Einstein’s Wormhole: Capturing Outlook & Google Calendars via Salesforce Guest User Bug
Blog Article Published: 11/12/2021
 This blog was originally published by Varonis here.
This blog was originally published by Varonis here.
Written by Nitay Bachrach, Varonis.
If your organization uses Salesforce Communities and Einstein Activity Capture, you might have unknowingly exposed your administrator’s Outlook or Google calendar events to the internet due to a bug called Einstein’s Wormhole discovered by the Varonis research team.
Exposed calendar events can contain highly sensitive contents such as attendee names and emails, meeting URLs and passwords, agendas, file attachments, and email replies sent to the organizer.
The issue was reported to Salesforce and their talented and extremely responsive team quickly fixed the bug. However, if your Salesforce Community was created prior to Summer 2021, you must remediate exposed calendar events.
Steps to take immediately:
1.) Change your guest user’s email to a dummy email (e.g., [email protected] or [email protected])
2.) Remove sensitive calendar events that Einstein associated with your guest user
More detailed steps are outlined below under the “Mitigation” section. Reach out to our team if you need assistance auditing your Salesforce instance.
Read on for a detailed explanation of how two seemingly unrelated Salesforce features are interconnected and security implications.

Einstein Activity Capture
Einstein Activity Capture (EAC) is a tool that lets you synchronize emails and calendar events between your Microsoft Exchange or Google accounts and Salesforce.
Einstein Activity Capture replaces the older and soon-to-be-obsolete Lightning Sync. In this article we will say Einstein Activity Capture, but the same concepts are also relevant to Lightning Sync.
The idea behind Einstein Activity Capture is to boost your sales team’s productivity by consolidating relevant customer emails and meetings into one central system: Salesforce.
Einstein is smart, so when you create a meeting as an organizer, it will attempt to find other Salesforce people (users, leads, contacts) to sync the event to.
Einstein Activity Capture synchronizes the user’s calendars, the following chain of events occurs:
- Salesforce connects to the calendar, be it Outlook or Google Calendar, and retrieves the events.
- Salesforce adds the events to the user’s Salesforce calendar.
- Salesforce looks at the event’s participants and searches for users, leads, and contacts with matching emails.
- If Salesforce finds records with matching email addresses, it adds the events to their Salesforce calendars as well.
More on how event sync works here.
Einstein’s Wormhole
Up until the Summer 2021 release, guest users were created with the Salesforce admin’s email address.
Let’s revisit our Einstein sync process with this new detail.
Imagine your CTO sends an Outlook meeting invite to the company’s Salesforce admin (let’s call her Judy). It’s a sensitive roadmap meeting involving several key players in the business. Since the guest user shares an email address with Judy, here’s what will happen (prior to the Summer 2021 release):
- Salesforce finds the CTO’s event where the admin is a participant.
- Salesforce looks for users and other objects with an email address matching the participants.
- Salesforce will find Judy the Salesforce admin and sync the event to her calendar.
- Salesforce will ALSO find the guest user and sync the event to the guest’s calendar.
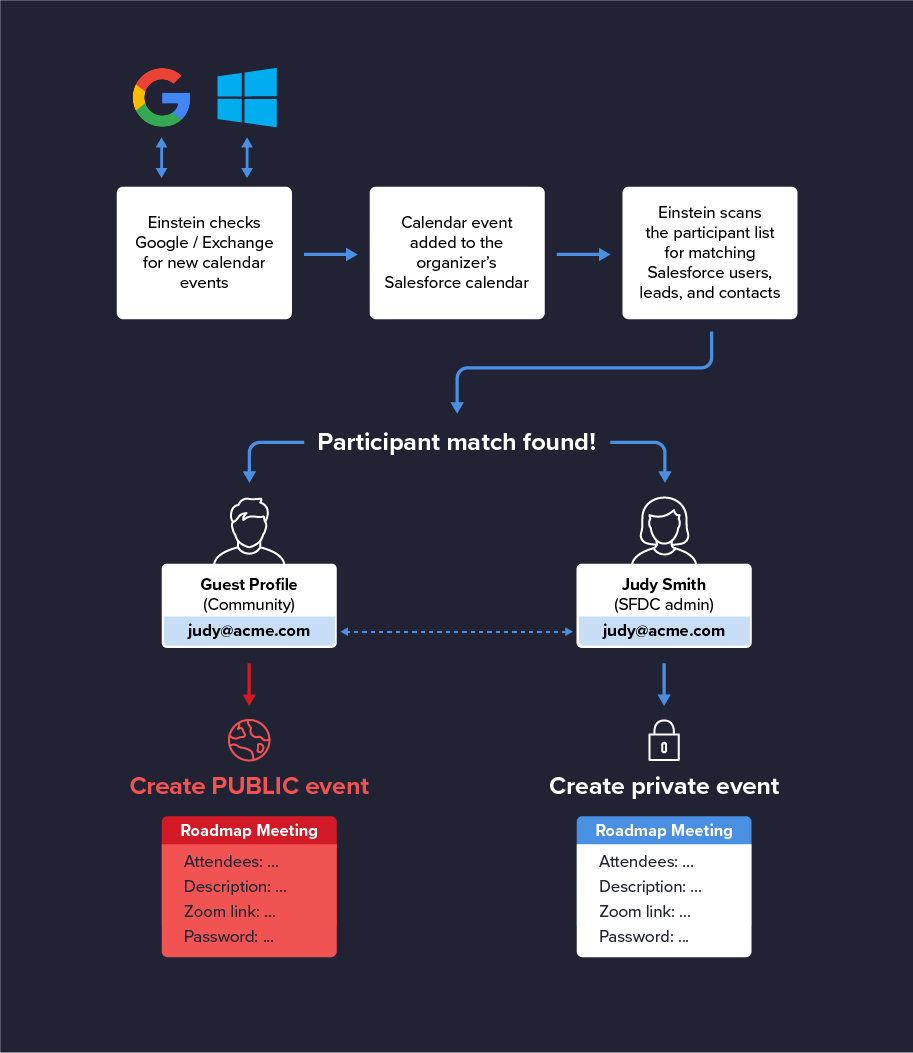
As a result, the event and its details (participants, subject, dial-in, Zoom link, and even the replies to the invite) are exposed to the Internet via the guest user.
The events themselves may contain sensitive information, which by itself can do harm to the business; With a meeting link, password, and attendee list, an attacker could potentially join a meeting without being noticed.
The information can also be used by malicious actors to carry out spear phishing attacks or use details from the meeting to compromise other services, move laterally, etc.
Mitigation
Salesforce quickly fixed this bug so that all new Community sites will not associate the guest user with a real user’s email address.
If your Community was created before Summer ‘21, we recommend you change the guest user’s email for all your Community sites to a dummy email that isn’t associated with a real user’s calendar.
The snippet below can be run in the Development Console and will change the email address of all guest users:
for (User user: [SELECT Id FROM User WHERE UserType='Guest']) {
user.Email = '[email protected]';
update user;
}
To access the Development Console, click on the gear at the top of the page and select “Development Console” (make sure that you are logged in as an admin!).
In the Development Console, press Ctrl+E (works on both Windows and Mac) to open the “Execute Anonymous Window.”
Paste the code into the window and click “Execute” to automatically change the email address of all guest users.
Deleting sensitive event objects associated with the guest user is not as easy. If you need help doing this, please reach out and our team will be happy to help.
Takeaways
The biggest takeaway from this research is that SaaS risk increases as services become interconnected. In this case, two seemingly disconnected features are tied together in an unexpected and undesired way. These small misconfigurations or minor vulnerabilities can have disastrous consequences.
In addition, it’s crucial for enterprises to understand the shared responsibility model when working with SaaS providers. SaaS applications are mainly secure; however, once an enterprise puts data into these SaaS applications, it’s the enterprise’s responsibility to protect the data.
It’s critical for organizations to understand their SaaS landscape and how products affect one another. Think about creating something akin to a network topology diagram for your SaaS products to paint a clear picture of how data flows from one app to the next.
Consider using a cloud security product to visualize exactly what a user (even a guest user!) has access to across all your different SaaS apps, classify sensitive data, and monitor behavior for anomalies.
Disclosure Timeline
- 2021-08-08: Reported to Salesforce
- 2021-08-11: Triaged
- 2021-08-19: Fixed
About the Author
Nitay is a security researcher based in Tel Aviv, but you might encounter him anywhere in world. He is a cloud security expert, highly experienced in offensive security operations and reverse engineering. Nitay’s expertise also includes IoT devices, Linux, and local network security.
Related Articles:
The Narrow Escape from the xz Disaster
Published: 05/07/2024
The Anatomy of an ALPHA SPIDER Attack
Published: 05/06/2024






