Protecting PII in the Cloud
Published 07/25/2023
Written by Ashwin Chaudhary, CEO, Accedere.
Cloud computing has revolutionized the way businesses operate, providing flexibility, scalability, and cost savings. PII (Personal Identifiable Information) refers to any data that can be used to identify a specific individual. PII is often sensitive information that needs to be protected to ensure the privacy and security of individuals. However, cloud environments can also pose significant risks to PII if not properly secured.
What is PII?
Any information that can be used to identify an individual falls under the category of PII. The most common types of data exposed in these breaches are personally identifiable information (PII).
Why is PII important?
PII is important because it can be used for identity theft and fraud if it falls into the wrong hands. PII falls under Privacy regulations and the consequences of non-compliance with privacy requirements are as follows:
- Legal Ramifications
- Reputation Damage
- Financial Impact
- Loss of Customer Trust
- Regulatory Scrutiny and Audits
- Limited Business Opportunities
Challenges for Protecting PII in Cloud
Data Security: Cloud environments are susceptible to security breaches, which can lead to unauthorized access to PII.
Data Privacy: Cloud providers may have access to PII stored on their platforms, raising concerns about data privacy.
Compliance Requirements: Various compliance regulations, such as GDPR, CCPA (California Consumer Privacy Act), or sector-specific regulations like HIPAA, impose strict requirements for protecting PII.
Data Residency and Jurisdiction: Cloud services often operate across multiple jurisdictions, and data may be stored or processed in different locations.
Shared Infrastructure: Cloud environments involve shared infrastructure where multiple customers' data coexist on the same physical resources.
Insider Threats: Unauthorized access or misuse of PII by insiders, including employees of the organization or cloud service providers, remains a significant concern.
Data Transfer and Interoperability: Transferring PII to and from the cloud and ensuring interoperability between different cloud services can introduce security risks.
Vendor Lock-in and Service Continuity: Organizations may face challenges if they need to switch cloud providers or migrate data from one provider to another while maintaining the security and integrity of PII.
Data Breaches Statistics
According to research by Surfshark, 41.6M accounts were leaked in the first quarter of 2023, i.e., one account was leaked every second.
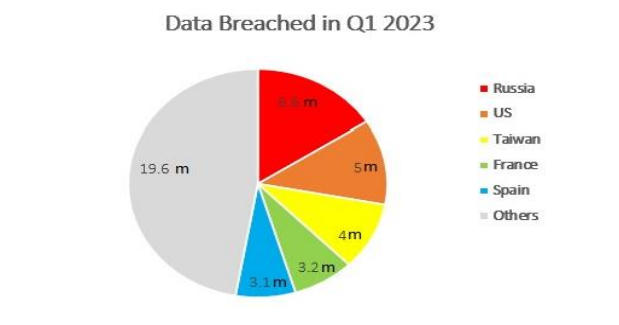
In an article by Mr. Scott Mathrick on March 7, 2023, Top cyber security breaches of 2022, a few of the data breaches related to Personal data are listed below in the table.
| Affected Entities | Entities Countries | Data Breached | Impacted Users |
| Optus September 22, 2022 | Australia | Personal & Medical Information like names, dates of birth, phone numbers, email, and home addresses, driver's license and/or passport numbers, and Medicare ID numbers | 11 million |
| WhatsApp November 16, 2022 | Germany(G), US, UK | Personal Information of 500 million users from 84 countries | 32 million (US)
11 million (UK) 6 million (G) |
| Nelnet Servicing June-July 2022 | US, Canada | Sensitive data like student loan account registration data, including names, addresses, phone numbers, and social security numbers | 2.5 million |
| Revolut September 11, 2022 | British-Lithuanian, Europe | Personal Information like Database, names, addresses, and partial payment card information | 50,150 |
Controls to be addressed via processing PII
- People have the right to know the purpose and how their personal information is being collected, used, and shared.
- Before sharing the PII with any third-party Consent from the PII owner is a must.
- A privacy Notice must be communicated to the PII owner if there is any change in the privacy policy.
- Protecting PII ensures that individuals can maintain control over their personal data and can limit access to it by unauthorized parties.
One of the major international standards for privacy information management is ISO/IEC 27701. Protecting private information assets and proving compliance with privacy and data protection laws are two of ISO 27701's key goals, regardless of location or industry.
Protecting PII with ISO 27701 Certification
- Promotes trust in your company's handling of personal information.
- Effective commercial agreements may be facilitated.
- Assists in ensuring adherence to various privacy laws.
- Assists in fostering confidence in your company's management of personal information.
- Enhances organizational clarity regarding roles and duties.
In addition to legal and ethical obligations to protect PII, businesses also face regulatory requirements. For example, the General Data Protection Regulation (GDPR) in the European Union requires businesses to protect the privacy and security of personal data. Failure to comply with these regulations can result in significant penalties and reputational damage for businesses.
How to protect PII?
Protecting PII is essential to prevent identity theft and ensure privacy criteria. Here are some best practices to help protect PII.
- Limit the collection of PII: Collect only the information you need and avoid collecting unnecessary data.
- Securely store PII: Store PII in a secure location and limit access only to authorized personnel.
- Use access controls and segmentation: Access controls should be used to restrict access to PII based on job function and need-to-know. Segmentation can also be used to isolate sensitive data from other less sensitive data.
- Implement multi-factor authentication: Multi-factor authentication adds an extra layer of security to user accounts, making it harder for unauthorized users to gain access to PII.
- Use encryption: Use encryption to protect PII while in transit and at rest.
- Train employees: Educate employees on the importance of protecting PII and provide training on best practices for handling PII.
- Monitor PII usage: Monitor the use of PII and implement security measures to detect and prevent unauthorized access or use.
- Regularly review and audit logs: Regularly reviewing and auditing logs can help detect any potential security incidents or breaches. This can also help identify any areas where security can be improved.
- Conduct regular vulnerability assessments and penetration testing: Regular vulnerability assessments and penetration testing can help identify any weaknesses in your cloud environment before they can be exploited by attackers.
Protecting PII is necessary to ensure privacy, prevent identity theft, meet legal and regulatory obligations, and protect the reputation of businesses.
By implementing these best practices & implementing ISO/IEC 27701 for protecting PII, organizations/entities can ensure that they meet their legal and ethical obligations to protect sensitive information. By adopting a proactive approach to ensure Privacy that includes regular audits, vulnerability assessments, and pen testing organizations can stay ahead and protect PII in cloud environments.
About the Author
Ashwin Chaudhary is the CEO of Accedere, a Data Security, Privacy Audit and Training Firm and an ISO/IEC Certification Body as well as a CPA Firm. Ashwin is a CPA from Denver, Colorado, MBA, CITP, CISA, CISM, CGEIT, CRISC, CISSP, CDPSE, CCSK, PMP, ISO27001 LA, ITILv3 certified cybersecurity professional with about 20 years of cybersecurity/privacy and 40 years of industry experience. He has managed many cybersecurity projects covering SOC reporting, ISO audits, VAPT assessments, Privacy, IoT, Governance Risk, and Compliance.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
The Great Divide: How AI Is Splitting the Cybersecurity Landscape
Published: 02/12/2026








.jpeg)
