CSA Survey Finds Organizations are Shifting their Use of IAM Capabilities in 2021
Published 11/25/2020
The use of cloud services have continued to increase over the past decade. Particularly in the wake of the COVID-19 public health crisis, many enterprises' digital transformations are on an accelerated track to enable employees to work from home. CSA surveyed these organizations to better understand how cloud services are being used during this transition and how organizations are securing their operations over the next 12 months.
Below is a summary of the key findings found in this report. You can download the full results here.
Key Finding 1
Multi-cloud is being used by many organizations.

81% of respondents reported that their organizations are utilizing a multi-cloud strategy. However, further follow up demonstrated that companies rely heavily on one of public cloud providers over the others. The other providers tend to be used for more specialized workloads. There also isn’t one cloud provider that is favored across the industry. The market share among the top providers has become more evenly spread. The use of public cloud platforms has allowed organizations to adapt to the remote workforce. The majority are using a multicloud approach increasing the complexity of security and visibility issues for many organizations. Organizations developing in these platforms are increasingly turning to agile techniques and technologies incorporating DevOps methodologies.
Key Finding 2
Diversity of production workload types is expected to increase.
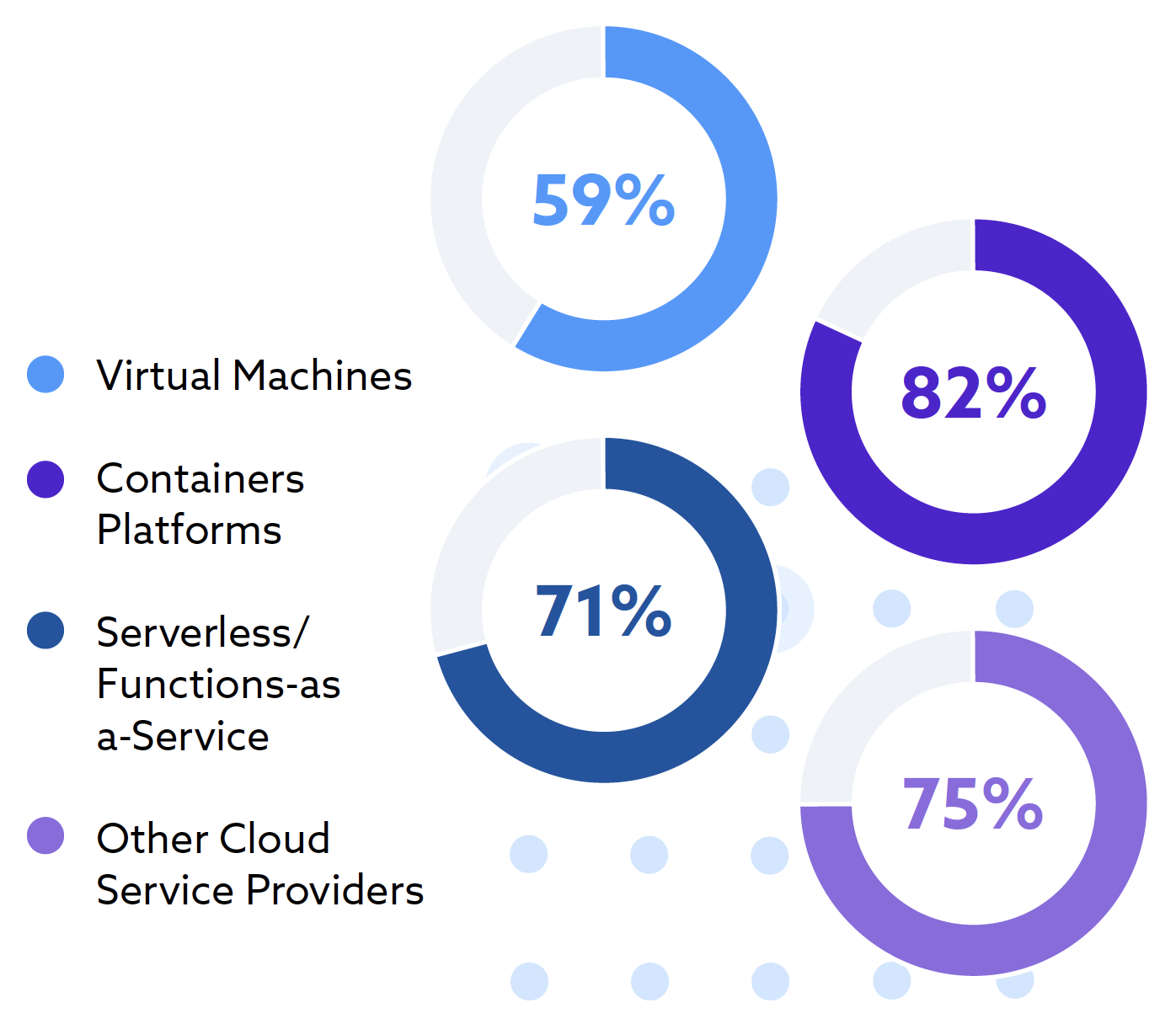
Respondents expect more diversity of production workload types. In addition to increased production with traditional virtual machines (59%), workloads using cloud-based services such as containers platforms (82%), serverless/ functions-as a-service (71%), and other cloud provider services (75%) are also expected.
The use of these technologies allow for increased portability, agility, and the embedding of security in code or “shifting security left.” This shift of security within the DevOps production cycle ensures quality testing and that security is built in earlier in the development process. The growing remote workforce and utilization of cloud services and development technologies has created a complex environment requiring additional security tools or strategies for identity security
Key Finding 3
Organizations are shifting their use of IAM capabilities over the next year.
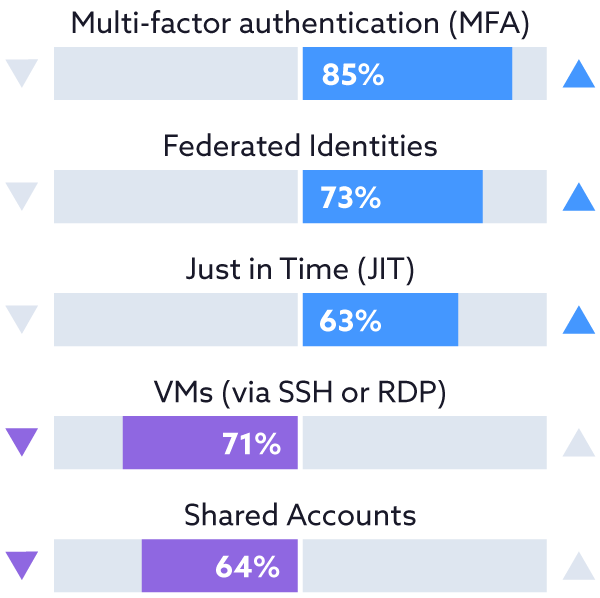
On-premises or in the cloud, IAM methods such as MFA, federated identity, JIT, and advanced user privilege and access capabilities allow for more granular control and reduce security risks. Many of the organizations surveyed predict a rise in the use of these IAM techniques and will utilize a mix of cloud service provider capabilities as well as third-party vendors to meet those needs.
Key Finding 4
Privilege and permission management rated as a top IAM security challenge for organizations for both humans and machines.
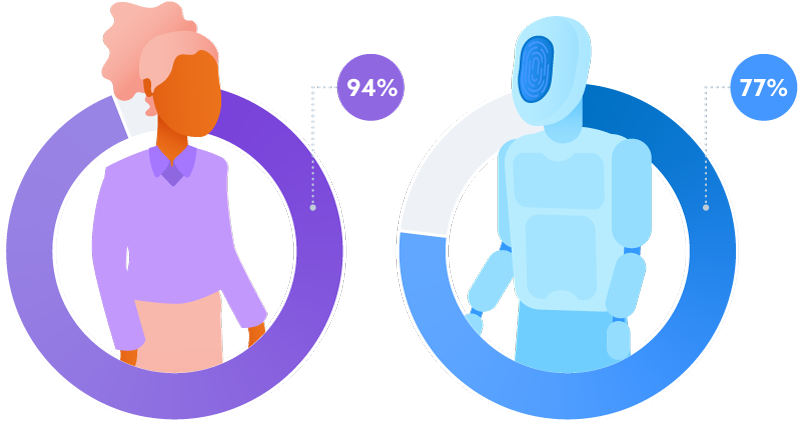
Privilege and permission management was rated as high or extremely high priority for human identity (94%) and machines (77%).
You can read the full results of the survey for free.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026





.jpeg)

