The Credential Theft Food Chain - How Does a Bad Actor Move Laterally Once In?
Published 09/09/2022
Written by Anastasios Arampatzis, Tech Writer, Bora
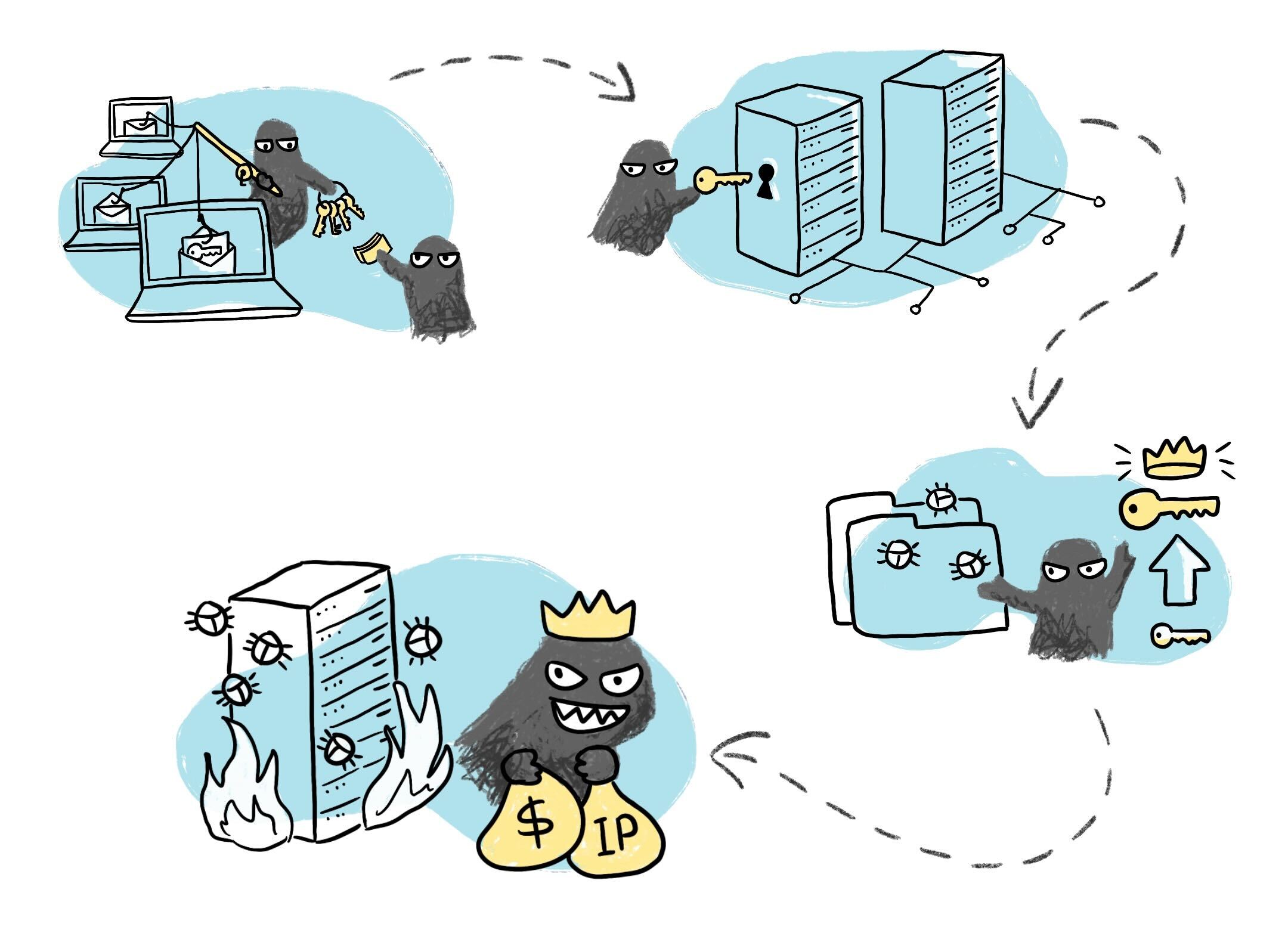
Any time a breach occurs, senior management and any subsequent media coverage often focus on how the criminal got into the network. Most company leadership would like to imagine that the breach resulted from a sophisticated, lengthy campaign to discover and exploit an unpatched weakness or the launch of a zero-day exploit. However, most of the events in recent memory have been explained with a short, albeit managerially, unsatisfying answer. That answer is that someone was convinced to follow a malicious link to a fraudulent login page that resulted in stolen credentials.
Credit: Yvonne Weng
The response of a person having their credentials stolen should not result in the full compromise of a network. However, the real question that senior management should ask is: how did they escalate to the point of getting an Administrator’s credentials and granting unfettered access to the entire infrastructure? The nefarious technique that elevates a standard login to super-user level is at the root of what is known as lateral movement.
What are your Credentials Worth?
One would think that stolen credentials can fetch a handsome price on the criminal marketplace, but, as was demonstrated many years ago, much of the information for sale on the Dark Web is offered in bulk for a modest price. In some cases, one need not buy credentials at all, as too many people still famously use weak passwords, such as qwerty, 1234567890, and, as described by one security journalist, “the mildly ingenious "1q2w3e" (a fun little finger dance on a keyboard — try it yourself)”.
The biggest problem with stolen credentials is that they generally do not trigger any intruder alerts. Barring any login time restrictions or geographic limitations, they are a known entity in the organization.
Doing the Funky Pivot
Once an attacker successfully logs into a system using stolen credentials, they can then embed malware and spyware and surreptitiously examine the local system to see if there are any artifacts of higher-level access. This method is exceptionally effective at escalating privileges because every system has had an administrative login on that system at one time or another.
There are many techniques to expose and enumerate accounts on a system. One significant approach that sets today's advanced persistent threats (APTs) apart from earlier, more straightforward intrusions is lateral movement. Even if identified on the machine that was initially infected, lateral mobility enables a threat actor to evade detection and maintain access. Additionally, if dwell time is prolonged, data theft may not happen for several weeks or even months after the first breach.
Once entry is accomplished, the attacker can pivot to higher-value targets by impersonating additional genuine users and taking over additional accounts. This pivot is also known as lateral movement. After first acquiring access to an endpoint, sometimes through phishing or malware infection, the attackers proceed across many systems in the network until they reach their target. Obtaining credentials, rising privileges, learning about all systems and accounts, and finally, gaining access to the targeted payload are all necessary to accomplish that goal. While efforts to prevent some of these attacks have been successful, many legacy systems are still vulnerable to this type of compromise.
Add Digital Confidence with Zero Trust
The new security model for preventing credential theft attacks has a very simple application. Multi-factor authentication (MFA) is the simplest and quickest way to prevent credential theft use, and MFA is a first step towards robust identity and access management. Some weak MFA implementations have raised concerns, but this is true of any weak implementation of any security program.
Overall the benefits offered by MFA far outweigh any concerns. A strong authentication program can be rolled out to an entire organization in a phased approach and completed in months. Few other security initiatives that require full-staff interaction can boast the same success.
Modern MFA programs have flexible options capable of satisfying even the most stubborn adopters. MFA is necessary for zero trust execution, and elevating digital confidence in any environment.
Worry No More
Zero trust can seem overwhelming. The core components alone can be intimidating, and in a broader requirement, such as that of protecting government systems, it can almost seem unattainable without an army. One of the first and perhaps easiest steps towards embarking on a zero trust journey is to protect credentials. This simple yet extremely effective method of credential protection can bring a satisfying smile to both the security team and senior management.
About the Author
Anastasios Arampatzis, a retired Hellenic Air Force officer with over 20 years of experience managing IT projects, was a certified NATO evaluator for information security. His interests include cybersecurity policy and governance, ICS and IoT security, encryption, certificates management, and exploring the human side of cybersecurity. Now he leverages his background and interests to produce cybersecurity content - contributing to 1000's of technology news blogs, thought-leadership articles, whitepapers, and eBooks. His latest named research includes co-authoring a chapter of the Handbook of Research on Cyberchondria, Health Literacy, and the Role of Media in Society's Perception of Medical Information.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How CSA STAR Helps Cloud-First Organizations Tackle Modern Identity Security Risks
Published: 02/13/2026
Offboarding Under Pressure: How to Keep SaaS and AI Data Secure During Layoffs
Published: 02/10/2026




.jpeg)

