SAP Security Patch Day January 2022: Log4j Causes Record-Breaking Number of HotNews Notes
Published 02/21/2022
 This blog was originally published by Onapsis on January 11, 2022.
This blog was originally published by Onapsis on January 11, 2022.
Written by Thomas Fritsch, Onapsis.
Highlights of January SAP Security Notes analysis include:
- January Summary - 35 new and updated SAP security patches released, including 20 HotNews Notes and six High Priority Notes
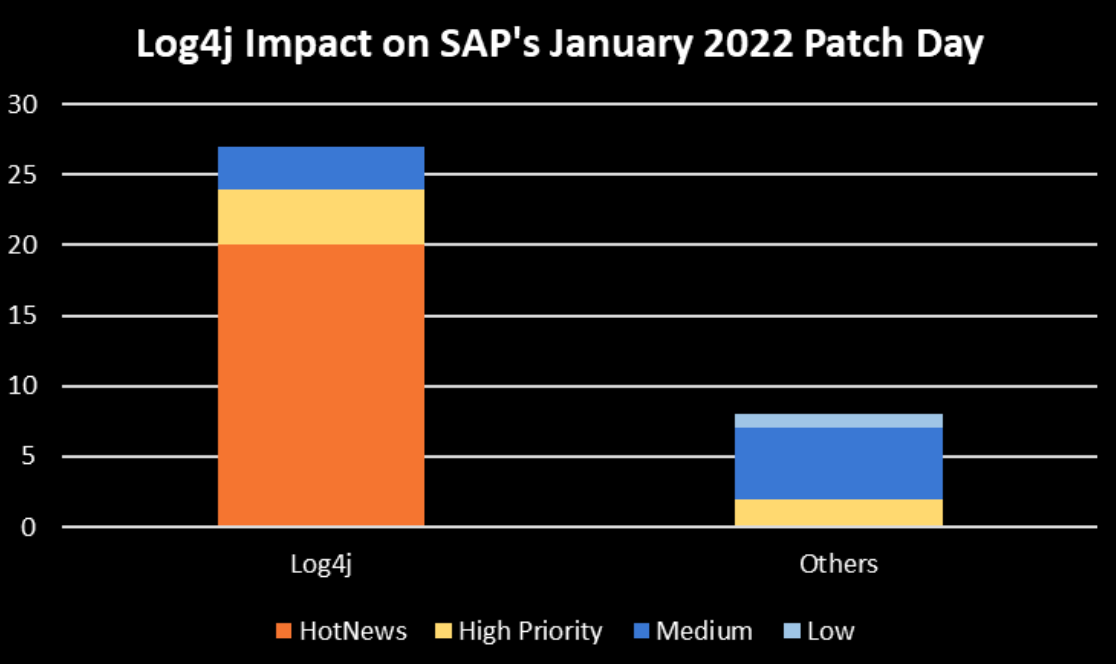
- Information on Log4j - 27 SAP Security Notes, including all 20 HotNews Notes and four High Priority Notes, patches Log4j issues
- Create Single Payment App (ID F0743) - S/4HANA app affected by two critical vulnerabilities
SAP has published 34 new and updated Security Notes on its January Patch Day (including the notes that were released or updated since last Patch Tuesday). This includes 20 HotNews Notes and six High Priority Notes.
It is not surprising that the overwhelming majority of the released SAP Security Notes patch issues were caused by vulnerable log4j versions.
The Log4j Notes in Detail
Checking the Log4j notes in detail, it is clear that, for some SAP applications, there is a way to optimize applying patches to the related vulnerabilities. As is commonly known today, there were multiple vulnerabilities detected and fixed in the log4j library:
CVE | Fixing Log4j Library Version |
CVE-2021-44228 | 2.15 |
CVE-2021-45046 | 2.16 |
CVE-2021-45105 | 2.17 |
CVE-2021-44832 | 2.17.1 |
When looking at the Security Notes for Java Web Service Adapter of SAP NetWeaver Process Integration (SAP NW PI) and XSA Cockpit, one can see separate patches for each of the above log4j versions:
CVE | Fixing Log4j Library Version | SAP NW PI | XSA Cockpit |
CVE-2021-44228 | 2.15 | ||
CVE-2021-45046 | 2.16 | ||
CVE-2021-45105 | 2.17 | ||
CVE-2021-44832 | 2.17.1 | - |
Because of the incremental character of the patches, affected SAP customers don’t need to implement all of them. Instead, it is sufficient to only apply the SAP patches that include the highest log4j version.
While analyzing all applications with regard to Log4j, SAP also detected a completely different vulnerability (tracked by CVE-2019-17571) in SAP Landscape Management Enterprise Edition 3.0. This serious vulnerability was caused by a much older version of the log4j library. SAP Security Note #3132198, tagged with a CVSS score of 9.8, patches a Code Injection vulnerability that was caused by log4j version 1.2. The log4j library is used by the legacy component SAP Crystal Reports and allows an attacker to inject code that can be executed by the application, thus gaining full control of the application. The note provides Patch 02 for SAP Landscape Management 3.0 SP 21. According to the referenced SAP Note #3131766, this patch removes SAP Crystal Reports completely. As this might be an issue for some customers, the note also mentions that version 1.2 of the log4j library is not affected by CVE-2021-44228.
For the most up-to-date information regarding the Log4j vulnerability, please refer to our Security Advisory here.
More High Priority Notes
SAP Security Note #3112928, tagged with a CVSS score of 8.7, patches a Cross-Site Scripting and a Code Injection vulnerability in the Create Single Payment app of S/4HANA (app ID F0743). This app is used by accounts payable accountants through SAP Fiori (SAPUI5). It allows them to make a direct payment to a supplier when no invoice exists as well as pay open supplier line items. The two vulnerabilities existed because uploaded and downloaded files were not checked by the app. The first vulnerability allows an attacker with basic user rights to run arbitrary script code, resulting in sensitive information being disclosed or modified. The second one enables an attacker with basic user rights to inject dangerous content or malicious code which could result in critical information being modified or completely compromise the availability of the application.
High Priority Note #3123196, tagged with a CVSS score of 8.4, was initially released on SAP’s December Patch Day and fixes a Code Injection vulnerability in an utility class for SAP NetWeaver AS ABAP. This note has been updated with some information about its validity. The original validity interval is only valid for SAP customers using the license-bound product Post-Copy Automation (PCA). For all other customers, the minimum patch level of the validity interval has been increased.
Summary and Conclusions
With 35 new and updated notes, including 20 HotNews Notes (all affecting Log4j) and six new and updated High Priority Notes, the first SAP Patch Tuesday in 2022 impressively demonstrates the serious impact of Log4j on SAP applications. As SAP customers can expect more patches in this area in the near future, we recommend to regularly check the following two central references for updates:
- Central Security Note for Remote Code Execution vulnerability associated with Apache Log4j 2 component (SAP Security Note #3131047)
- SAP’s Response to CVE-2021-44228 Apache Log4j Vulnerability
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
Agentic AI Pen Testing: Speed at Scale, Certainty with Humans
Published: 01/26/2026


.png)



.jpeg)