What is FedRAMP? Complete Guide to FedRAMP Authorization and Certification
Published 11/07/2022
Originally published by A-LIGN.
Written by Tony Bai, Federal Practice Lead, A-LIGN.
With the rise in cybersecurity attacks comes wariness from customers — no one wants to work with an organization that has an increased risk of falling victim to an attack. And when it comes to the Federal government, that rings especially true.
The Federal government has put measures into place to help mitigate risk when working with partner organizations. In fact, these organizations are required to maintain certain cybersecurity standards and authorizations in order to do business with the Federal government.
One of those requirements is the Federal Risk and Authorization Management Program, also known as FedRAMP. In this post, we’ll provide you with everything you need to know about the FedRAMP authorization process.
What is FedRAMP?
With cyberattacks and cloud-based technologies on the rise, federal departments and agencies needed a cost-efficient and risk-based approach to cloud adoption.
This led to the creation of the Federal Risk and Authorization Management Program (FedRAMP) in 2011. FedRAMP provides a standardized approach to security assessment, authorization, and continuous monitoring specifically for cloud products and services used by federal entities that store, process, and transmit federal information.
What is the goal of FedRAMP?
As a government cybersecurity framework, the goal is to accelerate the adoption of secure cloud solutions through the use of assessments and authorizations. For organizations that achieve FedRAMP authorization, it’s a powerful validation of the security of the organization’s cloud solution.
Why is FedRAMP important?
FedRAMP increases confidence in the security of cloud solutions through continuous monitoring and consistent use of best information security practices and procedures. This streamlined, regulated approach helps mitigate the risk of cyberattacks.
Who needs FedRAMP Authorization?
Federal agencies that host their technology in the cloud are required to use a FedRAMP certified Cloud Service Provider (CSP). If you are looking to do business with the government and host federal systems, then FedRAMP applies to your environment, and you will need authorization.
What are the key benefits of FedRAMP Authorization?
Becoming authorized offers CSPs many benefits, including:
- Improved real-time security visibility
- A uniform approach to risk-based management
- Significant savings on cost, time and resources by de-duplicating efforts related to meeting federal cybersecurity requirements
- Increased re-use of existing security assessments across agencies
- Enhanced transparency between government and CSPs
- Improved trustworthiness, reliability, consistency and quality of the Federal security authorization process
Does FedRAMP apply to global organizations?
Yes. Many global organizations are seeking to secure new business deals to strengthen their customer base. If international businesses want to sell a cloud service offering to the U.S. government, they should pursue FedRAMP authorized status.
Why is FedRAMP Authorization valuable to cloud service providers (CSPs)?
Federal cloud spending has seen a rise in recent years. In fact, analysis from Deltek found that federal cloud spending reached nearly $11 billion in FY 2021, up more than 40% from the $7.6 billion spent in 2019. CSPs looking to capitalize on this trend should seek to achieve FedRAMP Authorized status.
FedRAMP can also be reused to sell to multiple agencies. In fact, if you already have authorization, it can simplify the certification process for other federal and defense programs, like the DoD’s Cloud Computing Security Requirements Guide (CC SRG)
Who can perform a FedRAMP assessment?
Only accredited FedRAMP Third Party Assessment Organizations (3PAO) may perform FedRAMP assessments.
How do I get FedRAMP certified?
FedRAMP is an integrative standardized assessment designed to be a common one-stop-shop for CSPs seeking to do business with the U.S. government.
There are two paths CSPs can take to achieve authorization:
- Through an agency sponsorship when a government entity vouches for a CSP, streamlining their approval process.
- Through the Joint Authorization Board (JAB). The JAB is the primary governance and decision-making body for FedRAMP.
Although organizations are able to choose which process they’d prefer to take, most organizations choose to achieve certification via agency sponsorship. This is because the JAB path is very competitive as they only select 12 systems per year (specifically, three per quarter).
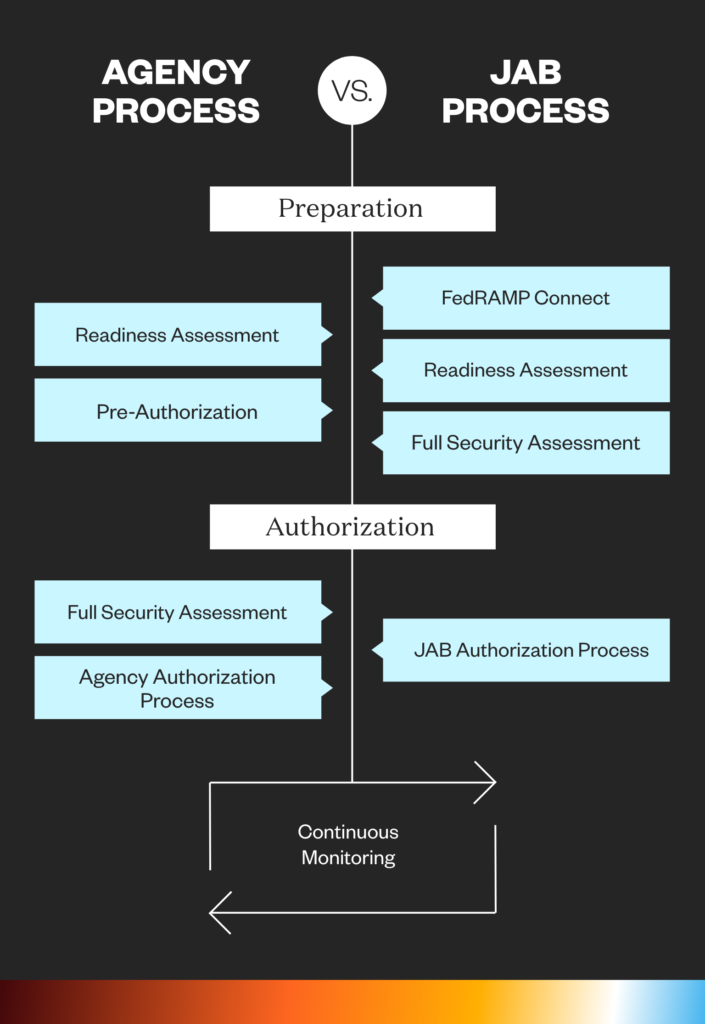
What is JAB P-ATO Status?
The JAB is the primary governing body for FedRAMP and includes the Department of Defense (DoD), Department of Homeland Security (DHS), and General Services Administration (GSA). The JAB selects approximately 12 cloud products a year to work with for a JAB Provisional Authority to Operate (P-ATO).
The JAB Authorization process involves:
- An evaluation via FedRAMP Connect
- Completing a FedRAMP Ready assessment
- Completing a full-security assessment
- Achieving authorization via the JAB
- Continuous monitoring post-authorization
What is Agency ATO Status?
In the Agency Authorization path, agencies may work directly with a CSP for authorization at any time. CSPs that make a business decision to work directly with an agency to pursue an ATO will work with the agency throughout the FedRAMP Authorization process.
The Agency Authorization process involves:
- An optional, yet highly recommended, FedRAMP Ready assessment
- Pre-authorization
- Achieving agency authorization
- Continuous monitoring post-authorization
What are the key processes involved with a FedRAMP Assessment and Authorization?
Regardless of which method (agency sponsorship vs. JAB) you choose, the authorization process always involves:
- A Preparation Phase, where the provider completes a System Security Plan (SSP). After this, a FedRAMP-approved third-party assessment organization (3PAO) will develop a Security Assessment Plan.
- A Full Security Assessment, where the assessment organization submits a Security Assessment report and the provider creates a Plan of Action & Milestones PoAM). The security assessment involves evaluating a company’s policies and procedures against a set of requirements from the NIST 800-53 controls to test security authorizations. Once granted, continuous assessment and authorization guidelines must be in place to uphold authorization.
- Authorization, where the JAB/authorizing agency determines whether the risk as described is acceptable. If confirmed, they submit an ATO letter to the FedRAMP project management office. The provider is then listed in the FedRAMP Marketplace.
- Continuous Monitoring, where the provider sends monthly security monitoring deliverables to each organization using the service.
What’s the timeline of a FedRAMP Assessment?
Step 0: It’s recommended you complete a gap assessment to address any holes in your environment. This ensures a CSP is ready for the FedRAMP authorization assessment to be submitted for FedRAMP Authorized status.
Step 1. Pre-Assessment Review (1-4 Weeks)
Step 2. Planning Activities (4 Weeks)
Step 3. Assessment Activities (7 weeks)
Step 4. Reporting Activities (5 weeks)
Step 5. Sponsor Issues Authority to Operate (2-3 weeks)
Step 6. Maintain Authorization
How long is FedRAMP valid?
A FedRAMP Ready designation is only valid on the Marketplace for twelve months.
What are the impact levels of FedRAMP compliance?
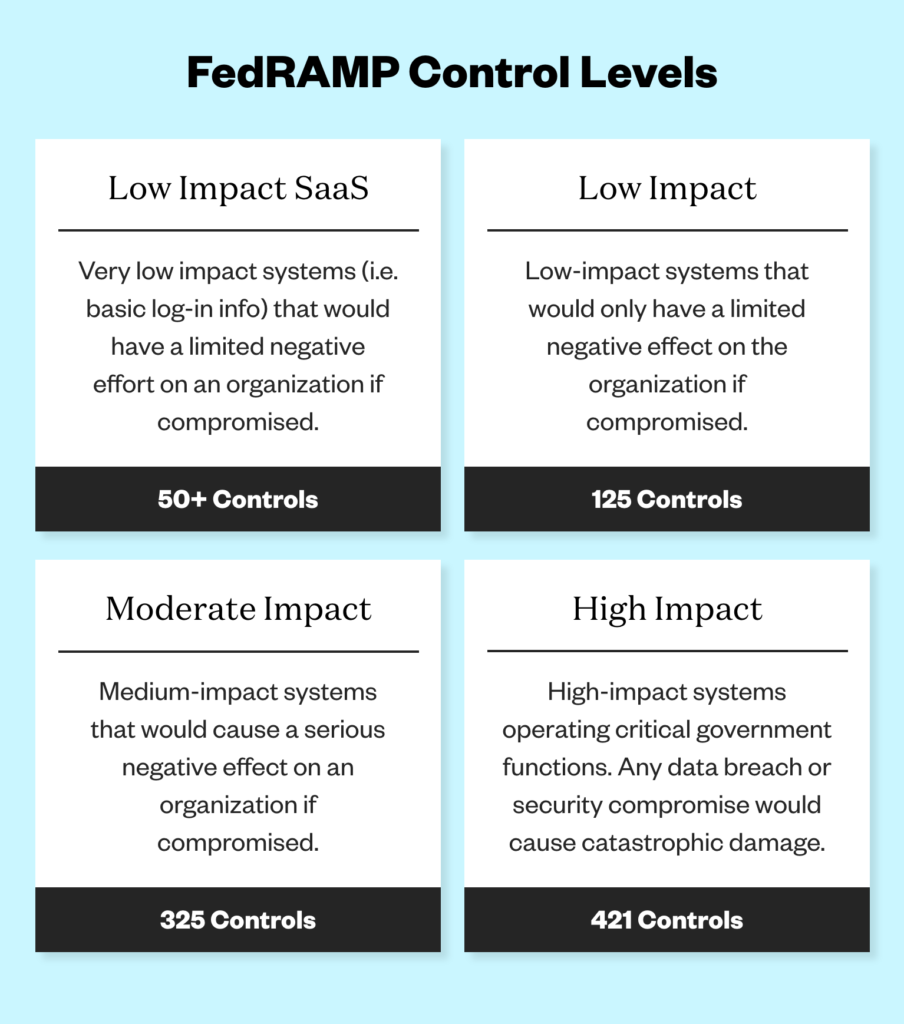
Low Impact SaaS (FedRAMP Tailored or Ll-SaaS): Ll-SaaS is a subset of low impact and typically includes 50+ of the controls to be independently assessed. This baseline accounts for SaaS apps that do not store personal identifiable information beyond basic log-in information, like usernames and passwords. Organizations that achieve the LI-SaaS level would experience minor adverse effects should a loss of confidential information occur. Information about the security controls required for this designation can be found here.
Low Impact Level: Low includes about 125 controls. Organizations that achieve the low authorization status would experience limited adverse effects if a loss of confidential information occur.
Moderate Impact Level: Moderate includes about 325 controls and the vast majority of organizations fall into this category. The loss of confidential information in this category would have a serious impact on an organization.
High Impact Level: High includes approximately 425 cybersecurity controls and mainly includes organizations that work in law enforcement and emergency services systems, financial systems, and health systems. Organizations should especially pursue High impact if any loss of confidential information could be expected to have a catastrophic impact.
Please note, the number of controls for each impact level are currently based on NIST 800-53 revision 4 and will change with the transition to revision 5. The transition plan and associated templates and guidance is expected to release by end of 2022.
For more information about the security controls required for each designation, click here.
FedRAMP vs. FISMA/NIST RMF
Prior to FedRAMP, the U.S. government introduced the Federal Information Security Modernization Act of 2014, or FISMA.
FISMA is the law directing government agencies to develop and maintain an information security program. FedRAMP is a cloud-specific implementation of NIST RMF. Even though FISMA and FedRAMP use the same standard, utilizing the same controls set within NIST 800-53, the two have different authorization processes.
In order to bring together all of the FISMA-related security standards, NIST created the Risk Management Framework. Whereas FISMA establishes the requirements of an agency’s cybersecurity program, RMF helps determine how that program should review, assess, and approve IT systems for use.
What’s the difference between FedRAMP and StateRAMP?
StateRAMP can be thought of as FedRAMP for state and local governments, and it has a Security Assessment Framework that is based on the National Institute of Standards and Technology Risk Management Framework (NIST RMF).
StateRAMP offers a fast track to authorization for current FedRAMP authorized services.
Is continuous monitoring needed for FedRAMP?
Yes. Monthly updates (scans and POA&Ms) to the Agency Sponsor or JAB (based on authorization pathway) are important to ensure your organization has maintained compliance with FedRAMP. Annual assessments that include penetration testing, select control assessment, system scanning, and more are critical to your continued compliance standing.
If your organization has experienced any significant changes that will impact your compliance standing, you’ll need your agency or JAB to review and assess through a Significant Change Request Assessment.
What are FedRAMP key terms?
Check out our FedRAMP compliance glossary of terms to learn the definitions for Third Party Assessment Organizations (3PAO), authority to operate (ATO), cloud service provider (CSP), Federal Information Security Modernization Act (FISMA), joint authorization board (JAB), National Institute of Standards and Technology (NIST) and more.
What are the common challenges of FedRAMP authorization?
- CSPs Might Not Know Authorization Is a Detailed Process: FedRAMP security standards are more prescriptive than general security assessment and requires granular detail.
- CSPs Might Overlook the Benefits of Control Inheritance: Inheriting as many security controls as possible from your CSP organization’s underlying FedRAMP authorized infrastructure provider will save time and resources.
- Organizations Underestimate the Power of Automation: Compliance automation software can help automate and streamline your authorization process.
What’s new with FedRAMP?
The FedRAMP Rev 5 Baselines: The final Rev 5 baselines and transition plan to Rev 5 are expected in early 2023. The biggest difference between the Rev 4 and Rev 5 baselines is that FedRAMP has introduced a threat-based methodology to determine which controls should be added on to the established NIST 800-53 Rev 5 baselines.
The Updated Readiness Assessment Report (RAR): A RAR is what CSPs use to determine if they are ready to undergo the extensive FedRAMP authorization process. In a thorough 19-page document, FedRAMP provided updated guidance as well as templates for 3PAOs evaluating CSPs for readiness.
Helpful FedRAMP Resources
What is FedRAMP and Why Does My Organization Need It?
Federal Compliance Definitions: A Glossary of Terms
3 Tips to Prepare for FedRAMP Authorization
Beginning the Authorization Process
FedRAMP can help organizations win more business and stand out from their competition, but the approval process is detailed.
As a CSP, you must implement the appropriate controls before you can begin the FedRAMP authorization process. Whether you seek authorization via an agency or through the JAB, it is important to ensure you have a trusted resource to help guide you through the process.
 About the Author
About the Author
Mr. Bai is a cybersecurity professional with a range of certifications. As the Federal Practice Lead at A-LIGN, Mr. Bai supports all FedRAMP, FISMA, NIST 800-171 and other NIST-based projects. He is responsible for overseeing all NIST-based engagements and providing security controls advisory and guidance to our clients. Mr. Bai has hands-on experience leading all stages of system security, including requirements definition, auditing, scanning, and mitigation. With over 27 years of information systems experience to include 10 years specializing in cybersecurity. His extensive background includes providing risk assessments of information systems for government agencies and commercial clients. Mr. Bai brings an impressive blend of knowledge of security controls and technical aspects of cybersecurity and IT operations.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
What is a Risk Engineer?
Published: 03/02/2026
OpenClaw Threat Model: MAESTRO Framework Analysis
Published: 02/20/2026






