive demand for access to this data. New Identities and access and being created automatically with little to no governance. In AWS alone there are 12,800 Cloud services with 13,800 permissions attached, creating an enormous set of permutations and combinations of cloud access.
Developers and product teams are rapidly combining cloud services with data to create new applications like AI Chatbots, customer data platforms, software supply chains, and third-party SaaS. These developer combinations continually expand the cloud access surface and also create chains of invisible and vulnerable access that can be weaponized quickly.
What Causes Shadow Access?
There are 2 key trends that are creating the perfect storm to enable the weaponization of access. One is the automated cloud via infrastructure as code driven by the CI/CD toolchains that are in use everywhere. The second important trend is the general environment of overly permissioned cloud environments plus programmatic access that is now commonplace in cloud native environments. The automation, programmability, and speed of the cloud make weaponization of access very easy for attackers and adversaries. APIs, automated provisioning, and generally overly permissioned cloud environments amplify the weaponization of access.
“The existence of hundreds (or sometimes thousands) of identities - both human and programmatic - across the CI/CD ecosystem, paired with a lack of strong identity and access management practices and common usage of overly permissive accounts, leads to a state where compromising nearly any user account on any system, could grant powerful capabilities to the environment, and could serve as a segue into the production environment."
- Verbatim from OWASP Top 10 CI CD SEC-2
Types of Shadow Access:
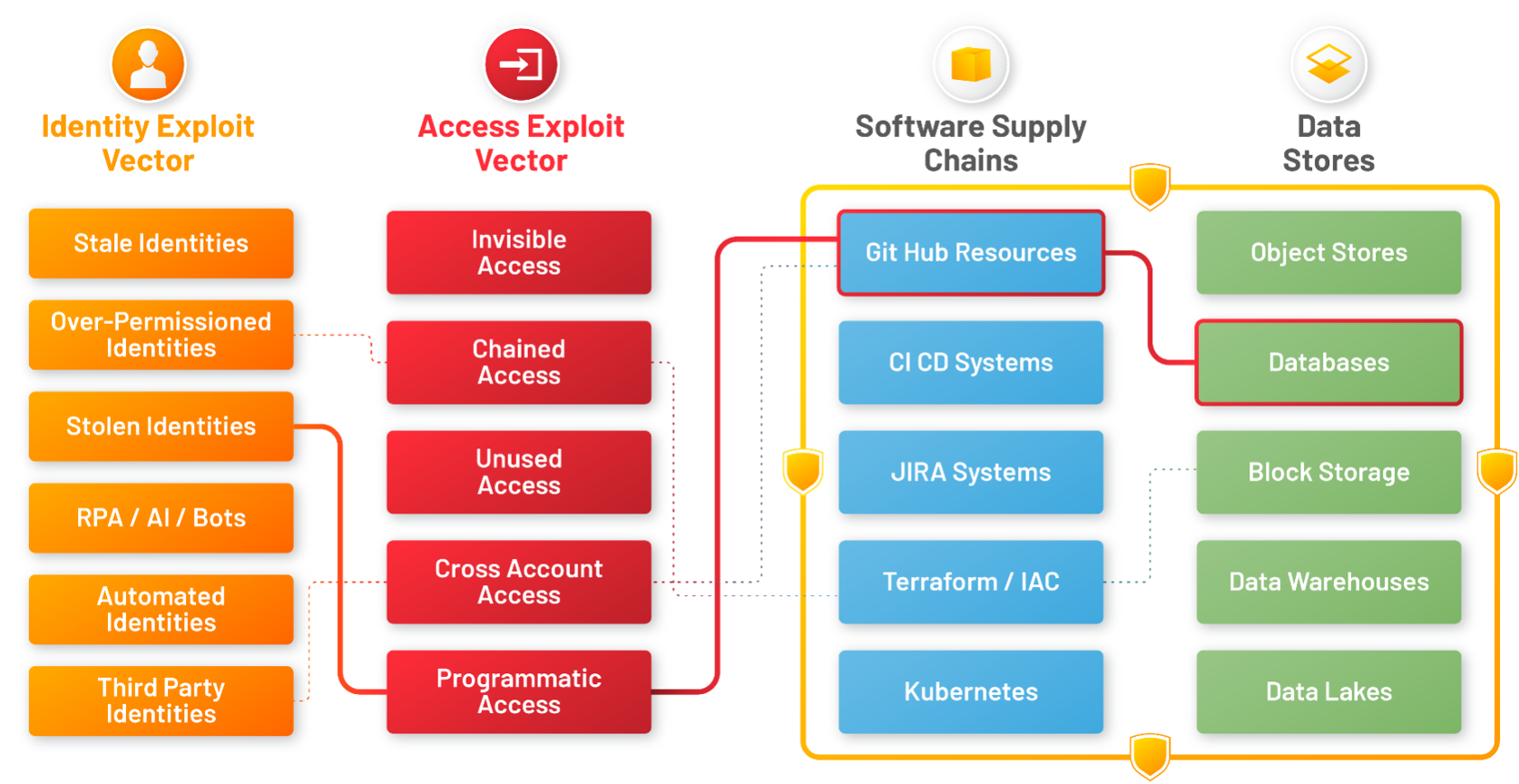
There are many types of shadow access created by combinations of identities (third party, developer, stale accounts, machine identities, etc.) with access types, such as dormant access, chained (or secondary access), unauthorized access (via malicious systms or IP), cross account access etc.
These identity vectors combine with access exploit vectors to access cloud services including, SW Supply chain, Applications, APIs, developer toolchains and cloud data including - disaster recovery assets, databases/stores, and sensitive data (PII, PHI,PCI).
Shadow Access results from this collection of identities and permissions called toxic combinations which create live and active pathways to access and exfiltrate data. Attackers weaponize the weakest link in this chain to exfiltrate data and carry out ransomware attacks, crypto-mining etc.
Impact
A perfect illustration of Shadow Access is the CircleCI breach. In this incident, the unauthorised actor exfiltrated customer information on December 22, 2022, which included environment variables, keys, and tokens for third-party systems.
Customers want to know whether their stolen keys were weaponized against their cloud accounts. Stated differently, customers want to track Shadow Access activity in their environments from these access keys and stop them. CircleCI or any other current tool has no way of answering this question.
Today Red teams, identity practitioners, audit, governance, security operations and data owners are all impacted by shadow access risks. They cannot solve the problem because of their own silos of processes - IAM processes, Data Security, SecOps and IAM governance that do not share data or context.
Cloud teams deal with too many IAM tools. This scatters IAM data (permissions, ticketing, access, approvals) in several different places.
- In the current environment, context is missing, making it difficult to dynamically manage the right accesses to the right data
- IAM governance is broken by IaC driven cloud automation and overly permissioned practices.
Each of these teams are asking the same question - is there a weaponized pathway to get to my data?
Solving the problem of shadow access and weaponization needs new operational processes built on the ground truth of IAM data, and a process that delivers a closed loop across detection, audit and governance and continuously operationalizes the principle of least privilege.
Our IAM Working Group has a new Shadow Access Subgroup! Learn more about the IAM Working Group and how to get involved.
Related Articles:
Are You Ready for Microsoft Copilot?
Published: 04/19/2024
Implementing a Data-Centric Approach to Security
Published: 04/19/2024
10 Tips to Guide Your Cloud Email Security Strategy
Published: 04/17/2024
The Widening Overlap Between Cloud Workloads and Cybersecurity
Published: 04/17/2024






