Know Your Cloud Security Acronyms: CWPP, CSPM, CIEM and CNAPP
Published 05/20/2022
 This blog was originally published by Orca Security here.
This blog was originally published by Orca Security here.
Acronyms help communicate lengthy phrases, but they can sometimes be confusing. This is especially true in the security industry, which has an alphabet soup of acronyms that can make even seasoned practitioners feel lost.
One of the new acronyms on the cloud security front is CNAPP, a term coined by Gartner which stands for Cloud-Native Application Protection Platform. With a new approach that simplifies cloud security, CNAPP is gaining attention because it combines multiple capabilities into one cloud security platform. A CNAPP secures the full application development lifecycle from code to production, and can replace tools such as Cloud Security Posture Management (CSPM), Cloud Workload Protection Platforms (CWPP), and Cloud Infrastructure Entitlement Management (CIEM), bundled into one platform.
Let’s dive into how all of these cloud security acronyms came into play, what each of these mean, and how CNAPP fits into the overall cloud security strategy.
How did we get here? A History of Cloud Security Technologies
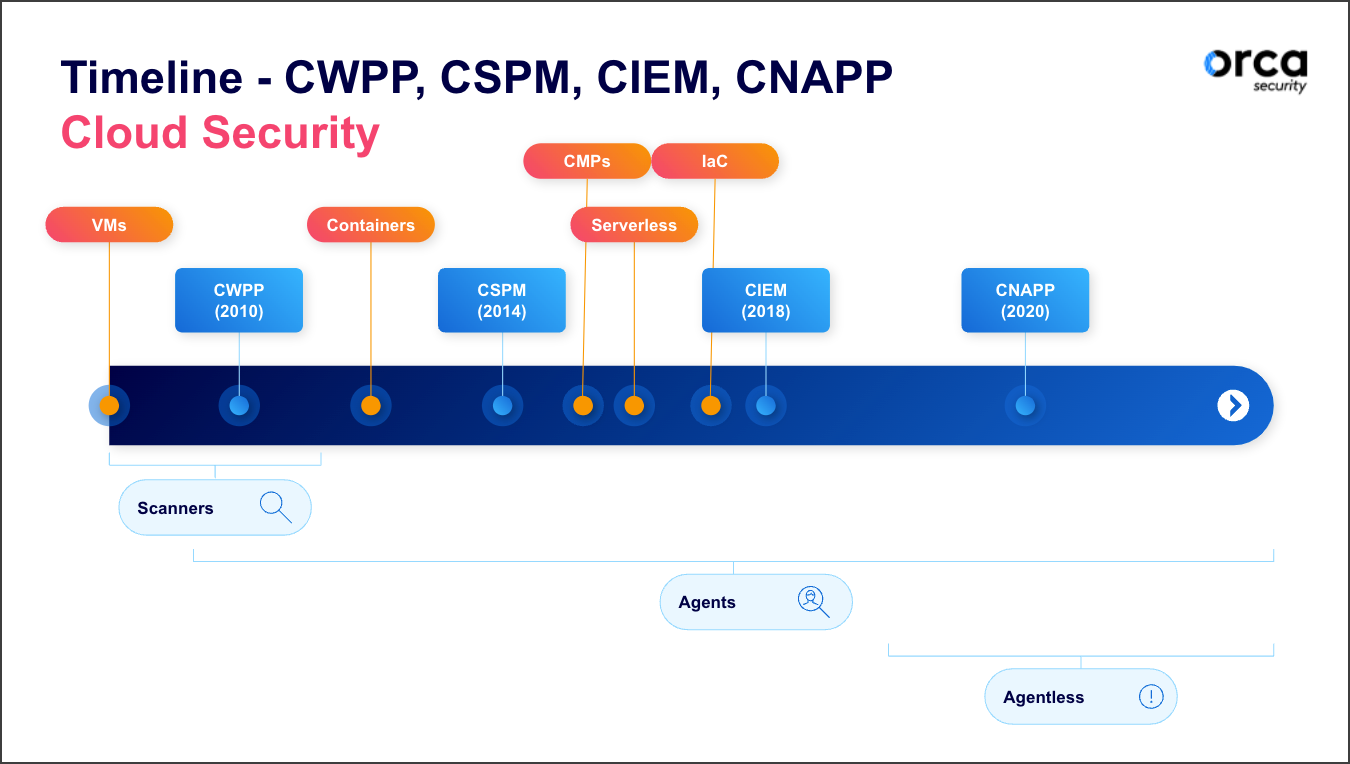
As organizations were looking for ways to minimize the overuse of limited (and expensive) on-premise technologies, they began virtualizing their IT infrastructure, substituting it with software and outsourcing it to service providers. As such, cloud security solutions were born out of necessity in the late 2000s in order to help organizations gain visibility and apply a layer of protection and security control to these new virtual environments.
Cloud security solutions needed to be defined for the marketplace. Gartner – a technological research and analyst firm – has led the process of defining market categories with cloud-related names, leading to a set of C-letter acronyms. In 2010, they defined the first category as the “Cloud Workload Protection Platform” (CWPP) that was intended to provide protection for the early adoption of virtual machines and containers.
Around 2014, when cloud service providers like AWS, Microsoft Azure, and Google Cloud began gaining popularity with their IT infrastructure as a service offerings (originally referred to as web services and now more commonly known as cloud computing), Gartner coined the new cloud security platform category “Cloud Security Platform Management” (CSPM). This technology helps organizations maintain the proper configurations of the cloud services that make up their cloud infrastructures in order to adhere to their part of the shared responsibility model of the public cloud.
A burst of cloud innovation occurred in the next four years, leading to identity anomalies in account entitlements and yet another category, called Cloud Infrastructure Entitlements Management (CIEM). By 2020, a new approach and innovation to remove the barriers of many siloed cloud solutions was born, bringing with it the need for the new acronym of CNAPP, which stands for Cloud Native Application Protection Platform. With the arrival of CNAPP technology, cybersecurity leaders can unify their technologies into one platform to detect, prioritize, and respond to security risks in the cloud.
What is a Cloud Workload Protection Platform (CWPP)?
According to Gartner, a Cloud Workload Protection Platform (CWPP) is a “workload-centric security solution that addresses the unique requirements of server workload protection in modern hybrid data center architectures that span on-premises, physical, and virtual machines (VMs), and multiple public cloud infrastructure as a service (IaaS) environments.” A CWPP deployment would ideally support container-based application architectures as well.
The purpose of CWPP technology is to secure server workloads in the public cloud. A CWPP solution discovers workloads that exist within an organization’s cloud-based deployments and on-premises infrastructure, offering a centralized solution for extending visibility into cloud resources in order to secure cloud workloads.
CWPP Summary
CWPP technology ensures public cloud workloads are secured, but it doesn’t cover all cloud security requirements. While CWPP solutions provide detailed visibility into what is happening inside the workloads, it lacks context and visibility to the connection between workloads, and the configuration of the infrastructure for which they reside.
| Capabilities | Challenges |
| Secure cloud and on-premise workloads: CWPPs discover workloads that exist within organizational cloud-based deployments and on-premises infrastructure and provide visibility into cloud resources and secure workloads. Granular, detailed visibility: CWPPs are great at gathering detailed information regarding vulnerabilities, sensitive information, malware scanning, asset versions, etc. that can be helpful when zooming into a workload. Runtime Protection: CWPPs can also provide file integrity monitoring (FIM), malware scanning, log inspection, app control and allow listing capabilities required to protect runtimes. Identity-based segmentation: CWPPs can provide techniques for enforcing policies based on application/workload identity, like tags and labels. Compliance for workloads: CWPPs can categorize their discovered risks into chosen compliance frameworks for easy and continuous reporting and auditing. | Agent-based: CWPPs require an individual agent to be installed and maintained for every asset to be secured, leading to slow deployment times, ongoing maintenance and organizational costs, and even impacts on asset performance. No insight into cloud control plane: CWPPs only cover workloads, they do not offer any insight into the control plane. For that, you would need to use a CSPM solution. Ineffective alert prioritization: CWPPs lack the visibility and context necessary to understand the full implications of a security issue. Without visibility into the cloud infrastructure, CWPPs alone can’t see the cloud estate in its entirety, and are unable to prioritize alerts based on environmental context. Partial coverage: It is virtually impossible to deploy agents everywhere, and when it is, agents are expensive to maintain. Agents are also not compatible with every operating system. For these reasons, CWPPs will inevitably have blind spots. Orca Security research shows that, on average, less than 50% of assets are covered by host cloud security solutions. In addition, agent-based CWPPs have no visibility into machines that are stopped, paused, or idle, leaving them vulnerable. No lateral movement risk detection: Attackers often try to get an initial foothold in the cloud environment and then laterally move towards their actual target. CWPPs alone are not able to identify which keys could provide attackers with access to other assets, leaving an important attack vector exposed. |
What is Cloud Security Posture Management (CSPM)
Cloud Security Posture Management (CSPM) is a market segment for cloud security tools that are designed to identify misconfiguration issues and compliance risks in the cloud. An important purpose of any CSPM solution is to continuously monitor cloud infrastructure for gaps in security policy enforcement.
CSPM platforms automate the identification – and in some instances the remediation – of risks across cloud infrastructures. Monitoring of the cloud infrastructure can be done through periodical queries that return a series of alerts about security policy or best practices violations. CSPMs provide organizations with centralized visibility and risk assessments of their entire cloud infrastructure.
CSPM solutions cover cloud environments and alert staff to misconfiguration mistakes that could expose the cloud environment to security risks or operational inefficiencies. In this way, CSPMs can also help organizations save money, identify important security risks, and educate teams for training.
CSPM Summary
CSPM solutions ensure public cloud services and configurations of the multi-cloud infrastructure are properly set. CSPM solutions are great for supplying cloud governance and cloud compliance for auditing, however, they lack depth of visibility into risks and threats beyond the cloud infrastructure, leaving gaps in coverage.
| Capabilities | Challenges |
| Security policy enforcement: CSPMs monitor misconfiguration issues, compliance risks, and enforce security policies in cloud environments. Multi-cloud configuration management: CSPMs are great for centralizing visibility of the entire cloud control plane (configurations) across multiple cloud service providers. Audits cloud control planes: CSPMs connect via API, allowing instant access and auditing of configurations across the entire control plane of multi-cloud environments. Provides compliance reporting for cloud infrastructures: CSPMs continually reviews and groups both proper and misconfigured findings into compliance frameworks that help organizations audit the proper management of their cloud infrastructure. Integrates with 3rd party threat intel: Most CSPMs digest native cloud service provider threat tools that can help further identify and prioritize and misconfiguration risks. | No insight into workloads: CSPM solutions are not able to go workload deep. For example, they don’t provide an alert if you have a vulnerable web server or an infected workload. For that, you would need a CWPP or CNAPP solution. Ineffective alert prioritization: CSPMs only consider the severity of a security issue, to determine priority. They can’t see the cloud estate in its entirety, and are therefore unable to prioritize alerts based on environmental context. No lateral movement risk detection: Attackers often try to get an initial foothold in the cloud environment and then move laterally towards their actual target. CSPMs are not able to identify which keys could provide attackers with access to other assets, leaving important attack vectors exposed or unidentified. |
What is Cloud Infrastructure Entitlements Management (CIEM)
A Cloud Infrastructure Entitlements Management (CIEM) solution identifies anomalies in account entitlements. IT and Security organizations use Cloud Infrastructure Entitlements Management (CIEM) solutions to manage identities and access privileges in public-cloud and multi-cloud environments. CIEM solutions apply the Principle of Least Privilege access to cloud infrastructure and services, helping organizations mitigate the risk of data breaches due to excessive entitlements.
Organization’s cloud environments can have hundreds of millions of discrete permissions granted to people, systems, and cloud services, and many of these may include unused permissions, non-federated accounts, and default and misconfigured permissions. Left unchecked, these permissions become an easy path for attackers to infiltrate cloud deployments. CIEM solutions allows your security team to govern which users (both human and non-human) can access which resources, across multiple clouds, services, users, and nonhuman entities.
CIEM Summary
CIEM solutions ensure identity access management (IAM) adhere to the principle of least privilege access to cloud infrastructures and services. CIEM capabilities have primarily focused upon IAM and entitlements risks and compliance. Although IAM has been suggested as the “new perimeter of cloud computing” – IAM and CIEM solutions still lack full security coverage of the cloud infrastructure and into the workloads.
| Capabilities | Challenges |
| Identity Access Management (IAM): CIEMs manage privileged identities with excessive permissions to cloud resources, and enforce least privilege at cloud scale. Audits multi-cloud access permissions: CIEMs continuously monitor and review all access permissions across multiple cloud service providers. Integrates with IdP (Identity Provider) solutions: CIEMs can work closely with Identity Providers to continue coverage from systems and cloud services to people with managed digital identities. Reports on entitlement risks and compliance: CIEMs supply visibility to risky or non-compliant cloud entitlements, which determine what tasks an identity can perform and which resources it can access across an organization’s cloud infrastructure Provides entitlement recommendations: CIEMs are also capable of understanding the entire cloud identity landscape, providing recommended best practices for policies and remediations to reduce access, enabling least-privilege. Least privileged permissions analysis: CIEMs not only enable least-privileged permissions, but they also ensure permissions are not over-administered as well. | Incomplete IAM: CIEMs can’t identify ‘alternative’ Identity & Access Management (IAM) mechanisms, such as SSH keys and AWS keys on the disk, and lateral movement risks. Gaps in Full Context and Visibility: Since CIEM solutions are primarily focused on defending “the new perimeter” of cloud – being Identity Access Management – CIEM solutions lack visibility into the control plane that CSPMs provide, as well as what is running within the actual workloads like CWPPs cover. |
What is a Cloud Native Application Protection Platform (CNAPP)?
A Cloud-Native Application Protection Platform (CNAPP) provides a holistic view of cloud security risks in one platform. As noted, a CNAPP integrates multiple cloud security capabilities, including CSPM, CWPP, and CIEM, with compliance and cybersecurity risk management.
Instead of siloed views, the right CNAPP solution provides full coverage and visibility into cloud estates and can detect risks across the tech stack, including cloud misconfigurations, insecure workloads, and mismanaged identity access. Furthermore, a CNAPP should incorporate ‘shift-left’ capabilities to identify risks earlier in the development lifecycle. By combining vulnerabilities, context, and relationships, some CNAPPs are able to perform cloud attack path analysis, recognizing how seemingly unrelated low severity risks can be combined to create dangerous attack vectors.
When an agentless CNAPP is deployed, the platform solves a number of problems that security teams are facing today with cloud security, including:
- Provides agentless coverage to address cloud security gaps that traditional agent-based tools cannot
- Offers complete visibility on all workloads for cloud-native services, such as managed containers and serverless functions
- Removes agent-related operational costs require to deploy and maintain agents and scanners
- Relieves cloud alert fatigue caused by ineffective risk prioritization
- Centralizes cloud security insights into one platform with holistic context, heuristic detections, analytics, reporting, and remediation guidance for security teams. Tools for cloud security posture management, cloud security workload protection, cloud vulnerability management, cloud infrastructure entitlements management, and cloud compliance can be consolidated – and expensive costs avoided – with the right CNAPP.
CNAPP Summary
The CNAPP is advantageous in a number of ways, with the key benefit of increasing visibility to the cloud. In Innovation Insight for Cloud-Native Application Protection Platforms Report, Gartner, Inc., notes, “The most significant benefit of a CNAPP approach is better visibility and control of cloud-native application risk.”
| Capabilities | Challenges |
| Manage misconfiguration risks: Reduce the chance of misconfigurations, mistakes, or security mismanagement of cloud-native applications. Consolidate security investments: Reduce the number of tools and vendors. Streamline governance and compliance: Reduce the complexity and costs associated with creating secure and compliant cloud-native applications. Prioritize critical alerts: Allow security departments to understand attack paths based on relationships—security vulnerabilities, misconfigurations, permissions, exposed secrets—that would enable an attacker to target an application. Increase DevSecOps visibility: Bi-directionally link development and operations visibility and insight into risk analysis to improve the overall enterprise security posture | Overlapping capabilities: An organization may have legacy cloud security systems that they cannot remove – some of these are noted below. With time, security leaders can remove these barriers by updating the cloud strategy and removing redundant technology when contracts expire. |
Evaluate CNAPP for Next-Generation Cloud Security
The evolution of cloud-native security opens up new opportunities for organizations to accelerate growth and generate revenue – without sacrificing security and compliance. Rather than deploying, analyzing and correlating multiple point solutions – leaving your team or organization with gaps in coverage or context – save time and gain insights into risks and attack paths that are only possible with a centralized CNAPP solution.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Why Zero Trust Needs to Start at the Session Layer
Published: 02/19/2026
Token Sprawl in the Age of AI
Published: 02/18/2026
AI Security: IAM Delivered at Agent Velocity
Published: 02/17/2026
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026


.png)



