Jenkins Vulnerability Estimated to Affect 43% of Cloud Environments
Published 03/04/2024
Originally published by Orca Security.
Written by Bar Kaduri and Deborah Galea.
On January 24th, Jenkins, a widely used open source CI/CD automation tool, released a security advisory regarding a new critical vulnerability that could allow arbitrary file read, possibly leading to Remote Code Execution (RCE). The vulnerability was discovered by Sonar Security on November 13th, and was assigned CVE-2024-23897 with a CVSS score of 9.8.
The vulnerability is very easy to discover and exploit, and could result in significant consequences for organizations using Jenkins for their CI/CD pipelines. From our scans, we found that 43% of organizations operate at least one unmanaged Jenkins server in their environment. In this blog post, we’ll review what the vulnerability is, why it’s so dangerous, and how to remediate it.
Jenkins security advisory
What is Jenkins?
Jenkins is an open source automation server, used for continuous integration/continuous delivery (CI/CD) processes used by DevOps teams. It helps automate application build procedures, testing and deployment stages. The Jenkins server is widely used due to its easy installation and ability to handle repetitive tasks, which saves a lot of time for DevOps teams.
About the Jenkins vulnerability
The vulnerability occurs when the Command Line Interface (CLI) component of Jenkins parses the ‘@’ character. Parsing the character with a file path after it, returns the entire file’s content for users with Overall/Read permission and the top three lines of files for users without any permissions at all.
The CLI component in Jenkins is used for access from a shell environment. This component is using the args4j library for parsing commands passed through the CLI and is the source of the vulnerability replacing ‘@’ followed by file path with the file content. This feature is enabled by default and Jenkins 2.441 and earlier, LTS 2.426.2 and earlier does not disable it.
How can hackers abuse the vulnerability?
This flaw in handling the ‘@’ character allows attackers to view sensitive files in the Jenkins instance such as etc/passwd, etc/shadow, keys files, source code and more.
In addition to that, this vulnerability allows remote code execution in several scenarios presented in Jenkins’ advisory. For example a stored XSS through build logs, a “Remember Me” cookie and CSRF protection bypass. Jenkins noted that this attack scenario list is not final, and it is likely that there are more scenarios that could lead to RCE by exploiting this vulnerability.
The vulnerability has several POCs available online, and many organizations have already reported exploitation attempts towards publicly facing instances.
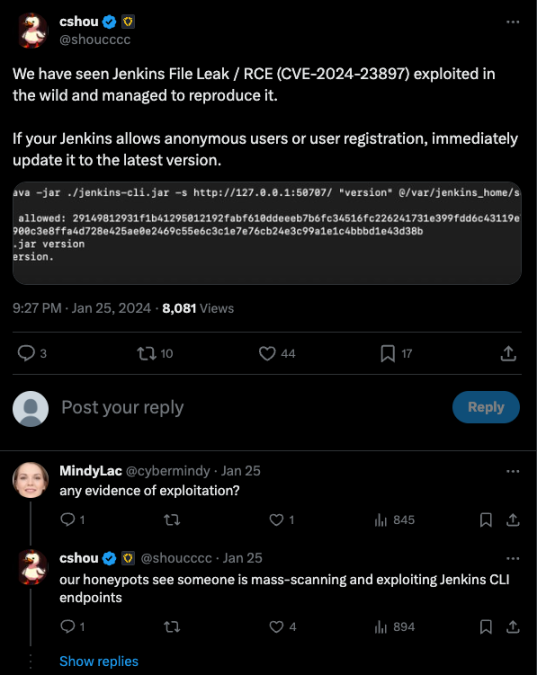
Reports of Jenkins CVE exploitation attempts
On January 30th, ShadowServer announced that they found over 45,000 exposed vulnerable instances worldwide, and shared the following heatmap, showing that the US, China and Germany are the most exposed countries.
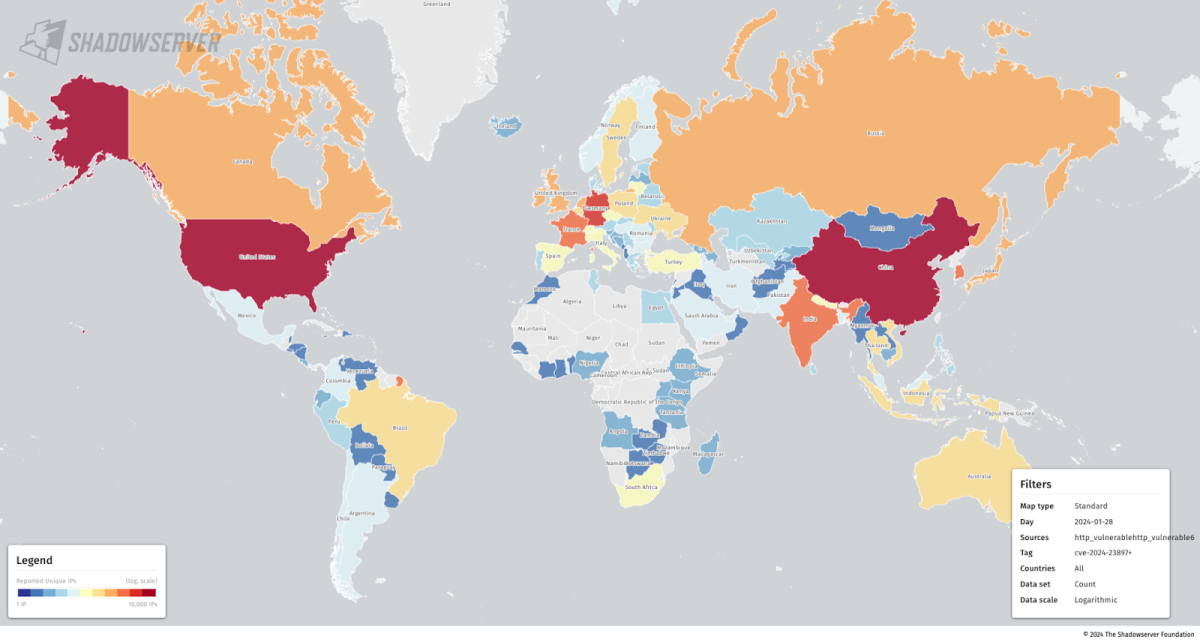
Heatmap of Jenkins servers exposed to CVE-2024-23897
How to remediate the Jenkins vulnerability
Due to the critical nature of this vulnerability, it is highly recommended to update the Jenkins server as soon as possible to Jenkins 2.442, LTS 2.426.3. If upgrading is not possible immediately, the Jenkins team recommends disabling access to the CLI. This should prevent any exploitation of the vulnerability and not require a restart of the server.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Agentic AI Pen Testing: Speed at Scale, Certainty with Humans
Published: 01/26/2026
My Top 10 Predictions for Agentic AI in 2026
Published: 01/16/2026
Best Practices to Achieve the Benefits of Agentic AI in Pentesting
Published: 01/13/2026







.jpeg)

