Cloud and Sovereignty: Are They Compatible?
Published 03/24/2022
 This blog was originally published by Atos here.
This blog was originally published by Atos here.
Written by Frederic Malicki, Pierre Brun-Murol, and Dominique Michiels.
In a period where moving to cloud and sovereignty are becoming central for many companies and institutions — especially in Europe — let’s take a moment to examine the apparent contradictions between these two concepts.
Does a migration to the cloud mean a loss of sovereignty?
First, it is important to remember that cloud environments bring multiple benefits: agility, elasticity, quick time to market, and off-the-shelf services and features. On the security side, these environments are very often secure by design, but all share the same shared responsibility model which makes the customer responsible for its own data protection. Cloud Service Providers (CSP) usually provide native data protection mechanisms, but the customer needs to assess the trustworthiness of these mechanisms in its unique business context, and leverage them appropriately.
Like any other technology, cloud environments can move the control plane outside the country and incorporate proprietary solutions that create a lock-in — in other words, there is a need to better assess the level of control through autonomy and reversibility. Those principles apply in particular to US hyperscalers. Cloud also implies a delegation of the management of the underlying technical infrastructure. As with any kind of delegation, this represents a new criteria to keep control over your data. However, this delegation of control is not an issue by itself if the customer’s choice is informed, especially considering:
- The sensitivity of exposed data and the associated risks
- Existing external controls that can mitigate these risks (see below)
- Existing elements of trust: data location, CSP nationality, local certification, etc.
How can you identify the required sovereignty level in cloud environments?
If the sovereign needs come from a legal obligation and a certification scheme aligns with this regulation, the answer is easy: Select a certified environment. In other cases, we recommend that customers adopt a risk-based approach and involve their internal risk owners — people who know exactly what threats must be addressed for the data to be migrated to cloud. Below, we have defined several steps you can take to meet your sovereignty needs while reducing the cost overhead and leveraging as much as possible the advantages of public cloud environments, if possible.
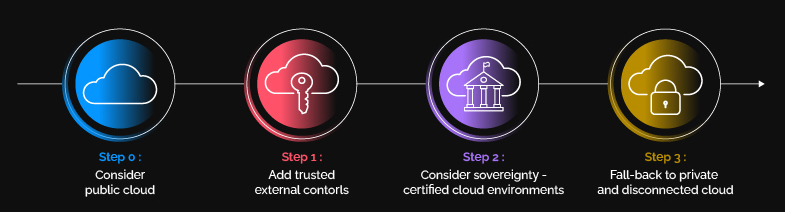
Step 0: Consider public cloud
If the CSP is not directly or indirectly involved in the identified risks, public cloud environments may very well fit your needs. Proper data protection mechanisms are still needed, but can be put in place by leveraging the CSP’s native security features.
Step 1: Add trusted external controls
If the CSP is directly or indirectly part of the identified threats, you can attempt to mitigate these risks by adding trusted external controls on top of public cloud environments. These external controls can be:
- A contractual agreement with the CSP
- A level of control over data encryption: Bring-Your-Own-Key, Hold-Your-Own-Key, external key management services, external hardware security modules, application-level encryption, etc.
- A level of control over identity and access management: automatic permission provisioning with recertification mechanisms, identity federation and authentication delegation, etc.
- A monitoring solution that can detect and respond to abnormal events that signal an identified threat
Of course, the trustworthiness of these external controls must be assessed and the residual risks accepted by the risk’s owners.
Step 2: Consider sovereignty-certified cloud environments
When external controls cannot reduce the identified risks enough, customers can consider cloud environments with a certification scheme that provides some sovereignty insurance (such as SecNumCloud in France, C5 in Germany, and the forthcoming EUCS at the EU level). In this case, customers need to verify that the certification scheme includes measures that mitigate the identified risks.
Of course, these certified cloud environments should also be considered when required by local regulations. Nevertheless, we recommend that customers formalize the risk coverage promised by the certification.
Step 3: Fall-back to private and disconnected cloud
If none of the previous steps sufficiently reduce the identified risks (for example for restricted data), customers should consider private cloud services that are disconnected from any non-trusted external management tools. These environments do provide some interesting sovereign aspects:
- It is often possible to dedicate a big part of the technical infrastructure including network access by customer
- The choice of location allows you to comply with legal and geographical requirements
- It is possible to enforce some constraints on operational teams, like nationality or clearance level requirements
However, they often still lack the wealth of advanced cloud services (serverless functions, PaaS services) that are the hallmark of public cloud (even if they are being developed).
What could make the selection of a cloud environment that meets sovereignty needs easier?
Admittedly, it’s difficult today for most cloud services customers to find the right balance between their sovereignty needs and their business priorities in terms of agility, IT cost reduction and quick time to market. We believe that initiatives like Gaia-X in Europe, which promotes standard descriptions of cloud services, security/sovereignty controls and cloud services interoperability, will change the situation and help customers navigate more easily between cloud services offerings.
Another challenge to overcome is that higher sovereignty often implies dedicated technologies with higher cost and less functional capabilities — thus limiting broader adoption. The situation is evolving day after day to maximize trusted solutions in public AND private cloud worlds, and that situation could be even more improved with the further development of compliant cloud offerings and by some promising technological innovations. For example, in coming years homomorphic encryption and trusted execution environments (TEE) may allow customers to process data in any environment with full control.
To conclude, we believe that cloud and sovereignty are indeed compatible, and that their association is a priority issue to guarantee the strategic autonomy of states, accelerate the digitalization of critical national industries which have been left behind, and enable companies to exchange and properly protect the data entrusted to them by customers.
The success of sovereign cloud offerings will depend on their ability to address security and compliance constraints while clearly stating the level of control they bring and providing fidelity as close as possible to public cloud platforms at an affordable price.
About the Authors
Frederic Malicki, Chief Technology Officer, Southern Europe, Atos
Frédéric Malicki is CTO for the Southern Europe RBU. He is responsible for bringing innovation and thought technology leadership in the region and supporting growth in our accounts. He has more than twenty years of experience in IT service delivery, solution architecture and consulting. Frédéric joined Atos in 2019 as CTO for IDM France. Prior to Atos, he worked for DXC Technology and HPE where he acted as a Client Executive, Account Delivery Executive, Solution Architect and SAP Consultant and worked for key accounts in France and EMEA. He is recognized as a dynamic team leader, able to rapidly adapt and comfortable with complexity. Frédéric holds an IT Master degree from the ISEN School of Engineering.
Pierre Brun-Murol, Cybersecurity Global Business Development, Atos Senior Expert
Pierre Brun-Murol is part of the Cyber Security Global Business Development team at Atos. He has always worked in the Cybersecurity domain and since he entered Atos in 2013, he contributed to various major cybersecurity projects and pre-sales in numerous cybersecurity areas of expertise: SIEM/SOC, Privileged Access Management, Cloud Security, etc. He was previously in charge of the portfolio for cybersecurity offerings in France. He is actively involved in innovative initiatives both internal and externals with global partners. He is also appointed an Atos Senior Expert in Cyber Security.
Pierre holds an Engineer degree from Supelec and a research-based master’s degree in applied sciences (Computer Engineering) from Polytechnique Montreal.
Dominique Michiels, Chief Service Delivery Officer, OVHcloud
Dominique Michiels is Chief Service Delivery Officer at OVHcloud, which involves running all services delivered to our customers. An IT enthusiast for 40 years, Dominique accumulated his considerable experience in IT production and development, performing diverse roles at Worldline (Atos subsidiary), such as the management of large cost centers & profit centers, including running large, complex international projects. In a multicultural landscape, he was also a key contributor to the various M&A and transformation program
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
The Great Divide: How AI Is Splitting the Cybersecurity Landscape
Published: 02/12/2026
Global Privacy Trends and Best Practices for Compliance in 2026
Published: 02/04/2026
The Agentic Trust Framework: Zero Trust Governance for AI Agents
Published: 02/02/2026





.jpeg)
.jpeg)