Unveiling the Dark Arts of Exploiting Trust
Published 05/14/2024
Originally published by CXO REvolutionaries.
Written by Tony Fergusson, CISO in Residence, Zscaler.
Trust is a fundamental aspect of human interaction, forming the foundation of relationships and societal harmony. However, trust can be deceptive, concealing hidden vulnerabilities that emerge when we let our guard down. This leaves us exposed to unforeseen risks and challenges.
There was a time when internet security was essentially synonymous with URL filtering. This recognized site = allow. This known bad website = block. These black-and-white distinctions served us well when the internet was more static. Today, trust isn’t so simple.
Content delivery networks (CDNs) and SaaS solutions have expanded our exposure to dangerous traffic from trusted web domains. Traditional malware authors today happily leverage these services to achieve their ends when able. In fact, Crowdstrike found that, in 2023, 75% of intrusions it detected did not involve malware but "the exploitation of vulnerabilities and trusted relationships."
Threat actors are turning to admin functions and trusted productivity sites to carry out attacks while avoiding detection. Widely-used web services like code repositories, cloud storage, text storage, and webhooks are increasingly weaponized by cybercriminals.
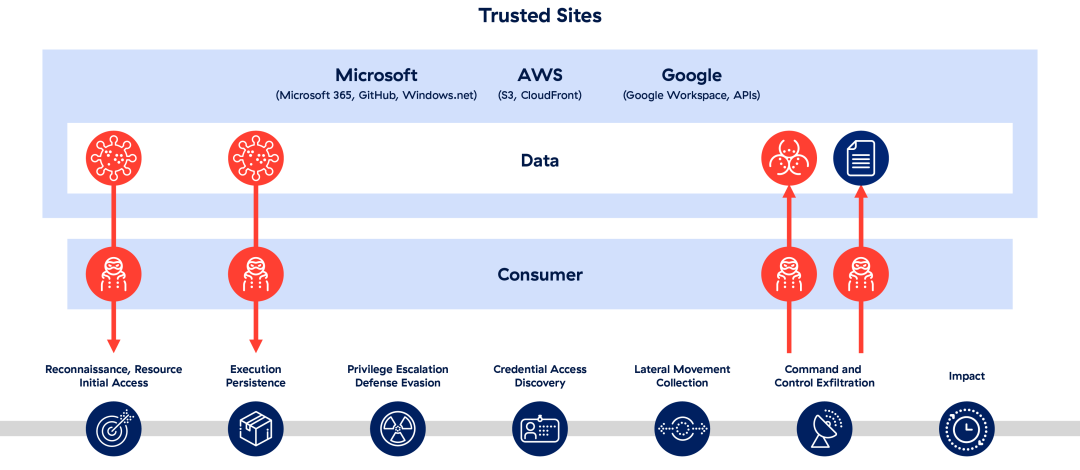
How trusted hypervisors can abet common cyber operations
For CISOs and their security staff, this recalls the age-old dilemma of user enablement vs. security. Their employees use these tools to facilitate collaboration and productivity. But bad actors are turning these trusted services against the organizations that rely on them.
Foraging for a digital payoff
Living off the land (LOTL) attacks rely on widely used admin functions and tools to conduct a cyberattack while evading detection. They often involve recognized and widely used tools like Remote Desktop Protocol (RDP) or Powershell.
Because these are trusted functions and features, their use tends not to trigger alerts from SOCs or other security personnel. This is despite the fact that recent announcements from Microsoft and U.S. officials say there is evidence that APT groups like the China-sponsored Volt Typhoon are turning to LOTL techniques to establish a presence in U.S. critical infrastructure assets. Zscaler threat researchers believe recent Ivanti breaches were meant to enable similar covert behavior.
You can find a list of some of the most common binaries, scripts, and libraries used to launch LOTL attacks here.
A case of broken trust
In contrast to LOTL attacks, living-off-trusted-site (LOTS) attacks take advantage of trusted web services used by many organizations to download malware, launch phishing campaigns, communicate with command-and-control (C2) servers, or exfiltrate data. Similar to LOTL, LOTS takes advantage of the fact that communication with sites like GitHub, SharePoint, or OneDrive tend not to arouse suspicion. These sites don't tend to monitor or control the content they deliver and are accessible to anyone with a credit card.
In one egregious example, security researchers discovered more than 100,000 code repositories on GitHub infected with malicious code. Well-meaning developers run the risk of embedding such code into their products without notice.
The popularity of SaaS-delivered solutions means threat actors have ample targets at which to aim their LOTS attacks. Roughly 25 percent of the traffic passing through the Zscaler Zero Trust Exchange, for instance, involves Microsoft 365.
You can find a list of the sites most commonly used to launch LOTS attacks here.
The path of least resistance
While many organizations today remain focused on endpoint protection, addressing security alerts, and similar signals, cyber criminals realize that a compromised identity alone can enable LOTL and LOTS attacks without creating much noise.
In thinking about how best to defend against LOTL and LOTS attacks, consider the famous “Pyramid of Pain” model developed by the security researcher David Bianco.
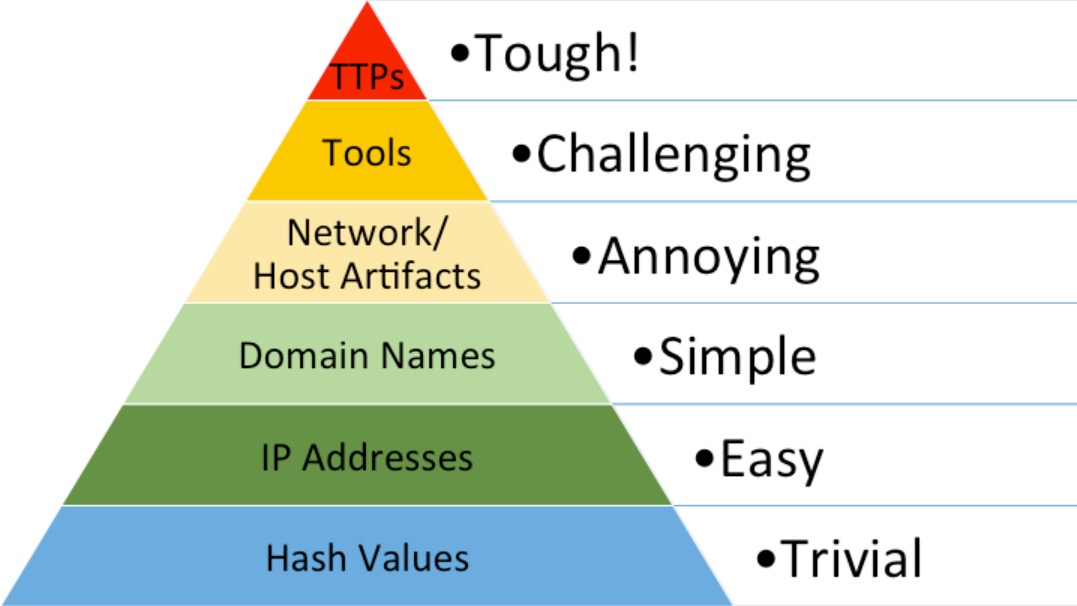
The "Pyramid of Pain" first conceived by David Bianco
It states that while hash values, IP addresses, and domain names are relatively easy to tweak, techniques, tactics, and procedures (TTPs) are far more difficult. So, start by addressing behaviors.
Code repositories, especially popular ones already used by an organization, provide "a significant amount of cover" for threat actors, according to MITRE. But, if I have a 10,000 user organization, and I notice a user communicating with a certain GitHub server every hour on the hour – that should raise a red flag. Supposedly trustworthy open-source code has been tampered with in potentially damaging ways even in recent weeks.
So behavioral cues are critical to flagging potential LOTL and LOTS attacks in progress. Additionally, because these attacks are so difficult to flag as suspicious, it’s important to enforce the principle of least privilege beyond the domain itself to individual cloud instances.
Security teams should pay particular focus to application instances for services like OneDrive and SharePoint that do not belong to the organization. Cloud Application Instances can restrict access to these tools to only the corporate tenant, and browser isolation can be used when the need to access non-corporate tenants arises.
The MITRE ATT&CK Framework notes that adversaries may use an "existing, legitimate external Web service" to download malware, conduct phishing attacks, exfiltrate data, or communicate with a C2 server and often mask this traffic with SSL/TLS encryption. This underscores the importance of inspecting encrypted traffic, at least for trusted domains that may communicate freely out from the organization.
SSL/TLS inspection is worthy of further exploration here. As mentioned, many of the most widely-used, legitimate productivity enablement tools do not consider it their responsibility to inspect the data flowing in and out of their tools. Cybercriminals have taken advantage of this fact to use them for smuggling corporations’ own data out from their networks for use as they see fit.
Along with SSL inspection, deception can be a powerful tool in discovering LOTS attacks because it addresses the difficult, top portion of the Pyramid of Pain. “Negative trust,” as a colleague of mine calls it, using honeypots and lures in front of users behaving suspiciously can quickly separate legitimate actors from those with ulterior motives by using something like a beacon file.
Ultimately, security administrators will overcome this problem the same as they have with previous ones. Namely, by:
- Knowing who and what they are up against by understanding threat actors’ tactics themselves with this new preference among threat actors
- "Risk hunting," or mapping known TTPs onto an organization's existing defenses and using that understanding to close any gaps discovered.
- Focusing on data protection over URL filtering, and using behavioral monitoring to protect what today’s cyber criminals tend to target most: customer data, intellectual property, and extortion material.
A CISO’s education is ongoing. It’s critical we recognize this pattern of moving away from malware as growing sophistication and tenacity from those who are able to access our systems. In the best spirit of zero trust, it's time to “never trust, always verify.”
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Building a Declarative Governance Framework for the Agentic Era
Published: 03/05/2026
How Attackers Are Weaponizing AI to Create a New Generation of Ransomware
Published: 03/04/2026
What is a Risk Engineer?
Published: 03/02/2026







.jpeg)
.jpg)
