Cyber Attacks in Russia’s Invasion of Ukraine
Blog Article Published: 03/25/2022
 This blog was originally published by Orca Security on March 11, 2022.
This blog was originally published by Orca Security on March 11, 2022.
Written by Bar Kaduri, Orca Security.
The modern internet has drastically changed the landscape of threats. It created a new dimension where countries and individuals can affect, disrupt and demolish systems that comprise our entire day to day life. From power stations to banks, all are at risk. The Orca Security Research Pod has been actively tracking cyber attacks leading up to and occurring in an ongoing manner as part of Russia’s invasion of Ukraine that occurred in late February. The cyber attacks have combined multiple threat vectors, including malware, distributed denial-of-service attacks, social engineering campaigns, and other coordinated techniques. This blog captures the major security information related to these efforts.
The Role of Cyber Attacks in the Russia-Ukraine Conflict
The Russian invasion of Ukraine physically started on February 24, 2022. However, the Russian cyber invasion to Ukraine started a long time ago, with many major events over the years, such as the Crimea annexation in which many Ukrainian websites were shut down, as well as the mobile phone network. Afterwards, two big power outages in 2015 and 2016 caused by cyber attacks left hundreds of thousands in the dark. The not-Petya ransom-wiper attack targeted the financial sector of Ukraine on a national Ukrainian holiday but was spreading from there to many organizations around the world, leaving huge financial damage.
In November 2021, when the tension between Ukraine and Russia re-emerged with Russian troops on the borders, the Ukrainian Security Service published technical information and intelligence about Gamaredon group, an APT group that attacked the Ukrainian government for years and is associated with Russia’s Federal Security Service.
WhisperGate Malware
In January 2022, the tension between the countries grew with the progress of US, NATO and Ukraine talks. A big increase of cyber-attacks was then detected. January 13 was the first time we saw destructive malware in this campaign. This malware, dubbed WhisperGate, is designed to look like a ransomware attack, but with no option for recovery. The malware wrote over the MBR component in Windows machines and downloaded another payload that removed all files from predefined paths. The file removal was not absolute, probably by attacker’s design, to cause more of a psychological damage.
Ongoing Cyber Attacks Leading to the Invasion
On January 14, 2022, over 70 Ukrainian websites suffered from defacement. The content of the sites was changed to the phrase “be afraid and wait for the worst” in 3 languages: Ukrainian, Russian, and misspelled Polish.
On February 15, 2022, a large DDoS attack was observed, taking down two of the biggest banks in Ukraine and several government sites. This attack was described as the biggest DDoS that had ever taken place in Ukraine.
Hermetic Malware Precedes the Invasion in February
Just one day before the physical invasion, two huge attacks took place. The first was a big DDoS attack that took down many government sites and banks. As this attack occurred, a second data wiping malware was detected in multiple Ukrainian organizations in the financial, government, aviation, and IT sector. The malware, dubbed “Hermetic”, consisted of three different malwares:
- Wiper: Deleted the data in the system
- Wizard: Responsible for network spreading
- Ransomware: Used to disguise the wiper’s actions.
Isaac Malware Also Seen in the Wild
The third wiper attack took place on the day of evasion. The malware, dubbed the Isaac wiper, is so far reportedly much less sophisticated than the previous two wipers used in attacks.
3/17/22 UPDATE: Significant Russian attributed cyber activity is still not seen. Another wiper that targeted Ukrainian entities called “CaddyWiper” was published this Tuesday. This wiper is not similar in any way to the previous wipers found around the invasion and avoids destroying data on domain controllers.
3/17/22 UPDATE: We also keep seeing small activities of actors that might be exploiting the situation. For example, the Ukrainian IT army volunteers are recently being offered an alleged tool that targets Russian entities. This tool was published by Talos as a Trojan.
Social Engineering Campaign Combined with SunSeed Malware
Over the past few days, we have heard about a new social engineering campaign called Asylum Ambuscade, targeting European immigration personnel. The campaign aims to extract information about refugees with malware dubbed SunSeed, discovered by ProofPoint.
Hacktivism and Ongoing Cyber Activities
Russia is not the only one leading cyber attacks in this conflict. Many hacktivist groups, people who use the internet and related cyber techniques to engage in civil disobedience for a cause, have announced that they concentrate their efforts now to cause damage and disruption to Russia. For example, the Anonymous hacker collective has declared a cyber war on the Russian government. In addition, the Ukrainian vice prime minister has tweeted about building an IT army of volunteers, that will defend the Ukrainian IT infrastructure.
Another interesting story happened when Conti’s ransomware source-code and internal chats were published after the cyber group expressed its support in Russia. Conti ransomware was one of the most impactful ransomware attacks of 2021, this publication led to the removal of its C&C infrastructure, leaving the ransomware impaired.
The cybersecurity and security research community is continuing to watch and track cyber attacks as part of this ongoing conflict. Since more complex attacks were attributed to Russia and its hacktivists in the past, additional events may occur as part of this conflict in the near future. As developments move forward and potentially include additional groups and research, we aim to provide timely updates.
3/17/22 UPDATE: We saw a massive leak of information from Roskomnadzor (Federal Service for Supervision of Communications, Information Technology and Mass Media) carried by the Anonymous collective. In addition, we’ve seen an NPM package deleting files for users based in Russia and Belarus.
Data and Recommendations
Meanwhile, many security vendors have reported a significant increase of all cyber-attacks, from Phishing to DDoS and more. “Leak” of this conflict has already occured in the past (for example with Not-Petya), and might occur again. Here at Orca Security, we have seen over a 60% increase in average SSH brute force attacks per customer on cloud infrastructure in the US. This anonymized data set from real-world cloud environments compares data from the week of February 24 and March 2 to weeks from the previous month.
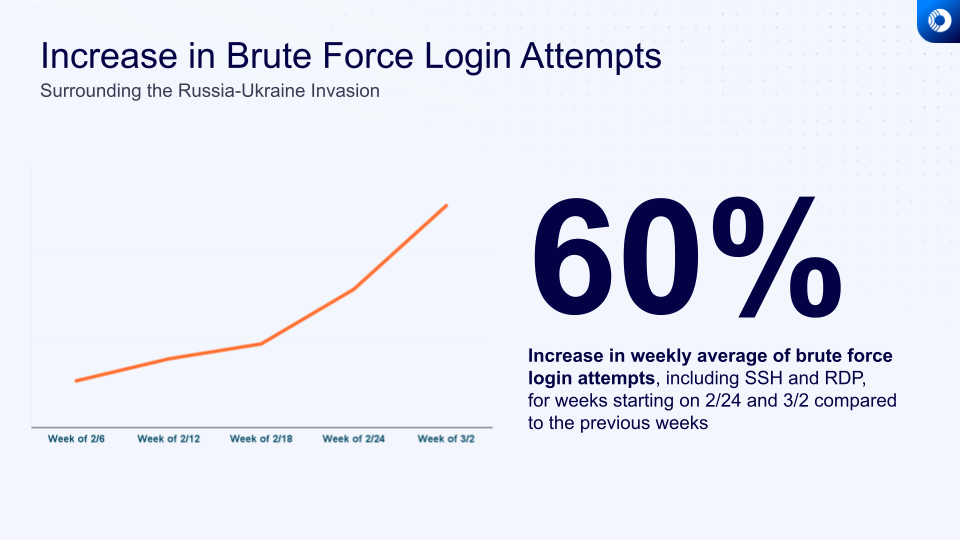
This can indicate two processes that are believed to happen at this stage in the cyber field of war. First, Russian hackers are looking for machines that could be “zombified” and leveraged to become participants in Russian DDoS attacks on Ukraine-related targets. We already see such tools in the wild. For example, the Hermetic wiper, published by Microsoft as FoxBlade, is capable of turning PCs into DDoS zombies. Second, Russian hackers might be looking for a foothold in significant western entities to execute attacks like data wiping or data exfiltration, which could lead to damage and embarrassment to Ukraine’s allies.
How can you protect yourself?
- Reduce your attack surface: Internet-exposed assets are a possible attack surface. Make sure to expose as minimal a number of assets as possible. In addition, for these assets, make sure not to grant high privileges to your account and not to store confidential data as un-encrypted.
- Patch vulnerabilities and keep assets updated: Unpatched machines can be exploited by a malicious actor. Keeping your assets up-to-date, can reduce the risk of remote exploitation.
- Use MFA and complex passwords: Multi-factor authentication (MFA) makes unauthorized access harder. Assets with complex passwords are harder to brute force.
- Use logging services: Logging services are now offered by all major cloud providers and help you stay on top of account monitoring.
Trending This Week
#1 The 5 SOC 2 Trust Services Criteria Explained
#2 What You Need to Know About the Daixin Team Ransomware Group
#3 Mitigating Security Risks in Retrieval Augmented Generation (RAG) LLM Applications
#4 Cybersecurity 101: 10 Types of Cyber Attacks to Know
#5 Detecting and Mitigating NTLM Relay Attacks Targeting Microsoft Domain Controllers
Related Articles:
Breach Debrief: The Fake Slackbot
Published: 04/22/2024
Are You Ready for Microsoft Copilot?
Published: 04/19/2024
Implementing a Data-Centric Approach to Security
Published: 04/19/2024






