Verizon’s 2022 Mobile Security Index Report – Confirming What We All Suspected
Published 09/14/2022
 Originally published by Thales here.
Originally published by Thales here.
Written by Todd Moore, VP, Encryption Products, Thales.
What happens when you combine a pandemic that forces most businesses into a remote work environment, coupled with increased mobile device use for many daily tasks? On the one hand, you get increased productivity and ease of access. However, most cybersecurity professionals saw this increased accessibility as an increased attack surface, and a prime opportunity for criminals. Sadly, according to the newly released Verizon Mobile Security Index, these security professionals were correct in their assumptions.
From the foreword of the report, all the way to the end, the analysis indicates that mobile devices pose a greater risk to organizations. This conclusion is not reached because the devices are necessarily unsafe, but because the volume of device use has increased. One fascinating finding was that the wider an organization’s global presence, the higher incidence of mobile device compromise. One would anticipate that larger organizations would have more stringent security controls for such a large employee base, making a smaller, apparently less secure organization the easier target. However, the larger the organization, the greater the compromise tally. When seriously contemplated, it is easy to see the factors that are influencing these events.
A primary means of communication
The report reveals that most people no longer consider their smartphones as secondary devices. Before you laugh at the obviousness of this, it needs to be brought into stark reality to fully grasp what has led to the rise of the mobile device as the new attack surface. As a simple, loose study, ask yourself how many of your friends and family own a “land-line” anymore? Mobile devices are now the primary means of communication and other activities. In fact, no one refers to them as “mobile devices” anymore.
Consumers and employees demanded the ability to be able to access office files from the convenient, ubiquitous device that is always available. This increased ability to access everything everywhere has also contributed to the problem. Countering all of the risks is an increased security spend, as the report indicates that 77% of respondents indicated that they are devoting more budget to security. If the phones are secure and the security spending has increased, how is it possible that successful attacks are occurring?
Points of weakness
One of the first points of weakness that the report discloses is that the failure of employees to disconnect often results in errors. While the report uses the term “negligence”, this is not intended as derisive, and it signals more the problem of burnout and fatigue. Fortunately, the report does not dwell on a “blame the user” approach. Rather, it shows that there are more systemic influences at work. One of these is that many companies still do not take cybersecurity seriously until after an event occurs. The Verizon report includes a startling statistic that appeared in the 2022 Thales Data Threat Report that “two-fifths of organizations are not confident that their current security systems could effectively secure the remote work environment.”
Another organizational weakness that contributes to the increased attack surface is the lack of training and policy. Short of a full training program, the Verizon report offers simple instructional sheets that can be easily extracted and printed to assist employees towards achieving better security practices for mobile device use.
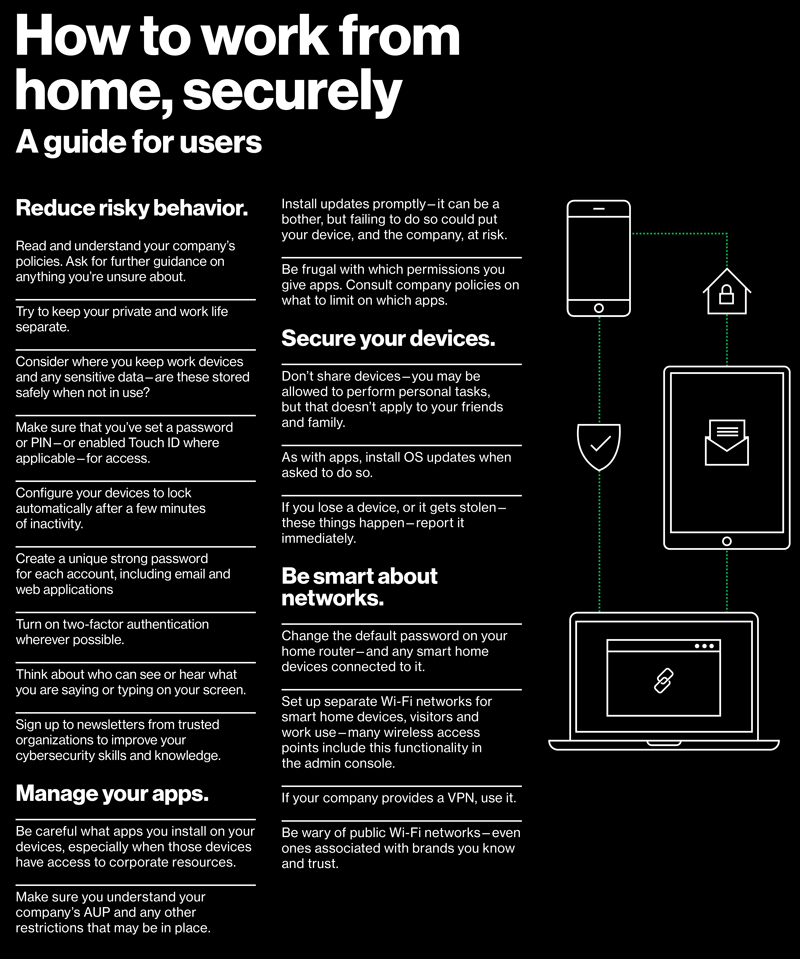
Security is a shared responsibility
Everyone knows the usual song about how important passwords are for mobile devices, how to be aware of “shoulder surfers”, and all the perils of social engineering, and these risks are reiterated in the recent report. Just as the report does not spend time blaming the user, it equally emphasizes that security is a shared responsibility. An important revelation that highlights this is that most people think that their employer’s systems, and their personal email providers have mechanisms to prevent attacks.
Attackers continue to improve their abilities to convince a person that a message is legitimate, and it would be appropriate for everyone to become avers well-versed in security as possible, acting as an enhancement to all of the technical safeguards that are in place.
Overall, the entire report offers a good mix of guidance and solutions for both the device owners, as well as organizations towards improving security in this new work environment.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Agentic AI and the New Reality of Financial Security
Published: 02/26/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026


.png)

.jpeg)

