SANS 2022 Cloud Security Survey, Chapter 3: How Do Enterprises Keep Their Cloud Infrastructure Secure?
Published 01/18/2023
Originally published by Gigamon.
Editor’s note: This post explores Chapter 3 of the SANS 2022 Cloud Security Survey. Read Chapter 1 and Chapter 2. And check back or future posts covering Chapter 4.
There’s been a cloud land rush over the past few years as more and more organizations move compute and storage to cloud providers, and it seems like security has been playing catch-up. But more and more organizations are rolling out the security controls and policies they need to keep their data and infrastructure secure. That’s what the results of the SANS 2022 Cloud Security Survey show — though they also show that there’s still work to be done.
In our previous post in this blog series, we saw that potential vulnerabilities and real-world attacks on the cloud were keeping security pros up at night.
In this installment, we’ll see how survey respondents are beefing up their cloud infrastructure to protect their data and organizational reputation. The good news is that the overwhelming majority — 77 percent — of surveyed organizations have cloud security and governance policies in place today, up from 69 percent in 2021. Let’s take a deep dive to see what controls these companies have implemented.
A Full Toolbox
Figure 1 illustrates the various tools surveyed organizations use to secure their cloud environments. And to get more granular, SANS broke the data down by tools that are internally managed, tools implemented as part of a security-as-a-service (SecaaS) environment, or tools that are hybrids straddling both worlds.
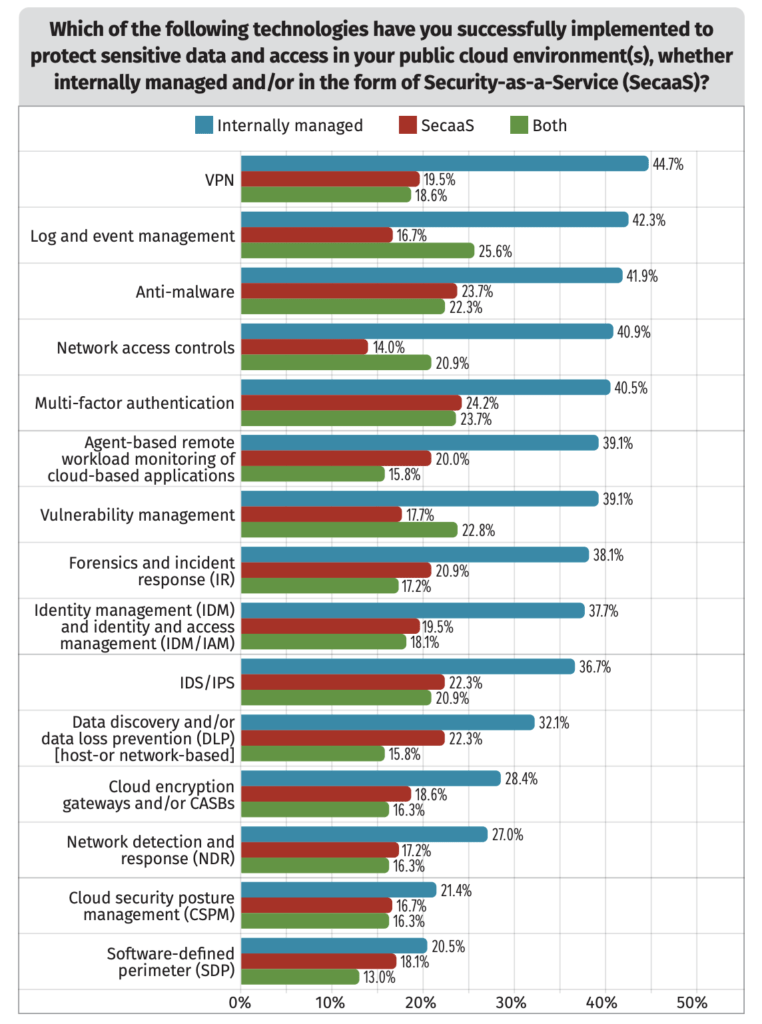
Figure 1. Security controls for cloud sensitive-data protection.
VPNs represent the most widely implemented internally managed tool, though at 45 percent, fewer organizations are managing traditional VPNs than previously. Meanwhile, the top SecaaS services in this year’s survey are multifactor authentication and anti-malware.
In general, these numbers represent positive trends over previous years. In particular, there’s been a relatively dramatic growth in SecaaS tooling: Most of these services were in the 10 to 15 percent range in the 2021 SANS survey, while many are now above 20 percent.
SANS also asked respondents to look ahead to the next year and try to identify the tools they plan to integrate in the near future. The top answers were forensics and IR tools at 35 percent and cloud risk assessment tools at 33 percent, with event management and SIEM platforms trailing close behind.
Detection and incident response have long been neglected by many teams, but as organizations focus more on cloud risk, they are realizing the need for more cloud-centric reporting and controls analysis.
You Can’t Secure What You Can’t See
SANS always asks surveyed organizations what their biggest challenges are in adapting forensics and incident response tools to the cloud. The results for 2022 are shown in Figure 2. The top response for the third consecutive year is a lack of real-time visibility into events and communications involved in incidents.
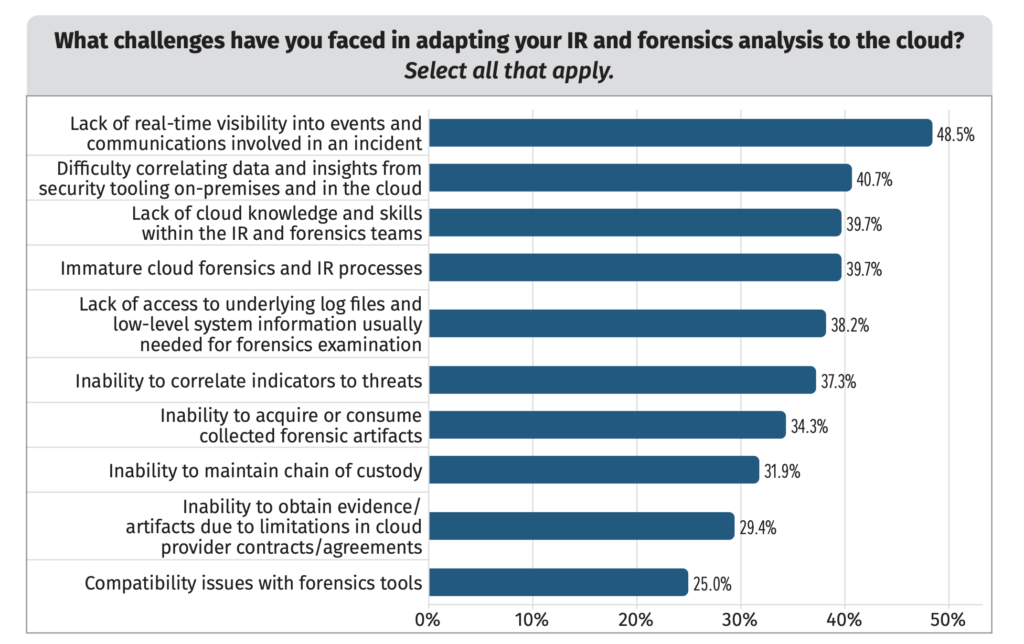
Figure 2. IR and forensics challenges in the cloud.
Organizations are clearly still struggling to get insight into events and cloud activity. Other related visibility challenges include difficulty in correlating events between on-premises and cloud environments, and getting sound forensics evidence like log files and system artifacts.
One way organizations are dealing with these blind spots is through the use of automation and orchestration tools, which has increased across the board since the previous survey.
In the fourth and final installment in this series, we’ll focus on a particular type of security control — cloud identity and access management — and see how respondents to the SANS survey are implementing it in their own organizations. In the meantime, you can dive into the full survey report and get the full details from survey respondents.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates





.jpeg)