SANS 2022 Cloud Security Survey, Chapter 4: Using IAM to Secure the Cloud
Published 03/20/2023
Originally published by Gigamon.
Editor’s note: This post explores Chapter 4 of the SANS 2022 Cloud Security Survey. Read Chapter 1, Chapter 2, and Chapter 3.
In its 2022 Cloud Security Survey, the SANS Institute offers valuable insights into how a representative set of organizations are meeting the security challenges of the cloud. Previous posts in this series have shed light on 1) how respondents use the cloud, 2) what specific security worries they face, and 3) what security controls they use to lock down their cloud infrastructure.
In this final installment, we’ll see how respondents to the survey are thinking about one specific type of security control: identity and access management (IAM). Identity in the cloud is a thorny problem, one we’ve covered on the Gigamon blog before. This was the first year that SANS surveyed its respondents on the topic, and the answers were illuminating.
Who’s in Charge of IAM?
The first thing SANS tried to learn was which team is in charge of IAM at each surveyed organization. This is a key question, as cloud rollouts often straddle organizational lines, and security can fall through the cracks if the right team isn’t in place.
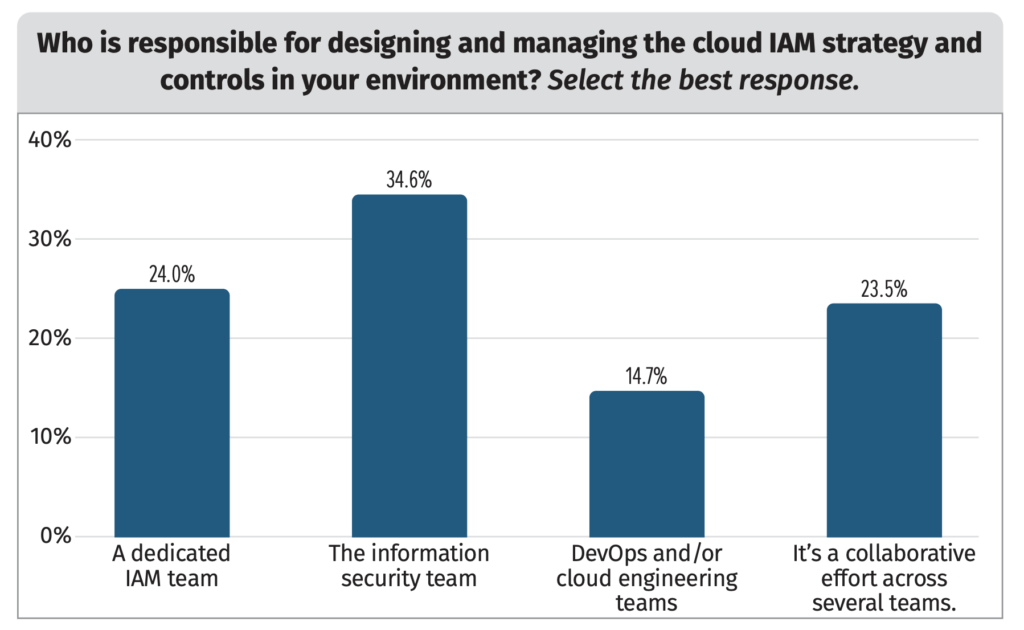
Figure 1. Cloud IAM responsibility.
The most common answer — at 35 percent — was the information security team; only 24 percent of respondents had a dedicated team for IAM. This reflects the fact that many surveyed organizations are on the smaller side and can’t support the headcount for such a dedicated team; that, in turn, illustrates the burden IAM can put on a smaller org. The remaining respondent organizations hand this responsibility to DevOps or cloud engineering teams.
Many Routes to IAM
What form did IAM take at SANS’s surveyed organizations, and what identity platforms did they use? Here, too, there was a diversity of responses, with many respondents choosing more than one answer.
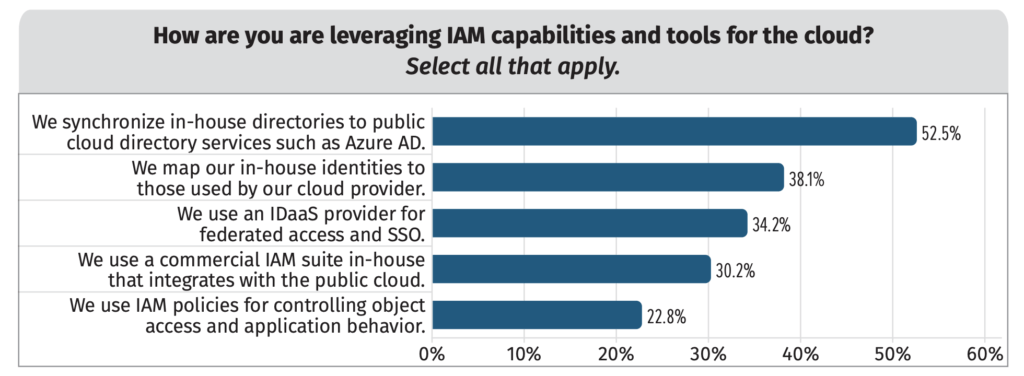
Figure 2. IAM platforms and utilizations.
More than half (53 percent) of surveyed organizations are synchronizing identity stores like Active Directory to cloud directory services. That enables federation to other cloud services and more flexibility in controlling user access to cloud assets, so it’s not a surprise to see it come out on top.
But there are a broad range of other IAM use cases in place as well: Approximately 38 percent of respondents are mapping identities to those available from cloud providers, and just over one-third are using identity-as-a-service (IDaaS) for federation and single sign-on (SSO). Others are leveraging their existing in-house identity suites for hybrid cloud integration.
The low penetration of IDaaS for federation is something of a surprise; SANS claims that the results don’t jibe with what they see in the larger community today. Perhaps this issue will come into greater focus after next year’s survey.
Also note that IAM policies for controlling object access and application behavior comes in pretty low on the list. Those organizations that answered yes to this question primarily rely on native cloud services such as AWS IAM Access Analyzer, manual efforts, or IaC templates to implement and maintain IAM policies. About a quarter use third-party tools, and another 20 percent use open source linting tools as well.
We hope you’ve found this blog series informative when it comes to how to approach the question of security in the cloud — and how improved visibility can help. For a more complete picture, take a dive into the full survey report and get the full details from survey respondents.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026




.jpeg)

