Definitive Guide to Hybrid Clouds, Chapter 3: Understanding Network Visibility in the Hybrid Cloud
Published 01/05/2023
Originally published by Gigamon.
Written by Stephen Goudreault, Gigamon.
Editor’s note: This post explores Chapter 3 of the “Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.” Read Chapter 1 and Chapter 2, and check back for future posts covering Chapters 4–7.
Migrating to the cloud can create tremendous opportunity, letting your organization operate more agilely, enable digital transformation, and accelerate growth — all while reducing complexity and cutting costs.
However, the shift to a hybrid cloud or multi-cloud environment does pose one significant hurdle: Network visibility is significantly reduced, and that makes operational and security monitoring difficult.
What’s Behind the Cloud Visibility Gap?
The network traffic monitoring and visibility tools designed for on-prem datacenters aren’t built for the cloud and often need to be refactored, even as security teams have tried — often in vain — to adapt them for cloud-based infrastructure.
Securing hybrid cloud and multi-cloud environments has been hard to achieve, largely due to the operational headaches that occur when installing agents, enabling network traffic inspection and monitoring, and configuring centralized tools that enable stakeholders to keep track of it all.
Additionally, the move to cloud security operations has been hindered because:
- Many cloud providers don’t have mature services available to access and collect network traffic
- Switching (Layer 2) is no longer available and has been abstracted away by public cloud tenants, so all access control and segmentation are applied via policies that usually only focus on Layers 3 and 4 (IP addresses and ports), as well as tags or object references
- Cloud-native tooling for network traffic flows is rarely designed with optimal performance and tracking in mind
So, How Can You Achieve Network Visibility in the Cloud?
Achieving network visibility in the cloud requires a different set of tools than is natively available in the cloud. Here is a quick look at how you can create a comprehensive cloud network visibility program:
- Assess your current network monitoring tools and capabilities to figure out what you have and where you are lacking
- Choose solutions that span both on-premises and cloud environments — but offer centralized management
- Link together virtual private clouds (VPCs) and network subnets to create the appropriate network scale and architecture
- Collect network flow data for monitoring communication to, from, and between workloads within network segments and subnets
- Use network access controls like security groups to their fullest extent, with logging of all events related to enabled rules for workloads and subnets
- Enable packet capture and send the packets to a centralized network visibility and analytics fabric before being selectively forwarded to monitoring and security tools
- Capture and process network traffic and information with a network visibility and analytics fabric
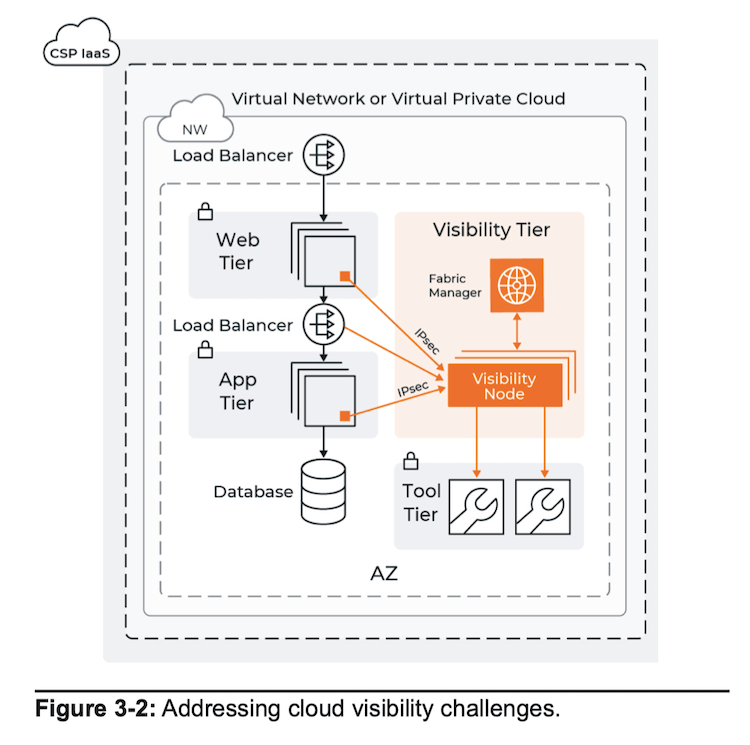
Those are just the highlights. For more in-depth analysis of achieving visibility in the cloud, read Chapter 3 of the “Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.”
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Cloud 2026: The Shift to AI Driven, Sovereign and Hyperconnected Digital Ecosystems
Published: 01/15/2026
Identity Security: Cloud’s Weakest Link in 2025
Published: 09/19/2025


.png)

.jpeg)
.jpeg)
.jpeg)