IBM Cost of a Data Breach 2022 – Highlights for Cloud Security Professionals
Published 12/02/2022
Originally published by Ermetic.
Security professionals are constantly inundated with warnings about the potentially colossal impact of security threats and risks to their organization. But what is colossal in real currency? By understanding how much the cost of a data breach can impact one's organizational budget, it's easier -- and more productive -- to engage in conversations about the impact of breaches and actions to take to avoid them. It will also help security teams show they are a business enabler and how implementing security controls can save money that can be applied to the business productively.
The comprehensive IBM Cost of a Data Breach Report provides data breach cost information and analyzes the business price across breach types, security technologies and industries. Conducted by Ponemon Institute, the report was sponsored by IBM Security, which analyzed and published the results. The 2022 report, IBM's 17th annual, is based on 3600 interviews of 550 organizations, across 17 countries and regions, and in 17 industries, that were impacted by data breaches between March 2021 to March 2022.
This post looks at the report’s key findings as related to cloud security – and their relevance in planning security for your own cloud environment.
Key Findings
Recurring Breaches Afflict the Vast Majority of Breached Organizations
The researchers studied 550 organizations that suffered from a data breach. A stunning 83% of organizations in the study reported having incurred more than one data breach; 17% of organizations were impacted by “just” one.
This means that data breaches are an ongoing problem for just about every organization. Having a breach, unlike vaccinations, gives no immunity from being breached again – unless, as explained below, you set up the proper security controls.
More Data Points on Data Breaches
45% of Breaches Were Cloud-Based
Nearly half of all breaches occurred in the cloud – and those that occurred in the public cloud were costlier. While hybrid cloud environment breaches cost an average of $3.8M, the average cost in private clouds was $4.24M and in public clouds it was $5.02M!
The Crazy Cost of a Data Breach
A data breach is an expensive matter. Per IBM, the average costs of breaches by type are:
- $4.35M - The average total cost of a data breach
- $4.82M - The average cost of a critical infrastructure data breach. Critical infrastructure includes financial services, industrial technology, energy, transportation, communication, healthcare, education and public sector industries
- $5.57M - The average cost of a breach for organizations with high levels of compliance failures
By detecting and mitigating data breaches and compliance gaps in advance, organizations can pre-empt the damage they will potentially cost. Imagine how many activities you could run or how many people you could hire with those budgets.
Ransomware Costs Organizations Much More Than “Just” the Ransom Payment
IBM found that the frequency of ransomware increased this year by 41%, from 7.8% in 2021 to 11% in 2022. The good news is that the average cost of ransomware went down slightly – from $4.62M in 2021 to $4.54M in 2022. The bad news, of course, is that ransomware costs are still so high and don’t include the cost of the ransom payment itself. Ransomware costs are also costlier than the general average costs of data breaches, evaluated at $4.35M.
And the Top Attack Vector Is… Credentials
Stolen or compromised credentials were the number one attack vector in the past two years. Compromised credentials were responsible for nearly one-fifth of all attacks in 2022. The average cost of credential related breaches was $4.5M. Notably, their lifecycle was also the longest, taking 243 days (!) to identify and 84 days to contain.
After credential-related attacks, the runner up for the most common breach cause was phishing, causing 16% of attacks. It was also the costliest of attack vectors, averaging $4.91M.
59% of Organizations Don’t Deploy Zero Trust
Zero trust, the modern security model established on the principles of identity-based security and least privilege access, has gained momentum across organizations. Yet, 59% of organizations have not yet deployed a zero trust strategy. In critical infrastructure industries, the percentage of organizations that have not yet deployed zero trust spikes to 79%.
Stalling the deployment process isn’t a cost-effective move. According to IBM, organizations that don’t deploy zero trust can expect to pay an average of $1M more than organizations that do. The right tools can assist organizations to quickly and effectively implement zero trust and the principle of least privilege.
Your Business Partners Might Be Putting You at Risk
IBM found that 19% of breaches occurred because a business partner was compromised. A business partner may be a supplier, a vendor or any other entity in the supply chain. The average cost of such a business partner related breach was $4.46M and the lifecycle was long - 235 days for identification and 68 days for containment.
Global Highlights
Data Breach Costs Are Rising Year Over Year
IBM found that the global average cost of a data breach in 2022 was the highest ever since the dawn of conducting these reports. The cost of a data breach in 2022 was $4.35M – a 12.7% increase compared to 2020, when the cost was $3.86M.

Average cost of a data breach in recent years, Cost of a Data Breach Report 2022, IBM Security
How a Cloud Security Strategy Can Lower Data Breach Costs
An IT/security strategy that prioritizes cloud infrastructure security can help reduce data breach costs. By investing in the right cloud security solution and prioritizing certain strategic actions, risks will be mitigated, the cloud attack surface and blast radius reduced and costs lowered, directly impacting your bottom line.
Which industry saw the highest increase in cost of breach?
For the 12th year in a row, healthcare is the industry seeing the highest breach related costs. Healthcare is one of the most highly-regulated industries and considered critical infrastructure by the US government.
The average cost of a healthcare breach in 2022 was $10.1M, a 9.4% increase compared to 2021, when the average cost was $9.23M. This cost is also approximately two to five times higher than the cost in other industries.
The financial industry cost also increased in 2022 compared to 2021. A 4.4% increase brought the total average cost to $5.97M, compared to $5.72M in 2021.
In 2022, the top five costly industries were healthcare, financial, pharmaceuticals, technology and energy, the same top five as in 2021. The industrial industry, comprised of chemical, engineering and manufacturing organizations, and seventh in the list of data breach costs, saw a 5.4% cost increase compared to 2021, bringing the cost of a breach for that industry up to an average of $4.47M.

Average cost of a data breach by industry, Cost of a Data Breach Report 2022, IBM Security
It’s also interesting to note that, according to IBM, high data protection regulatory environments, like healthcare, financial, energy, pharmaceuticals and education industries, “tended to see costs accrue in later years following the breach.”
How a Cloud Security Solution Can Help Secure Cloud Environments
If you work as a security professional in an industry that is prone to costly attacks, taking extra measures to secure your cloud environment can help reduce the risk of attacks and their costs. This is especially important in industries that provide public services, where costs are deemed a public matter, or in industries sensitive to price volatility, since these costs are harder to predict.
By shifting the security mindset and adopting modern cloud security principles like the principle of least privilege permissions, Just in Time access for developers, automated risk assessment and auto-remediation of risky entitlements and faulty configurations across multi-cloud environments, such industries can securely transition to the public cloud and secure their assets. A cloud security solution can help automatically implement and enforce these security and compliance best practices.
Data Breach Lifecycle
The definition of a data breach lifecycle, as per the IBM report, is “the time elapsed between the first detection of the breach and its containment.” These metrics, says IBM, “can be used to determine the effectiveness of an organization’s incident response and containment processes.”
IBM found that it takes an average of 277 days (more than three quarters of a year) to identify and contain a data breach. This is a slight improvement over 2021, when the lifecycle took 287 days.
The life cycle was divided as follows:
| Breach Identification (days) | Breach Containment (days) | |
| 2022 | 207 | 70 |
| 2021 | 212 | 74 |
See the complete year to year mapping of data breach lifecycle days here:
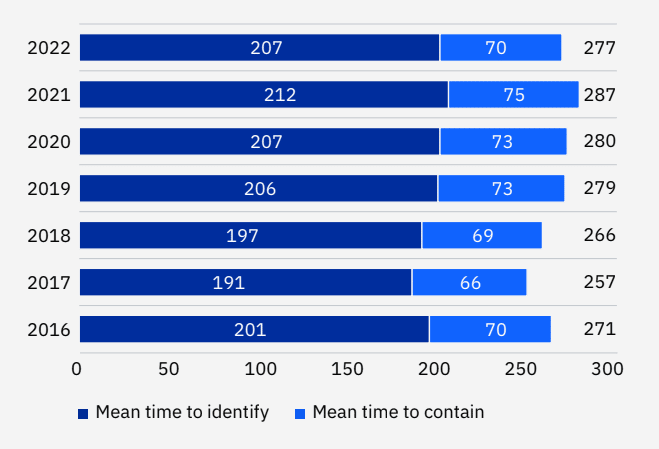
Average time to identify and contain a data breach, Cost of a Data Breach Report 2022, IBM Security
Why does data breach lifecycle matter? Shorter data breaches are associated with lower data breach costs: when comparing data breach lifecycles of more than 200 days with those of less than 200 days, the difference in costs was considerable: 26.5%. The longer data breach lifecycles incurred costs of $4.86M compared to $3.74M, the average costs of shorter life cycles.
How a Cloud Security Solution Can Shorten the Data Breach Lifecycle
Continuous monitoring of cloud environments to identify and mitigate risks and anomalies will cut down identification and containment times (and consequently data breach costs). How does this work? A cloud security solution implements cutting-edge cloud security principles like least-privilege and JIT access through organizational workflows. When identified, vulnerabilities like toxic permissions combinations or misconfigurations are automatically remediated to prevent breaches. If a breach does occur, visibility and analytics enable quicker identification and investigation to resolve issues faster.
Initial Attack Vectors - Stolen Credentials and More
As mentioned in the Key Findings section, stolen or compromised credentials was the most common initial attack vector in 2022, responsible for 19% of the breaches and had an average cost of $4.5M.
Following credentials, the next most common initial attack vectors were:
Second place: Phishing - 16% of breaches, $4.91M average costs
Third place: Cloud misconfigurations - 15% of breaches, $4.14M average costs
Fourth place: Third-party software vulnerability - 13% of breaches, $4.55M average costs
Interestingly, these top four initial attack vectors were also the top four in 2021. In addition, IBM found that more than 10% of attacks were caused by malicious insiders, at an average cost of $4.18M, and that the average cost of a social engineering breach was $4.1M.
See the complete initial attack vector map in the IBM report here:

Average cost and frequency of data breaches per initial attack vector, Cost of a Data Breach Report 2022, IBM Security
When it comes to the lifecycle of these initial attack vectors, stolen or compromised credentials also come up first. It took a mean time of 327 days to identify and contain a credentials-related breach – almost an entire year. It’s also 16.6% longer than the lifecycle mean time of data breaches overall.
By way of comparison, the phishing identification and containment lifecycle was 295 days, for third-party software vulnerabilities and malicious insiders it was 284 each, for social engineering it was 270 days and for cloud misconfigurations it was 244 days.

Average data breach lifecycle per attack vector, Cost of a Data Breach Report 2022, IBM Security
Per IBM, in most cases, the attack vectors with longer mean times to identify and contain were also among the most expensive types of breaches.
How a Cloud Security Solution Can Help Prevent Credentials Compromise, Misconfigurations and More
Cloud environments introduce thousands of new identities that need to be managed to ensure secure access. A cloud security solution provides visibility into these identities, including for third parties, and their permissions. It then auto-remediates vulnerabilities and misconfigurations to reduce the risk of exploitations that could result in data breaches by external actors or malicious insiders. To combat phishing, cloud security solutions can minimize the use of stolen credentials, identify anomalous behavior and prevent malware injections.
Key Cost Factors and Their Influence
To determine the cost of a data breach, IBM analyzed 28 factors divided into two types: factors that amplify the cost and factors that have a mitigating influence.
These are the 28 factors that IBM analyzed:

Key factors impacting data breach costs, Cost of a Data Breach Report 2022, IBM Security
Let’s look into a few of these factors to understand better how they might impact the total cost of a data breach:
Factors that help mitigate the costs of a data breach:
AI platform - Automation at high-scale enables performing capabilities that humans cannot perform themselves or it would be very difficult for them to do, especially at scale and for a long time. For example, managing permissions across cloud environments is very difficult, ineffective and, some would say, impossible to track manually.
DevSecOps approach - Shift left security practices and implementing security requirements in the engineering process, instead of afterwards, ensures code is delivered securely without impacting developer velocity.
Employee training - Employee awareness helps reduce vulnerabilities that arise from exploitations like social engineering. In addition, training on security tools helps stakeholders use such tools to their full extent and maximize their capabilities. This makes it all the more important to choose a tool that is user-friendly.
IAM - Centralized access management based on authentication and digital identities helps prevent breaches.
MFA - Multi-factor authentication supports identity-based access management. It is important to implement an identity-based approach that can monitor when MFA is missing.
Factors that amplify the costs of a data breach:
Security skills shortage - Inability to recruit and retain cloud security talent can result in oversights that cause misconfigurations or the inability to implement the most advanced and secure practices. An automated and easy to use cloud security solution can help overcome these gaps by providing capabilities that can be used by stakeholders of different levels of technological and business acumen.
Compliance failures - Compliance regulations are designed to ensure the security, protection and privacy of critical applications and data. Inability to comply means there are security gaps that can be maliciously or accidentally abused. A security solution that integrates compliance and security capabilities and monitors compliance to detect attack vectors in cloud configuration improves security posture while controlling access-related risk.
Third-party involvement - Third parties introduce new types of vulnerabilities because their practices and technologies don’t necessarily adhere to your security standards. A security solution that helps identify and mitigate third party risks enables continuous business collaboration, without the risk.
Cloud migration - Cloudification is essential for business agility, scalability and expansion. The new vulnerabilities introduced by the cloud shouldn’t impede digital transformation. Instead, choose a cloud security solution that can help mitigate them.
Security system complexity - Security tools promise endless security capabilities that often sound too good to be true. But if a system is too complex to operate, even the promise of the stars and the moon is meaningless. It’s important to find a tool that not only promises security but also seamlessly becomes part of the development lifecycle and supports security assessment in staging and production environments.
The impact of these features on data breach costs was exceptional:
- The difference between high and low levels of security system complexity was $2.47M, or 58%
- The difference between high and low levels of cloud migration was $2.27M, or 50.5%
- The difference between high and low levels of compliance failures was $2.26M, or 50.9%. Compared to the average cost of a data breach, organizations with a high level of cloud migration had an average cost that was $1.28M higher, a difference of 25.7%.
- On the other hand, when implementing high levels of DevSecOps, the cost of a breach was $1.17M lower, which is 26.7%.

Average cost of a data breach per amplifying factor, Cost of a Data Breach Report 2022, IBM Security

Average cost of a data breach per mitigating factor, Cost of a Data Breach Report 2022, IBM Security
Security Automation for 65.2% Lower Data Breach Costs
According to IBM, security automation (and AI) “involves enabling security technologies that augment or replace human intervention in the identification and containment of incidents and intrusion attempts. Such technologies depend upon AI, machine learning, analytics and automated security orchestration. On the opposite end of the spectrum are processes driven by manual inputs, often across dozens of tools and complex, nonintegrated systems, without data shared between them.”
Security automation helps significantly reduce the cost of breaches. IBM found that the average cost of breaches when security AI and automation are fully deployed was, on average, $3.05M lower than organizations with no security automation and AI. This is a difference of 65.2% and the largest savings IBM found in their study.

Average cost of a data breach by automation deployment model, Cost of a Data Breach Report 2022, IBM Security
The even better news is that organizations increased their adoption of security automation and AI in 2022. Full deployment increased from 21% to 31% between 2020 and 2022. On the opposite end, the percentage of organizations with no automation or AI security decreased from 41% in 2020 to less than a third, 30%, in 2022.

Security automation deployment levels, Cost of a Data Breach Report 2022, IBM Security
Security automation enabled organizations to detect and contain breaches much more quickly than those with no automation or AI deployed. While fully deployed security automation and AI resulted in an average of 249 days for identification and containment, automation and AI deployed only partially resulted in an extra 50 days - totaling a mean time of 299 days to identify and deploy. With no automation, the lifecycle was 323 days long, a hefty 74 days (approximately 2.5 months) longer than those with fully deployed automation.

Average data breach lifecycle per automation deployment level, Cost of a Data Breach Report 2022, IBM Security
How a Cloud Security Solution Can Help Automate Security
Security automation reduces the costs associated with data breaches. Automation reduces the risks of human error, enables continuous monitoring and automated risk mitigation and helps pre-empt attacks by recognizing anomalous patterns of activity.
In addition, automation provides capabilities that would be very difficult for humans to perform, like managing and analyzing large amounts of data, e.g in the case of entitlements management. Therefore, it behooves every organization to build automation into their cloud security strategy. When choosing a cloud security vendor, be sure to ask about automation capabilities.
Zero Trust
Zero trust has become a central practice in identity-based security (and some might even venture to say it is the linchpin of modern security). Per IBM, “the zero trust approach operates on the assumption that user identities or the network itself may already be compromised, and instead relies on AI and analytics to continuously validate connections between users, data and resources.”
Unsurprisingly, zero trust has positively impacted the average costs of data breaches. Organizations that deployed zero trust saved $1M in average breach costs, lowering their costs from an average of $5.1M to $4.15M, compared to those that didn’t. That is a 20.5% savings!
Unfortunately, though, 59% of organizations have not yet deployed zero trust. As we have seen, this has an immediate impact on the average costs of data breaches.

The impact of zero trust on the average cost of a data breach, Cost of a Data Breach Report 2022, IBM Security
How a Cloud Security Solution Can Help Implement Zero Trust Principles
Implementing zero trust principles, such as least privilege access, JIT access and visibility into resources and assets, reduces the costs of data breaches (and the chances of breaches occurring). However, when resources are cloud-based, this is not always easy to do.
An identity-based cloud security solution provides solutions for asset inventory, entitlements management, infrastructure visibility, anomaly detection, compliance and risk remediation, while shifting left on these capabilities into CI/CD pipelines. This drives cross-organizational and automated implementation of zero trust practices.
Ransomware
While the average cost of ransomware breaches has slightly decreased - from $4.62M to $4.54M, the frequency of such attacks has actually increased: 11% of breaches in 2022 were ransomware, compared to 7.8% in 2021.
It’s important to note that these are the costs incurred by the organization on top of the ransom itself. This means that no matter if the ransom cost is or isn’t paid to the ransomware gang, the organization is probably spending millions of dollars on average for all other aspects of the attack.
In addition, ransomware attacks were on average more costly than other data breaches - $4.54M for ransomware compared to the $4.35M average for data breaches overall. A destructive or wiper attack cost, on average, was $5.12M, which is $0.77M more than the overall data breach average.

Should organizations pay ransoms? There are many factors that influence the answer, and it is a question each organization should answer for itself. In terms of data breach costs, though, organizations that did not pay the ransom incurred average costs of $5.12M, compared to $4.49M of those that did. This is a $0.63M average difference - 13.1%.
 Average cost of a ransomware data breach: paid vs. non-paid ransom, Cost of a Data Breach Report 2022, IBM Security
Average cost of a ransomware data breach: paid vs. non-paid ransom, Cost of a Data Breach Report 2022, IBM Security
Ransomware attacks also resulted in longer detection and containment lifecycle. It took 326 days to identify and contain one and 324 days to identify and contain a destructive attack, while the overall global average was 277 days. The ransomware lifecycle took 49 days longer than the global average.
 Average ransomware data breach life cycle time, Cost of a Data Breach Report 2022, IBM Security
Average ransomware data breach life cycle time, Cost of a Data Breach Report 2022, IBM Security
How a Cloud Security Solution Can Help Prevent Ransomware
Research conducted by Ermetic has found that organization environments have high potential for ransomware, due to misconfigured identities, publicly exposed machines, risky third-party identities and risky access keys. This means that ransomware could be lingering within the cloud environment long before it is activated or that the environment is at risk for ransomware even if ransomware hasn’t been triggered yet.
A cloud security solution can help detect risks that could lead to ransomware attacks early and often to prevent attacks, minimize blast radius or shorten ransomware life cycles.
Supply Chain Attacks
Supply chain compromises are, as IBM put it, breaches “resulting from a compromise of a business partner such as a supplier.”
According to the IBM study, supply chain attacks were prevalent - comprising 19% of attacks. Costs were higher than the overall average, with an average of $4.46M compared to $4.35M - a 2.5% difference. In addition, the identification and containment lifecycle was 303 days, which is 26 days longer than the overall average of 277 days.
How a Cloud Security Solution Can Help Prevent Supply Chain Attacks
A cloud security solution helps reduce vulnerabilities triggered by external partners, vendors and supply chains (and also internal employees and machine services). These entities pose potential identity and access risks through the thousands of identities associated with them.
To enable business continuity and environment protection, an effective cloud security solution enforces least privilege and detects the irregular use of credentials and other identity based threats on supply chain vendors. It then remediates those threats to help minimize exposure to malware and ransomware from third party vulnerabilities.
Critical Infrastructure
IBM bases their classification of critical infrastructure on CISA, the US Cybersecurity and Infrastructure Security Agency. As mentioned, critical infrastructure industries are financial services, industrial, technology, energy, transportation, communication, healthcare, education and the public sector.
In these industries, 22% of attacks were caused by human errors, 12% occurred due to ransomware attacks and 17% due to supply chain attacks.
 Critical infrastructure data breach types, Cost of a Data Breach Report 2022, IBM Security
Critical infrastructure data breach types, Cost of a Data Breach Report 2022, IBM Security
When it comes to security controls, critical infrastructure industries seem to be less technologically advanced - they have a much lower prevalence of zero trust deployed, only 21%. This also incurred higher data breach costs. The average cost of a breach when no zero trust was deployed was $5.4M, compared to for those who did - a 24.3% difference.
However, in critical infrastructure industries, identification and containment life cycles were faster - 273 days, compared to 282 days for other industries.
 Average life cycle of critical infrastructure data breaches, Cost of a Data Breach Report 2022, IBM Security
Average life cycle of critical infrastructure data breaches, Cost of a Data Breach Report 2022, IBM Security
How a Cloud Security Solution Can Help Secure Critical Infrastructure
As critical infrastructure industries transition to the cloud, they encounter new security threats like cloud misconfigurations and having to manage and monitor thousands of identities and their permissions. To ensure these companies can enjoy the promise of the cloud while securing their assets and data and ensuring compliance, it is recommended to implement practices that will advance their cloud security maturity.
The whitepaper “Cloud Security Maturity Model: Vision, Path, Execution” contains clear, practical and achievable goals that guide organizations toward cloud infrastructure security. By combining processes, technologies and training together into one framework that is easy to follow, the model helps organizations in critical infrastructure industries adopt least privilege and zero trust strategies to secure their cloud environments.
Cloud Breaches, the Cloud Model and Cloud Security Maturity
Cloud infrastructure adoption is accelerating, with 72% of the organizations surveyed operating in the cloud. Some are working in an environment that is completely cloud-based, some in a hybrid model.

However, 43% of organizations had not yet started applying security practices to safeguard their cloud environments or were in the early stages of applying them.
 Cloud security maturity levels, Cost of a Data Breach Report 2022, IBM Security
Cloud security maturity levels, Cost of a Data Breach Report 2022, IBM Security
This is aligned with the findings in the report “State of Cloud Security Maturity 2022” by Osterman Research and commissioned by Ermetic, which found that nearly 43% of the organizations surveyed were at an ad-hoc stage of cloud maturity. The ad-hoc stage is defined in the study as usually not having a defined playbook for incidents. “There may be some sort of response for the incidents detected, but any response will be ad-hoc and not very well defined.”
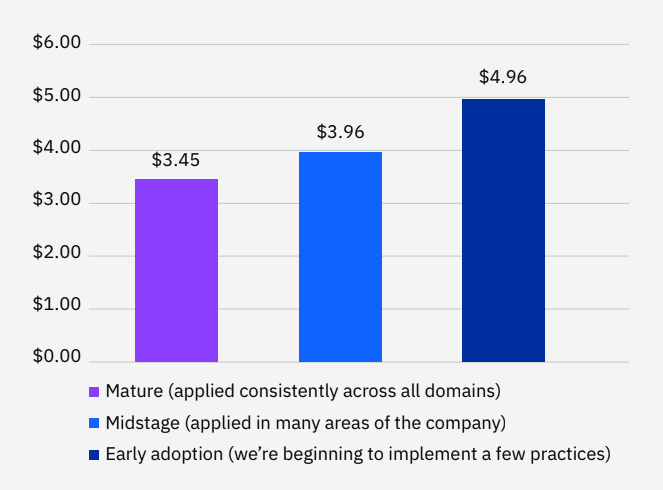
Achieving cloud security maturity pays off - the average cost of a data breach in organizations with mature cloud security was $0.66M lower than those at early stages of cloud security adoption - $3.87M compared to $4.53M. It was $0.72M lower than those that had not yet started applying cloud security practices - $3.87M compared to $4.59M. This is an 18.6% difference.

Mature cloud security also enables identifying and containing data breaches much more quickly than organizations in early stage adoption phases. It took organizations 237 days to identify and contain a breach, which is 40 days shorter than the global average of 277 days, and 64 days shorter than organizations in an early-stage - resulting in a 23.8% difference.
Organizations that had not yet started implementing cloud security practices spent nearly a year - 345 days - identifying and continuing breaches.
Organizations that had not yet started implementing cloud security practices spent nearly a year - 345 days - identifying and continuing breaches. This is more than 100 days longer than organizations with mature cloud security practices.

Average life cycle of data breaches per cloud security maturity level, Cost of a Data Breach Report 2022, IBM Security
How to Achieve Cloud Security Maturity
As mentioned earlier, our cloud security maturity model helps with:
- Prioritizing and implementing cloud security controls and procedures
- Gaining a clear picture of where your organization currently stands on its path to a secure cloud environment
- Designing a cloud security strategy
- Getting stakeholders on board
The framework provides milestones for four stages of maturity across three verticals: people, processes and technologies. For example, risk-based access review for sensitive resources and privileged identities is stage 3 – part of the access governance field in the technology vertical. By adapting the framework to steps and milestones that are right for your organization, it will be easier for you to progress and improve your cloud security maturity, and thus reduce breach costs and shorten breach lifecycles.
Who is responsible for cloud security?
Organizations that deploy the public cloud for their cloud environments are often left confused when having to decipher which part of security they are responsible for and which is under the responsibility of the cloud provider. This is deemed “The Shared Responsibility Model”. It pays to take on responsibilities and to keep track of who’s responsible for what.
- Breaches that were the responsibility of the cloud provider had an average total cost of $4.98M - the highest average cost.
- Breaches that were the responsibility of the organization’s own IT or security team had an average total cost of $4.1M.
- Breaches that were the shared responsibility of the cloud provider and the organization’s IT or security team had an average of $3.98M.
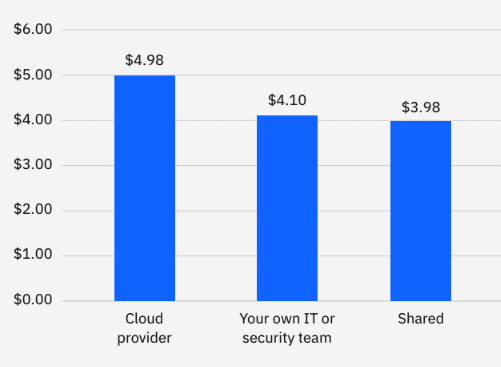
Average cost of a cloud data breach per responsible stakeholder, Cost of a Data Breach Report 2022, IBM Security
In addition, when comparing cloud breaches, the public cloud had the costliest ones. Breaches in a public cloud cost an average of $5.02M while private cloud breaches cost an average of $4.24M. In the hybrid cloud model, breaches cost an average $3.8M.
 Average cost of a cloud data breach per cloud model, Cost of a Data Breach Report 2022, IBM Security
Average cost of a cloud data breach per cloud model, Cost of a Data Breach Report 2022, IBM Security
The “Shared Responsibility Model” is considered a challenging framework for security professionals, due to its lack of clarity, indistinct ownership guidelines and the high levels of expertise required to manage it. However, ignoring the model is worse than the challenges of trying to decipher it.
Leaving gaps in public cloud security can result in cloud misconfigurations or permissions loopholes that could lead to significant and costly breaches. A cloud security solution can help automate risk identification and remediation efforts to reduce these risks and prevent exploitations that will incur heavy business costs.
Security Skills Gap - 62% Not Insufficiently Staffed to Meet Needs
The novelty of the cloud security discipline, the heightened demand for the cloud following digital transformation and the pandemic, and the technological complexity of cloud environments have resulted in a cloud security talent and skills shortage. As a result, says IBM “many organizations struggled to fill positions on their security teams.” The actual percentages are alarming - approximately one third, 38%, said their organization were sufficiently staffed to meet their security management needs – which means 62% were not.
Taking care of this human resources gap is worth the effort: “Those organizations that said they were sufficiently staffed saw considerable cost savings in terms of data breach costs, compared to those without enough employees to staff their teams,” says IBM. The average cost of a breach at these organizations was $4.01M, 12.8% lower than insufficiently staffed teams, where the cost was $4.56M.
How a Cloud Security Solution Can Help Bridge the Skills Gap
A cloud security solution is a technological platform, but a good solution can help with your processes and people as well. A platform that is easy to use, automated and provides insights across Security, DevOps and IAM for all public cloud providers can be used by stakeholders without extensive training or the advanced technological skills known to but a few.
Recommendations for Security Professionals
Transitioning to the cloud advances business innovation and growth, so the next natural step for an organization is to advance their cloud security maturity. Actions related to choosing the right technologies, implementing healthy processes and conducting seasonal training will protect cloud infrastructure and help overcome the challenges of transitioning to the public cloud. The cloud can take your organization and career far, so needs proper attention on your behalf.
Let’s focus for a minute on the technological aspect. To reduce and eliminate the costs incurred by cloud-related data breaches, choose a cloud security solution that prevents breaches like ransomware, implements principles of least privilege and zero trust, and JIT and is based on automation. Such a solution will shorten the data breach lifecycle, close the skills gap and reduce third party risks. Consequently, it will save costs.
The access risk is the greatest threat to your cloud environment. By taking an identity-first approach to managing permissions risk you will minimize the primary attack vectors such as credentials theft and compromise. Your CEO and CFO will thank you.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How AI is Simplifying Multi-Framework Cloud Compliance for CSA STAR Assessments
Published: 03/06/2026
Building a Declarative Governance Framework for the Agentic Era
Published: 03/05/2026
How Attackers Are Weaponizing AI to Create a New Generation of Ransomware
Published: 03/04/2026





.jpeg)
.jpg)