Survey Report: Cloud Security Posture Management and Misconfiguration Risks
Published 09/20/2021
 Written by VMware.
Written by VMware.
The worldwide public cloud services market grew 24.1% YoY in 2020.[1] With companies relying heavily on public clouds as the driver for digital transformation, the security of their cloud applications, data, and underlying infrastructure remains a top priority for Chief Information Security Officers. In a related report last year, the National Security Agency concluded that misconfiguration of cloud resources is the most prevalent of the cloud vulnerability types and the easiest to exploit to access cloud data and services.[2]
At VMware, we strive to help your company improve cloud security posture and better manage risk. Earlier this year, to add to the industry’s knowledge about public cloud security, we commissioned CSA to survey nearly 1,090 IT and Security professionals to drill deeper into this complex topic of misconfiguration risks.
Key research topics in the survey included:
- Current state of cloud security programs, including top risks and usage of security tools
- Cloud Security Posture Management (CSPM) challenges faced by organizations in mitigating misconfiguration vulnerabilities
- Organizational readiness, success metrics, and teams responsible for different aspects of cloud security posture management
- 1 in 6 companies (17% yes vs. 65% no) experienced a public cloud security breach or incident due to a cloud misconfiguration in the past year
- Lack of knowledge and expertise in cloud security best practices (62%) as well as lack of security visibility and monitoring capabilities (49%) are two primary causes of cloud misconfigurations
- Only 56% of respondents reported that their company can detect cloud misconfigurations in less than a day, and 37% reported that they can remediate cloud misconfigurations in less than a day
- 70% of respondents reported that their company’s cloud security, IT operations, and developer teams are not aligned on security policies and/or their enforcement strategies
- Respondents with better interdepartmental alignment on security policy and/or enforcement policies are more likely to be confident in their ability to defend against a security breach
From the results of the survey, key findings include:
1 in 6 Companies Experienced a Misconfiguration-Related Security Breach or Incident
Overall, misconfiguration mistakes continue to wreak havoc on business operations with over 1 in 6 companies (17% yes vs. 65% no) reporting that they experienced a public cloud security breach or incident due to a cloud misconfiguration in the past year. Let’s look at a few insights from the report that shine light on key challenges companies face in managing misconfiguration risks.
CSPM Challenge #1: Lack of Cloud Security Knowledge, Expertise, and Visibility
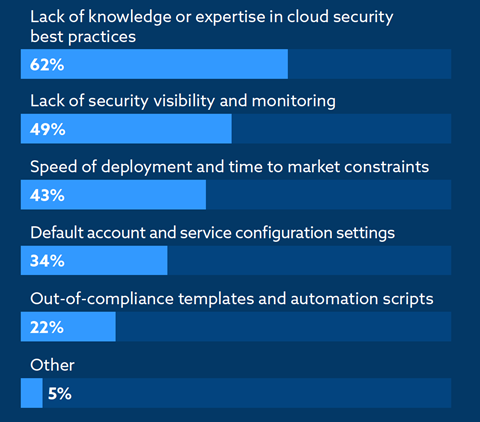
Lack of knowledge and expertise in cloud security best practices (62%) as well as lack of security visibility and monitoring capabilities (49%) were identified as two primary causes of cloud misconfigurations in most companies.
Scarcity of experienced cloud security professionals is no hidden secret in the industry. Often, in many companies, a single security professional is seen supporting hundreds of developers using public clouds. Additionally, with the onus of training the broader company on cloud security best practices often falling on central teams, shortage of cloud IT security experts can have an adverse cascading effect on a company’s cloud security posture.
Companies facing shortage of such skills must look at specialized CSPM solutions to augment and help their understaffed security teams scale cloud knowledge and best practices across the wider organization. With most CSPM solutions enabling standard cloud best practices and compliance frameworks out-of-the box, security teams can quickly help automate identification, reporting, and alerting of cloud misconfiguration risks to developer teams.
CSPM Challenge #2: Delay in Detection and Remediation of Cloud Misconfigurations
Length of Time to Detect Misconfigurations
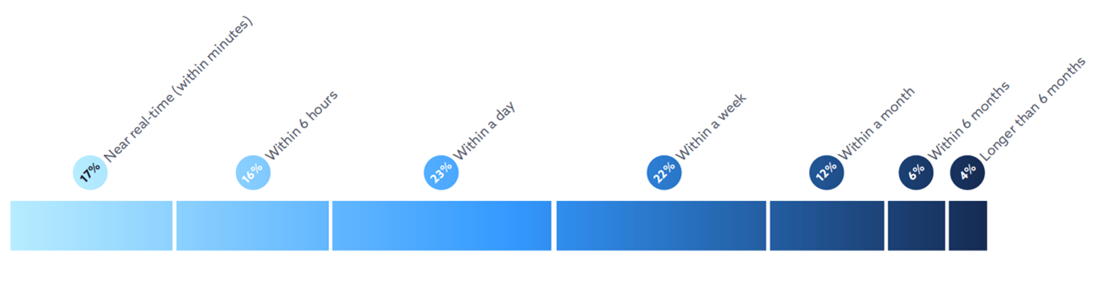
Length of Time to Remediate a Misconfiguration

56% of respondents reported that their company can detect cloud misconfigurations in less than a day, and 37% reported that they can remediate cloud misconfigurations in less than a day. While on paper, these statistics can look impressive, the long tail of companies that take longer to mitigate misconfiguration risks is extremely concerning.
Several honeypot experiments have revealed that attackers are becoming increasingly sophisticated and using automated techniques to exploit cloud vulnerabilities. 3 In a recent experiment, the security research team at Comparitech, created a simulation of a cloud server with fake data inside of it. The team found that the server was attacked 175 times during the 12-day experiment, with the first attack happening 8 hours and 35 minutes after deployment and subsequent attacks happening within minutes of the server being indexed by popular IoT search engines used by attackers. 3
The speed at which your company can detect and remediate misconfiguration mistakes goes a long way in determining how successful your security teams will be in preventing breaches that exploit misconfiguration vulnerabilities. When shortlisting solutions to build the foundation for your CSPM strategy, you should prioritize solutions that enable real-time security to outpace the speed of cloud infrastructure changes and automated techniques leveraged by criminals.
CSPM Challenge #3: Lack of Alignment Between Cloud Security, IT Operations, and Developer Teams
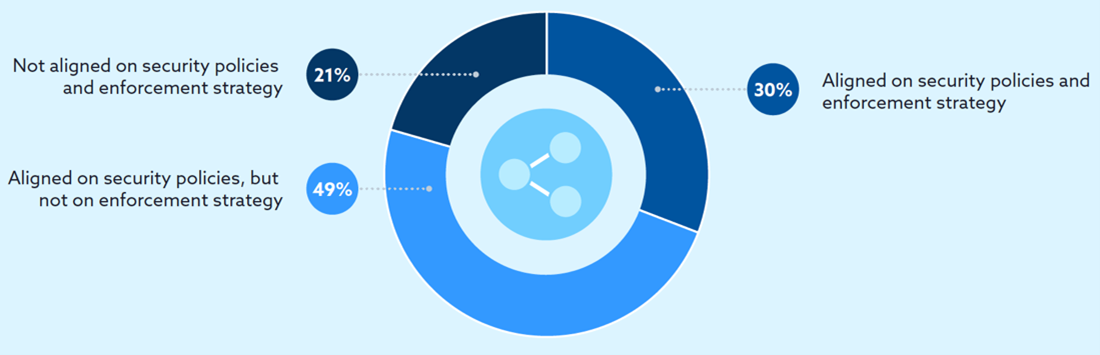
This brings us to one of the most crucial insights in the report. In the research, 70% of respondents reported that their company’s cloud security, IT operations, and developer teams are not aligned on security policies and/or their enforcement strategies. While identifying the right CSPM solution is foundational for building a successful cloud security program, it’s equally important to have a holistic plan for your cloud governance strategy.
This starts with clarifying people and teams’ security responsibilities, providing a forum for governance and developer teams to agree on company security standards and policies, and building a process to proactively identify and remediate misconfiguration risks. This also requires that the CSPM solution you choose is easy to operationalize and integrates without a lot of change management and tweaking of company security processes.
With improved alignment, the results are evident. Respondents who have better interdepartmental alignment on security policies and/or enforcement policies are more likely to report they are “extremely confident” or “very confident” in their ability to defend against a security breach (Extremely confident: full alignment – 15%, partial alignment – 2%, no alignment – 1%; Very confident: full alignment – 49%, partial alignment - 27%, no alignment –16%).
The Bottom Line
The research validates our belief at VMware that the key to helping companies better manage their multi-cloud security posture is to make it easy to operationalize cloud security and scale scarce cloud security resources, while enabling a deeper understanding of risks with intelligent insights, real-time detection, and more secure remediation capabilities.
To learn more about additional insights in the State of Cloud Security Risk, Compliance, and Misconfiguration report, please fill in a brief form and download the report here.
The State of Cloud Security Risk, Compliance, and Misconfigurations survey was conducted from May 2021 to June 2021 and gathered 1,090 responses from IT and security professionals located in the Americas (51%), Asia-Pacific (20%), and Europe, the Middle East, and Africa (29%). Please refer to the report for a complete breakdown of the survey demographics.
Sources:
- Worldwide Public Cloud Services Market Totaled $312 Billion in 2020 with Amazon Web Services and Microsoft Vying for the Top Position Overall, IDC, 13 May 2021
- Mitigating Cloud Vulnerabilities, National Security Agency, 22 Jan 2020
- Unsecured databases attacked 18 times per day by hackers, Comparitech, 10 June 2020
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates





.jpeg)