RECON (CVE-2020-6287) and its impact on Cloud Applications
Published 09/29/2020
By Shamun Mahmud, Sr. Research Analyst at Cloud Security Alliance
Key takeaways
- Cloud adoption is growing when it comes to ERP Applications
- ERP Applications in the cloud can be vulnerable security issues and organizations need to apply the proper security controls and patches.
Introduction
The RECON vulnerability (CVE-2020-6287), patched by SAP on July 13th, affects many SAP Solutions running on top of SAP Netweaver JAVA Application Server and was assigned a maximum CVSS score of 10.0. Based on that, one might wonder things like:
- What is the relevancy of this vulnerability when it comes to SAP Applications running in the cloud?
- Are these applications exposed in the same way?
- Should SAP customers take a different approach when it comes to the Cloud?
So we'll try to address some of these questions in this post.
Business Applications and the Cloud Security Alliance
In 2019, the CSA released the findings from the first research survey on “Enterprise Resource Planning (ERP) Applications and Cloud Adoption.” The study offers greater insight into cloud preparation and migration, the features and benefits gained, and the security and privacy challenges for ERP systems in a cloud environment.
According to the survey, 69 percent of organizations are migrating data from ERP applications to the cloud, moving to major cloud infrastructure-as-a-service providers, and the overwhelming majority, almost 90 percent, state that these applications are mission-critical.
“The cloud computing ecosystem is maturing rapidly and business-critical applications, such as ERP solutions, are being moved to cloud environments. With this shift, organizations are starting to explore the question of whether a cloud environment might alleviate traditional challenges that business-critical applications normally face”
- John Yeoh, Director of Research, Americas for the Cloud Security Alliance.
Among the survey’s other key findings:
- Americans (73%) and APAC (73%) were more likely to report that they were currently migrating business-critical applications to the cloud than those in EMEA, where regulations, such as the European Union General Data Protection Regulation (GDPR), impacted organizational plans for technology purchases, cloud services and third-party policies.
- On-premise models (61%) are employed most commonly, with cloud SaaS (41%), cloud IaaS (23%) and cloud PaaS (17%) following.
- Biggest concerns for migrations are around security and compliance.
By themselves, ERP applications utilize complex systems and, consequently, are challenging to secure. In the cloud, their complexity increases due to factors such as shared security models, varying cloud service models, and the intersection between IT and business controls. Nevertheless, due to cloud computing benefits, enterprise resource planning applications are increasingly migrating to the cloud.
Potentially vulnerable systems in the cloud
More and more, organizations are running business applications in the cloud in general and the component that is affected by the RECON vulnerability (CVE-2020-6287) in particular.
Using internet scan engines, it is possible to identify in a passive way SAP Applications that are internet-facing. This can be done by searching the HTML response, the HTTP headers and many other data points that can be helpful to identify if an IP address is actually serving an SAP Application. The number of SAP Applications that are JAVA based and internet-facing, according to these types of search engines is consistent with other data points, such as the previously mentioned CSA survey. Even though the numbers are not exactly the same (which is expected, as the sources of data are very different), the top 3 Cloud providers serving SAP Applications are.
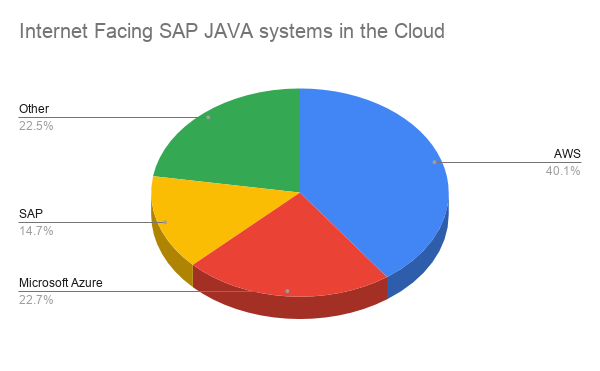
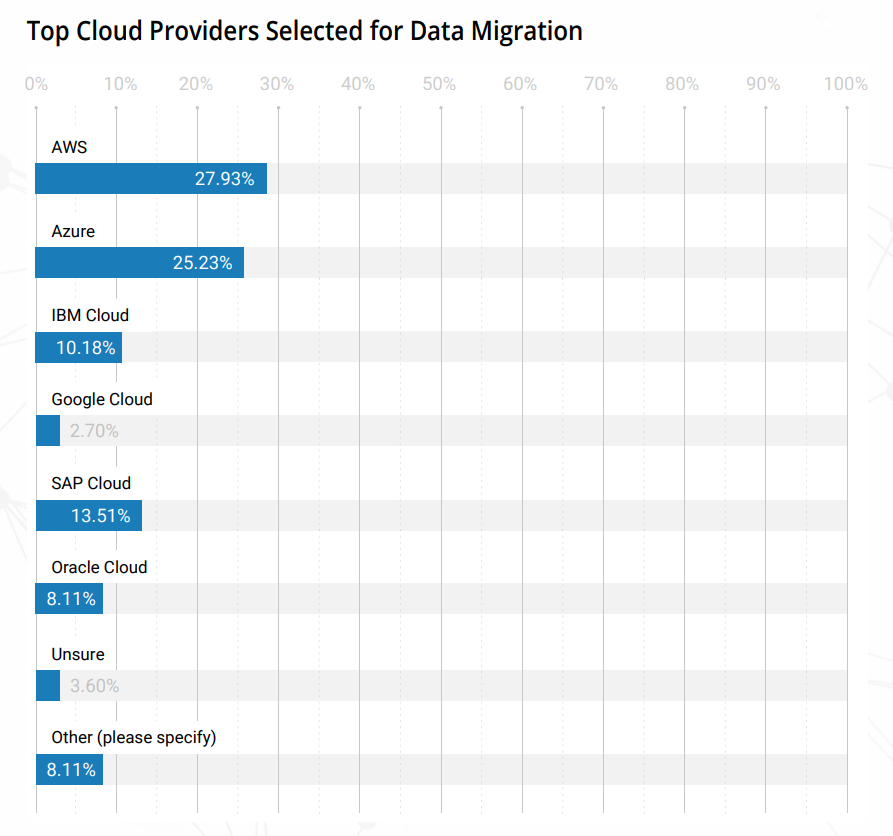
Image 2: Main providers of SAP Applications in the cloud by Internet search engines and by the CSA Survey “Impact of Cloud on ERP”
Addressing the questions
Now let's get back to addressing the initial questions that we laid out at the beginning of this post:
1. What is the relevancy of this vulnerability when it comes to SAP Applications running in the cloud?
As seen, SAP Applications are running in the cloud and more and more being transitioned to hybrid environments. Especially in Infrastructure as a Service models, organizations need to ensure the proper security processes are in place including patching, secure configuration and monitoring to begin with.
2. Are these applications exposed in the same way?
Yes, applications even running in the cloud can be exposed to software vulnerabilities as it is the case of the RECON vulnerability so it is up to organizations to ensure the right controls are in place around software vulnerabilities in general (not only RECON).
3. Should SAP customers take a different approach when it comes to the Cloud?
Applications running in the cloud are potentially even more exposed as these could be Internet facing and not going through all the processes that organizations already established for on-premise applications, therefore it is even more important to consider security for business applications running in the cloud.
The Role of the Cloud Security Alliance
Those are some of the reasons why we started theCSA Cloud ERP Working Group, to help organizations understand and manage the risk of running business applications in the cloud. We have released a set of assets that provide guidance around controls for business applications irrespectively of the cloud service model adopted. Feel free to join and help too!
References
[1] Enterprise Resource Planning and Cloud - CSA Survey
[2] CSA Cloud Enterprise Resource Planning Working Group
The RECON Vulnerability Content Series
Back in July, SAP issued patches for the RECON vulnerability that was identified and disclosed to SAP by the Onapsis Research Labs. Because of the severity and the amount of potential vulnerable Internet exposed SAP systems, the DHS-CISA along with many other global organizations issued CERT Alerts warning organizations of the criticality of the RECON vulnerability. Both SAP and Onapsis urged organizations using SAP Applications to apply the patches immediately. In the days following the release of the patches for RECON, the Onapsis Research Labs and other security/threat intelligence organizations and researchers witnessed and reported rapid threat activity including scanning for vulnerable systems and ultimately weaponized exploit code posted publicly. This content is part of coordinated effort with threat intelligence experts, researchers and organizations to provide further insight, intelligence and actions you should take to ensure your organization is protected from the RECON vulnerability. All the parts can be found here:
- Part 1: The Vulnerability @Onapsis Blog
- Part 2: The Mitigations @SAP Community Network
- Part 3: Relevance to the Cloud @Cloud Security Alliance
- Part 4: Threat Intelligence @DigitalShadows
- Part 5: Active Scanning @Stratosphere Labs
- Part 6: Tools Techniques and Procedures @BlueLiv
- Part 7: Active Exploitation @Onapsis Research Labs
- Part 8: Compliance @The Institute of Internal Auditors
- Part 9: Data Privacy @Radical Compliance
- Part 10: Programmatic Approach @Linkedin
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Why DNS TXT Records Deserve Governance in Security Programs
Published: 02/02/2026
Your Cloud May Be Secure, But Are Your Backups? Lessons From The EY Incident
Published: 01/12/2026
IaC Security in the Age of AI: New Threats, Smarter Solutions
Published: 01/05/2026




.jpeg)

.jpeg)