Zooming In: 6 Ways Cybercriminals Use the Black Market to Steal Zoom User Data
Published 08/01/2024
Originally published by Abnormal Security.
In the wake of the COVID-19 pandemic, video conferencing platforms like Zoom experienced an unprecedented surge in popularity. However, this increased usage also attracted the attention of cybercriminals who sought to exploit the platform's growing user base. Here, we’ll take a look at the methods used to obtain stolen Zoom accounts, the platforms where they are traded, and the motivations behind this illicit market.
1. Phishing Pages
Cybercriminals use a variety of techniques to obtain stolen Zoom accounts, with phishing remaining the most prevalent tactic. Attackers create fake login pages that closely mimic the official Zoom website and distribute links to these pages via email or instant messaging. When unsuspecting users input their credentials, the information is immediately captured by attackers. The following examples illustrate how easily these deceptive pages can be created and then shared among cybercriminals.
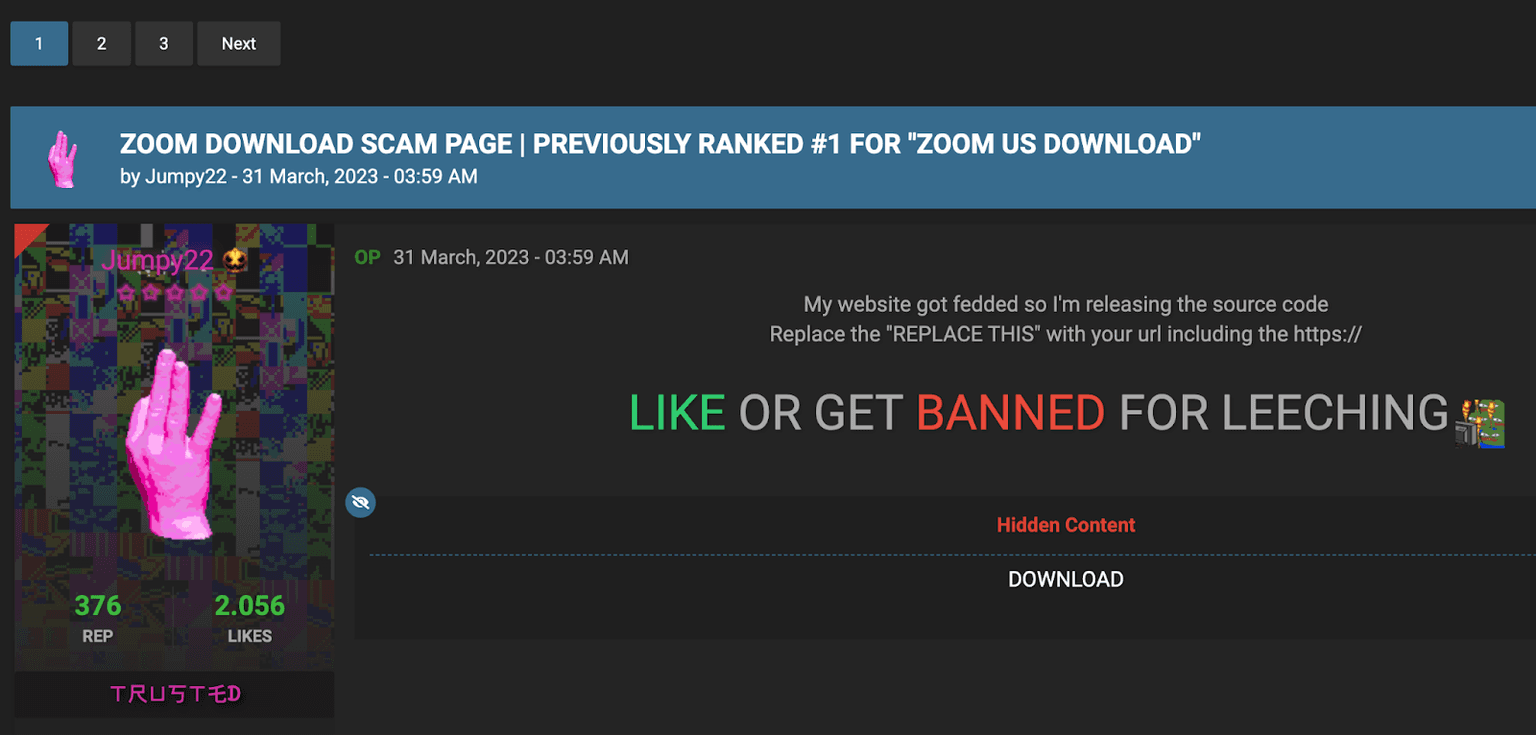
Figure 1: A Zoom scam page being shared on a cybercrime forum.
2. Information Stealers
Information stealers, a type of malware designed to harvest sensitive data from infected devices, also play a significant role in the theft of Zoom accounts. These malicious programs can be delivered through various means, such as email attachments or compromised websites. Once installed, they silently collect data, including usernames and passwords, which are then sent back to the attackers. Figure 2 showcases an example of an information stealer called Planet Stealer which was recently put up for sale, and captures Zoom credentials due to its native keylogging capabilities.
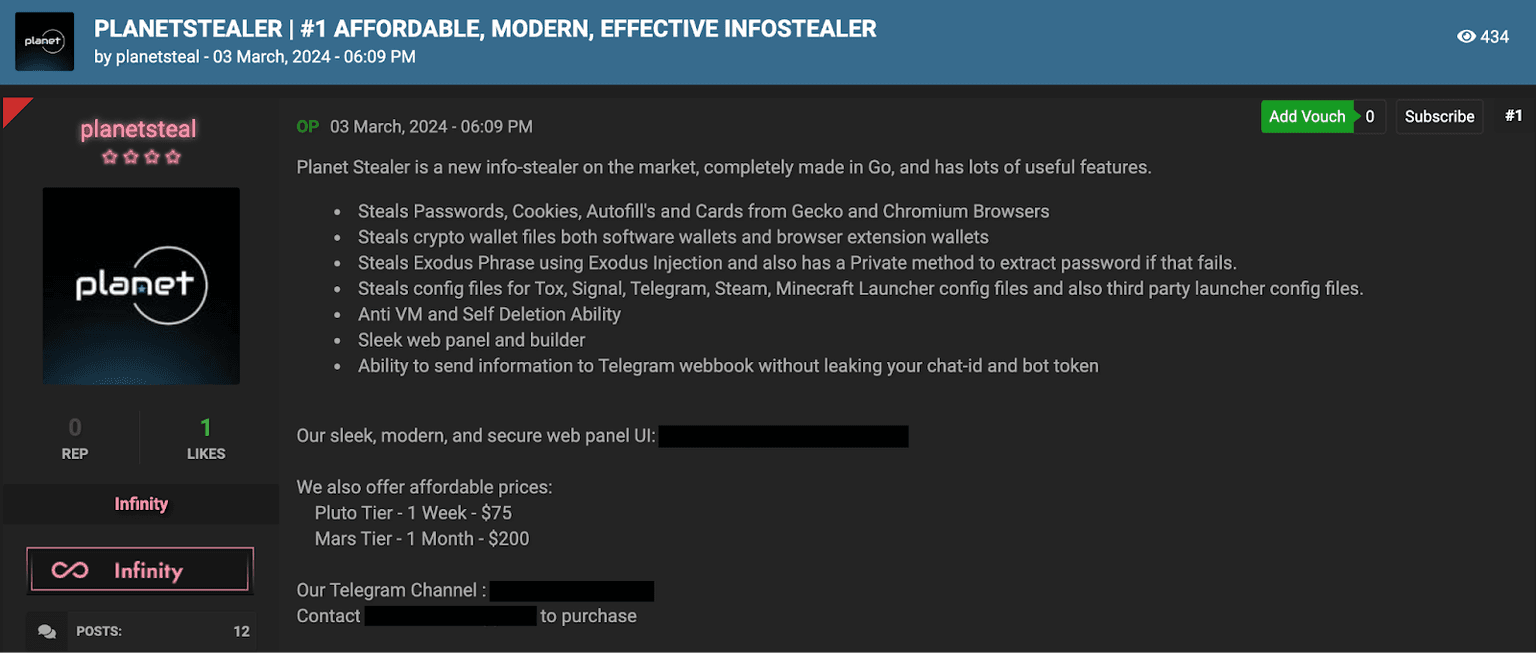
Figure 2: An information stealer being sold on a cybercrime forum.
3. Credential Stuffing with OpenBullet Configurations
Another method used by cybercriminals to obtain Zoom user data is credential stuffing. This automated attack method takes advantage of the fact that many users reuse the same login information across multiple online services. Attackers obtain large collections of stolen credentials from previous data breaches and use software, such as OpenBullet, to test these credentials against Zoom's login system. As shown in Figure 3, cybercriminals often seek out OpenBullet configurations optimized for specific websites, enabling them to test a large number of accounts efficiently.
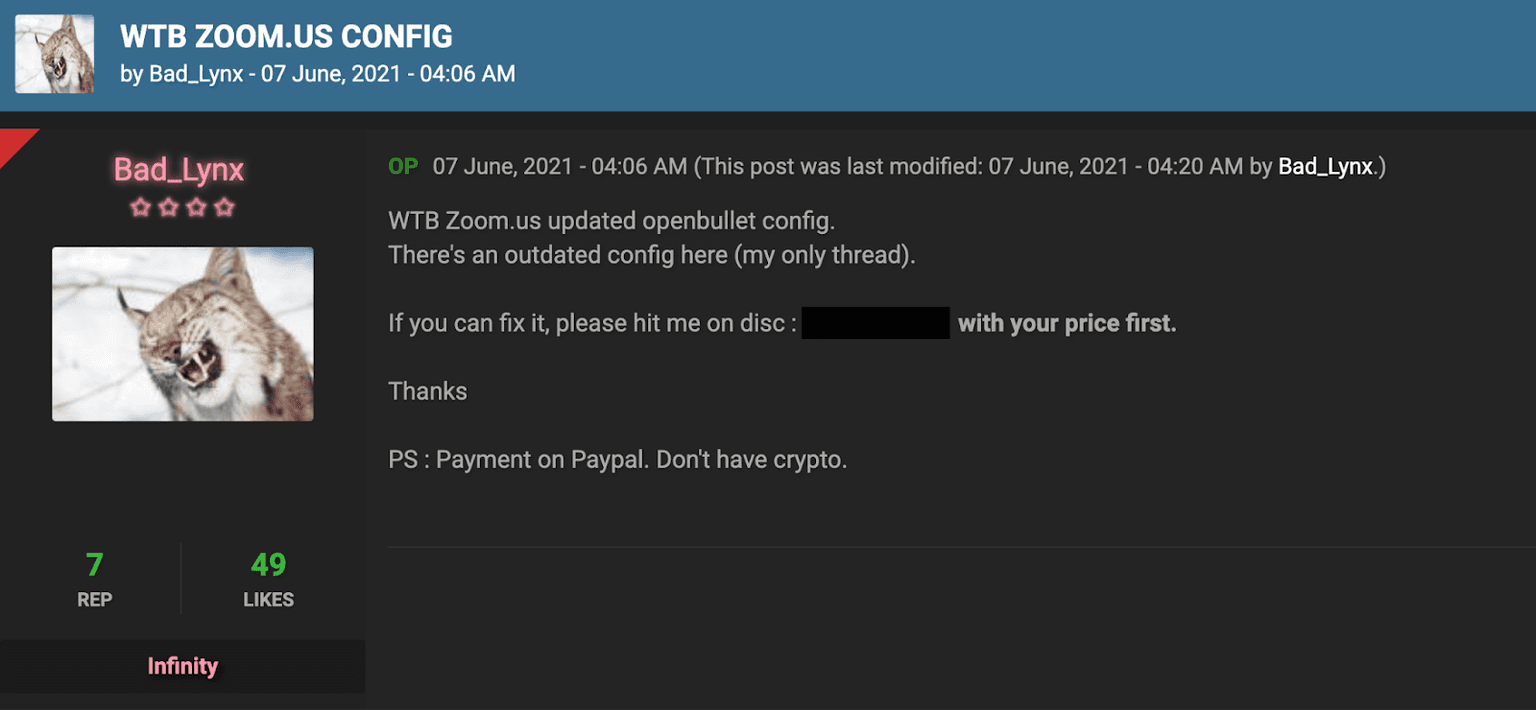
Figure 3: A user looking to purchase an OpenBullet configuration for Zoom.
4. Cloud Log Markets
Once Zoom accounts have been stolen, they are distributed through various platforms to reach potential buyers. Cloud log websites, for instance, serve as centralized repositories for stolen account information. These websites, often operated by cybercriminals who specialize in collecting and organizing stolen data, contain not only Zoom accounts but also other sensitive information like names, email addresses, and credit card details. Figure 4 presents an example of a cloud logs market called Exodus Market.

Figure 4: An example of a cloud log market called Exodus Market.
5. Digital Stores
Digital stores, also known as account shops, are another popular destination for stolen Zoom accounts. Sometimes these marketplaces operate on the dark web, accessible only through software like The Onion Router, known as Tor. Tor is a free and open-source internet network that allows anonymous communication by routing internet traffic through a network of relays, concealing a user's location and activity from network surveillance. On these platforms, stolen accounts are sold individually or in bulk, with prices varying based on factors such as the account's age and subscription level. Figure 5 demonstrates how Zoom accounts can be acquired for as little as $3.00 each on a digital store called FullAccess.
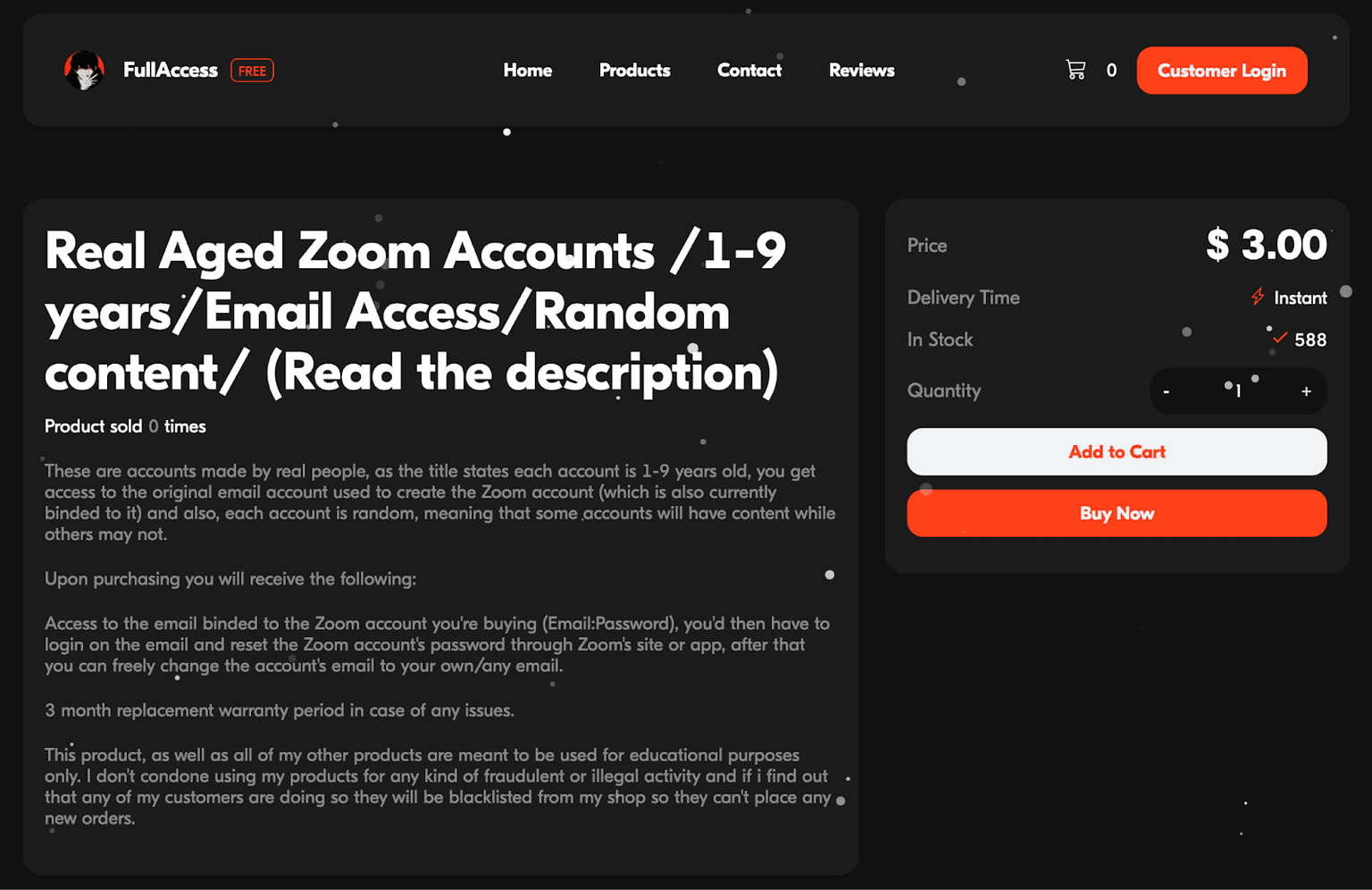
Figure 5: Zoom accounts being sold on a digital store for $3.00.
6. Cybercrime Forums
Cybercrime forums and networks are communities where hackers and cybercriminals frequently gather to share information, tools, and stolen data. These platforms are often invitation-only and require users to prove their criminal credentials before gaining access. On these forums, stolen Zoom accounts are openly traded, sold, or even given away for free as a way to build reputation within the cybercriminal community. Figure 6 illustrates an example of a cybercriminal offering 200+ Zoom accounts in bulk on one platform, highlighting that they are mostly premium accounts with credit cards attached.
Figure 6: A user selling 200+ Zoom accounts in bulk.
Why Attackers Are Stealing Zoom Accounts
While it may appear that cybercriminals are only targeting consumers, the reality is that they are targeting everyone they can, including enterprise accounts. The demand for stolen Zoom accounts is likely driven by the desire for cheap access to the platform's premium features, such as longer meeting durations and larger participant limits. By purchasing stolen accounts at extremely low prices, buyers can gain access to these features without paying the full subscription fee. However, not all buyers are aware that the accounts they are purchasing are stolen. Cybercriminals often disguise these accounts as promotional offers or discounts, luring in unsuspecting users and customers.
The demand for Zoom accounts also stems from the underground market's operation as a profitable resale scheme. Information stealer logs, which contain stolen account information, are initially sold at relatively low prices on cloud log websites. However, when these accounts are then sold on digital stores, the prices are often marked up significantly. This allows cybercriminals to profit from the resale of stolen accounts, creating a lucrative business model that incentivizes the continued theft and distribution of Zoom user data.
Defending Against Stolen Zoom Accounts
The black market for stolen Zoom accounts is thriving, with cybercriminals using techniques like phishing, information stealers, and credential stuffing to obtain and sell compromised credentials. As these attackers become increasingly sophisticated, protecting your user data will be more important than ever.
Safeguarding Zoom credentials from cybercriminals demands a proactive and dynamic approach. Unlike traditional security measures, AI-powered cybersecurity solutions can swiftly detect and neutralize emerging threats by analyzing vast datasets in real time, effectively staying ahead of cybercriminal tactics.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Token Sprawl in the Age of AI
Published: 02/18/2026
Breaking Down the SOC 2 Trust Services Criteria: Privacy
Published: 02/18/2026
AI Security: IAM Delivered at Agent Velocity
Published: 02/17/2026
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026









