What Did We Learn About Cyber Risk Management in 2021?
Published 12/17/2021
 By Bob Maley, Chief Security Officer at Black Kite
By Bob Maley, Chief Security Officer at Black Kite
“The more things change, the more they stay the same.”
Author Jean-Baptiste Alphonse Karr wrote this in 1849 and it still rings true today, especially in cybersecurity. The number of reported data breaches in 2021 have soared past the total for 2020 and ransomware is the main culprit. The US Treasury ties $5.2 billion in BitCoin transactions to ransomware payments and the average payment has climbed 82% to over $500,000 per transaction.
Ransomware Trends Haven’t Changed
In July, CISA launched StopRansomware.gov to centralize reports, alerts, and other resources. The website is a great response to help educate the general public, but much of the information has been already circulating for more than a decade. The campaign provides guidance for addressing common ransomware attack vectors, but the compliance checklists aren’t built to scale.
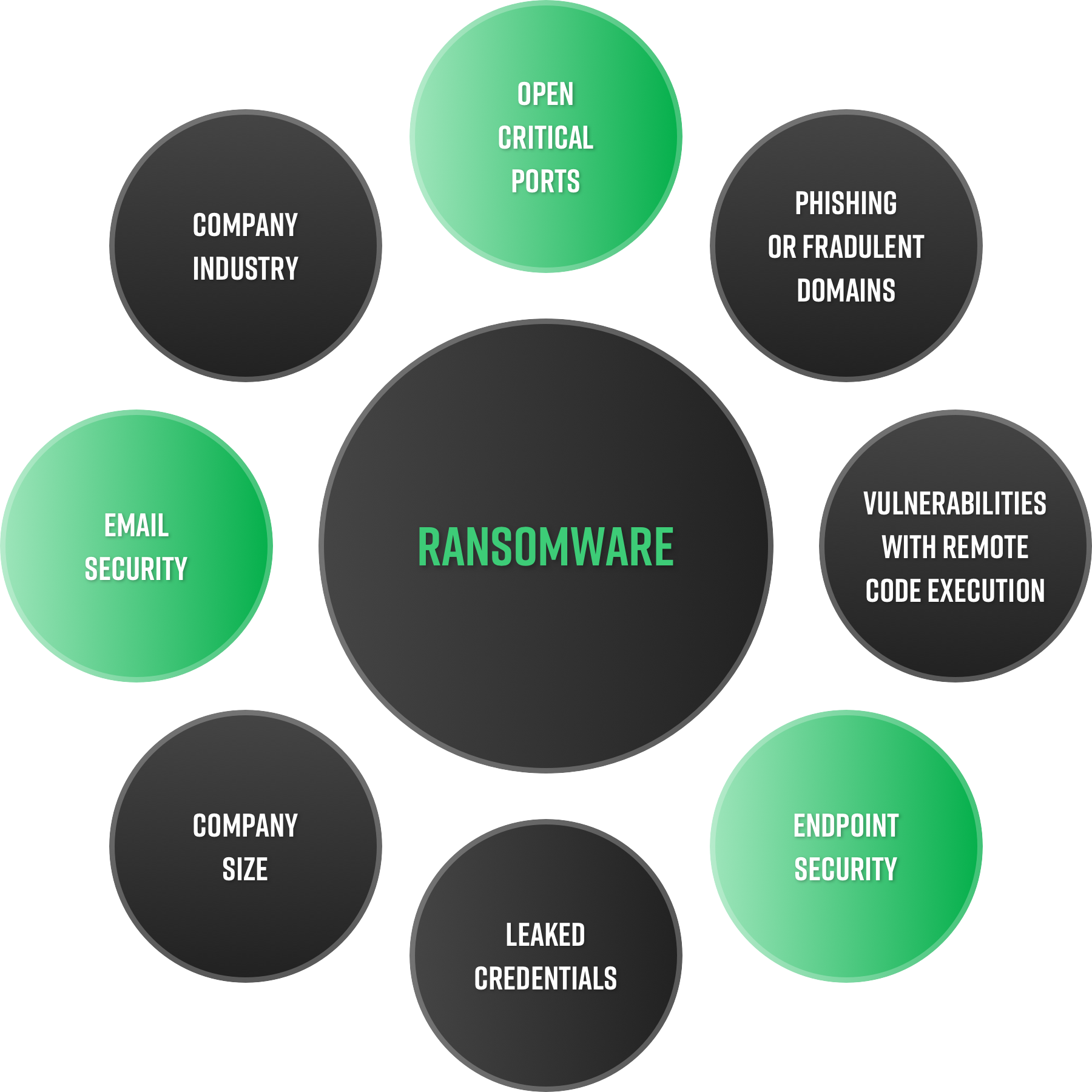
Cybercriminals have found that sharing information and working together in large enterprise groups allows them to spread further and deeper into organizations of all sizes. They are also very adaptable, quickly overcoming challenges and finding new ways to execute a cyber attack.
Is Cloud Security the Secret?
Let’s start with an example from the list of common vulnerabilities above.
Vulnerabilities with remote code execution (RCE) enable network manipulation. RCE intrusions are complex attacks made by malicious threat actors to gain access to a device, regardless of its geographical location. Cybercriminals may pose as an approved network user, receiving the same privileges and network access as the system end user, allowing them to steal, delete, and/or copy critical data. Patch management and regular security updates are an integral part of maintaining secure infrastructure.
48% of small and midsize businesses still rely on unsupported or approaching-end-of-support operating systems for their security needs. In most cases, once a system reaches end-of-life status, there are no more patches available, vastly increasing the threat landscape and leaving the organization wide open for an attack. Technically under most compliance frameworks, that organization can say they are patch compliant.
Cloud security introduces more scalability for infrastructure and has significant potential to alleviate many of the concerns described above. The cloud provides a centralized location for data and applications and often helps streamline information security practices and activity monitoring.
What About Third Parties?
Cybercriminals recognize the opportunity to target organizations with poor cyber posture to make their way into larger, more secure companies that hold confidential information and are willing to pay higher ransom amounts.
Ransomware can put an entire supply chain at a standstill. Continuous supply chain risk assessments alert teams when vulnerabilities are detected to mitigate potential access points before a cybercriminal has the chance to. Third party risk is a crucial part of any cybersecurity management program.
The Bottom Line - It’s Not Too Late
In 2021, cybercriminals learned how to be more agile, exploiting vulnerabilities in new ways and sharing information via underground networks across ransomware groups.
If there is one thing that we should learn, it’s that signals are the secret weapon to becoming more agile than the bad actors. Borrowing a page from their playbook, we must get inside their OODA loop and practice Observing, Orienting, Deciding and Acting. Otherwise, once we’ve realized the full scope of a breach, we may be equally as deep into a new attack.
Remember, compliance doesn’t equal security, and book smart doesn’t equal street smart. You must constantly monitor and adapt your security procedures to maintain proper protection.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
7 Cloud Security Lessons from the AWS Crypto Mining Campaign
Published: 03/09/2026
How Attackers Are Weaponizing AI to Create a New Generation of Ransomware
Published: 03/04/2026
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026


.png)

.jpeg)
.jpg)
