The State of Remote Work Offboarding Security
Published 08/01/2022
 Written by Marie Prokopets, Co-founder and COO, Nira.
Written by Marie Prokopets, Co-founder and COO, Nira.
As companies switch to remote, distributed, and hybrid workforces, security risks related to offboarding have grown. When employees leave or change roles, organizations must protect their sensitive data from accidental or malicious data exfiltration and breaches which can cause harm to both revenue and reputation.
We wanted to learn more about what companies are doing to keep their company information secure while offboarding employees in a remote work environment.
To do so, Nira worked with Gartner Peer Insights to survey IT and security professionals about how offboarding has been affected during the COVID-19 pandemic, their most significant security threats, and their future priorities for offboarding processes.
Offboarding processes have changed and become more demanding in a remote workforce
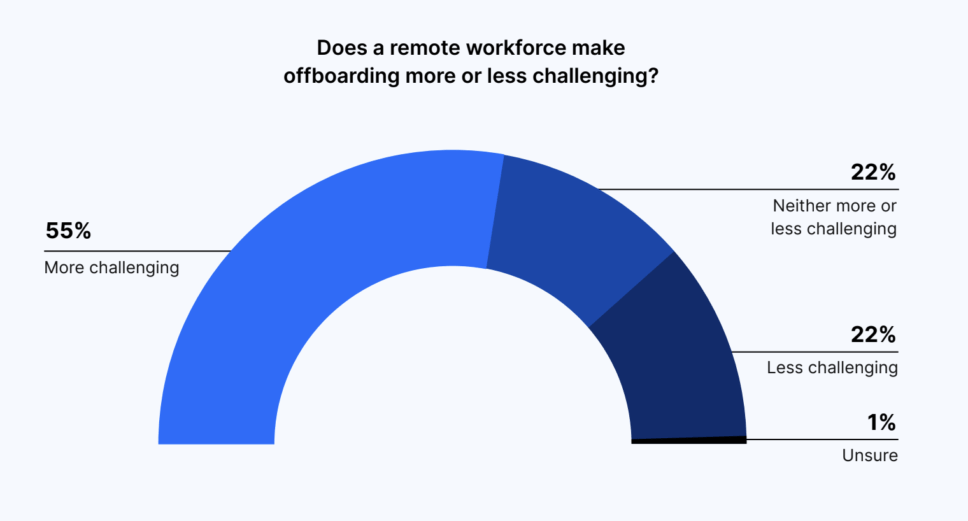
Fifty-eight percent of executives said offboarding processes have changed as a result of needing to support a remote workforce. And 55% of IT and security professionals described remote offboarding as more challenging.
Offboarding was seen as a significant security threat—and access privileges were the biggest concern
Seventy-six percent of IT and security executives said that employee offboarding represents a significant security threat.
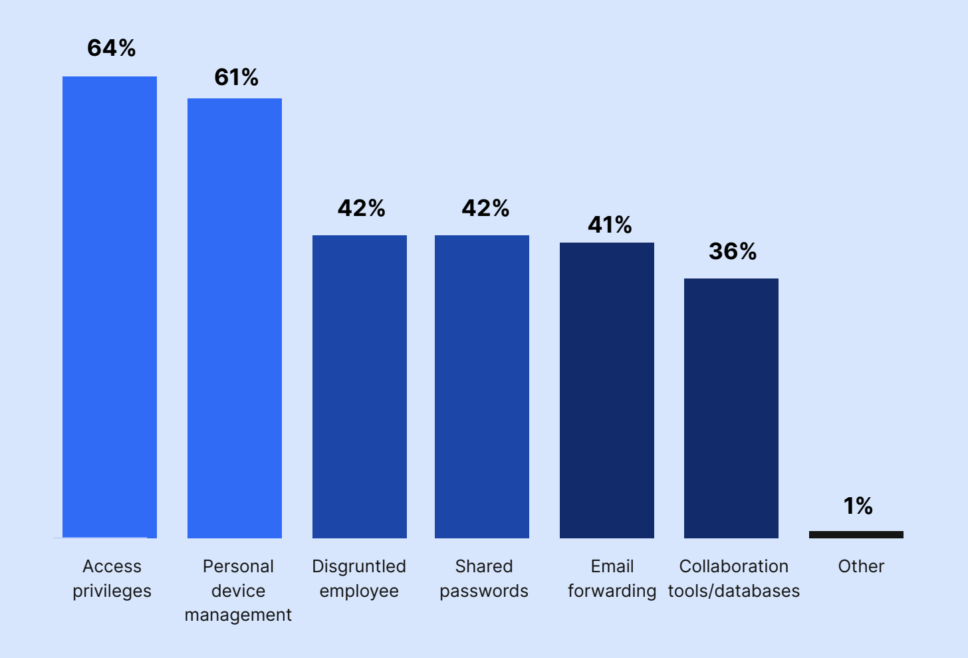
Access privileges (64%) and personal device management (61%) were viewed as the largest threats to offboarding.
Other IT and security professionals mentioned shared passwords (42%), disgruntled employees (42%), email forwarding (42%), and collaboration tools/ databases (36%) as potential issues.
What do you think are the biggest security threats with the offboarding process?
Most offboarding security breaches are caused by accident
When it comes to employees, most executives did not view them as intentionally trying to sabotage or harm the company.
Two-thirds (67%) of leaders said that employees who leave the organization are more likely to cause security breaches by accident, rather than on purpose.
This is on track with past research that shows 80% of access-risk incidents are not malicious.

Although most employees are not maliciously stealing or sharing information, that doesn’t make the risk caused by accidental breaches any less real or costly for companies.
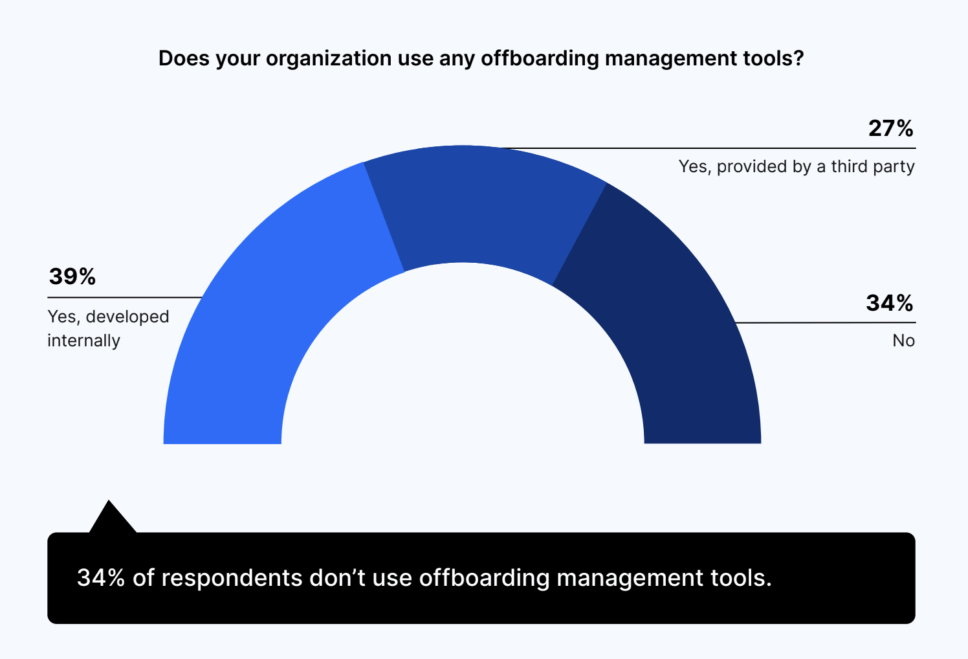
To combat unauthorized access to company information, companies may turn to offboarding management tools.
Two-thirds of companies use offboarding management tools; nearly 40% develop their own tools; while 27% rely on third parties. Meanwhile, 34% of respondents admitted to not using offboarding management tools at all.
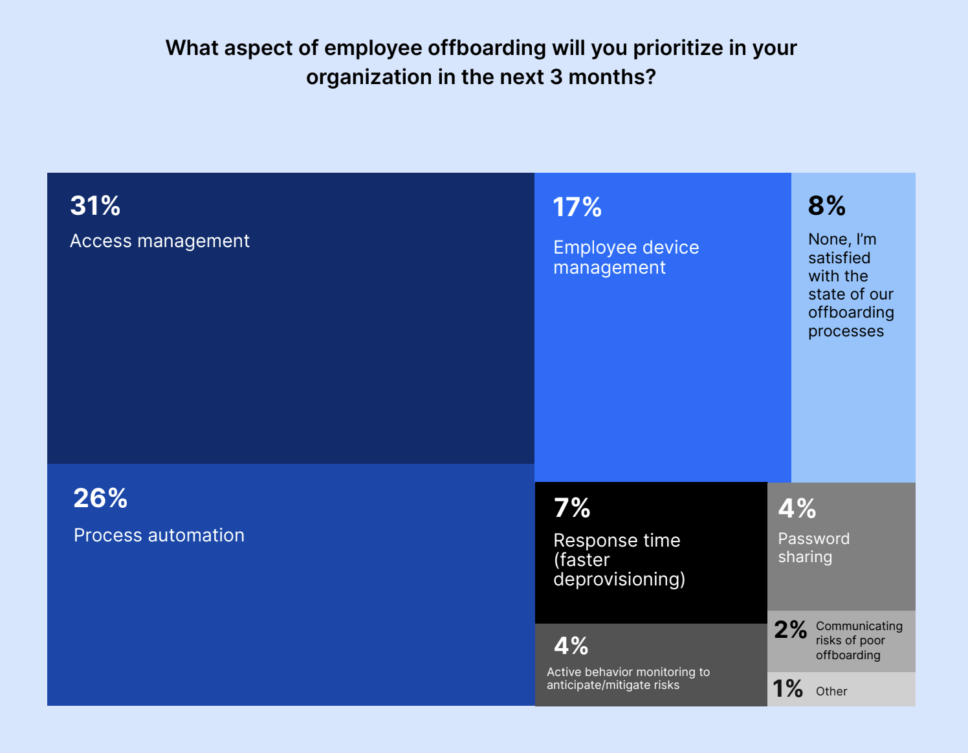
Access management remains a priority over the next quarter
Over the next three months, IT and security leaders said they were prioritizing access management (31%) followed by process automation (26%) during employee offboarding. Meanwhile, 17% were interested in employee device management and 7% in response time (faster deprovisioning).
While the majority of executives (92%) wanted to prioritize offboarding security, 8% of executives were satisfied with the overall state of their offboarding processes and had zero plans to change their offboarding processes over the next quarter.
When an employee leaves an organization, a comprehensive offboarding process can help mitigate the risk of company information being accessed by former coworkers or other unauthorized parties.
This is especially vital in a remote or hybrid environment, where company data is available on personal accounts and devices. Methods like using an access control system make this process quick and easy while at the same time helping keep your data safe. For the full survey on the state of offboarding security for remote work, visit here.
About the Author
Marie Prokopets is the Co-founder and COO of Nira, a real-time access control system designed to protect cloud-based company information from unauthorized access. She previously worked at Diageo, where she focused on innovation, M&A, and strategy. She also spent time at PwC working with Fortune 500 companies and private equity firms on their corporate strategy and acquisitions.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates




