Life During Wartime: Proactive Cybersecurity is a Humanitarian Imperative
Published 02/07/2024
Written by:
Stan Mierzwa, M.Sc.; CISSP, Head Center for Cybersecurity & Lecturer, Kean University; President CSA NJ Chapter
Diane Rubino, M.A.; Adjunct Assistant Professor, School of Professional Studies, New York University; Nonprofit Board Member.
In brief:
- Humanitarian agencies responding to conflict face massive challenges in distributing aid. Cyberattacks add to that burden.
- This short overview, tailored for non-technical leaders, demystifies the process and equips clouds security experts to proactively champion cloud security at non-profits, and non-governmental organizations.
It’s impossible to imagine the nonprofit world without information technology (IT). Every mission-driven, social change non-profit, and non-governmental organization, including aid agencies responding to crises in Israel-Gaza, the Ukraine, and other flash points, leverages IT to boost effectiveness and efficiencies.
Yet risk, cyber and otherwise, is a byproduct of technological efficiency. Even the most well-planned relief efforts can be delayed or negatively impacted by hackers. First responders and those delivering longer- term support need to think about thwarting bad actors.
Rather than re-inventing fire, organizations can reduce risk with a straightforward plan and introduced focus into the realm of cyber. This strategy is adapted by nonprofit leaders for the sector from the National Institute of Standards and Technology’s (NIST) well-considered Cybersecurity Framework.
Call to Act: Cyber Defense Planning
Cyberthreats may only seem like a problem for higher-profile organizations—or for financial institutions and credit card companies. But not-for-profit groups can be targeted too and can possibly be an easy bull's eye.
Potential solutions may seem so complex, costly, or time-onsuming that they’re easier to ignore than act upon. But some steps -- like inventorying hardware and software -- are low-budget and straightforward. This move alone can highlight vulnerabilities and is a necessary step for building a secure foundation.
One central idea of this writing is to pose a nuanced response to the question, “Who’s responsible for cybersecurity?” It may appear to be the exclusive terrain of IT experts. While there's some truth to that perception, that’s not the full story. What’s also needed is strong institutional leadership who can ensure such issues are prioritized and implemented by the organization.
Bigger challenges = More threats
When operations become more complex, attack surfaces -- entry points intruders exploit for access – multiply. Cloud products, data collection solutions, hardware, remote and mobile systems, software, and physical security-protection equipment (IT-fueled access-control, alarms, fire- and environmental protection, and surveillance), are just a few of the potentially susceptible areas.
Internet-connected or cloud-based data repositories and solutions offer rapid resolutions to cyberattacks. These tools also offer opportunities to study how these attacks happen and what can be done to prevent them going forward.
Organizations that work in high-profile, politically sensitive situations and sectors may also be the target of ideologically motivated hackers, in addition to garden-variety wrongdoers. This heightens the potential that their essential work can be disrupted.
It may seem improbable - even impossible - for those working to put out real fires to add cybersecurity prevention to their to-do list. But a brief pause can help agencies avoid exacerbating existing humanitarian crises.
Think Like a Pro: Basic Ideas, Powerful Actions
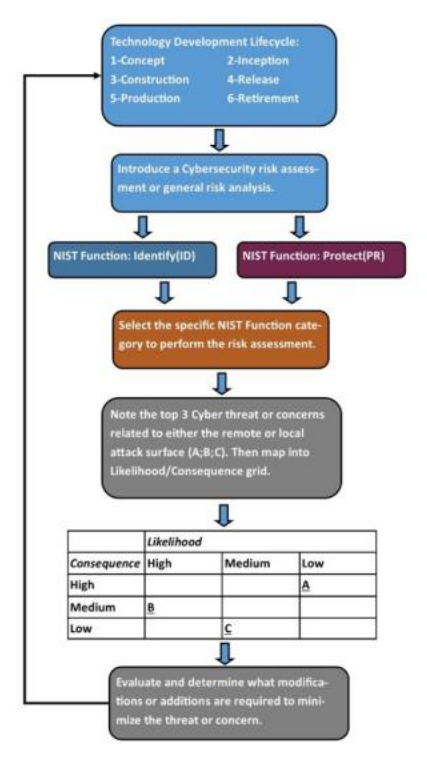
1. Cybersecurity risk assessment and staff training can be introduced at any phase of the activity/project.
2. Select a phase of the project lifecycle, Concept, Inception, Construction, Release, Production(Implementation), and Retirement. If you’re already implementing the project, start there. Then, from the NIST Cybersecurity Framework’s Identify, Protect, Detect, Respond, and Recover Framework, select one action from each of the first two functions. The Federal Trade Commission has a Framework cheat sheet outlining more straightforward action. Link: www.ftc.gov/business- guidance/small-businesses/cybersecurity/nist-framework2.
- Identify: Jumpstarts cyber-protection efforts by: drafting an inventory of hardware and software; or reviewing existing cybersecurity policies to identify gaps and gain greater security awareness.
- Protect: Enhance the ability to limit attacks by: establishing a data security protocol or ensuring that any existing security software, like an anti-malware program, is up-to-date and updated regularly.
3. Note the top cyber threats or concerns in the Identify function of the project phase.
4. Rank the threats using a likelihood/consequence grid.5. Based on the grid, prioritize the modifications needed to minimize threats.
Figure 1: A likelihood/consequence grid.
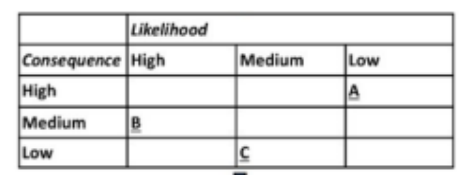
5. Based on the grid, prioritize the modifications needed to minimize threats.
6. Apply the steps above the Protect function, determining if concerns require change.
Figure 2: Program Development Lifecycle Phases with Cybersecurity Risk Analysis.
Sky-High Stakes
The U.S. government sends billions of dollars in assistance to Ukraine, Israel, Gaza, and other humanitarian hotspots.3 Because need is dire, humanitarian and global public health organizations have and continue to respond quickly, with IT used to support efforts. It didn’t take long, but two relief organizations providing support and aid to Israel and Gaza reported hacking attempts shortly after October 7. (Siddiqui, 13-Oct-2023). Presumably, there have been other instances since.
Some domestic nonprofits may navigate politically sensitive environments, too. With the upcoming presidential election, prominent politically aligned nonprofits may have prioritized robust cybersecurity measures to avoid hacking attempts and breaches. The security preparedness of less established groups, however, raises additional questions.
With escalating cyber threats in a polarized society, safeguarding the data of non-profits has become even more critical. This includes confidential details about: how they operate, who donates, and information about vulnerable clients.
At a minimum, organizational leadership, information technology, and cybersecurity teams should coordinate response activities and avoid glossing over the technology components of their efforts. Keeping a keen eye on potential risks taking some straightforward steps, is a start. It may curtail potential breaches that could deter effective, expedient humanitarian response initiatives.
Don't let an avoidable cyber breach become the undoing of crucial humanitarian efforts here and abroad. Open communication between leadership and cyber teams and coordinated efforts within an evidence- based framework are the building blocks of digital defense. Proactive cybersecurity isn't just a necessity; it's a humanitarian imperative.
About the Authors
Stan Mierzwa [email protected]
Stan leads the Center for Cybersecurity at Kean University and teaches undergraduate and graduate courses in cybersecurity, information security, and Management Information Systems. He is the National Security Agency Center of Academic Excellence Cyber Defense Point-of-Contact for the university. Stan is a first-generation college graduate and is currently a Ph.D. candidate in the middle of a dissertation focused on the non-technical or soft-skill competencies of cybersecurity college graduates. He is a Certified Information Systems Security Professional (CISSP).
Diane Rubino [email protected]
Diane is a communications practitioner and professor specializing in climate-change communications; organizational and communications ethics; misinformation. She’s on the faculty of New York University and Columbia University. Diane’s written dozens of articles and given workshops and guest lectures around the world. She’s earned Fulbright awards to Bulgaria, Pakistan, and Serbia and spent twenty years in the nonprofit sector as a professional and advocate. Diane is on the Board of Directors of the Hoboken Family Planning Clinic.
Additional Resources
Mierzwa, S. and E. Perez. (2021 March 10) Taking a Practical Timely Opportunity to Evaluate the Security of Your Cloud Video Surveillance Solution. Online resource: https://cloudsecurityalliance.org/blog/2021/03/10/...
Mierzwa, S., RamaRao, S., Jung Ah, Y., & Gyo, B. (2020). Proposal for the development and addition of a cybersecurity assessment section into technology involving global public health. International Journal of Cybersecurity Intelligence & Cybercrime, 3(2), 48-61. https://www.doi.org/10.52306/03020420BABW2272
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
What is a Risk Engineer?
Published: 03/02/2026
Zero Trust for Agentic Pipelines That Touch Cloud Production
Published: 02/27/2026
Agentic AI and the New Reality of Financial Security
Published: 02/26/2026
AI Security: When Authorization Outlives Intent
Published: 02/25/2026





.png)

.jpeg)

