Behind the Breach: Phishing & Token Compromise in SaaS Environments
Published 07/17/2023
Originally published by Obsidian.
Earlier this year, Gartner published a new research report focused on the human component of cybersecurity which explored trends around cybersecurity leadership, challenges with hiring, and attacks targeting individuals. One notable prediction—that by 2025, lack of talent or human failure will be responsible for over half of significant cyber incidents—resonated particularly with our threat team because of a recent security incident we observed firsthand.
When a client in the technology sector approached Obsidian regarding a security assessment, a successful SaaS account takeover attempt was uncovered in their environment. In this case, a victim user had fallen for an email phishing campaign and failed to take corrective action even after recognizing what had happened.
Below, we’ll review the timeline of events related to this incident, share key takeaways and practical guidance, and reflect on Gartner’s prediction about human responsibility in cybersecurity.
What happened?
The incident began with a targeted user falling for a phishing email that used the guise of enrollment in company benefits. The email was sent from a seemingly legitimate external domain, included a mention of the target’s full name, and stated a clear end date for enrollment, providing a sense of legitimacy and urgency. The user signed in and used SMS for their multi-factor authentication.
At the same time, the victim credentials and MFA code were intercepted and reused by the attacker via an AWS IP address originating in an entirely different state.
Only a few minutes later, the victim user seemed to recognize what had occurred and responded by reporting and deleting the phishing email. This prompted a second round of security scanning, and yet, it wasn’t caught by Defender for Office 365. The user also failed to take any further corrective action by resetting their password or existing sessions, allowing the attacker to maintain access.
The adversary was observed digging into the victim account from a different AWS data center and tapping into prior exchanged and intercepted session tokens. When our team began investigation, it was clear that there were several parallel sessions between the victim user and attacker during this period.
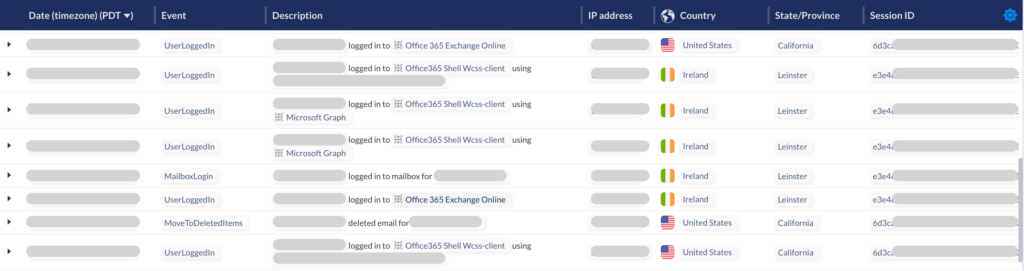
After connecting to the client environment, two especially significant threat events were detected:
- Session Token Reuse: This confirmed the interception and reuse of a victim’s SaaS session token, a technique which can be otherwise discreet and very difficult to detect without the right tooling.
- Suspicious MFA Enrollment: To ensure their own persistence in a target environment, bad actors will often attempt to enroll new MFA devices that they control. Obsidian identified this technique when the attacker added a new mobile second factor.
The email was submitted for rescanning one final time, this time by a systems administrator. Once again, the email came back marked as safe. Because the systems administrator is not a security analyst, they are not obligated to conduct security checks on the victim user—nor were they even able to because of insufficient visibility into the SaaS environment. As a result, incident remediation did not occur until later security team engagement.
What are the takeaways, and what can I do to remain secure?
While it is an excellent firsthand example of several adversarial techniques used against SaaS environments and security measures like MFA, this incident is far from unique or isolated. To that end, there are three key takeaways and security recommendations we can provide:
- Social engineering techniques such as phishing remain effective against human targets. Even with a robust security education program, it’s important to account for and expect human vulnerability. Use stronger MFA methods such as WebAuthN whenever possible.
- Initial lines of defense are not bulletproof. This organization did plenty correctly with their implementation of MFA and their use of email scanning. Still, both of these typically effective measures failed against the attack in question.
- Threat detection capabilities are critical. Because this attacker was able to penetrate several security measures and implement persistence measures, their access to the SaaS environment was durable and discreet. In this case, threat detection helped account for the victim’s false sense of security as they reported the email but did not update their credentials. Equip your security teams with threat detection and response tools purpose built to address these situations.
In the wake of this incident, Gartner’s assessment of human vulnerability in cybersecurity holds true.
“Gartner predicts that by 2025, lack of talent or human failure will be responsible for over half of significant cyber incidents. The number of cyber and social engineering attacks against people is spiking as threat actors increasingly see humans as the most vulnerable point of exploitation.”
As your organization continues to invest in security education and protective solutions, pay some mind to the tools and strategies you have in place to rapidly address incidents where these measures fail. Account for the realities of social engineering and insider risk as you plan out the future of your organizational security.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026
AI Security: When Authorization Outlives Intent
Published: 02/25/2026





.png)
.jpeg)


