Change These 7 Security Settings After Creating a New AWS Account
Published 11/17/2022
Originally published by Varonis.
Written by Shane Waterford, Varonis.
If you’ve just created your Amazon Web Services (AWS) account and are worried about AWS data security, you have a valid reason — unknown organization-wide settings or simple misconfigurations could put your data at risk of exposure. However, there are a few immediate steps you can take to dramatically improve your security posture.
Amazon provides you with tools and services to help secure your environment, but ultimately the responsibility lies with you to configure these services correctly and to routinely monitor for gaps or issues. AWS relies heavily on role-based access control and by default, services, and users (bar the root user) have very little to no access. The most important steps you need to take to improve AWS security relate to user management and standard policies.
Replacing the root user with an administrator should always be your first step. Once that's done, you’ll need to create users with access that reflects the minimum amount of permissions required to do their job. Next, secure those users' access by defining password policies.
As the organization begins to scale and you begin to use more services, you may require more fine-tuned configuration options. There are some high-level services, however, that will continue to ensure good security, no matter how big or fast the organization grows. AWS services like CloudTrail and Security Hub can be used to monitor and alert users about security issues from day one.
1. Create an admin account
The principle of least privilege is a well-known security concept that limits a user's access to only what is required to perform their job. For example, providing a user with both read and write access to an S3 bucket when only read access is required would be a violation of least privilege.
Root user credentials offer unlimited access to an account and all of its resources. With this in mind, it's easy to see why root access is rarely required, instead, you should use identity and access management (IAM) users and IAM roles with restricted permissions. It is an acceptable practice to create a single administrator user for day-to-day account administration — AWS created a role (with a subset of root access controls) specifically for this purpose.
How to add an administrator:
- Log in to your AWS account using your root user credentials.
- Navigate to the AWS IAM service using the console search bar.
- Select “Add user.”
- Set admin or administrator as the username.
- Select AWS Management Console access and Programmatic access (if required) for the access types.
- Enter a strong password containing upper- and lowercase letters, digits, and special characters. Use a password manager to generate a strong password or select an autogenerated password if needed.
- Uncheck “Require password reset.”
- Select next.
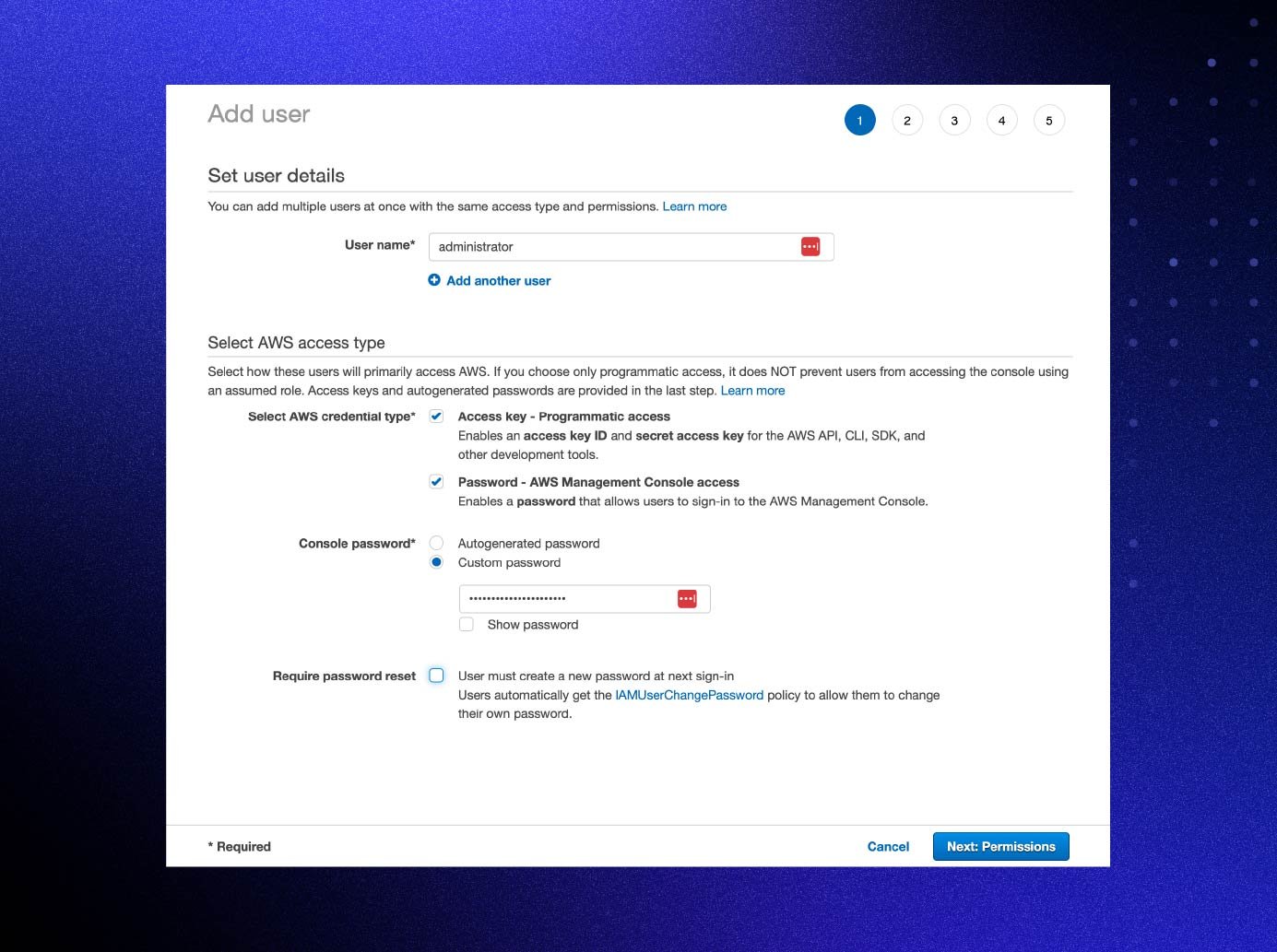
- Choose “Attach existing policies directly” and select the AdministratorAccess policy.
- Select “Next” again to complete user creation. If programmatic access was selected, store the provided access keys somewhere secure.
Tip: Similar to how you create the administrator user to prevent root access, you should create more users in a similar manner to prevent the use of the admin user when not required. All further users and roles should strictly follow the principle of least privilege.
Why is this important?
You should only use the root account on rare occasions for activities such as updating billing details, enabling AWS marketplace or AWS support, or canceling the AWS account.
2. Update root user access
After you’ve created an admin user, it's time to restrict root user activity to only top-level account administration duties. Never generate access keys for a root user. Instead, use a strong password and immediately enable multi-factor authentication (MFA) to prevent its misuse — accidental or otherwise.
How to update root user access:
- Log into the account using root user credentials.
- Once you’ve logged in, click on the username and select “My Security Credentials” from the dropdown menu.
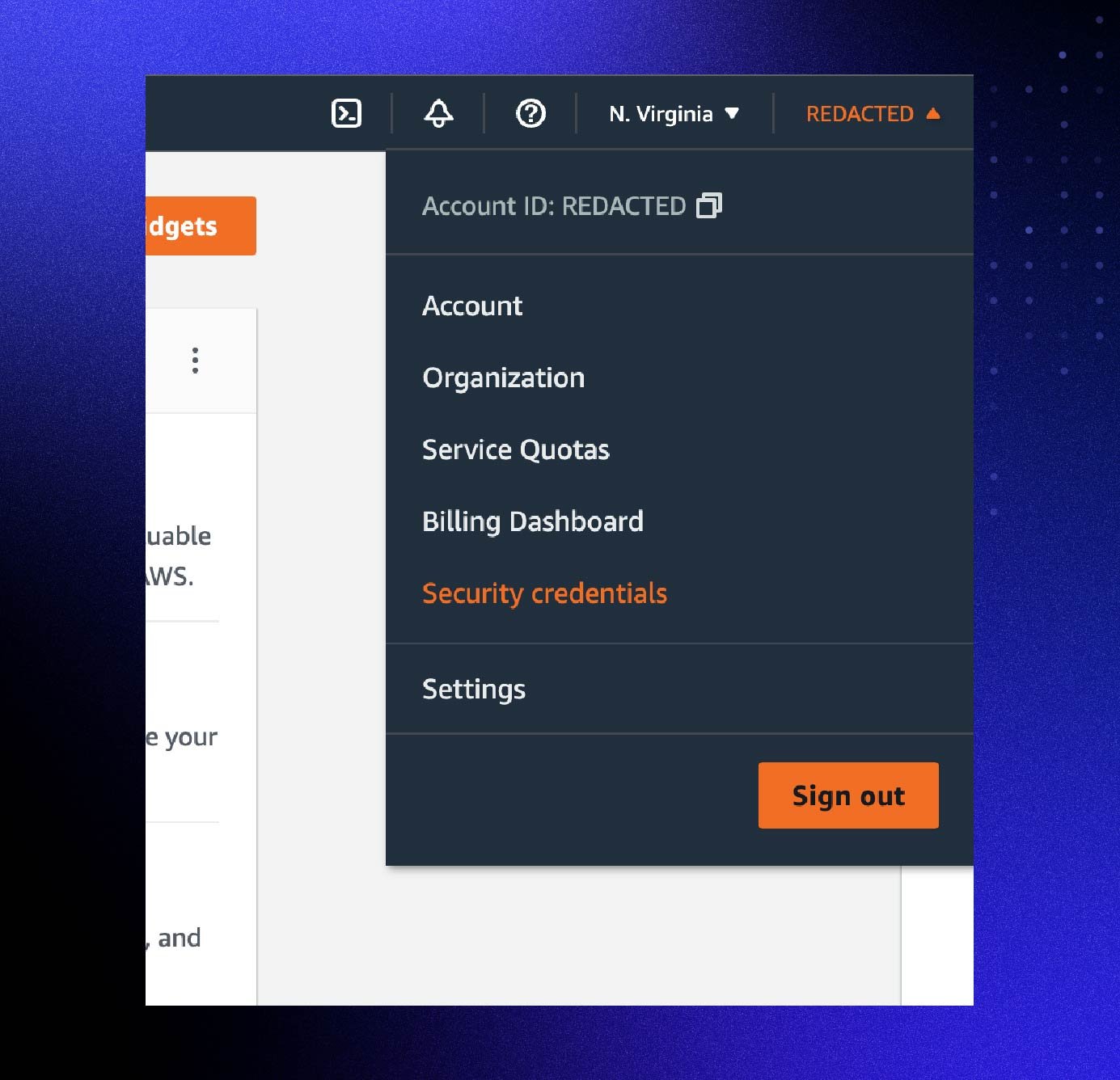
- Select “Activate MFA” and choose your desired MFA approach following the on-screen instructions.
Tip: MFA is not a replacement for strong passwords. Use a randomized password with letters, digits, and special characters. If you feel worried about misplacing or forgetting the password, use a password manager.
Why is this important?
The root user has access to all services and resources and can perform administrative actions including canceling your AWS account.
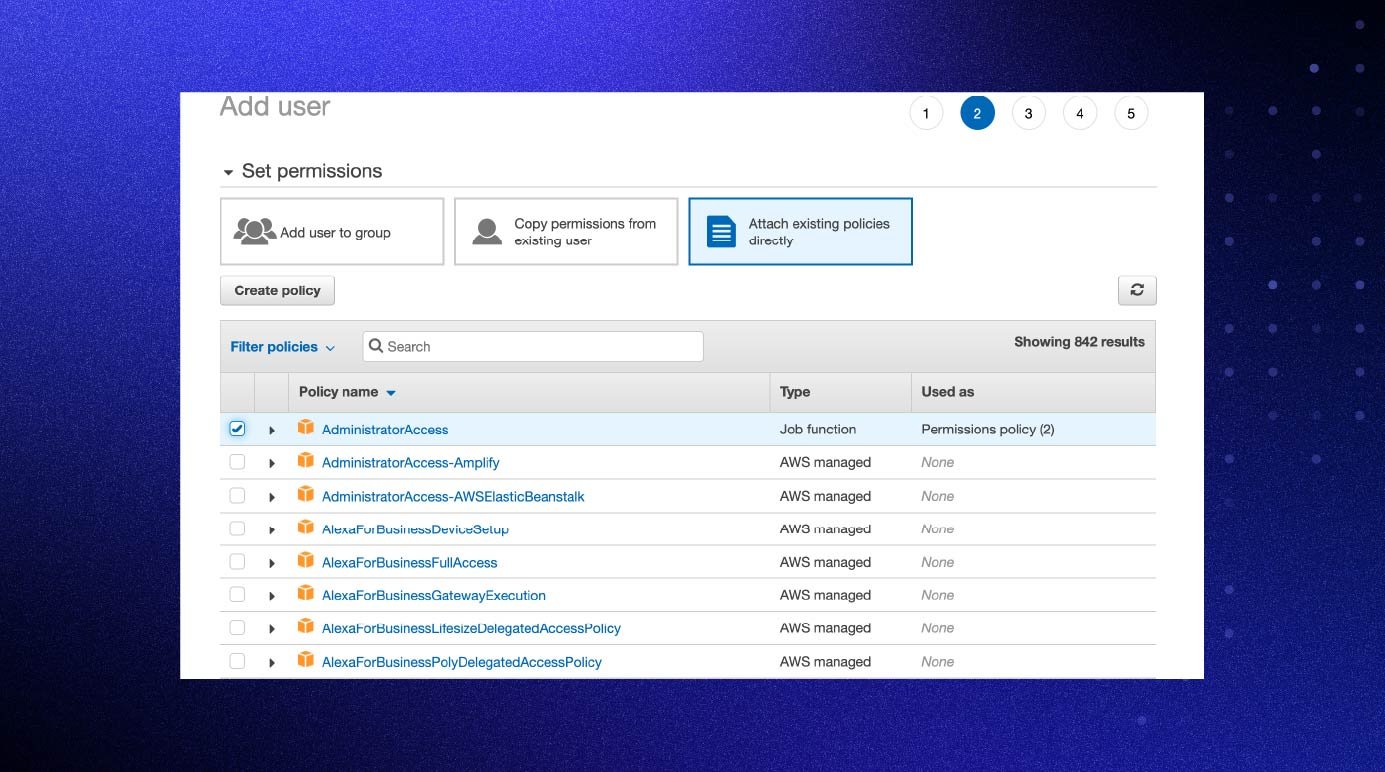
3. Create your AWS users
Now that you’ve created an administrator user, the next step is to create your day-to-day AWS users and define their access; using the administrator role should be limited to only when it’s necessary.
The easiest way to create your AWS users is by using groups. This will allow you to easily change multiple users' access at once. This is useful if a certain group suddenly needs access to a new service, or no longer needs access to another. It’s important to note that users should not share the same login, as this will affect traceability and accountability.
How to add daily AWS users:
- Sign in to AWS and open the IAM service.
- Choose “Users” and then choose “Add users.”
- Type a username for the new user (use the Add Additional User option to bulk-create users). The username will be their sign-in name for AWS.
- Select how the user(s) will access AWS. If the users require API access then select programmatic access; if they are allowed to log into AWS then select AWS Management Console access. You can select both, but consider the use cases and be careful to avoid providing unnecessary access.
- Select “Require password reset” to ensure users change their password the first time they sign in.
- On the next page, select how you want to assign permissions.
- The easiest way to assign permissions is by using groups. For now, choose “Create group.” The next time you want to add a user to this group, it will appear as an option on this page. Type in the group name and select the policies you wish to apply. Remember to follow least-privilege principles to limit users' access to only the services and resources they require to complete their job.
- The next screen is related to tags, so just click “Next” for now.
- Review the options you configured and click “Create User” to access the users' credentials. Distribute these carefully — selecting the “send email option” will provide the user with their username and console URL (if required), however, it is up to the administrator to provide the password or access keys using a custom channel such as via a phone call or over email.
Tip: At first glance, it may be difficult to select a policy that matches your exact requirements. In this case, select the most suitable option and later create a custom policy that can be added to that group.
Why is this important?
Minimizing access and keeping a record of who has access to what is critical for securing your AWS account, especially for those seeking to become compliant with standards such as ISO and SOC 2.
4. Secure access using MFA
Now that you’ve created users and groups, it's time to secure the access of those users via MFA.
How to manage MFA:
- Sign in to AWS and open the IAM service.
- Choose “Users” from the “Access management” menu and in the ‘Users’ list choose the name of the user with console access.
- Choose the “Security credentials” tab and next to “Assigned MFA device,” select “Manage.”
- In the “Manage MFA Device’” wizard, choose your desired MFA approach and follow the on-screen instructions.
- Repeat these steps for all users with console access.
Tip: If using a virtual device for MFA such as Google Authenticator, submit your codes immediately after generating them to ensure the MFA device is in sync.
Why is this important?
A user’s access is only as secure as their password. Whereas access keys are inherently complex, a bad actor may be able to guess your password. MFA reduces this risk.
5. Set standard password policies
It's time to double down on securing user access. Use password policies to make sure passwords meet company, and if applicable, regulatory standards.
How to set password policies:
- Sign in to AWS and open the IAM service.
- Choose “Account” settings.
- Choose “Change Password Policy” in the “Password Policy” section.
- Select the options that you want to apply to your password policy and save your changes.
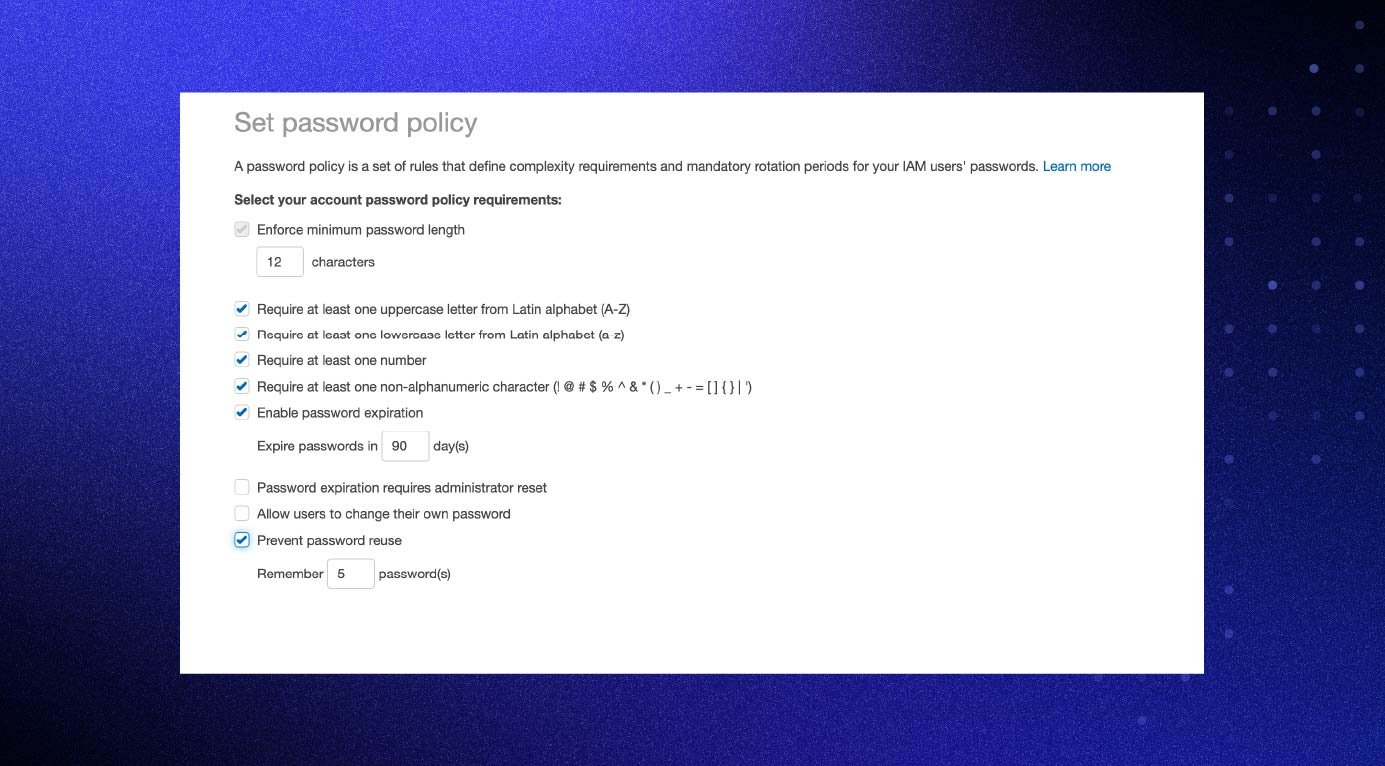
Tip: Choose a balance between secure and maintainable. For example, expiring users' passwords every day could become a logistical nightmare.
Why is this important?
While it’s vital to maintain a secure password policy, multi-factor authentication becomes less secure if one of the factors is negligible. Having a strong password ensures that even if an MFA token gets compromised, any passwords brute force attacks will fail.
6. Define custom policies
When assigning policies to groups, you may have noticed that AWS provides an extensive library of prepackaged policies. These policies will cover a lot of standard use cases, but it's essential to define your own policies if the out-of-the-box policies still provide your users with too much access.
For most companies, this is an ongoing, iterative process, and it's an important practice to start early, as these policies are the foundation of a secure AWS architecture.
How to create your policies:
- Sign in to the console and open the IAM service.
- Choose “Policies” and then choose “Create Policy” or “Get Started” if no policies have been created yet.
- Choose “Create Your Own Policy” and add a descriptive name in the policy name field.
- Use a policy generator such as the one provided by AWS to craft a policy document; the screenshot below shows a generated policy that limits the user to a specific set of actions against a specific set of services and resources. You can copy the provided policy into the “Policy Document” field and click “Create Policy.”
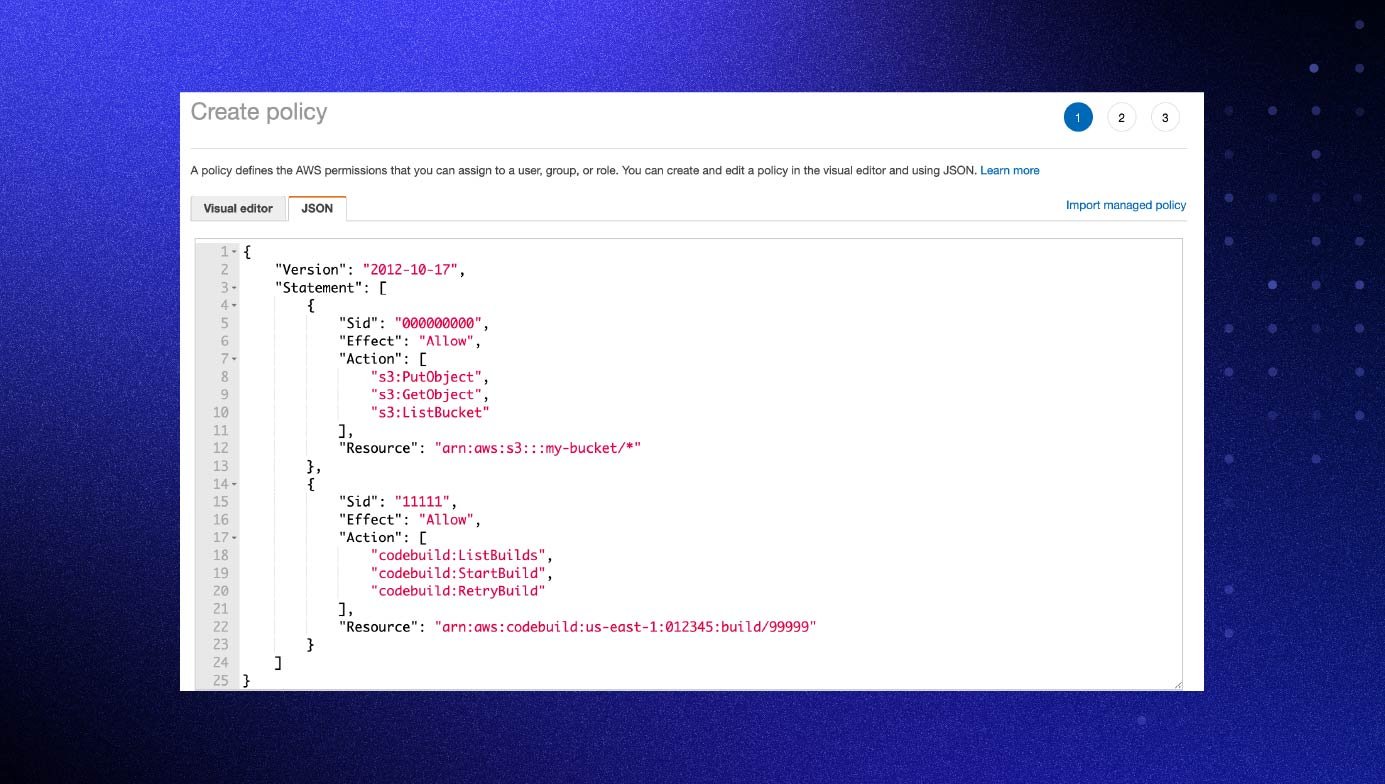
Tip: Always refer to the principle of least privilege when writing policies. Reduce any potential attack vectors by limiting the policy to only allow required actions against required resources.
Why is this important?
Limiting a user to a predefined set of actions and services or resources prevents misuse of AWS services, accidental or otherwise.
7. Secure EC2 use
Once you have your policies and procedures in place and your console users are ready to start using AWS, you can look at locking down individual services at the service level. One example is AWS’s popular compute service, Elastic Compute Cloud (EC2). EC2 allows users to spin up compute instances with their choice of processors, storage types, and operating systems. This is undoubtedly a tremendous help to developers, however, it is also a dangerous service to have enabled if it’s not secured. One of the most simple steps to secure EC2 use is to restrict users to pre-approved tagged Amazon Machine Images (AMI), a supported and maintained image provided by AWS.
How to secure EC2:
- Have the development team or security team create an AMI that meets company security requirements and then review and tag it.
- Use your policy knowledge from earlier tips to create a tag condition that restricts users' permissions to launch only instances that use the tagged AMI.
- Attach this policy to the user group.
Tip: See this link for a detailed breakdown.
Why is this important?
Using an insecure EC2 instance can open up your organization to sophisticated attacks. Should attackers gain access to that instance, they can assume its role and access all the same resources.
Other AWS security tips to keep in mind
Now that the AWS account has been fully set up, it's time to start future-proofing your AWS security. There are practices and principles you should follow outlined below.
Use infrastructure as code via CloudFormation.
The CloudFormation service lets you define your entire infrastructure as code (IaC). This allows you to version-control your infrastructure using tools such as git and makes it easy to subject your architecture to peer review and automated validation. You can easily configure, update, and redeploy services and policies across accounts and regions without fear of human error.
Create stages using AWS Organizations.
AWS Organizations allow you to quickly scale your organization by programmatically creating AWS accounts and managing them all from one central hub. This means you can audit and apply policies to multiple accounts and simplify your billing all in one place.
Easy account management combined with CloudFormation allows you to create and monitor development, staging, and production accounts, giving you confidence that production is always stable. You can also have separate accounts for auditing and monitoring, which makes breaking down AWS bills easy.
CloudTrail increases activity visibility.
Once you have set up multiple accounts, it's important to monitor each account's activity for auditing purposes. CloudTrail logs will show every action a user takes and will allow you to quickly identify if anyone is performing actions they shouldn’t or if any users need resources they cannot access. CloudTrail logs will show what user performed (or attempted to perform) what action against which resource and when.
To make sure CloudTrail truly reflects your account's activity, ensure it is configured to send all logs to a central bucket that no one but the CSO can access. This prevents users from carrying out actions and removing any traces of their own activity from CloudTrail.
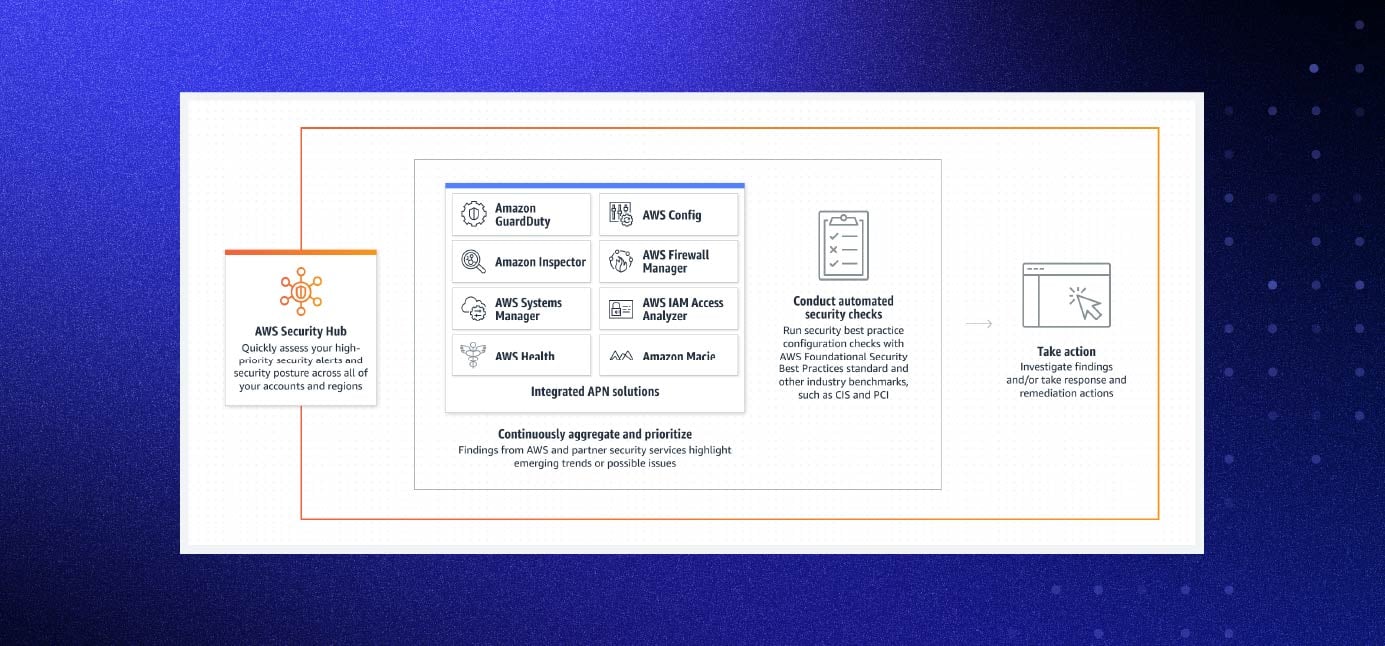
Automate security with Security Hub.
As your organization scales, manual processes can become increasingly difficult. AWS offers a range of services to tackle different security issues. Even with those tools, though, managing the findings of the services can be overwhelming.
Security Hub reduces the effort required to collect and prioritize security findings across accounts and services. It automatically handles data in different formats and normalizes the data so that it can highlight and correlate findings across multiple services. Security Hub can identify activity patterns and help provide insight into what's happening in your account.
This service uses industry best practices and standards to provide you with overall health status. Service Hub even integrates with EventBridge, allowing you to automate the remediation of specific findings.
Closing thoughts
IAM is crucial to securing AWS as your organization scales, and role-based access control sits at the heart of AWS security. Before you configure your new AWS account, you can find additional helpful information about IAM here.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026




.jpeg)

