Definitive Guide to Hybrid Clouds, Chapter 6: Examining Network Visibility, Analytics, and Security Use Cases
Published 04/06/2023
Originally published by Gigamon.
Written by Stephen Goudreault.
Editor’s note: This post explores Chapter 6 of the “Definitive Guide™ to Network Visibility and Analytics in the Hybrid Cloud.” Read Chapter 1, Chapter 2, Chapter 3, Chapter 5, and check back for a future post covering Chapter 7.
Your hybrid cloud environment is growing so fast that your network and security teams could be struggling to monitor and defend this ever-increasing attack surface.
Teams simply don’t have the capability to see all traffic — and catch the threats before damage is done. Investments in advanced monitoring and detection tools can help, but ONLY if they provide all the security without disrupting the business.
Benefits of a Cloud Visibility and Analytics Fabric
The right network visibility tool shouldn’t cause latency or complicate businesses workflows. In fact, a cloud visibility and analytics fabric (VAF) can actually reduce complexity, decrease time-consuming tasks, like troubleshooting, and eliminate tool sprawl, all while helping you protect your network and reduce operational overhead.
A VAF is the visibility layer between your network infrastructure and network monitoring and security tools. It helps ensure each tool receives all the relevant traffic it was designed for (but nothing else), acting as a comprehensive next-generation network packet brokering platform.
A VAF will:
- Flag suspected data exfiltration based on type and quantity of data flows, DNS records, and lookups associated with suspicious activity
- Check SSL/TLS certificate use and expose nefarious communications hidden within encrypted flows
- Identify suspicious and unauthorized external remote connections
- Find and eliminate rogue apps and shadow IT operations
- Obfuscate internal compute source IDs, account numbers, birth dates, credit card numbers, and personally identifiable information (PII)
- Detect rogue DNS and DHCP servers
- Collect key metrics that help your security team improve network events and activities
Ultimately, a VAF can help security teams uncover network blind spots and malicious traffic patterns, and eliminate the need for extended, futile investigations by pinpointing unusual traffic in busy networks and highlighting events and flows of interest quickly.
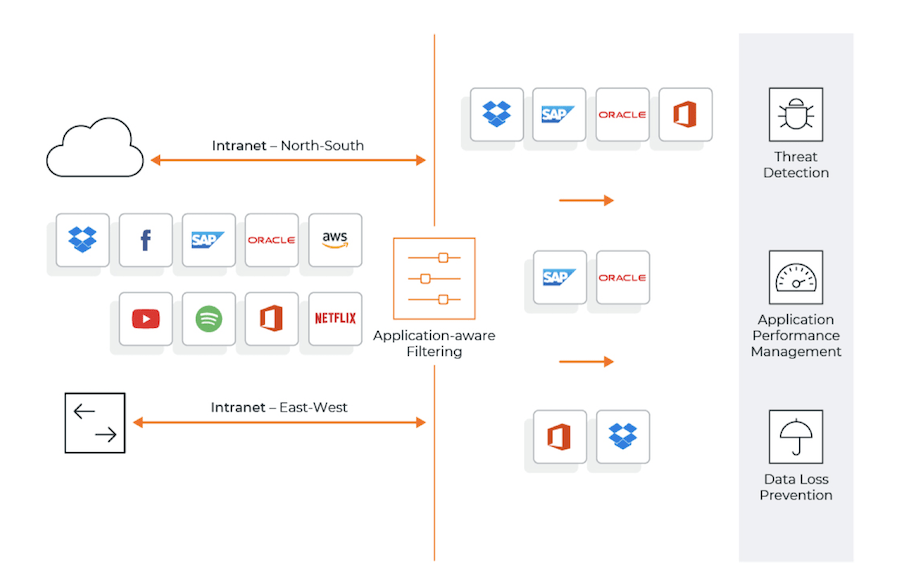
Figure 1: Extracting application flows of interest.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Cloud 2026: The Shift to AI Driven, Sovereign and Hyperconnected Digital Ecosystems
Published: 01/15/2026
Identity Security: Cloud’s Weakest Link in 2025
Published: 09/19/2025





.png)

.jpeg)
.jpeg)
.jpeg)