Why Phishing is a Bigger Threat than Ransomware
Published 10/08/2021
This blog was originally published by Bitglass here.
Written by Jonathan Andresen, Bitglass.
While enterprise security teams have had their hands full battling an increasing number of more sophisticated ransomware attacks, phishing attacks are on the rise with the easing of pandemic-related restrictions.
In fact, recently Microsoft warned of a widespread credential phishing campaign that leverages open redirector links in email communications as a vector to trick users into visiting malicious websites while effectively bypassing security software.
"Attackers combine these links with social engineering baits that impersonate well-known productivity tools and services to lure users into clicking," Microsoft 365 Defender Threat Intelligence Team said in a report published this week.
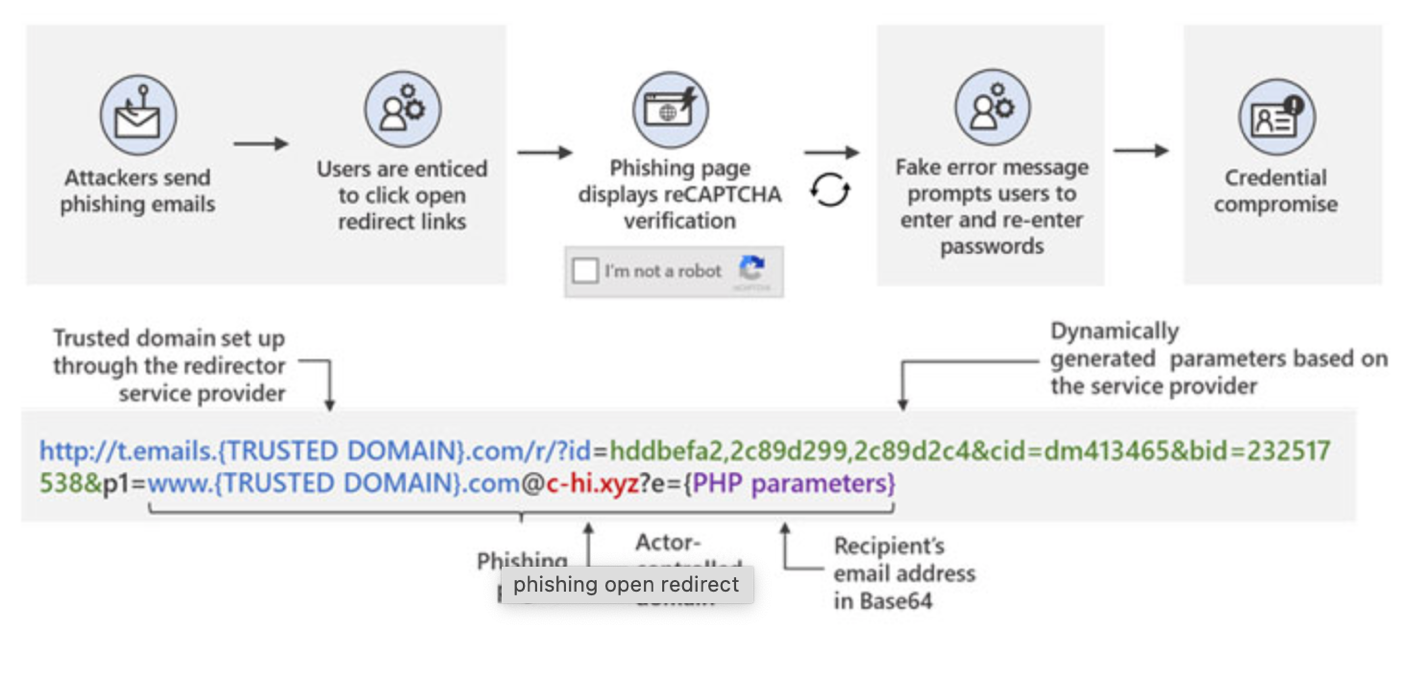
"Doing so leads to a series of redirections — including a CAPTCHA verification page that adds a sense of legitimacy and attempts to evade some automated analysis systems — before taking the user to a fake sign-in page. This ultimately leads to credential compromise, which opens the user and their organization to other attacks."
It’s clear that attackers will keep hammering away at remote access technologies and vulnerabilities in cloud environments, attempting to steal credentials and thereby obtain confidential enterprise data.
While large ransomware attacks certainly make news coverage, phishing attacks are more common and have increased significantly. The latest data shows a world-wide-web laden with phishing websites. Since 2016 phishing has replaced malware as the leading type of unsafe website. While there were once twice as many malware sites as phishing sites, there are now nearly 75 times as many phishing sites as there are malware sites.
So how to stop phishing attacks? The first step is to recognize that no one application vendor can solve all your security needs. It’s best to implement a centralized security control point across cloud services, web, and private datacenter applications with a common policy framework for data protection, threat protection, and acceptable use policy.
Preventing today’s increasingly dynamic phishing attempts requires next-generation “on-device” web security that can block phishing sites and apply advanced threat protection across all the user’s devices, both managed and unmanaged. Ensuring safe browsing in a mobile-to-cloud environment requires comprehensive security controls with deep visibility, bringing together disparate security functions into a single-cloud delivered security platform, without agents, VPNs, and performance bottlenecks.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
Agentic AI Pen Testing: Speed at Scale, Certainty with Humans
Published: 01/26/2026


.png)



.jpeg)