The Biggest Cloud Security Threats to Watch Out for in 2024
Published 02/09/2024
Originally published by Orca Security.
Written by Bar Kaduri.
It’s hard to believe that 2023 is nearing its end. As we look ahead to 2024, the Orca Research Pod has continued to examine attacker techniques and targets in cloud environments, as well as identify vulnerabilities and weaknesses that attackers can potentially exploit.
Based on our research, in this blog post we describe three key areas of growing concern that cloud security teams should prioritize in the coming year: attacks on cloud-based AI platforms, software supply chain risks, and cloud-native malware.
1. Attacks on Cloud-based AI Platforms
The use of artificial intelligence (AI) platforms has spiked exponentially in 2023. According to a Salesforce report, 49% of the general population uses generative AI, and 34% uses it every day. In a McKinsey Global Survey published in August, one-third of all respondents say their organizations are already regularly using generative AI in at least one function—meaning that 60% of organizations with reported AI adoption are using generative AI.
The increased adoption is not only limited to generative AI. Cloud-based AI platforms such as Amazon SageMaker, Google Cloud Vertex AI, and Azure OpenAI Service have become indispensable tools for organizations aiming to leverage the power of artificial intelligence technology. These fully managed AI platforms provide a comprehensive set of tools and services for building, training, and deploying machine learning models, foundational for technologies such as generative AI and predictive analytics.
Like any cloud-based asset, there are potential security risks. Some of these risks are brand new, such as model data poisoning, in which a malicious actor intentionally feeds wrong or inappropriate data to the model to tamper with its training process and cause it to provide falsified information. However, some of these risks are derived from the fact that an AI model is a service running code and interacting with consumers and developers. Considering this fact, AI platform users can expect security risks coming from:
1. Theft of Sensitive Data – AI models rely heavily on training data. Just like in any data storage in the cloud, organizations can unintentionally or intentionally store sensitive information, such as personally identifiable information (PII), payment card information (PCI), private health information (PHI) as well as dev keys, secrets, and tokens. The Orca research team found that 54% of organizations store PII in databases, while 21% of organizations using AWS storage have at least one internet-exposed S3 bucket containing sensitive data. Training an AI model on such data, could lead to sensitive data exposure if no additional precaution is taken.
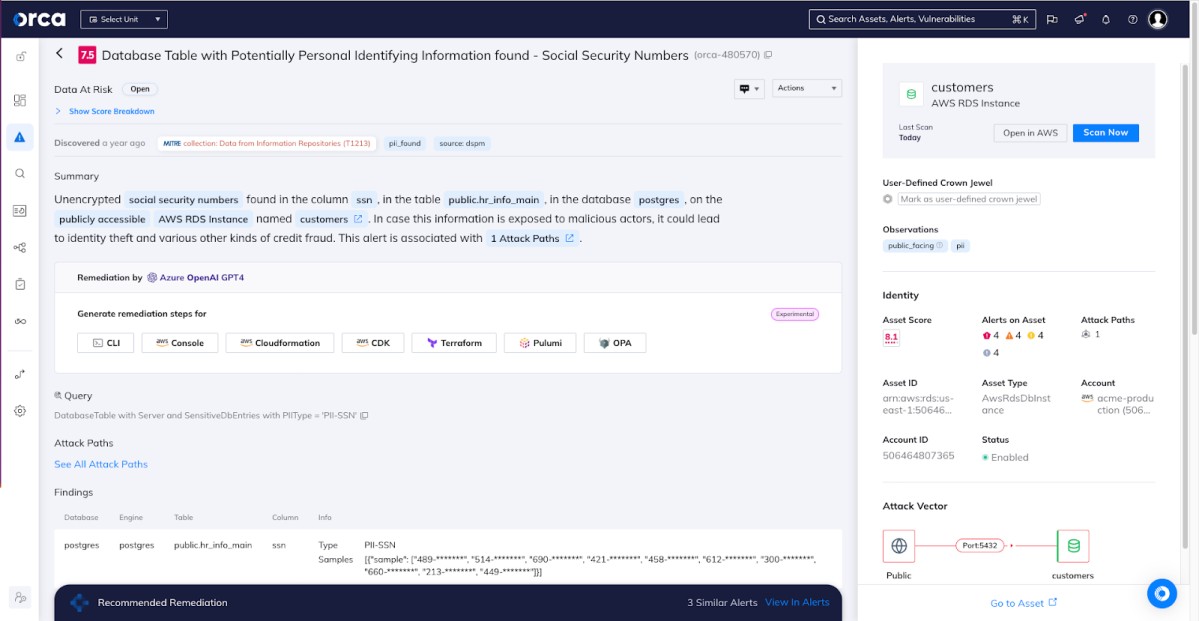
An alert to a database that contains PII. Note that the database is public-facing, increasing the risk.
2. Unauthorized access to code – A misconfiguration can threaten the integrity of a model’s code. For example, the Orca research team found that 82% of organizations that use the AWS SageMaker service have at least one SageMaker notebook exposed to the internet, exposing them to attackers. Malicious actors may exploit misconfigured access controls, gaining unauthorized access to the model’s underlying code. This can lead to the theft of proprietary algorithms or, in extreme cases, enable remote code execution (RCE).
3. Denial of Service attacks – Attackers can manipulate inputs to AI models, flooding them with malicious or resource-intensive inputs, causing unnecessary computations and driving up operational costs. Additionally, sustained input abuse could overwhelm the system, resulting in a denial of service (DoS). It’s recommended to implement input validation and rate-limiting mechanisms to prevent abuse.
4. Output abuse – Inadequate validation and handling of model outputs can lead to the extraction of unintended information, potentially exposing backends to vulnerabilities like Server-Side Request Forgery (SSRF), Cross-Site Scripting (XSS), and SQL injection.
To ensure the security of cloud-based AI platforms, organizations need to implement a multi-layered defense strategy:
- Access Control and Least Privilege – Implementing strict access controls and adhering to the Principle of Least Privilege (PoLP) is essential to prevent unauthorized access to AI platforms. Only individuals with a need to access the platform should be granted appropriate privileges, minimizing the risk of accidental exposure or intentional misuse.
- Encryption – Encrypting data used in AI models both at rest and in transit is crucial to protect sensitive information from unauthorized access. Organizations should utilize encryption mechanisms provided by the cloud platform or employ additional encryption solutions for an extra layer of security.
- Regular Audits and Monitoring – Continuous monitoring and auditing of the platform’s activities is vital to identify any suspicious behavior, such as unusual code changes, unexpected spikes in resource usage, changing patterns in input data, or potential security breaches. Implementing robust logging mechanisms and an automated cloud security platform can aid in detecting and responding to security incidents in a timely manner.
- Security Training and Awareness – Educating employees about the best security practices and potential threats related to AI platforms is critical. Regular training sessions can help employees recognize and respond appropriately to security incidents or suspicious activities.
2. Software Supply Chain Risks
Supply chain attacks have gained prominence in recent years, with cybercriminals focusing on exploiting vulnerabilities in third-party services, including those in software or code that is part of dependencies in production or the CI/CD process. 61% of U.S. companies have been impacted by a software supply chain attack over a 12-month period in 2022-2023, according to a Capterra report.
High-profile security breaches involving companies like Okta and CircleCI, both of which led to customer data being stolen, highlight the criticality of addressing supply chain risks. In both of these cases, attackers were able to steal credentials or tokens to gain access to sensitive information. These SaaS third-party services are widely used by organizations to help build and manage their applications. Using one example to highlight the scope of this risk, the Orca research team found that 56% of organizations are using an external identity provider (such as Okta, but others as well) for user authentication.
Working with third-party services or applications can save development time and effort. Often this communication is easily done through API keys, tokens, or credentials. If these secrets are left unencrypted, unchanged, or are overly accessible, attackers can gain unauthorized access to control critical systems or sensitive data, including customer data, representing a supply chain risk.
Another type of supply chain risk is when an organization’s application is built with code dependencies infected by attackers. If successful, this type of attack can have disastrous consequences, infecting all the vendor’s customers that install the malicious package. These organizations could then be targeted with unauthorized access, data theft, ransomware, and more.
To mitigate supply chain risks within cloud environments, organizations should focus on:
- Rotate keys and change credentials – Regularly rotate API keys, tokens, passwords, and other sensitive credentials to lessen the potential impact of a compromised supply chain partner. Timely key rotation reduces the window of opportunity for attackers and minimizes the potential fallout. The Orca research team found that 79% of organizations had unrotated keys. It’s clear that the majority of organizations still need to improve in this regard.
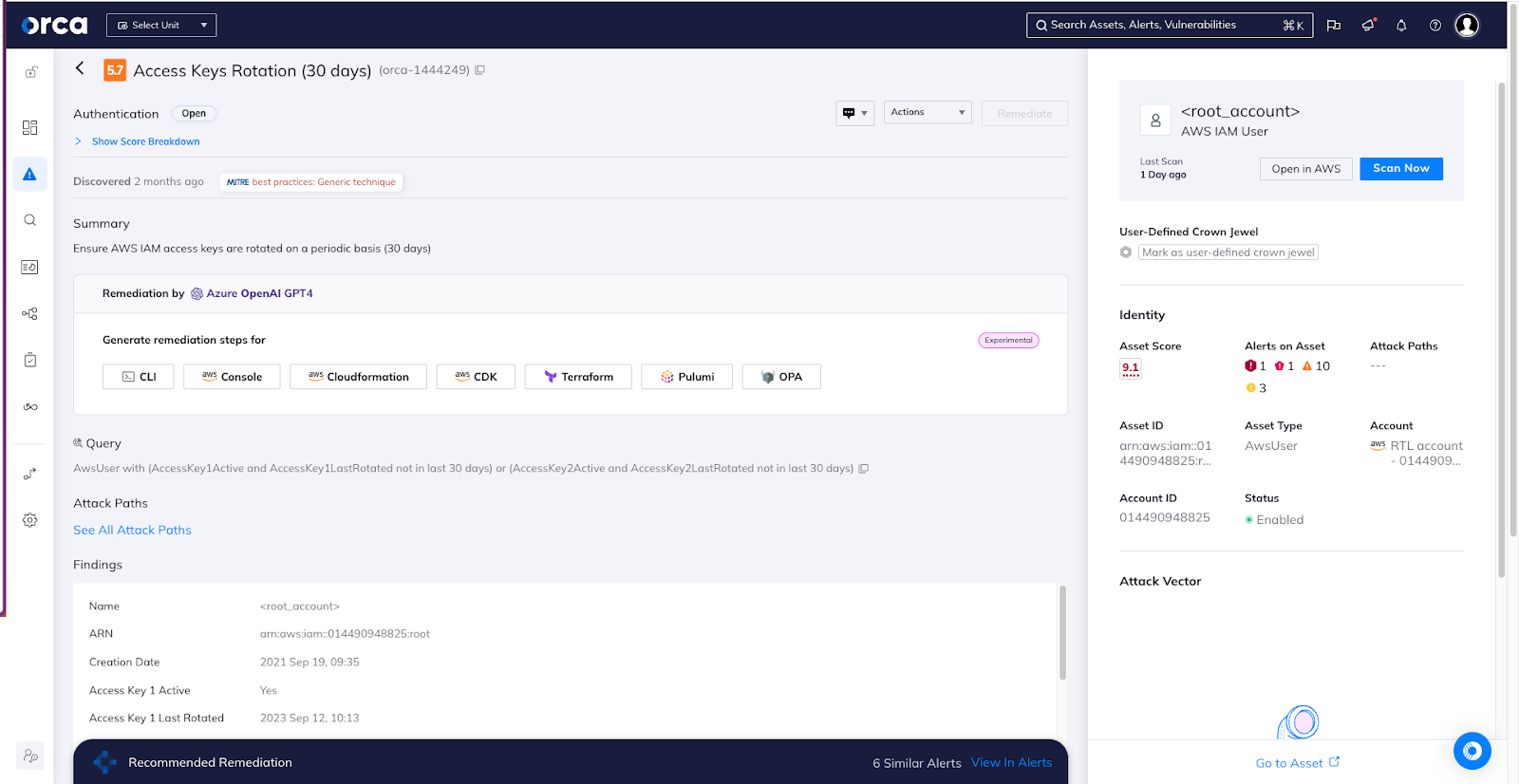
An alert to AWS IAM access keys that have not been rotated for 30+ days.
- Encrypt secrets and store them safely – Encrypting API keys, tokens, credentials, and other secrets before storing them in configuration files or environment variables protects against unauthorized disclosure. In addition, it is unsafe to store hard-coded credentials and other secrets in application source code. The Orca research team found that 69% of organizations store unencrypted secrets (API keys) in code repositories (Github, BitBucket, or others), a worryingly high number. Using secure key management systems, typically provided by cloud service providers, to store and manage encryption keys adds an extra layer of security. Utilize a secure, centralized vault that supports robust access controls. This ensures that only authorized users and applications have the necessary permissions to access the API keys.
- Adhere to the Principle of Least Privilege – It’s not only important to limit access to API keys, but also to limit the permissions of the keys themselves. Review and minimize redundant permissions associated with the account role assigned to the API key. By limiting the scope of permissions to what is strictly necessary for the intended function, you reduce the potential impact of a compromised key.
- Automated security scans – Implement automated security scans that regularly check code dependencies for vulnerabilities and other security issues. This can help to catch any malicious packages before they are able to cause harm.
- Vendor Assessment and Due Diligence – Conducting thorough assessments of cloud service providers and other third-party vendors before engaging their services is essential. Evaluating the vendor’s security practices, certifications, and their own supply chain risk management protocols helps in making informed decisions and reducing the potential for breaches.
3. Cloud-Native Malware
According to Gartner, 65% of application workloads will be optimal or ready for cloud delivery by 2027, up from 45% in 2022. As cloud services become increasingly interconnected and data transfers between various cloud platforms occur frequently, the risk of cloud-native malware infections rises. Cloud-native malware is specifically designed to target cloud environments, exploiting vulnerabilities in cloud infrastructure or applications, or spreading through cloud storage and collaboration tools.
We wrote earlier this year about the rise of malware in cloud storage buckets, and the challenges of remediation. For example, the Orca research team found that it takes organizations an average of 12 days to remediate malware on VMs, but 91 days to address malware in storage buckets, which is 7.5x longer.

An alert to malware detected in an Azure Blob Storage container.
Attackers are becoming increasingly more sophisticated in carrying out malware attacks in cloud environments. Just a few weeks ago, an analysis of the Dagon Locker Ransomware by The DFIR Report showed how attackers are utilizing AWS knowledge to move within an AWS account and exfiltrate data. Leveraging existing cloud functionality and tools to conduct what appears like legitimate user activities, often known as masquerading, can reduce detection and allow for prolonged presence inside the cloud environment. Cybercriminals are continually developing new techniques to exploit vulnerabilities in cloud infrastructure to distribute malware, conduct phishing attacks, or compromise sensitive data.
To protect against cloud-based malware threats, organizations should follow these recommended practices:
- Identify and patch vulnerabilities – The Orca research team found that 94% of attack paths in cloud environments gain initial access through exploitable vulnerabilities. Regular vulnerability assessments and patch management are essential to keep cloud platforms and associated software up to date, reducing the likelihood of exploitation by malware.
- Leverage malware detection – Deploying malware detection capabilities helps identify and eliminate potential threats before they can cause harm. Make sure the tool you use not only finds known malware by using signatures, but also uses heuristic scanning to detect unknown malware and zero-day threats.
- Limit permissions – Ensure that permissions to assets that contain sensitive data are configured to adhere to the least-privilege principle and that write access is limited only to trusted sources. In addition, it’s critical for security teams to be able to identify and reduce lateral movement paths that attackers could potentially exploit, if they have bypassed perimeter security controls. By reducing permissions and privileges, lateral movement threats are diminished as well.
- Enforce Multi-factor Authentication (MFA) – Enforcing MFA for accessing cloud services mitigates the risk of unauthorized access and helps prevent account compromises.
- Monitor activity – Implement logging and monitoring to detect suspicious behavior and events.
- Prioritize remediation – If you cannot remediate all instances of malware, make sure you prioritize those cloud assets that contain sensitive information and/or are connected to the greatest number of instances, since a breach of these assets could cause the greatest impact to the business. A critical component to effective prioritization is to be able to identify how detected malware can combine with other cloud risks–including vulnerabilities, misconfigurations, the location of PII, API risks and more–to create dangerous attack paths. The ability to have extensive visibility into the wider cloud environment is of paramount importance.
- Regularly Back Up Data – Establish a robust backup strategy for critical data, and regularly back up your systems to a secure, isolated location. Cloud providers typically offer managed backup services that automate and streamline this process.
As organizations embrace the cloud and its vast potential, it becomes increasingly vital to raise awareness about the accompanying security risks. By adopting measures such as key rotation, encryption, principle of least privilege, multi-factor authentication, regular monitoring, and security training, organizations can strengthen their cloud security posture and mitigate risks.
Remember, proactively addressing these risks is crucial to preserve the numerous benefits of cloud technology. Stay vigilant, stay informed, and make cloud security a top priority in 2024 and beyond!
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Zero Trust for Agentic Pipelines That Touch Cloud Production
Published: 02/27/2026
Core Collapse
Published: 02/26/2026
Agentic AI and the New Reality of Financial Security
Published: 02/26/2026
AI Security: When Authorization Outlives Intent
Published: 02/25/2026





.png)
.jpeg)
.jpeg)

