Using SOC Reports for Cloud Security and Privacy
Blog Article Published: 02/10/2020
By Ashwin Chaudhary, Chief Executive Officer, Accedere Inc

Data security and privacy are increasingly challenging in today’s cloud-based environments. Many organizations are storing a significant amount of data in distributed and hybrid cloud and even unmanaged environments, increasing challenges for regulatory compliance. Meanwhile, privacy mandates such as GDPR recommend data anonymization, which can be another form of encryption. Without a proper data governance program; however, organizations may face difficulties in meeting these privacy compliance mandates.
Providing independent third-party assurance such as a System and Organization Controls (SOC) 2 report helps address these concerns and helps cloud service providers (CSPs) stay ahead of the competition. This assurance also helps organizations mitigate data security and privacy risk.
Recently I authored a report on SOC Reports for Cloud Security and Privacy that was published by ISACA. In this article, I’ll be giving an overview and summarizing several of the topics discussed in the report, including:
- Cloud Assurance for CSPs
- Privacy Compliance for Cloud
- Controls for User Organizations
Cloud Assurance for CSPs
There are several approaches CSPs can leverage to provide assurance to their customers. Below I explain how each resource can be used to provide customers with confidence in using their CSP’s services.
Cloud STAR Certification Roadmap
CSA7, in collaboration with the American Institute of CPAs (AICPA), developed a third-party assessment program of CSPs called the CSA Security Trust Assurance and Risk (STAR) Attestation. The STAR program provides multiple benefits, including indications of best practices and validation of the security posture of cloud offerings.
SOC 2 for Cloud CSA STAR Attestation
The SOC 2+ Framework allows a SOC 2 to report on any additional controls over and above the trust services criteria controls for security, availability, confidentiality, processing integrity and privacy. Taking advantage of this framework, STAR Attestation provides a framework for Certified Public Accountants performing independent assessments of CSPs using SOC 2 engagements with the CSA’s Cloud Controls Matrix (CCM).
Cloud Controls Matrix (CCM)
The CCM is the only meta-framework of cloud-specific security controls, mapped to leading standards, best practices and regulations. CCM provides organizations with the needed structure, detail, and clarity relating to information security tailored to cloud computing. CCM is currently considered a de-facto standard for cloud security assurance and compliance.
Level 2 CSA STAR Attestation
The STAR Attestation is positioned as a third party certification at Level 2 of the Open Certification Framework. The STAR Attestation is a rigorous third-party independent assessment of the security of a cloud service provider (figure 2 and is based on type I or types II SOC attestations supplemented by the criteria in the CCM.
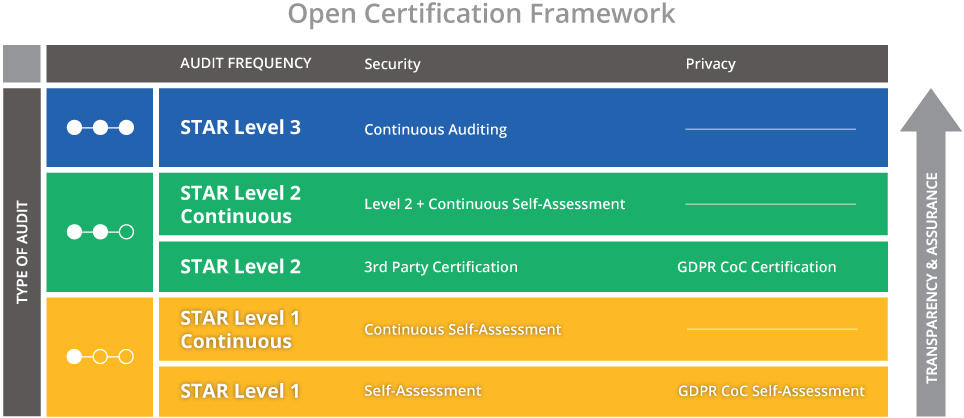
Figure 2—STAR Certification Framework 1
This assessment:
- Is based on a mature attestation standard
- Allows for the immediate adoption of the CCM and the flexibility to update the criteria as additional criteria and technology and market requirements change
- Does not require the use of any criteria that were not designed for or readily accepted by the CSP
- Provides for robust reporting on the service provider’s description of its system and on the service provider’s controls, including a description of the service auditor’s tests of controls in a format very similar to the current SSAE 18 reporting, thereby facilitating market acceptance 2
- Is a mature attest standard (it serves as the standard for SOC 2 and SOC 3 reporting)
- Provides for robust reporting on the service provider’s description of its system and on the service provider’s controls, including a description of the service auditor’s tests of controls in a format very similar to the current SSAE 18 reporting, thereby facilitating market acceptance
- Provides evaluation over a period of time rather than a point in time
- Provides recognition with the AICPA logo
STAR Attestation builds on the key strengths of SOC 2 because it:
- Is a mature attest standard (it serves as the standard for SOC 2 and SOC 3 reporting)
- Provides for robust reporting on the service provider’s description of its system and on the service provider’s controls, including a description of the service auditor’s tests of controls in a format very similar to the current SSAE 18 reporting, thereby facilitating market acceptance
- Provides evaluation over a period of time rather than a point in time
- Provides recognition with the AICPA logo
CSA Continuous Assessment (Level 2 and 3 Continuous)
STAR Level 2 Continuous builds on top of the STAR Level 2 requirement of third-party assessments and improves it by allowing the CSP to demonstrate a higher level of assurance and transparency with the addition of a continuous self-assessment.
In STAR Level 2, a CSP is assessed by a third party through one of the Level 2 programs against a determined and appropriate scope. The Level 2 programs, including STAR Certification, STAR Attestation, and C-STAR, are based on varied but demanding cloud security criteria of the CSA CCM, the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC) ISO/IEC 27001 standards or the AICPA Trust Services Criteria (TSC), applied toward the CSP’s assessment scope.
Level 3 Continuous Certification is a highly selective cloud security assessment program, extending the assurance level of a cloud service beyond the trust given by the certification cycle of ISO/IEC 27001 and the audit period of AICPA SOC 2 Type II reports.
STAR Level 3 Continuous requires all continuous assessments to be performed under the supervision of a third-party auditor. This differs from Level 2 Continuous, which requires a frequently submitted self-assessment on top of Level 2 by the CSP itself.
C5 Cloud Controls
In February 2016, the Bundesamt fur Sicherheit Institute (BSI)3, or the German Federal Office for Information Security, established the Cloud Computing Compliance Controls Catalog (C5) certification after it noted the rise in cloud computing in Germany. 3 With the C5, the BSI redefined the bar that CSPs should meet when dealing with German data. The establishment of the C5 elevated the demands on CSPs by combining the existing security standards (including international certifications such as ISO 27001) and requiring increased transparency in the data processing. C5 controls can be applied globally.
C5 is intended primarily for professional CSPs, their auditors, and customers of the CSPs. The catalog is divided into 17 thematic sections (e.g., organization of information security, physical security). C5 makes use of recognized security standards, such as ISO 27001, the Cloud Controls Matrix of the Cloud Security Alliance and BSI publications, and it uses these requirements wherever appropriate.
A SOC 2 report proves that a CSP complies with the requirements of the catalogue and that the statements made on transparency are correct. This report is based on the internationally recognized attestation system of the International Standard for Assurance Engagements (ISAE) 3000, which is used by public auditors. When auditing the annual financial statements, the auditors are already on site, and auditing, according to C5, can be performed without much additional effort.
Privacy Compliance for Cloud
Privacy laws are now changing and may become more stringent. After GDPR, new privacy laws are already in force, such as the US California Consumer Privacy Act (CCPA). It may be prudent for organizations to be more proactive and adopt measures for privacy governance.
To demonstrate privacy-related controls, organizations can include the privacy criteria as part of the scope of their SOC 2 report.[i]Additionally, controls for any other specific laws can be included as additional subject matter. In the wake of new privacy mandates, organizations are encouraged not only to include privacy criteria in their SOC 2 report but also to demand including them in their vendors’ SOC 2 report to mitigate risk.
SOC 2 Description for Privacy 4
A SOC 2 report contains a description of services that the service provider provides. When the description includes privacy, service organization management discloses the service commitments and system requirements identified in the service organization’s privacy notice or in its privacy policy that are relevant to the system being described.
When making such disclosures, it may also be helpful to report users if service organization management describes the purposes, uses, and disclosures of personal information permitted by user entity agreements.
AICPA Trust Services Criteria (TSC) for Privacy 5
With approximately 50 points of focus, the TSC organizes the privacy criteria as follows:[ii]
- Notice and communication of objectives—The entity provides notice to data subjects about its objectives related to privacy.
- Choice and consent—The entity communicates choices available regarding the collection, use, retention, disclosure, and disposal of personal information to data subjects.
- Collection—The entity collects personal information to meet its objectives related to privacy.
- Use, retention and disposal—The entity limits the use, retention, and disposal of personal information to meet its objectives related to privacy.
- Access—The entity provides data subjects with access to their personal information for review and correction (including updates) to meet its objectives related to privacy.
- Disclosure and notification—The entity discloses personal information, with the consent of the data subjects, to meet its objectives related to privacy. Notification of breaches and incidents is provided to affected data subjects, regulators and others to meet its objectives related to privacy.
- Quality—The entity collects and maintains accurate, up-to-date, complete and relevant personal information to meet its objectives related to privacy.
- Monitoring and enforcement—The entity monitors compliance to meet its objectives related to privacy, including procedures to address privacy-related inquiries, complaints, and disputes.
Controls for User Organizations
To protect its data in the cloud, users should consider implementing the following controls to minimize the risk:
- Create a secure design before moving to the cloud
- Conduct a cloud impact assessment
- Understand the crown jewels (data) and create a flow analysis
- Monitor role-based access controls (RBAC)
- Evaluate SOC reports with relevant controls of the CSPs
- Implement multifactor authentication (MFA)
- Analyze back up and encryption controls
- Evaluate policies and procedures
- Perform configuration audits
- Perform periodic internal audits
- Ensure compliance with laws e.g. data residency
Read the full report from ISACA
Data governance and privacy programs that align with organizational goals can help in increasing the maturity roadmap. Continuous monitoring and assurance programs such as the SOC 2 can address weaknesses and provide better visibility to the organization’s stakeholders. If you’re interested in learning more, you can find the full version of the report here.
About the Author
Ashwin Chaudhary, MBA, CPA, CISSP, CCSK CISA, CRISC, CISM, CGEIT, ITIL, PMP is the Chief Executive Officer of Accedere Inc., a Certified Public Accountant (CPA) firm focusing on System and Organization Controls reporting, cloud data security and privacy. He can be reached at [email protected].
References
- Cloud Security Alliance, “CSA Security Trust Assurance and Risk (STAR),” https://cloudsecurityalliance.org/star/
- Amazon Web Services, “Shared Responsibility Model,” https://aws.amazon.com/compliance/shared-responsib...
- Federal Office for Information Security, “Compliance Controls Catalogue (C5),” USA, https://www.bsi.bund.de/EN/Topics/CloudComputing/C...
- American Institute of Certified Public Accountants, “System and Organization Controls: SOC Suite of Services,” https://www.aicpa.org/soc
- American Institute of Certified Public Accountants, “Trust Services Criteria,” 2017, https://www.aicpa.org/content/dam/aicpa/interestar...
Related Articles:
How to Set Your Small Privacy Team Up for Success
Published: 04/17/2024
How to Audit Your Outdated Security Processes
Published: 04/16/2024
Cloud Relationships: Getting to Grips With the ‘Vendor of My Vendor’
Published: 04/15/2024
Cantwell Proposes Legislation to Create a Blueprint for AI Innovation and Security
Published: 04/15/2024






