Top 10 Audio/Video Conferencing Security Best Practices
Blog Article Published: 04/22/2020
By Michael Born, Sr. Security Consultant at SecureSky
With the recent shift of much of the global workforce to home office work environments, it’s a good time to revisit Audio/Video conferencing security best practices. In this blog we will highlight what we consider the Top 10 ways you can train your employees to practice good, risk-reducing security hygiene when scheduling, creating and running online meetings using one of many popular audio/video conferencing platforms. We will also highlight ways to implement detection and alerting controls for audio/video conferencing platforms that offer such robust security features.
Top 10 Recommendations
- Log, monitor and alert on everything the platform allows; baseline and configure according to your organization’s needs.
- Avoid using personal rooms for meetings. Create a new meeting ID each time you schedule a meeting.
- Use strong passwords (12 characters or more) for meetings when possible and only provide those passwords to individuals that need to join the meeting. Never share meeting passwords publicly.
- Turn on “Announce When User Enters” for all meetings.
- Enable meeting “waiting rooms” if possible.
- Enable “mute participants on arrival” if available.
- Restrict meetings to authenticated attendees only if possible.
- Turn off video if not needed and disable private chat if possible.
- Share specific applications only and not your entire desktop in accordance with your organization’s security policies.
- Keep your “host” pin private and treat it like sensitive data.
For specifics, we’ll cover a couple of the more popular platforms.
ZOOM
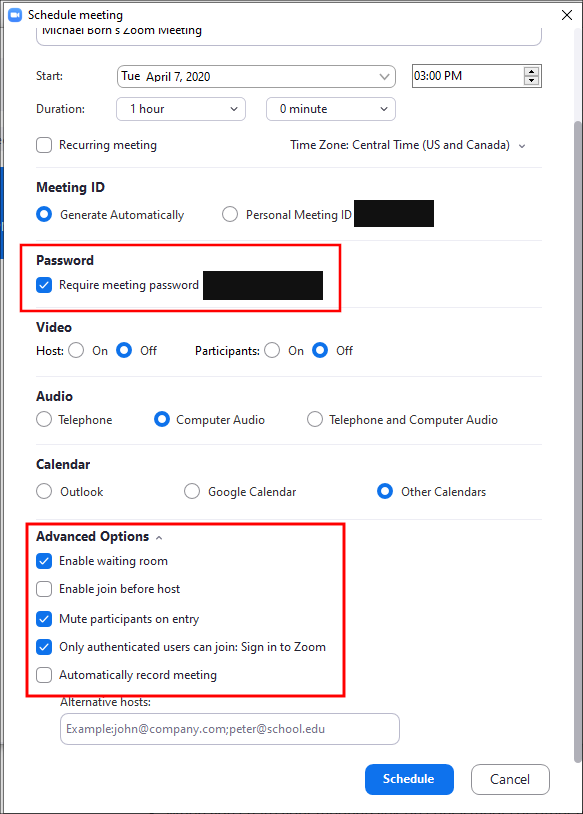
In Zoom, the “Advanced Options” area contains several settings that will help secure your meetings. In the screenshot below, we have highlighted the important settings to turn on (blue check). Nothing replaces user training however. We cannot stress enough how important it is to treat certain aspects of a scheduled meeting as sensitive data. This includes the meeting password, the meeting URL/ID and the host key. Only send the meeting URL/ID and meeting password to individuals you want to attend the meeting. We recommend protecting the host key as well.
CISCO WEBEX
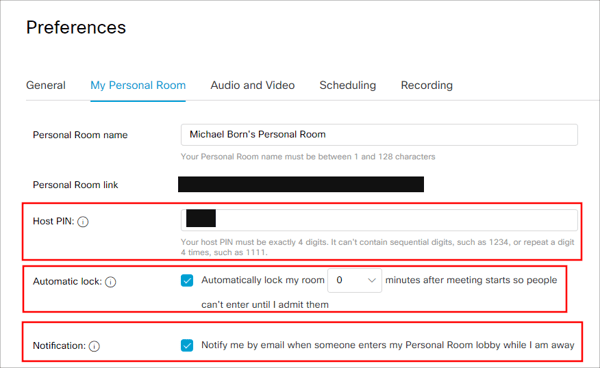
If your organization uses Cisco WebEx, there are additional options that you can configure to harden meetings which are above and beyond the default settings. It is important to note that individual users can alter their own settings, so if you have an organization WebEx administrator, it may be wise to enforce the following settings as the organization default. Uses who can control their own profile settings are recommended to use the following settings under “Preferences.” First, change the default “Host PIN.” Unfortunately, we’re stuck to using a 4-digit pin. Change this often. Second, activate “Automatic lock” for personal rooms and set them to lock immediately once the session begins.
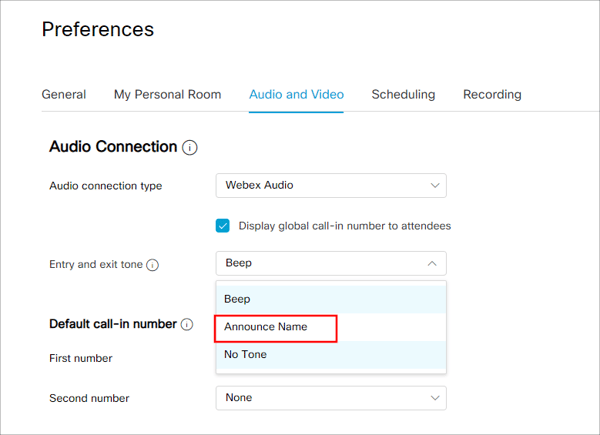
Under the “Audio and Video” settings, make sure to choose “Announce Name” under “Entry and exit tone” setting. This prompts the user to say and record their name when entering the meeting.
Next, when scheduling a meeting, there are additional security settings to configure. We’ve highlighted the important settings in the screenshot below. Make sure to set a strong password (minimum of 12 characters or more). One trick is to copy the password created for you, click on the regenerate icon, and then paste the copied password on the end of the newly created password. This allows you to quickly create a longer password for your meetings. Alternatively, use a password manager to quickly generate a much longer random password on the fly. If you’re hosting a public meeting, you can enable the “Require attendee registration” settings to force users to enter an email address and other information. This helps the meeting organizer validate email addresses of invited guests (assuming attendees enter accurate information of course).
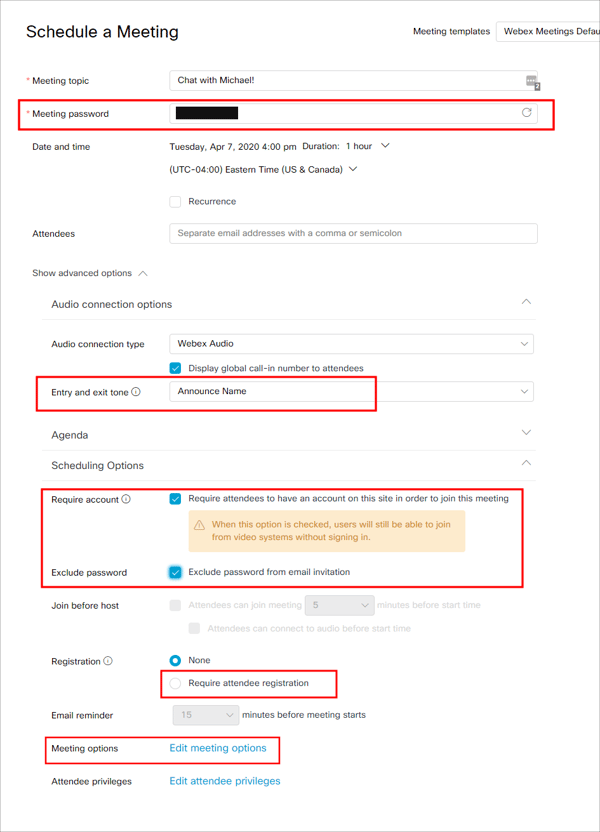
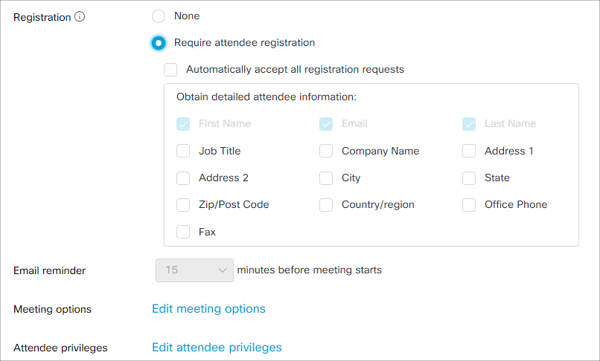
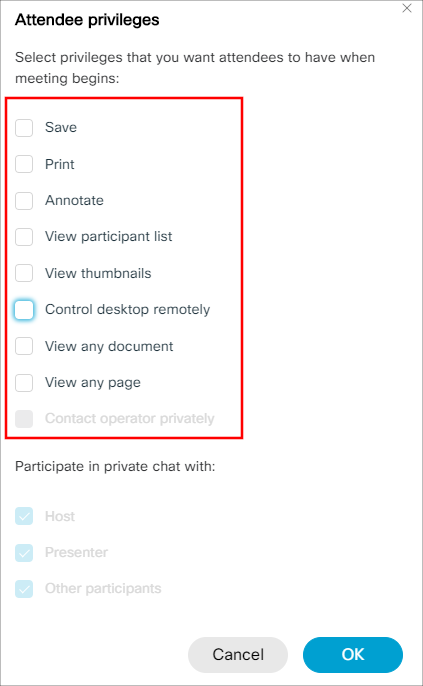
Additional meeting options allow the meeting organizer to disable chat and note taking as well to disrupt potentially malicious attendees.
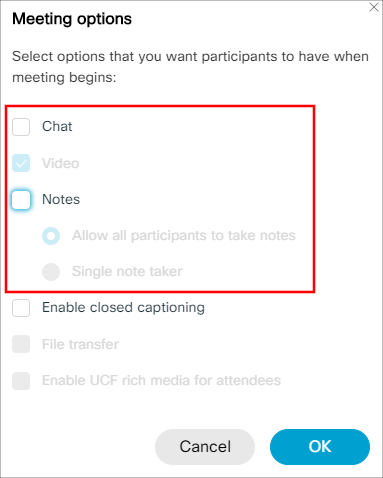
Like the “Meeting options”, the “Attendee privileges” option allows the meeting organizer to lock down the meeting even more and provide additional privilege settings for users attending the meeting.
MICROSOFT TEAMS
Microsoft Teams can create a challenge, as the hardening settings are handled in the Microsoft Teams “admin” portal. With that said, however, there are several great security settings that your organization can configure to not only harden Microsoft Teams, but to monitor and alert upon authentication and file transfers within the platform using Microsoft Sentinel.
Teams Settings
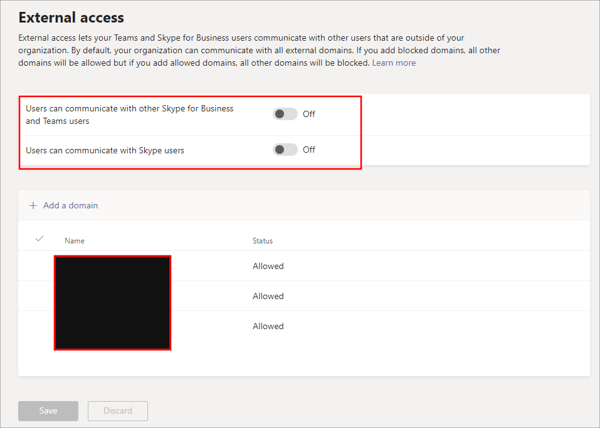
Some of the more important settings for Teams involve “External Access.” Make sure to turn the first two settings to “Off” to prevent external IM communication with external Skype for Business and Teams users, and Skype users so that chat is contained internally. If necessary, enable a whitelist of allowed domains that can join scheduled Teams meetings. Use these domains for any of your customers that need to join scheduled Teams meetings.
Similarly, the “Guest Access” settings dictate whether Guests can access your Teams meetings and chat.
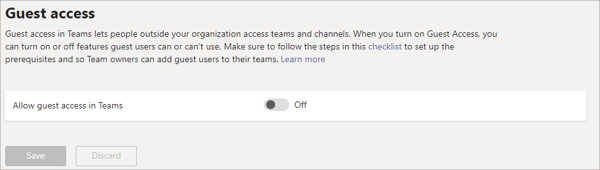
The “Teams Settings” contain additional settings that may vary from organization to organization. We recommend reviewing these settings and configuring them according to the information security policies at your organization. You’re not limited to just these settings either. Teams allows your organization to configure specific policies with very granular detail. Creating those policies is out of the scope of this blog, but we recommend using Policies in addition to the above settings to lock down your Teams platform even more.
Logging, Monitoring, and Alerting with Sentinel
In a recent post by Microsoft (https://techcommunity.microsoft.com/t5/azure-sentinel/protecting-your-teams-with-azure-sentinel/ba-p/1265761), Pete Bryan details some incredible functionality with Sentinel, Logic Apps and configuration settings to monitor Microsoft Teams. By enabling audit logging in Microsoft 365 and creating an Azure AD app to allow API access, we can have Sentinel monitor and alert on suspicious behavior within Microsoft Teams and its users. You can read the article for yourself, but I want to highlight an important piece of information from the article. You want to collect two different but related sets of logging information. First, Microsoft 365 “Audit.General” logs will capture Teams events. Second, AzureAD logs will help capture issues with Identity for Teams users. Make sure to follow Mr. Bryan’s advice on normalizing the data with KML queries too and implement some of the hunting queries detailed in the article.
No matter which of these audio/video conferencing solutions your organization uses, these top 10 steps along with end-user training will help reduce risk associated with your now primarily remote workforce.
References
https://docs.microsoft.com/en-us/microsoftteams/enable-features-office-365
https://blog.zoom.us/wordpress/2020/03/20/keep-uninvited-guests-out-of-your-zoom-event/
https://help.webex.com/en-us/8zi8tq/Cisco-Webex-Best-Practices-for-Secure-Meetings-Hosts
Trending This Week
#1 The 5 SOC 2 Trust Services Criteria Explained
#2 What You Need to Know About the Daixin Team Ransomware Group
#3 Mitigating Security Risks in Retrieval Augmented Generation (RAG) LLM Applications
#4 Cybersecurity 101: 10 Types of Cyber Attacks to Know
#5 Detecting and Mitigating NTLM Relay Attacks Targeting Microsoft Domain Controllers
Related Articles:
Detecting Compromised Accounts in Microsoft 365
Published: 04/04/2024
Powerful Cloud Permissions You Should Know: Part 1
Published: 03/26/2024
Defend Against Azure Cross-Tenant Synchronization Attacks
Published: 03/15/2024
Phishing in Azure Cloud: A Targeted Campaign on Executive Accounts
Published: 03/11/2024






