Cloud Incident Response: Guideline for the Dark Cloudy Days
Published 04/22/2020
By Prof. Alex SIOW, Professor (Practice) in the School of Computing, NUS & LIM Soon Tein, Vice President, IT, ST Engineering Electronics

When in the cloud, there are other considerations to IR strategies. Handling incidents on the cloud is fundamentally different than traditional on-premises IT, and this deviation arises due in part to three key aspects – Governance, Visibility and Shared Responsibility of the cloud.
Governance
When organizations engage multiple cloud service providers (CSPs), in addition to the fact that data could reside in multiple locations in the cloud, it could also be challenging getting the various organizations to investigate an incident together.
Visibility
Running workloads and services in the cloud means that organizations no longer have the same rights of visibility as traditional IT. Much of the underlying supporting infrastructure and services are abstracted and organizations can often only view logs provided by the CSP for the specific service being used. This can be a challenge when trying to fully understand an incident and stem its spread or escalation.
Shared responsibility
Cloud security involves various stakeholders such as cloud customers and CSPs and / or third-party providers. The various stakeholders have their part to play in this shared responsibility model. Generally, the customers are responsible for their own data, and the CSPs for the cloud infrastructure and services that they provide.
A common framework that IR teams adopt is the lifecycle in NIST SP800-61R2 Computer Security Incident Handling Guide which runs through the phases of Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Mortem.
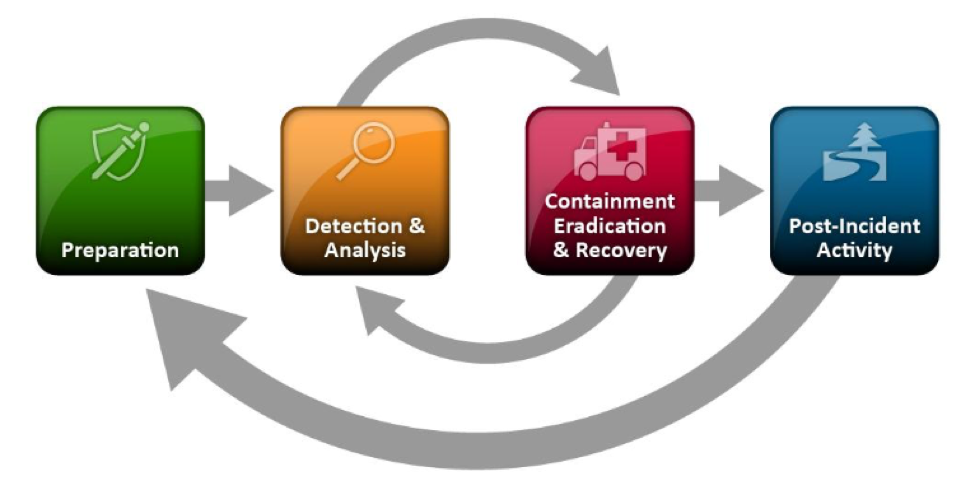
Incident Response Lifecycle in NIST SP800-61R2 Computer Security Incident Handling Guide
To further reinforce the CIR, a vital puzzle piece of ‘Coordination and Information Sharing’ that is iterated at each phase of the CIR plan should be considered. Effective communication is not limited to just reporting to the customers. An attack typically affects more than one organization, simultaneously. Thus incident information sharing is mutually beneficial in helping other organizations guard against the same threats. The CSA runs the Cloud Cyber Incident Sharing Center (CloudCISC) that facilitates the sharing of incident data between participating CSPs.
When a critical incident occurs, there is no time to waste figuring out the game plan - every second that goes by is more data being potentially compromised. Having a methodical, step-by-step response plan can help organizations be better prepared when dealing with cloud incidents, which helps to manage and minimize damage to businesses.
The Cloud Incident Response (CIR) Working Group (WG) coalesces various industry incident response best practices and frameworks available in the industry in an on-going work, ‘Cloud Incident Response Framework’. The framework covers the major causes of cloud incidents (both security and non-security related) and their handling and mitigation strategies with the aim to provide a holistic and consistent view across widely used frameworks for the reader. This serves as a go-to guide for cloud users to effectively prepare for and manage the aftermath of cloud incidents, and also a transparent and common framework for CSPs to share cloud incident response practices with their customers.
The WG recently released a ‘Cloud Incident Response – A Quick Guide’, a succinct prequel to the main framework covering key ideas and concepts. Readers can expect a step-by-step guide, from preparation to post-mortem, with CIR guidelines curated for different levels of incident severity in the upcoming deliverable.
As a work in progress, the CIR WG welcomes individuals who are interested in contributing to this work to join the WG by registering here.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How Organizations are Addressing Cloud Investigation and Response
Published: 01/22/2026
Your Cloud May Be Secure, But Are Your Backups? Lessons From The EY Incident
Published: 01/12/2026
Closing the Cloud Forensics and Incident Response Skills Gap
Published: 12/16/2025






.jpeg)