The Rise of QR Code Phishing Attacks: Exploring Quishing Threats
Published 07/01/2024
Originally published by Abnormal Security.
Bad actors have been using phishing emails to steal sensitive data for three decades. Impersonating a trusted individual or brand and manufacturing a sense of urgency, attackers deceive targets into providing private information like login credentials or bank account details.
Because email wasn’t initially designed with security in mind, early email platforms lacked the native functionality to proactively detect and block phishing attacks. Additionally, threat actors had the benefit of end-user naivete—targets had no reason to believe the sender was anyone other than the person or company they claimed to be.
Over time, however, as email security tools evolved and end users became more aware of common attack ploys, cybercriminals had to adjust their tactics and adopt more sophisticated approaches. QR code phishing, the newest iteration of phishing, is the latest in a long line of malicious initiatives designed by enterprising attackers to evade organizational security measures and manipulate targets.
Hook, Line, and Cybercrime: The Growth of Quishing
This evolution in strategy is part of the broader history of phishing, which is characterized by opportunistic threat actors capitalizing on innovations in communication that have led to an increasingly interconnected world.
For example, spear phishing, a more targeted form of phishing that began to emerge at the turn of the millennium, became a viable option when bad actors realized they could make their attacks more personalized (and more convincing) by harvesting the wealth of data available online.
Similarly, the rise of voice phishing (vishing) and SMS phishing (smishing)—two attack strategies that started gaining prominence in the 2010s—was facilitated by the pervasiveness of cell phones and the popularity of texting. And now, in the 2020s, we have QR code phishing.
There are multiple factors that contributed to the rapid increase in phishing attacks that utilize malicious QR codes:
Ubiquity
Since 2020, scanning QR codes has become a common element of everyday activities like making payments and checking into appointments. Hence, receiving an email requesting we scan a QR code to reset a password or access a document is unlikely to trigger suspicion—a fact attackers exploit.
Novelty
Cybersecurity awareness training underscores the importance of not clicking links in unexpected emails. The advantage of QR codes is that they achieve the same goal of redirecting targets to a phishing page but may not raise alarms the way a standard link-based phishing attack might.
Signal Scarcity
Unlike traditional email threats, quishing attacks contain minimal text content and no obvious URL, which significantly reduces the number of signals available for legacy security tools to analyze and use to detect an attack.
Mobile Device Vulnerability
Using a QR code moves the attack from the recipient’s company-controlled laptop to the target’s personal mobile device, which lacks the lateral protection and posture management available in a cloud-based business environment.
How Threat Actors Use Malicious QR Codes in Phishing Attacks
While malicious QR codes sent via email can be used for a variety of purposes, they are primarily utilized for credential phishing. Indeed, 90% of QR code attacks detected by Abnormal are credential phishing attacks.
In quishing attacks, the QR code is linked to what appears to be a legitimate website (often an emulation of a Google or Microsoft login page) with a prompt to enter login credentials or other sensitive details. Unfortunately, any information provided can then be used by the perpetrator to compromise the target’s account and launch additional attacks.
Multi-Factor Authentication (MFA) Activation
In approximately 27% of all quishing attacks, threat actors send fraudulent notices related to multi-factor authentication (MFA)—as shown in the real-world example of a quishing attack below.

Example of a QR code phishing attack designed to appear as a notification from Microsoft
The cybercriminal attempts to compel the target to scan the malicious QR code by claiming it is the first step in setting up the multi-factor authentication required by their organization. The subtext is that failure to do so will mean losing access to their Microsoft 365 account, which would significantly inhibit their ability to do their job—causing them to be highly motivated to act quickly.
Shared Document Notification
The second most popular strategy, used in approximately 21% of all QR code attacks, is to send targets fake notifications of a shared document. In this example, the attacker informs the target their signature is required on a pending document and claims they can view and sign the document by scanning the included QR code.
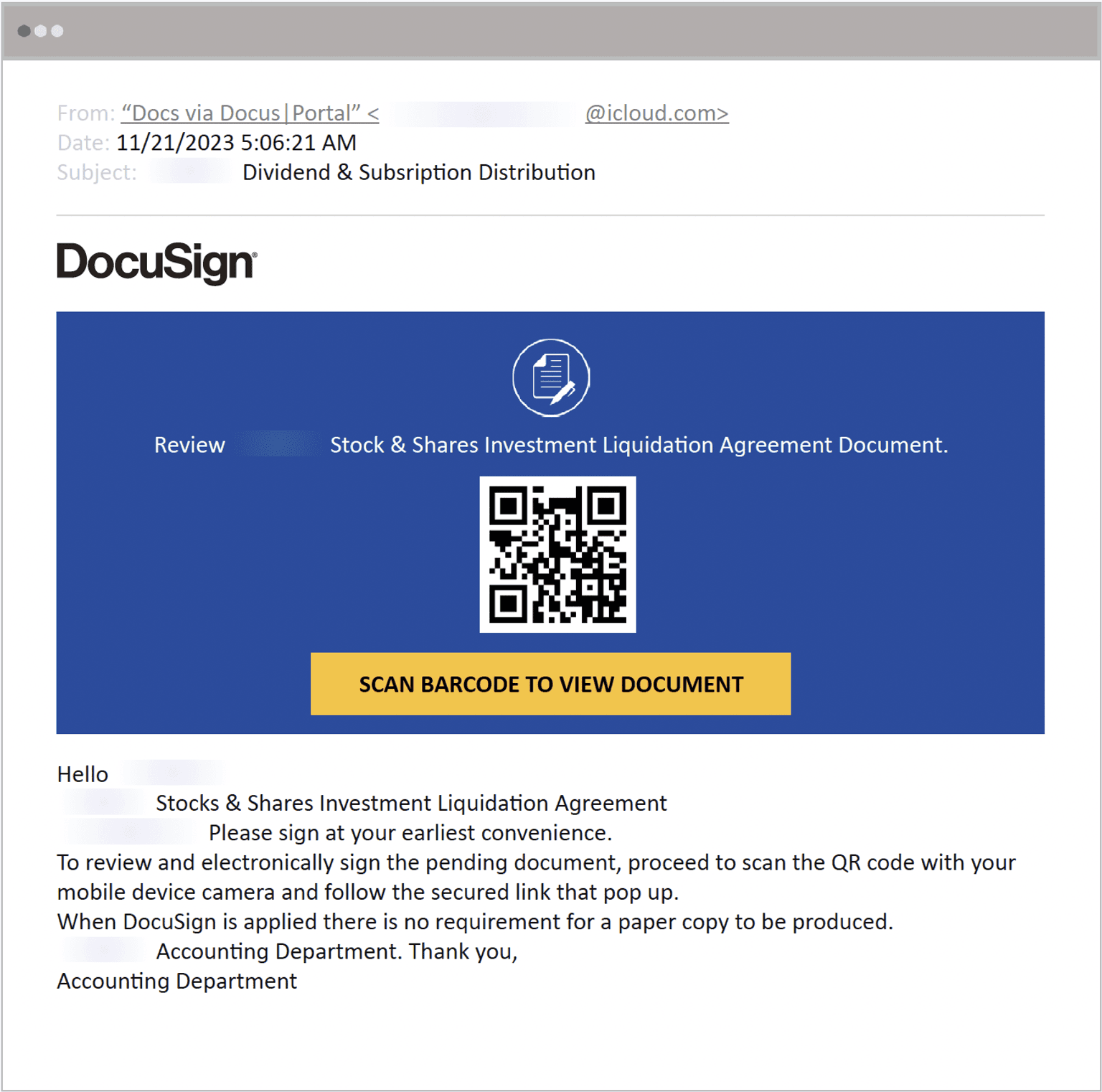
Example of a QR code phishing attack crafted to resemble a DocuSign notification
Quarantined Message Alert
While the most prevalent attack themes center on multifactor authentication and notices of shared documents, these certainly aren’t the only tactics bad actors use in quishing attacks.
Another recurring, albeit less common, strategy is sending targets an email claiming they have messages that have been quarantined by Microsoft 365, as in the following example. By being deliberately vague about what types of messages are on hold, the hope is the target will be enticed to scan the QR code to find out more details.
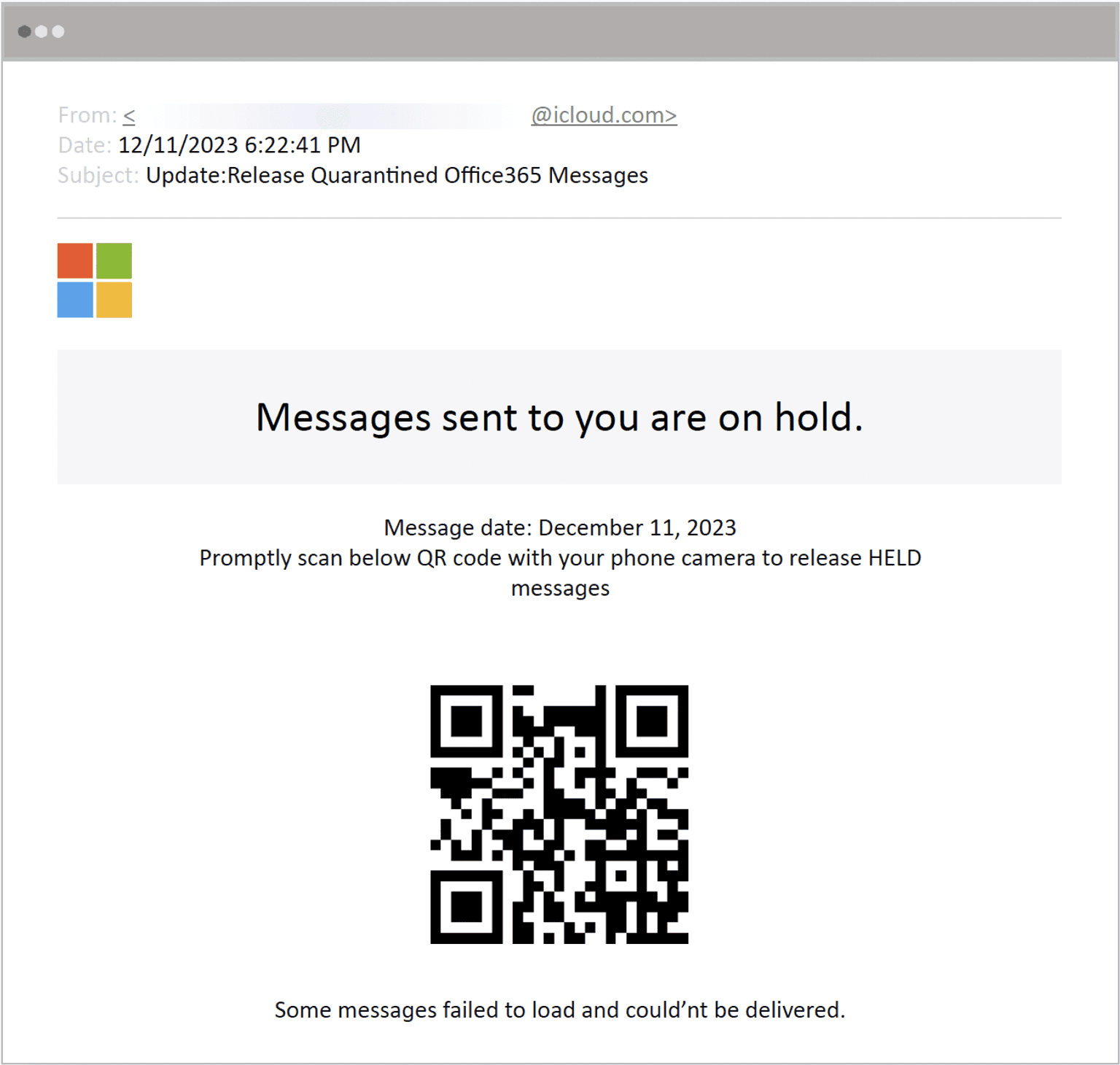
Example of a QR code phishing attack impersonating an alert from Microsoft
In each of the examples above, the perpetrators utilize social engineering to establish trust and manufacture a sense of urgency. For example, they all integrate some level of the impersonated company’s branding into the messages. The threat actor in the first example even goes one step further and incorporates the attack motif into the sender name.
To instill worry and spur action, the MFA-themed attack claims the target is at risk of losing access to important applications. And because the use of DocuSign is generally reserved for important and/or confidential documents, cybercriminals know posing as that company and claiming financial documents are in need of attention will likely convince the target to act quickly.
Additionally, many of the QR code attacks stopped by Abnormal are sent from an iCloud address, as in the last example. Because iCloud.com is a legitimate sender domain, the emails pass SPF, DKIM, and DMARC checks, which improves the likelihood of a legacy security solution marking the email as safe.
Blocking QR Code Attacks to Keep Organizations Safe
Cybercriminals have repeatedly showcased their impressive ability to identify new ways to exploit everyday communication tools to convince employees to reveal confidential information or execute fraudulent transactions.
With the emergence of each new attack strategy, it becomes increasingly evident that traditional email security solutions like secure email gateways (SEGs) are unable to defend against cybercriminals' constantly changing tactics. Organizations must recognize the shortcomings of SEGs and invest in modern solutions that use AI-native detection engines to stop advanced threats like QR code phishing before employees can engage.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026
Agentic AI and the New Reality of Financial Security
Published: 02/26/2026
AI Security: When Authorization Outlives Intent
Published: 02/25/2026
The Visibility Gap in Autonomous AI Agents
Published: 02/24/2026





.png)
.jpeg)


