SANS 2022 Cloud Security Survey, Chapter 2: What Security and Compliance Worries Do IT Pros Have About the Cloud?
Published 12/14/2022
Originally published by Gigamon.
Written by Chris Borales, Gigamon.
Editor’s note: This post explores Chapter 2 of the SANS 2022 Cloud Security Survey. Chapter 1 is available here. Check back for future posts covering Chapters 3 and 4.
The cloud is sold more and more as the answer to what ails IT, promising eternal uptime and helping to replace costly capacity spending on in-house infrastructure with a more modest monthly operating expense. But what about security? Should corporate IT departments trust that their cloud provider has security problems in hand — or will those problems still keep them up at night?
According to the SANS 2022 Cloud Security Survey, IT pros are worried about cloud security — and with good reason. In our first post in this blog series, we looked at how those survey respondents use cloud services in the real world.
In this post covering Chapter 2, you’ll see how different data protection laws affect cloud usage and migration, and learn about what security threats loom — the ones that users really encounter, and the ones they fear are lurking out there.
The Cloud and the Law
SANS asked its respondents what types of sensitive data they were storing in the cloud in order to understand how users thought about cloud services’ security and regulatory exposure. The results are in Figure 1.
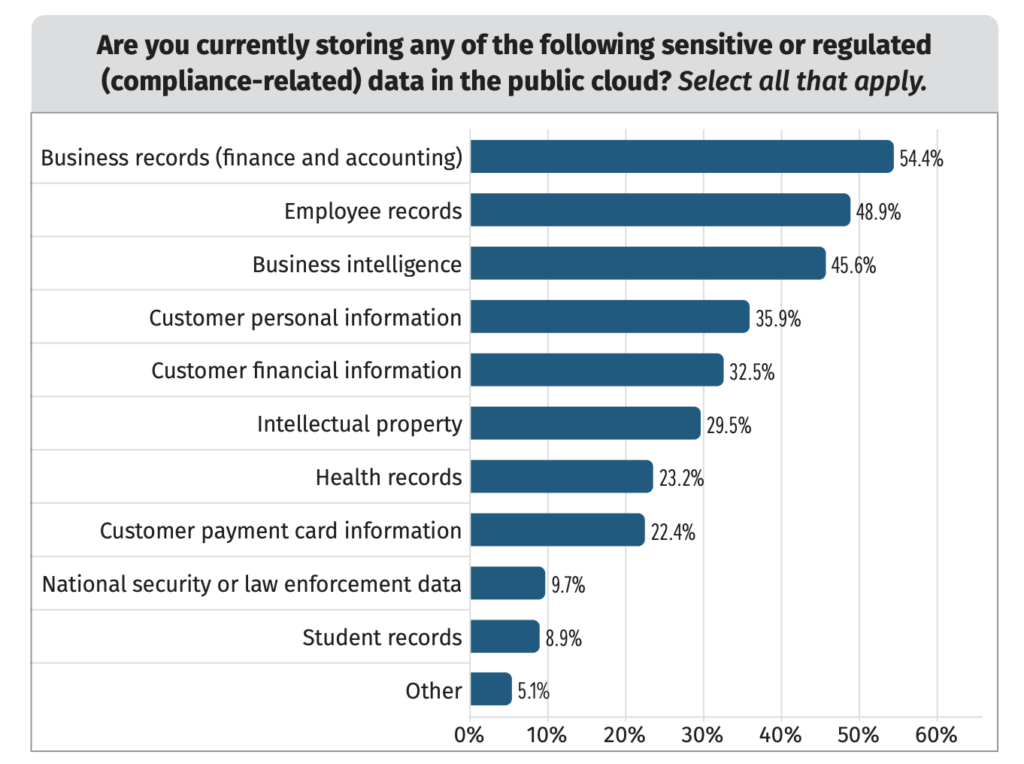
Figure 1. Sensitive data in the cloud.
While the specific ranking of types of data has changed a bit over previous surveys, the general trend has not. About half of surveyed organizations are willing to put a variety of sensitive data types in the cloud. That number plunges when you start talking about data that is more tightly regulated: Less than a quarter of respondents are storing health records or credit card info in cloud-based systems.
If you’re going to store consumer personal data in the cloud, you make sure your providers will comply with privacy regulations, and that’s leading to respondents’ hesitancy in this area. A whopping 62 percent said that privacy laws like the GDPR are having an impact on their cloud strategies; that’s up from 55 percent in 2021, and that trend is likely to continue.
Fears of the Known and Unknown
One question SANS asks in its survey is: “What sorts of cloud security incidents are you concerned about, and what sort of incidents actually happen to your organization?” The results are illustrated in Figure 2. Just over half were worried about unauthorized application components or compute instances being installed on their cloud instances; poorly configured interfaces and APIs; and an inability to respond to incidents. However, the most common difficulties that were actually experienced were downtime, lack of proper in-house skills, and unauthorized access by outsiders.
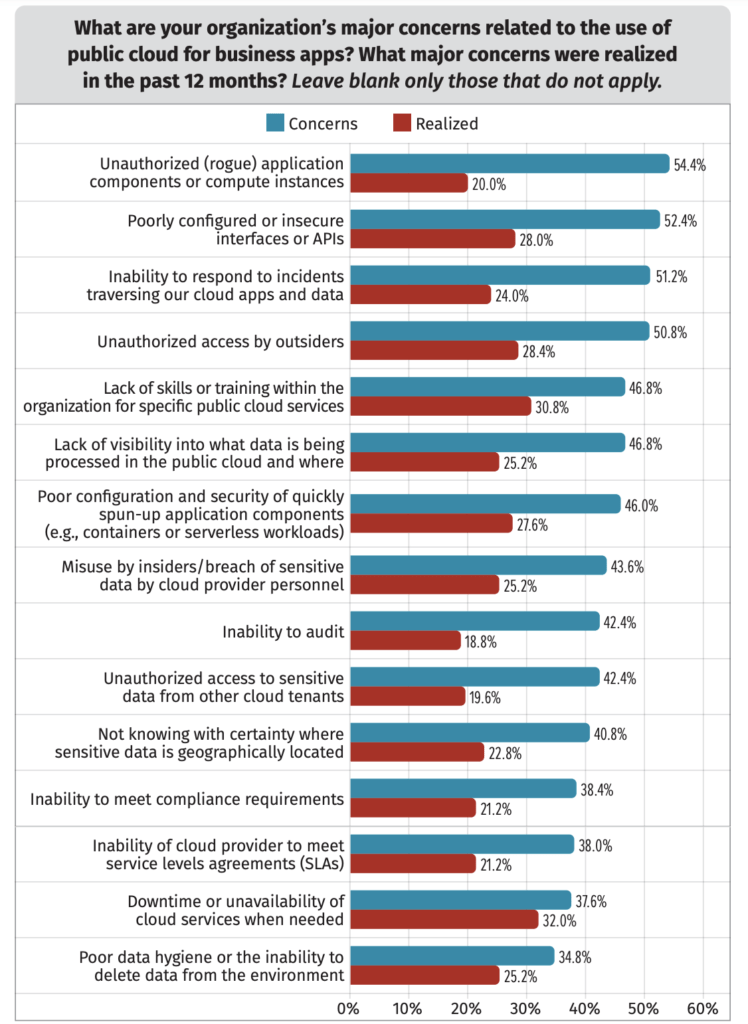
Figure 2. Concerns and incidents in cloud today.
What’s the reason for the disconnect? As cloud infrastructure grows more complex and cloud APIs allow distributed applications to straddle cloud and on-prem resources, it becomes increasingly difficult for IT leaders to get total visibility into organizational cloud assets. The possibilities that shadow IT or insider threats will eat up cloud resources, or that a misconfigured API will open up a hole for attackers, are real and difficult to solve. In some ways, the unknown is scarier than more pedestrian threats, even though those are very real.
Remote Workers Remain a Concern
Most of the survey respondents also worry that remote workers are a potential vector for an attack on their cloud infrastructure. Up to 62 percent said that remote work scenarios increased their cloud risks, up from 43 percent in 2021. Nevertheless, only 19 percent of respondents said that they actually had experienced a breach, which is almost identical to 2021’s results. That said, more organizations were unsure of the answer to this question than in the past.
Obviously, the cloud revolution has caused a lot of anxiety for IT departments. What are they doing about it? The next installment in this blog series will take a look at the tools and technologies security pros use to lock down sensitive data in the cloud. In the meantime, you can dive into the full survey report and get the full details from survey respondents.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates




.jpeg)