HITRUST CSF Assessments: e1, i1, r2—What’s the Difference?
Published 06/26/2023
Originally published by BARR Advisory.
Written by Kyle Cohlmia.
HITRUST CSF is the most widely-adopted cybersecurity framework for healthcare organizations in the U.S. HITRUST CSF provides broad assurance for different risk levels and compliance requirements with greater reliability than other assessment options. There are three types of HITRUST CSF Assessments to consider when deciding what’s best for your organization—the e1, i1, and r2 Assessments.
HITRUST recently released CSF version 11, which added the e1 Assessment to its services and updated the i1 and r2 Assessments, allowing organizations to reuse work from lower-level HITRUST assessments and progressively achieve higher assurance by sharing common control requirements in inheritance. CSF v11 was designed to be threat-adaptive to protect organizations against new and emerging threats.
When it comes to HITRUST assessments, the level of effort each assessment takes directly correlates to the level of assurance it provides. For example, while the e1 Assessment is low effort, it provides only basic assurance. The r2 Assessment requires significantly more effort, but a higher level of risk assurance.
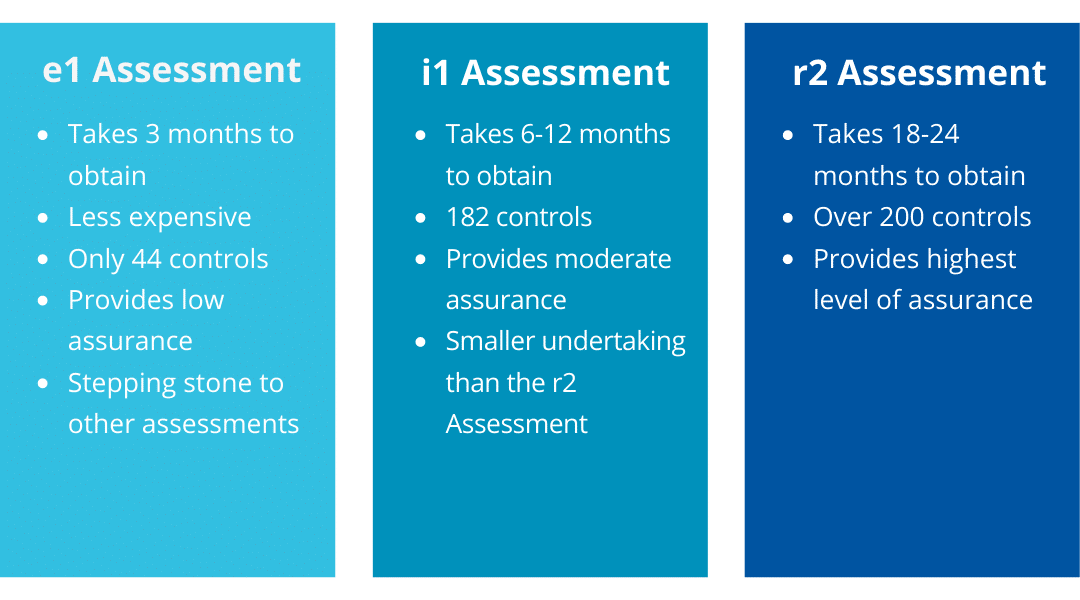
HITRUST Assessments Key Differences
Let’s take a closer look at the e1, i1, and r2 Assessments and how they can benefit your organization.
HITRUST e1 Assessment
The HITRUST Essentials, 1-year (e1) Assessment is a low effort yet reliable assessment that helps organizations focus on foundational cybersecurity controls and prepares them for the most critical cybersecurity threats.
The e1 Assessment can serve as a stepping stone to more comprehensive and higher-effort assessments such as the HITRUST i1 Assessment or r2 Assessment. With only 44 controls, it is significantly more attainable than other cybersecurity assessments.
Similar to other HITRUST assessments, the e1 Assessment is threat-adaptive, which means that as the threat landscape evolves, the requirements will also proactively shift to address risks as they emerge. This includes mitigations for the most critical cybersecurity threats such as ransomware, phishing, brute force, and abuse of valid accounts.
The e1 Assessment is valid for one year from its issuance date. After that year, we recommend building on the established cybersecurity foundation with a higher level assessment.
Who Needs the e1 Assessment?
As the minimum level of cybersecurity assurance in the HITRUST framework, the e1 Assessment is an excellent first step for any organization looking for validation of essential cybersecurity controls that plan to progress to more robust assessments in the future. We recommend the e1 Assessment to startups or other organizations that are just getting started in their cybersecurity journey.
While the e1 Assessment reliably demonstrates an organization’s commitment to the basics, it doesn’t provide coverage of compliance related to laws like HIPAA or other leading cybersecurity practices.
HITRUST i1 Assessment
The HITRUST Implemented, 1-year (i1) Assessment is designed to address the constantly developing threat landscape. As a threat-adaptive assessment, the i1 requirements will also be updated to address future risks as they emerge.
The Provider Third Party Risk Management Council, which is comprised of prominent chief information security officers from leading health systems and provider organizations, announced that any moderate-risk vendors that want to work with them must obtain the HITRUST i1 Certification. The Council’s governing organizations include Cleveland Clinic, Mayo Clinic, and Tufts Medicine.
The HITRUST i1 Assessment is valid for one year from its issuance date. Because the control set evolves over time, vendors will obtain the i1 on an annual basis. With the new HITRUST v11 updates, the i1 Assessment decreased controls from 219 to 182, which helps accelerate the time it takes to complete certification.
Who Needs the i1 Assessment?
The HITRUST i1 Assessment is a good choice for any vendor looking to provide a moderate level of assurance on transparency, accuracy, consistency, and integrity. It allows smaller organizations with less support staff to become HITRUST certified. The reason for this is the i1 only addresses the implementation of each control as opposed to the r2 which requires a policy, procedure, and the actual implementation of the control.
HITRUST r2 Assessment
The HITRUST Risk-based, 2-year (r2) Assessment offers the highest level of assurance and requires significantly more effort than the e1 and i1. Within the updated v11 HITRUST CSF framework, i1 Assessments now serve as the baseline for the r2 Assessments, which has reduced the number of controls in scope considerably.
The r2 Assessment is valid for two years with an interim period in between and addresses five key areas—policy, procedures, implementation, measurement, and management—and over 200 controls.
Who Needs the r2 Assessment?
The r2 is the right assessment for established organizations who obtain a significant volume of sensitive data and protected health information (PHI) to keep secure. As the most comprehensive of the HITRUST assessments, the r2 is key for organizations that need high-level assurance and have the necessary resources and team dedicated to complete a larger, more complex assessment.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
What is a Risk Engineer?
Published: 03/02/2026
OpenClaw Threat Model: MAESTRO Framework Analysis
Published: 02/20/2026





.png)



