The Real Cost of Cryptomining: Adversarial Analysis of TeamTNT
Published 03/06/2023
Originally published by Sysdig on November 16, 2022.
Written by Nicholas Lang, Sysdig.
TeamTNT is a notorious cloud-targeting threat actor, who generates the majority of their criminal profits through cryptojacking. Sysdig TRT attributed more than $8,100 worth of cryptocurrency to TeamTNT, which was mined on stolen cloud infrastructure, costing the victims more than $430,000. The full impact of TeamTNT and similar entities is unknowable, but at $1 of profit for every $53 the victim is billed, the damage to cloud users is extensive.
Public cloud adoption has created a vast-enough attack surface that it’s now viable for malicious actors to specialize in exploiting this type of environment.
One threat actor who specifically targets cloud infrastructure and vulnerabilities is known as TeamTNT and has been active since late 2019. Because TeamTNT is very open with public communications, frequently self-attributes, and attacks the public internet en masse, they are by far the best-documented cloud-focused threat actor.
This article is part of the 2022 Sysdig Cloud-Native Threat Report.
Adversary Profile
There is very little evidence that TeamTNT consists of more than one person. However, an individual who goes by Hildegard claims to be the “leader of the group” and is likely a German male, over 25 years of age.
TeamTNT is active on Twitter and can often be found posting political content, jokes at the expense of security companies, and comments about their own cybercriminal operations. This is unusual for a threat actor as they typically avoid drawing unnecessary attention to themselves.
Based on Twitter activity, Hildegard is socially liberal. Hildegard follows many center-left and left-leaning German politicians and pundits on Twitter, and often interacts directly with them. In fact, the majority of two of Hildegard’s top three Twitter Circles are mainly left-leaning pundits, with the rest being malware analysts. Given that there is no noticeable discretion with which TeamTNT chooses its targets, hacktivism can be ruled out as their motivation.
In screenshots posted to Twitter, Hildegard uses ParrotOS, which bills itself as “The Operating System for Hackers.” ParrotOS provides the ability for a user to route all of their traffic through Tor, allowing the ParrotOS user to hide their true IP address from the endpoints they are attacking or from the dubious websites they are browsing. One of the main advantages of using a tool like Tor is that it helps to prevent accidental leakage of their IP Address, which may happen with other tools.
Notable Activity
TeamTNT’s humble beginnings were in attacking vulnerable Redis deployments, using these as an entrypoint for running Monero cryptominers. Monero is a popular choice for cryptominers due to its inherent privacy features, making it much less traceable than most other cryptocurrencies. TeamTNT then expanded its operations with their “Dockergeddon” campaign, targeting exposed Docker API endpoints. Perhaps its most notorious and public campaign was the subsequent “Chimaera” campaign. In the Chimaera campaign, TeamTNT targeted Docker, AWS, and Kubernetes endpoints.
Team TNT allegedly compromised over 10,000 Docker, Kubernetes, and Redis devices during the Chimaera campaign.
Over the years, TeamTNT has scaled up its operations in order to make as much money as possible with the lowest amount of effort. This has included building out management infrastructure and automation to facilitate mass exploitation. The Chimaera operation included a custom dashboard to orchestrate all of the compromised devices.
Sysdig TRT was able to identify TeamTNT’s infrastructure of command and control servers through our honeynet system and by correlating the evidence with other sources, including voluntary self-attribution by the threat actor.
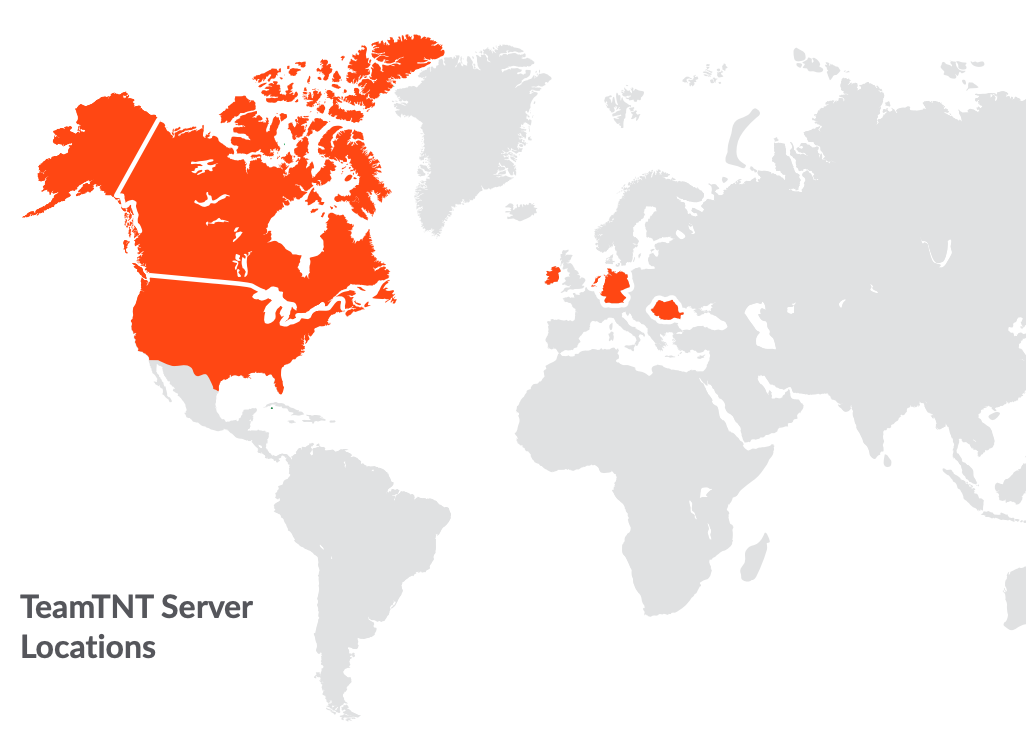
TeamTNT’s servers are primarily located in Europe and North America, including the United States, Canada, Germany, the Netherlands, Ireland, and Romania.
Tracking TeamTNT Operations
TeamTNT is best known for its cryptojacking worm activity, which began in 2019, exploiting vulnerable instances of popular Key-Value store Redis, where the first iterations of TNT’s payloads were deployed, mostly based on shell commands to download and run Xmrig.
“TeamTNT expanded operations to include the compromise of exposed Docker API endpoints. Attacking an exposed Docker API, especially those that run as root, is a no-exploit way to run arbitrary code on someone else’s system.”
For a financially motivated actor, cryptojacking is very appealing due to the difficulty of tracing privacy-coin transactions and the ease of turning the compromised system into a profit-generating asset. As TeamTNT is persistent on a system, it is stealing CPU cycles and earning digital cash at the expense of the victim.
Compared to other profit-motivated and extortion-based attacks, such as Ransomware, cryptomining is a simpler source of income that poses a much lower risk to the attacker. Ransomware is a hot topic these days and attracts a lot of attention from law enforcement if the wrong target, such as a hospital, is hit. The ability to run arbitrary Docker images and commands on exposed endpoints, combined with the relatively widespread availability of said endpoints, led TeamTNT to craft a few iterations of Docker images containing their toolset, further detailed here.
As 2021 progressed, TeamTNT transitioned from using preloaded images uploaded to Docker Hub to generic or “safe” images, like ‘alpine’ or ‘ubuntu:18.04,’ to evade initial detection, after which they run malicious shell commands and scripts.
Chilean security researcher Germán Fernández was able to view and post screenshots of the TeamTNT miner control panel in November 2021, to which Hildegard replied, “Would you like an SSH account to the server? I could save you a lot of time.” This may just be Hildegard trolling, but shows an apparent lack of concern for operational security.
At this point in its 2021 operations, TeamTNT was using the open source tool XmrigCC to manage its network of compromised endpoints. XmrigCC is a custom fork of Xmrig with a server and client component used by both legitimate and nefarious actors. It allows an operator to get a view of all of its miners and how they are performing.
In 2022, Sysdig TRT also witnessed TeamTNT adjusting its scripts to connect with the AWS Cloud Metadata service.
For example, an EC2 instance in AWS has access to a special server endpoint in order to get information about itself. It is commonly located at: http[://]169.254.169.254/latest/meta-data/. The IAM credentials associated with the EC2 instance are also stored at this endpoint. Using these credentials, TeamTNT could gain access to other resources, such as an S3 bucket that the EC2 instance is able to access. If there are excessive permissions associated with these credentials, the attacker could gain even more access. Sysdig TRT believes that TeamTNT would want to leverage these credentials, if capable, to create more EC2 instances so it could increase its cryptomining capabilities and profits.
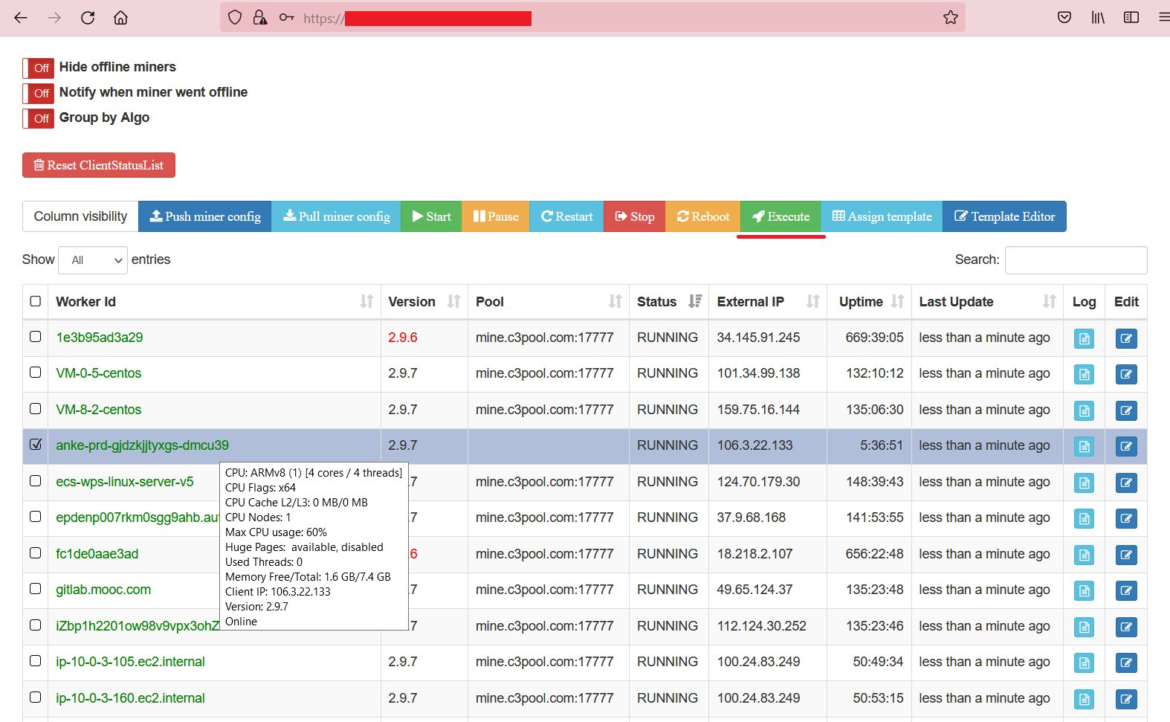
TeamTNT XmrigCC Server Control Panel
One relatively recent tactic that TeamTNT has implemented is the use of Xmrig-Proxy to further obfuscate its activity. TeamTNT runs Xmrig-Proxy on its attacker-controlled infrastructure, and connects to it from compromised machines. A value-add of Xmrig-Proxy is that TeamTNT can hide its wallet address from the compromised machine, further confounding efforts to track the quantity of XMR mined. It also allows the miner to connect to IP Addresses that are not known mining pools, making detection more difficult.
A typical Xmrig configuration file will list the mining pool, the wallet address, and the coin to be mined. With Xmrig-Proxy in play, each individual miner doesn’t need to know which wallet it is mining for because the wallet address is stored on the Xmrig-Proxy server.
Financial Impact of Cryptojacking
The Sysdig Threat Research Team recovered 10 TeamTNT XMR wallets used during the aforementioned mining campaigns by analyzing all known attributed samples. However, there are likely other wallets that were undiscoverable. Additionally, Sysdig TRT attributed more wallets to different threat actors who used TeamTNT tactics. This research included samples captured in the Sysdig honeynet, as well as popular malware repositories such as VirusTotal and Malpedia. Sometimes a discovered wallet would lead to an undiscovered malicious binary, which may have embedded other undiscovered wallets in it, and so on. Other times, a discovered wallet would lead to an Xmrig config file with other wallets or pools listed.
Because the cryptocurrency being mined by TeamTNT is privacy-coin Monero, it is difficult to follow the coinage once it leaves the mining pool and to identify the purpose of the group conducting activities. There are tools available to investigate Monero, like CipherTrace, but it is restricted to government and financial institutions.
Monero is the de-facto cryptojacking coin choice because most cloud infrastructure runs without an attached GPU, heavily disincentivizing GPU-based miners, which would be more lucrative. Of the privacy-coins, Monero (XMR) is currently the highest-value for CPU-based mining.
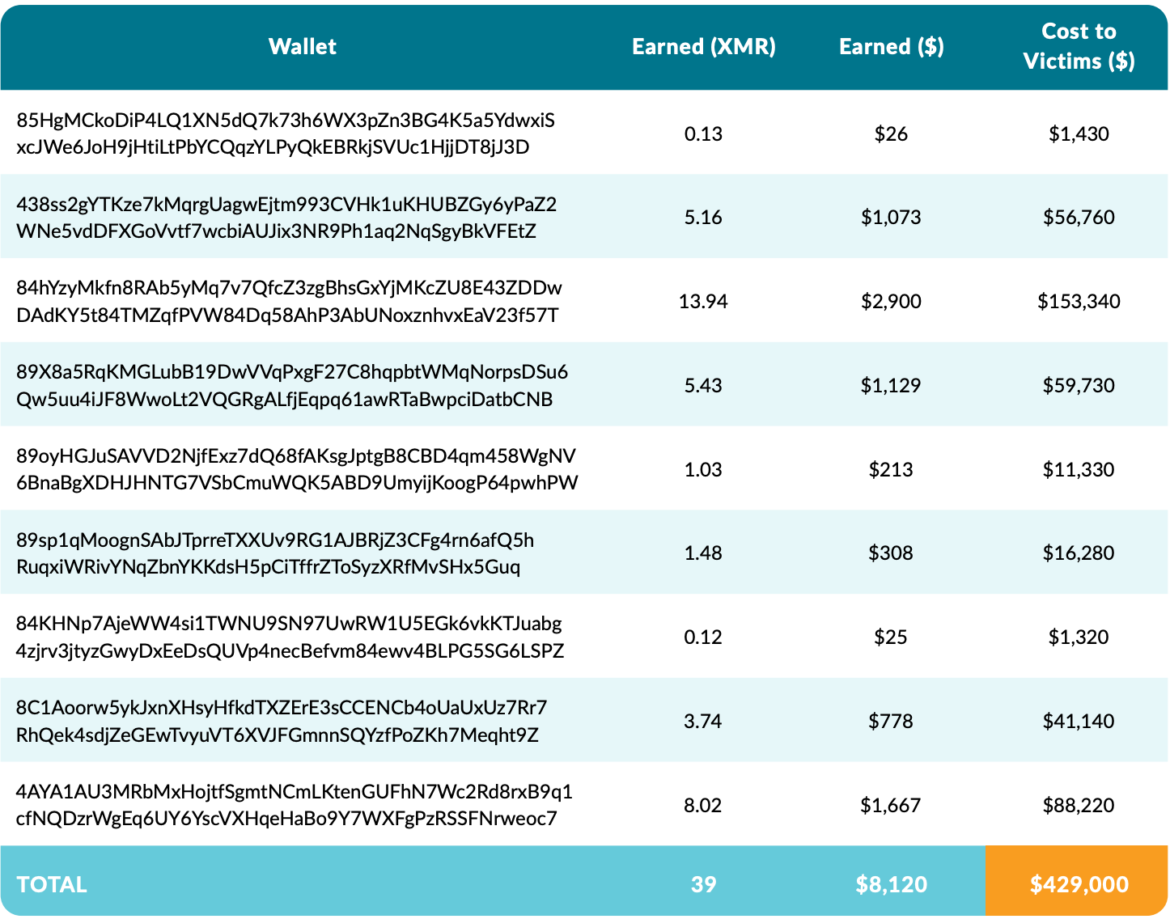
Cryptocurrency Wallets Attributed to TeamTNT
Sysdig researchers conducted several experiments to estimate the cost of the TeamTNT Chimaera operation and other activities to its victims. The “trail of crumbs” that positively correlated to TNT activities was approximately 40 XMR, which amounts to more than $8,000 USD worth of Monero payments to known TeamTNT wallets. The protections Monero provides make getting exact numbers difficult, especially when it comes to older wallets. The true impact is likely much higher.
“The cost of mining 1 XMR on a single AWS EC2 instance is roughly $11,000.”
Better-provisioned instances (such as c6a.8xl) will mine the coin faster, but the cost per hour scales roughly linearly with the amount of vCPUs. There are many possible configurations to increase the cost of an EC2 instance, such as adding additional RAM or storage, but $11,000 is the median cost across many different tested configurations.
“On average, to make $8,100, an attacker will need to drive up a $430,000 cloud bill. They make $1 for every $53 their victim is billed.”
The crypto wallets attributed to TeamTNT by Sysdig TRT are listed in the table above. Dollar values are calculated based on the value of XMR at time of investigation around April 2022, but because cryptocurrency is highly volatile, the real attacker earnings can vary greatly over time, further skewing the ratio of attacker revenue to victim cost.
Conclusion
Cryptomining is the most common outcome of cloud and container-based compromises seen by Sysdig TRT this year.
Many adversaries, such as TeamTNT, solely deal in the mining of cryptocurrencies. It is low-risk and relatively easy to implement compared to extortion activities like Ransomware. Even a lone threat actor like TeamTNT can cause great damage to a company with minimal effort. Other types of attacks, such as espionage, may be occurring, but this year, they flew under the radar.
As threat detection technologies improve for cloud and containers, and become more widely implemented, Sysdig TRT expects to discover more in regards to other malicious activities.
Want more? Download the full 2022 Sysdig Cloud-Native Threat Report.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
7 Cloud Security Lessons from the AWS Crypto Mining Campaign
Published: 03/09/2026
How Attackers Are Weaponizing AI to Create a New Generation of Ransomware
Published: 03/04/2026
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
Core Collapse
Published: 02/26/2026


.png)

.jpeg)

.jpeg)