Definitive Guide to Hybrid Clouds, Chapter 1: Navigating the Hybrid Cloud Journey
Published 11/04/2022
Originally published by Gigamon.
Written by Stephen Goudreault, Gigamon.
This post explores Chapter 1 of the Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.
Many organizations are deploying assets to the cloud, which is often the start of their cloud migration journey. But there are both obvious and subtle differences in how these applications, security controls, and services work in the cloud.
The physical, data link layer and about half of the network layer have been abstracted away from users. Those services are managed by the cloud service provider. This could mean that many long-relied-upon tools and third-party solutions may not work well or at all in public clouds.
What Are Hybrid Clouds?
Let’s take a moment to define hybrid cloud. This is when some of your assets are maintained on premises or internally while others are run in public cloud environments. Outside of green field deployments, this is a very common scenario, as it may not be feasible or desirable to shift everything to the cloud. In this context, we could also consider the public cloud as software-defined datacenters (SDDCs).
Most organizations struggle to adapt internal security controls to cloud environments. These security controls could rely on a service that has been abstracted away or that solves for something that is not a problem in the cloud. I would say that almost all security processes and workflows built around traditional on-premises tools and controls will need to be refactored into the public cloud. While the problems these tools solve for may be the same or similar as on prem, how you go about it in the cloud could be very different.
Migrating on-premises infrastructure into the cloud always comes with challenges. Solutions may lack feature parity in cloud versions or have features that don’t translate into the cloud. You may face performance and cost issues for services that make sense on prem but do not fare well as forklifted monolithic solutions in the cloud. There can also be lack of compatibility with certain cloud providers’ automation, orchestration, and deployment architectures.
Data in the Cloud: It’s Your Responsibility to Secure It
Additionally, there may be some confusion about the shared responsibility model. Some security responsibility is assumed by the cloud provider, while other security controls and capabilities are managed by customers. If you put data into the cloud, it is your responsibility to secure it. That means restricting access and ensuring there are no default credentials or overly broad permissions set. The cloud provider secures the underlying infrastructure on which your data lives. There are minor variations, but don’t assume you can upload anything with blank or no credentials and expect it to be secure.
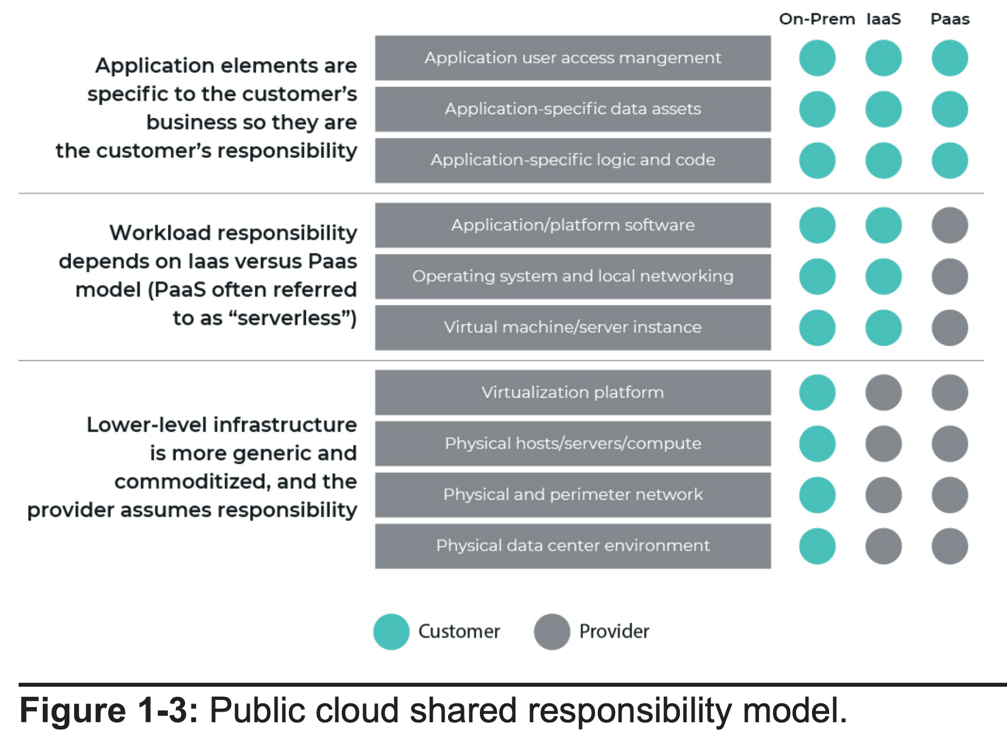
In public clouds, customers are responsible for the security of most assets and workloads as well as cloud services. Network and identity security are also the responsibility of the customer. While cloud providers maintain the infrastructure that facilitates an SDDC, any other infrastructure is entirely under the control of the customer. This fact should drive all security control and process requirements in the IaaS cloud.
The Trouble with Cloud Providers’ Security Tools
Cloud providers’ security offerings may be easy to implement and affordable, but they usually don’t have extensive capabilities available in mature third-party solutions. Cloud providers’ security tools and services often provide basic, foundational functionality that may be adequate for smaller organizations.
Larger organizations and those with more extensive compliance and security requirements, however, may find them less flexible and less compatible with existing tools and processes. Additionally, each cloud provider has its own flavor of tools, and managing them in a multi-cloud environment can become challenging. Public cloud providers offer some security benefits, mainly in the areas of resilience and physical security, but leave the vast majority of security controls and management to customers.
More Avenues for Attack
While cloud services offer many advantages, there are significant risks both cloud providers and customers need to address. Attackers target the hybrid cloud because it opens up an entirely new attack surface. Configuration errors, customer unfamiliarity with the cloud, and lack of governance are giving attackers more targets in cloud environments than ever.
The cloud has allowed for a new class of operators who may not be familiar with best practices or are not skilled at properly securing their cloud deployments. Early in our cloud journeys, everyone I know personally, as well as myself, was compromised in four hours or less due to mistakes that were not a big deal on prem but had huge consequences in the cloud.
How They Attack Cloud-Based Assets
Many types of attacks are used against cloud-based assets, and some can be exploited for use in ransomware attacks:
- Attacks against cloud admins and users (account hijacking)
- Hijacking resources to run crypto mining servers, leaving cloud customers with the compute charges
- Discovery and theft of exposed cloud storage assets
- Exploitation of vulnerable cloud applications with zero-day attacks against the common OWASP Top 10
- Vulnerabilities that some cloud-native web application firewalls don’t catch
- Exploitation of exposed cloud-provider APIs
- Compromise of misconfigured cloud control plane services (this happens more than you think)
The cloud provider environment itself is a complex software platform with many different settings and options that can be misconfigured. For example, failing to enable multifactor authentication for administrative portal access could lead to brute force attacks against accounts. Exposed provider APIs may afford attackers a foothold to enumerate cloud assets or even gain remote access to cloud environments.
The Hybrid-Cloud Approach
In hybrid cloud networks, network engineering and security architecture teams need to look at new controls and new methods for developing and implementing network security practices in their environments. Organizations should implement a layered defense model that includes cloud-native network access controls for workloads, network traffic capture and security monitoring capabilities, and third-party platforms and services that can help augment and centralize network security functions.
Be warned, however — many cornerstone security tools need to be carefully evaluated to see if they create more problems in the cloud than solve. Trying to leverage monolithic virtualized legacy on-prem security controls in the cloud is a sure way for cloud teams to attempt to bypass network teams moving forward.
Learn More in Chapter 1
For more detail, read Chapter 1 in the Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud. There you’ll find information about:
- Shifting from on-premises to cloud-based infrastructure
- Understanding the shared responsibility model
- Evaluating top risks in the hybrid cloud
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Agentic AI and the New Reality of Financial Security
Published: 02/26/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026
What Actually Makes an Agentic AI Solution Scalable?
Published: 01/20/2026


.png)
.jpg)

.jpeg)
