BEC and VEC Attacks on the Rise in 2023
Published 10/16/2023
Originally published by Abnormal Security.
Written by Jade Hill.
Despite advancements in legacy security and increased employee awareness, cybercriminals still see email as a primary channel for attacks. And it’s easy to understand why—employees continue to fall for social engineering and financial transfer requests from suspicious actors.
It’s not that we haven’t made any progress. It’s that threat actors have made progress alongside us, becoming more sophisticated and manipulating new technology for malicious attacks.
The number of sophisticated business email compromise (BEC) and vendor email compromise (VEC) attacks rose in the first half of 2023. This continues a five-year trend, with no signs of slowing down.
To combat the threat of BEC and VEC attacks, it is essential to understand where these attacks are coming from and how to stop them.
The Growing Threat of BEC Attacks
Between January and June 2023, BEC attacks increased by 55% over the previous six months. In that same timeframe, nearly half of all organizations received at least one VEC attack.
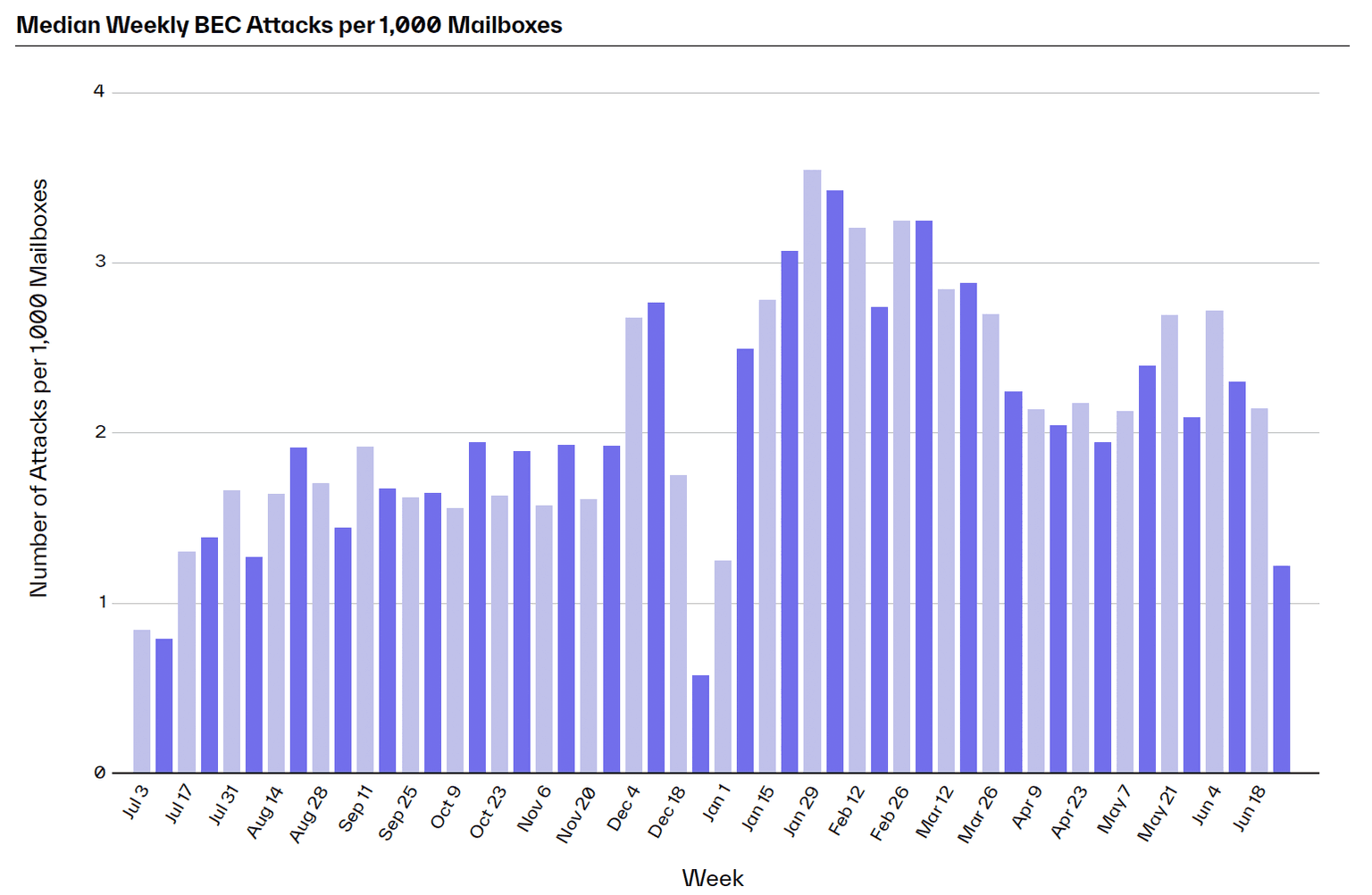
BEC attacks increased from 1.6 attacks per 1,000 mailboxes in the latter half of 2022 to 2.5 attacks over the first half of 2023.
Cause for concern goes beyond the frequency of attacks. Clever cybercriminals know how to make their scams extra convincing. By researching targets via public sources—like websites, LinkedIn profiles, and SEC disclosures—threat actors glean information to improve their persuasiveness. Additionally, attackers use generative AI to rapidly produce high-quality email copy to deceive targets.
BEC is already the most financially devastating threat to organizations, with the FBI IC3 identifying $51 billion in exposed losses from 2013 to 2022. The success of these attacks could explain why, according to our data, BEC is beginning to outpace malware delivery in the first half of 2023.
While BEC attacks are surging everywhere, the technology industry is the most popular target for BEC attacks, with an average of four attacks per 1,000 mailboxes. Other hot targets include construction, advertising and marketing, finance, transportation, and media/entertainment industries—all with over three weekly attacks per 1,000 mailboxes. Each of these industries is targeted for its valuable intellectual property. But no matter the industry, BEC attacks are not to be trifled with.
The Escalation of VEC Attacks
VEC attacks are escalating because attackers identify vendors as soft targets. By exploiting vendor email accounts and using the information stored in mailboxes, threat actors can more effectively infiltrate partners and customers. And since VEC attacks are often sent through legitimate (albeit compromised) email accounts, they are nearly impossible for employees to detect.
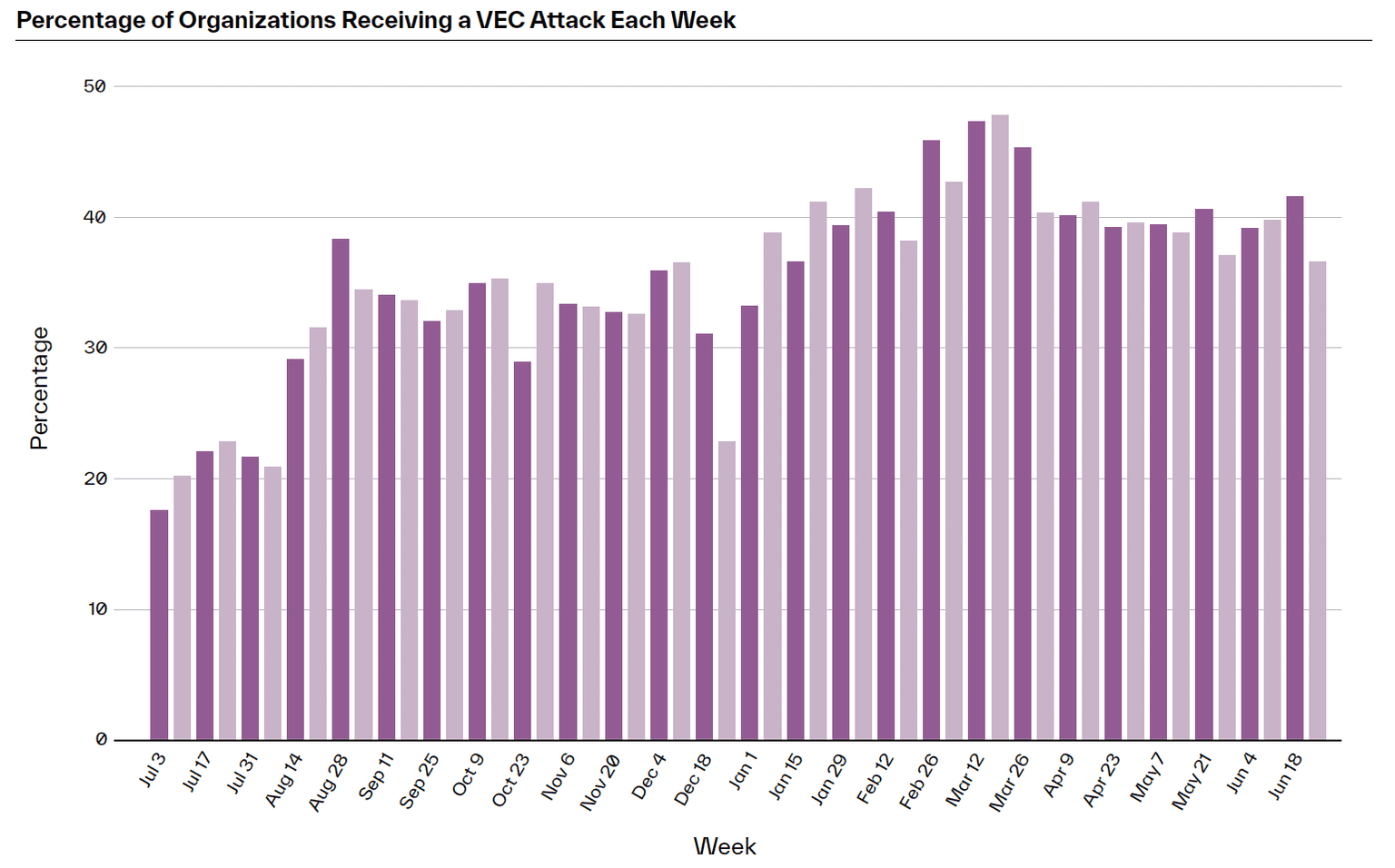
The probability of receiving a VEC attack rose from 45% in the latter half of 2022 to 48% in the first half of 2023.
VEC is particularly dangerous because attackers mimic legitimate vendor communication—or even hijack real conversations—to encourage recipients to send fraudulent payments or update banking account information.
As you can imagine, the costs of these attacks are substantial. While most VEC attacks request less than $150,000, some can cost millions in damages—like this $36 million VEC attack. Beyond the hefty price tag, VEC strains professional relationships and severely impedes operations.
All companies are vulnerable to VEC attacks. However, the advertising and marketing industry took the most heat in the first six months of 2023, with 76.9% of companies targeted by VEC. This could be due to the industry's heavy reliance on software as-a-service (SaaS), partners, and events—which can all be mimicked by bad actors. Other popular targets include agriculture, food processing, engineering, transportation, and retail industries—all of which rely heavily on vendors across the supply chain to run their businesses.
The more heavily businesses rely on vendors, the more opportunities attackers have for exploitation.
Protecting Your Email from BEC and VEC Attacks
Organizations want to defend themselves against all kinds of inbound attacks, including socially-engineered BEC and VEC. Unfortunately, legacy email systems aren’t equipped for the task, and security awareness training can only do so much.
The good news is that organizations can ensure complete protection against the full spectrum of cyberattacks. Behavioral AI-based email security platforms help organizations detect even minor deviations to identify suspicious activities and block attacks. Pairing advanced behavioral science with risk-adaptive detection is the only surefire way to defend your finances, data, and brand reputation against bad actors.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Implementing CCM: Threat & Vulnerability Management Controls
Published: 11/21/2025
Red Teaming Voice AI: Securing the Next Generation of Conversational Systems
Published: 11/20/2025
It’s Time to Make Cloud Threat Modeling Continuous
Published: 11/20/2025
Reflecting on the 2024 Microsoft Breach
Published: 09/15/2025







.jpeg)
.jpeg)
