It May Only Take One Attack to Get Stung by OneNote!
Published 04/28/2023
Originally published by Skyhigh Security.
Written by Rodman Ramezanian, Global Cloud Threat Lead, Skyhigh Security.
Part of Microsoft’s extensive 365 application suite, Microsoft OneNote offers users a powerful yet flexible information management workbench. As organizations continue their rampant surge into the cloud, OneNote presents a useful notetaking and task management bridge between corporate premises, BYOD, and enterprise cloud realms. Thanks to the wide adoption of OneNote, however, attackers have turned their attention to the app as a viable route for malware distribution.
Security research from the likes of BleepingComputer, Trustwave, and Sevagas has discovered that threat actors are increasingly embedding files into OneNote documents and tricking users into executing them. Shockingly, it wasn’t until late-2022 that attachments within OneNote were exempt from Microsoft’s native Mark of the Web (MOTW) labelling regime, which is effectively designed to notify Windows OS, applications, and end-users that the file originated from the web and shouldn’t be trusted by default.
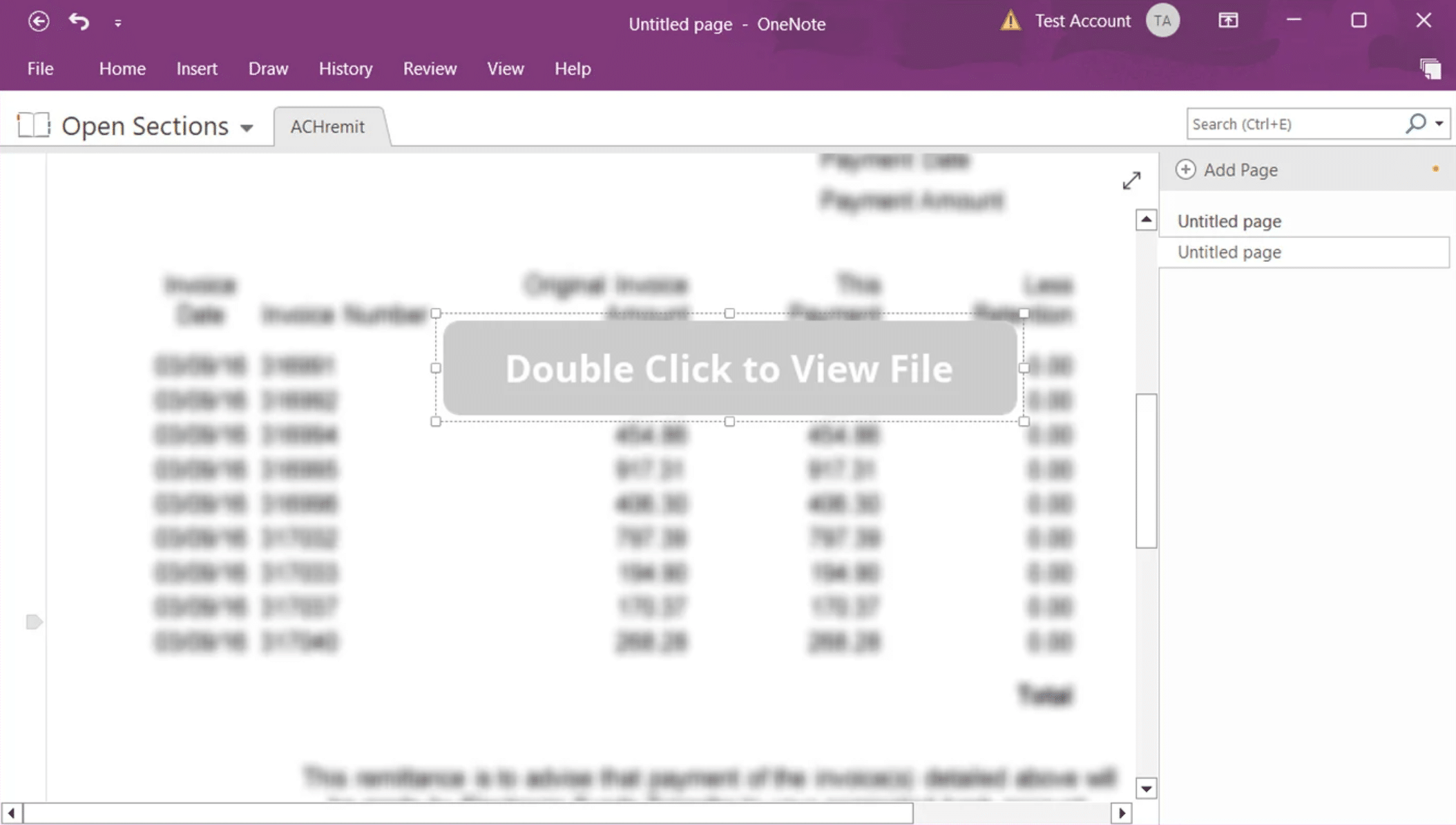
Figure 1. Malicious Microsoft OneNote attachment sample (Source: BleepingComputer)
While this MOTW labelling issue appears to have been silently patched by Microsoft at time of writing – greatly minimizing the risks associated with .one files – it unfortunately does not eliminate the risk completely. Threat actors can embed a wide range of file types within infected OneNote documents, including but not limited to Visual Basic Script (VBS) payloads as seemingly innocuous attachments. Using social engineering, the attachments disguise themselves as legitimate content for businesses, including invoices, mechanical drawings, DHL shipping notifications, remittance forms, and other documents. The files, however, launch malicious scripts once users are convinced to double-click on the embedded malware within the notebook.
Why do these breaches occur?
In the quest to fuel productivity, accessibility, and collaboration, organizations embrace native applications like Microsoft OneNote to empower their workforces.
When software companies like Microsoft update their products to prevent nefarious uses, threat actors naturally shift their focus and tradecraft to develop newer attack techniques offering stronger efficacy.
Attacks abusing OneNote for malware delivery are, in fact, quite similar to those leveraging other forms of infected Office files: the user is lured into opening the document and disabling security checks, resulting in the execution of malicious code.
What makes these attacks particularly effective for cybercriminals is that the targeted user physically interacts with the infected document that’s laced with convincing traps. After all, even though opening the malicious attachment may generate a warning dialog, there is still a high risk that users will ignore it.
For example, attackers use fake graphical buttons in their OneNote files (very much like the native Windows clickable buttons) that would seemingly download the requested document, but when clicked, run the embedded malware script instead.
Unfortunately, social engineering also plays a big role in the effectiveness of these campaigns, with victims continuing to be misled and duped into executing that initial payload and foothold for the perpetrators.
What can be done?
As always, cautiously vetting incoming emails and instant messages is highly recommended. After all, files like these can be distributed very easily thanks to the interweaving of collaboration platforms like Microsoft 365. The same vigilance must be applied to web browsing activity, since fraudulent and risky content online can facilitate the dropping of malware payloads.
Considering, also, the fact that .one file attachments are infrequently used nowadays and considered somewhat unusual or suspicious, recommendations circulating the intelligence community suggest blocking .one file extensions until further notice.
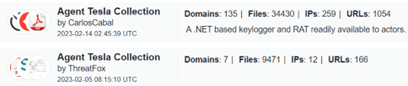
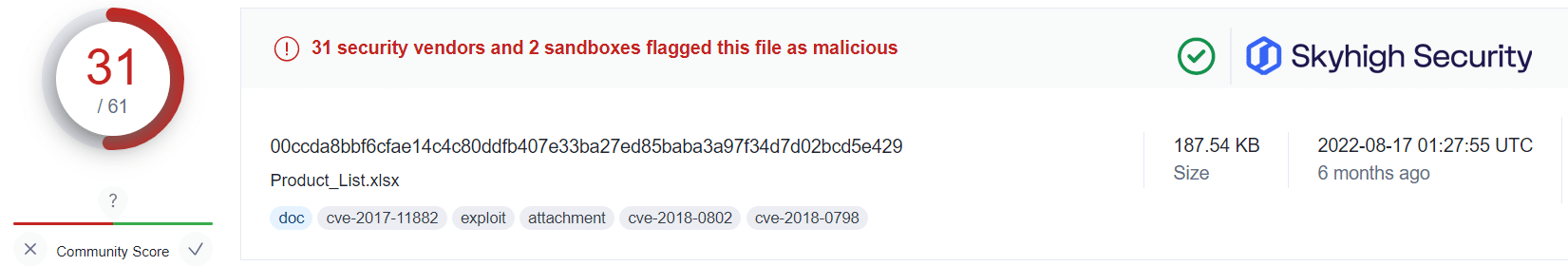
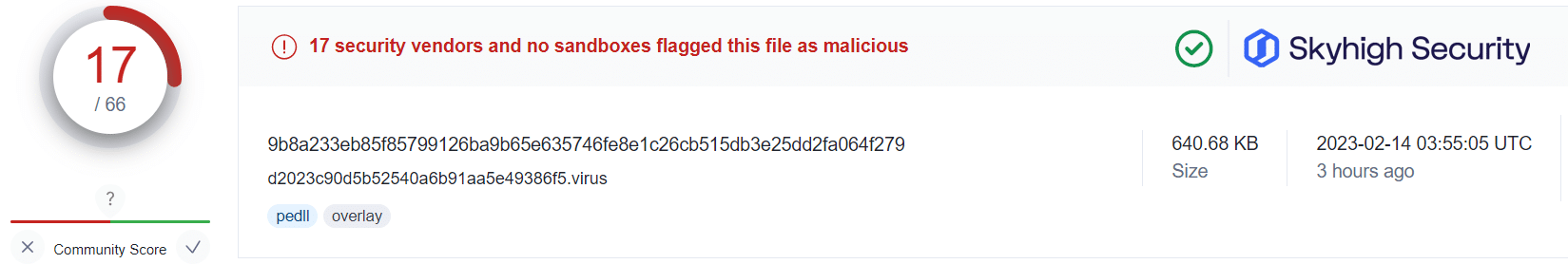
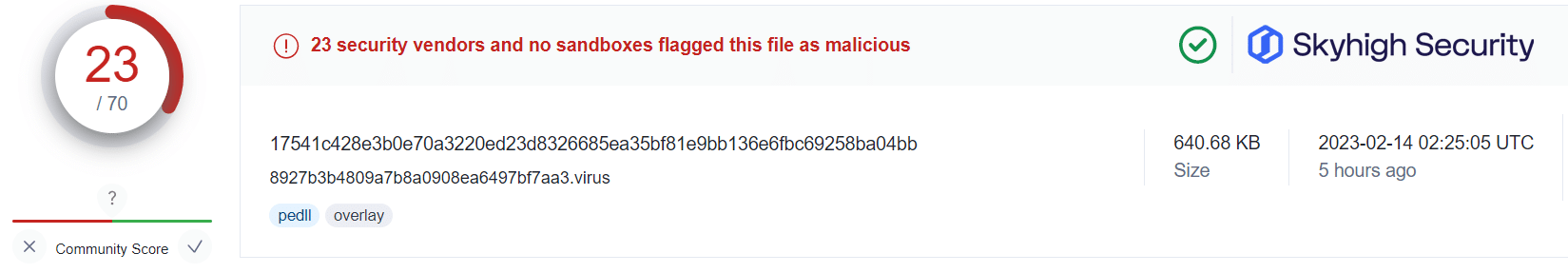
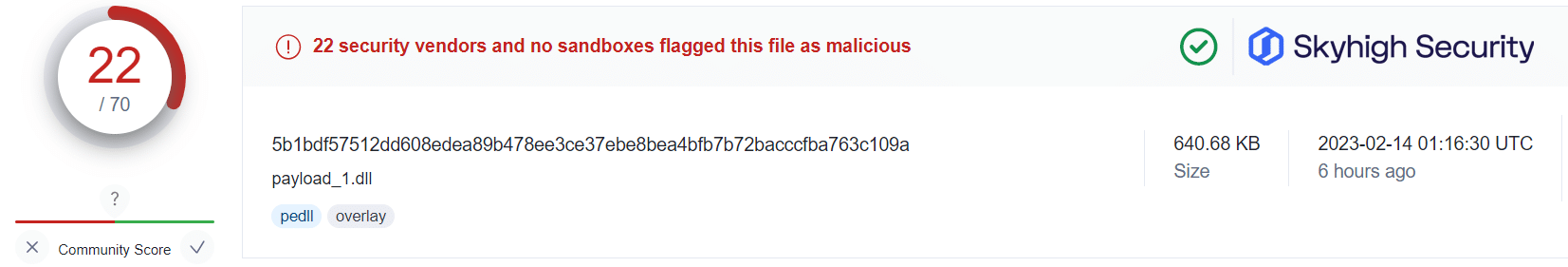
Recent industry research suggests an increasing number of malware campaigns abuse OneNote documents for the delivery of malware, such as AgentTesla, Quasar RAT, Qbot/Quakbot, and DoubleBack, among many others.
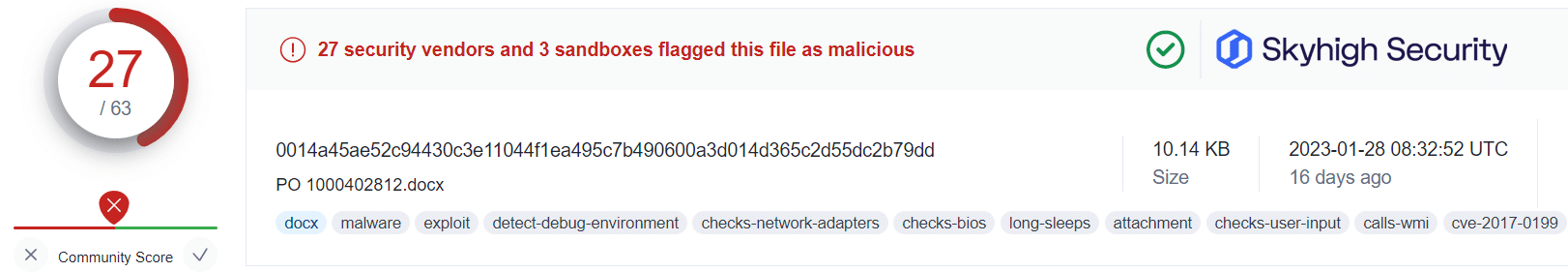
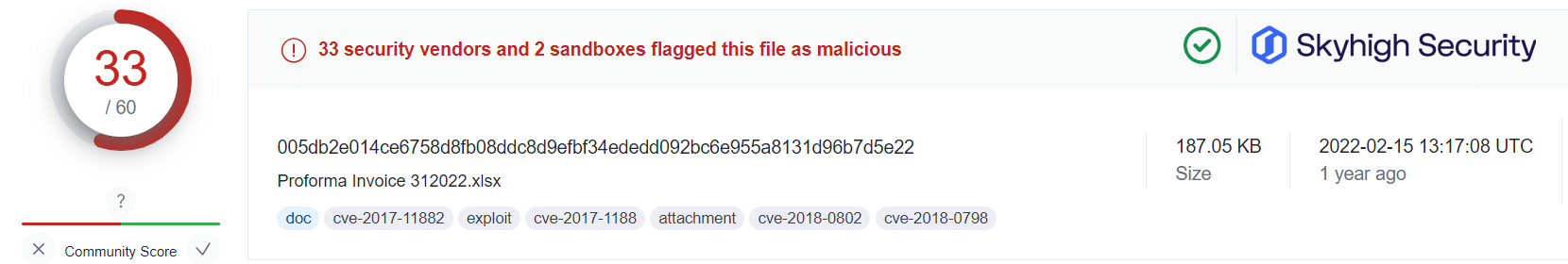
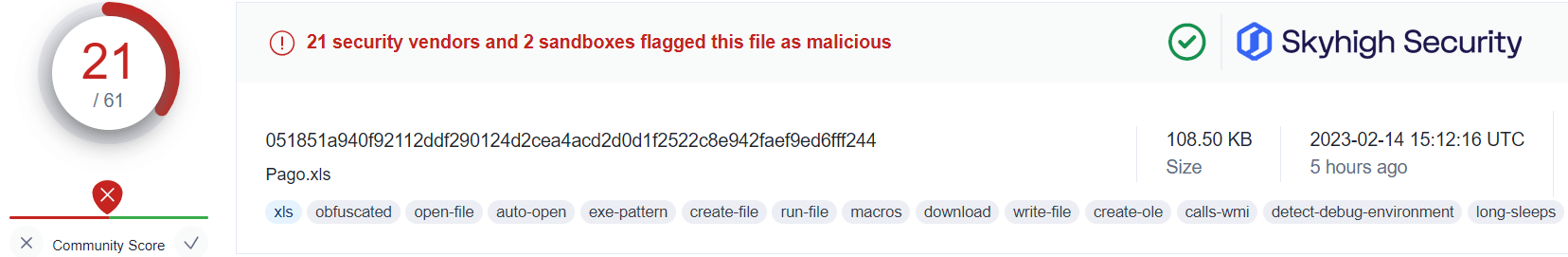
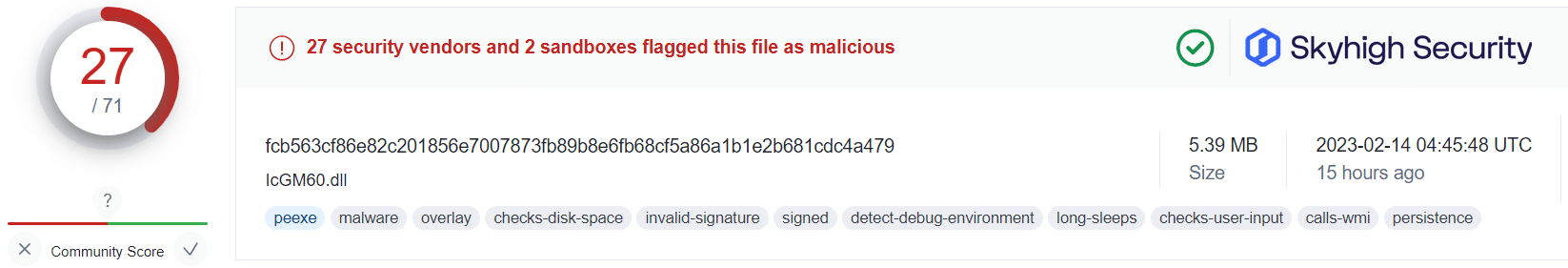
Applying this information alongside the public VirusTotal database, and using randomized sampling of hashes associated with those campaigns, we are presented with some insightful findings:
What this tells us is that even in cases where users have fallen victim to the malicious OneNote attachment, a Gateway Anti-Malware (GAM) emulation and heuristics engine can identify and prevent the malware-ridden payloads from being retrieved from the attacker’s servers.
As always, however, the best advice remains to stay vigilant and protect your systems and users by only opening messages and attachments from trusted parties.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026






.png)
.jpeg)


