What Is a Feistel Cipher?
Published 10/11/2022
 Originally published by TokenEx here.
Originally published by TokenEx here.
Written by Valerie Hare, Content Marketing Specialist, TokenEx.
Quick Hits:
- Feistel cipher is a design model designed to create different block ciphers, such as DES.
- The model uses substitution and permutation alternately.
- This cipher structure is based on the Shannon model proposed in 1945.
What Is a Feistel Cipher?
The Feistel cipher is a design model or structure used to build various symmetric block ciphers, such as DES. This design model can have invertible, non-invertible, and self-invertible components. Additionally, the Feistel block cipher uses the same encryption and decryption algorithms.
The Feistel structure is based on the Shannon structure proposed in 1945, demonstrating the confusion and diffusion implementation processes. Confusion produces a complex relationship between the ciphertext and encryption key, which is done by using a substitution algorithm. On the other hand, diffusion creates a complex relationship between plain text and cipher text by using a permutation algorithm.
The Feistel cipher proposed the structure that implements substitution and permutation alternately. Substitution replaces plain text elements with ciphertext. Permutation changes the order of the plain text elements rather than being replaced by another element as done with substitution.
Feistel Cipher Encryption Example
The Feistel cipher encryption process involves numerous rounds of processing plain text. Each round includes the substitution step and then the permutation step. Check out the following example describing the encryption structure used for this design model.
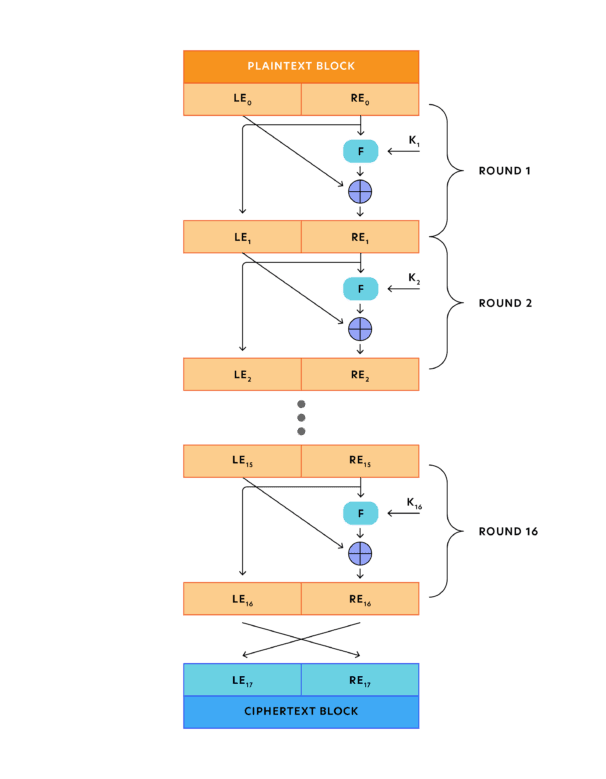
- Step 1 – The first step involves the plain text being divided into blocks of a fixed size, with only one block being processed at a time. The encryption algorithm input consists of a plain text block and a key K.
- Step 2 – The plain text block is divided into two halves. The left half of the plain text block will be represented as LE0, and the right half of the block will be RE0. Both halves of the plain text block (LE0 and RE0) will go through numerous rounds of processing plain text to produce the ciphertext block.
For every round, the encryption function is applied on the right half REi of the plain text block plus the key Ki. The function results are then XORed with the left half LEj. XOR is a logical operator used in cryptography that compares two input bits and produces one output bit. The XOR function results become the new right half for the next round RE i+1. The previous right half REi becomes the new left half LEi+1 for the next round.
Every round will execute the same function, in which a substitution function is implemented by using the round function to the right half of the plain text block. The result of this function is XORed by using the left half of the block. Then, a permutation function is used by switching the two halves. The permutation results are provided for the next round. Indeed, this is how the Feistel cipher model implements the substitution and permutation steps alternately, similar to the Shannon structure mentioned above.
Feistel cipher design features that are considered when using block ciphers:
- Block size – Block ciphers are considered more secure when the block size is larger. Though, larger block sizes reduce the execution speed for the encryption and decryption process. Typically, block ciphers have a block size of 64-bits, but modern blocks like AES (Advanced Encryption Standard) are 128-bits.
- Easy analysis – Block ciphers should be easy to analyze, which can help identify and address any cryptanalytic weaknesses to create more robust algorithms.
- Key size – Like the block size, larger key sizes are considered more secure at the cost of potentially slowing down the time it takes to finish the encryption and decryption process. Modern ciphers use a 128-bit key, which has replaced the earlier 64-bit version.
- The number of rounds – The number of rounds can also impact the security of a block cipher. While more rounds increase security, the cipher is more complex to decrypt. Thus, the number of rounds depends on a business's desired level of data protection.
- Round function – A complex round function helps boost the block cipher's security.
- Subkey generation function – The more complex a subkey generation function is, the more difficult it is for expert cryptanalysts to decrypt the cipher.
- Quick software encryption and decryption – It's helpful to use a software application that can help produce faster execution speeds for block ciphers.
Feistel Cipher Decryption Example
It may be surprising that the Feistel cipher model uses the same algorithm for encryption and decryption. There are a couple of key rules to consider during the decryption process:
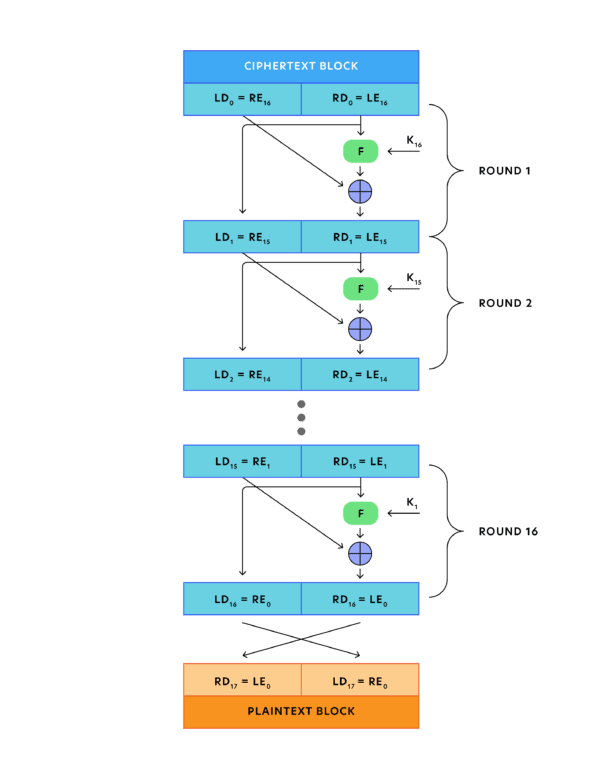
As shown in the figure above, the cipher text block contains two halves, the left (LD0) and the right (RD0).
Like the encryption algorithm, the round function is executed on the right half of the cipher block with the key K16. The function's result is XORed with the left half of the cipher text block. The XOR function's output becomes the new right half (RD1), while RD0 switches with LD0 for the next round. Indeed, every round uses the same function, and once the fixed number of rounds is executed, the plain text block is achieved.
Final Points
The Feistel cipher is a well-known cryptography design model that organizations can use to help secure their sensitive data. Even if a hacker knows the cipher algorithm, a strong encryption cipher should prevent the criminal from deciphering the cipher plain text without having the key or sets of keys. In addition to this cipher model, businesses should adopt a layered cybersecurity strategy to help prevent threat actors from stealing or exposing their sensitive information. Tokenization is an effective solution that replaces original data with unique, randomly generated numbers called tokens. Tokenized data can be stored and managed via a secure cloud platform. If a breach impacts an organization, hackers will only be left with tokens that lack valuable information.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Achieving Resilience Through Zero Trust
Published: 08/29/2025
The Emerging Identity Imperatives of Agentic AI
Published: 08/28/2025
Risk-Based vs. Compliance-Based Security: Why One Size Doesn’t Fit All
Published: 08/27/2025
"Set It and Forget It” Access Control is No Longer Enough
Published: 08/20/2025




.jpeg)
.jpeg)
.jpeg)