Zoom Users At Risk In Latest Malware Campaign
Published 03/07/2023
Originally published by Cyble on January 5, 2023.
Modified Zoom App Employed In Phishing Attack To Deliver IcedID Malware
Zoom is a video conferencing and online meeting platform that allows users to host virtual meetings, webinars, and video conference calls. It is available on various devices, such as desktop computers, laptops, tablets, and smartphones, and can be used for personal and business purposes.
Zoom has become increasingly popular in recent years, particularly due to the COVID-19 pandemic, which has increased remote work and the need for virtual communication tools. Threat Actors (TAs) generally target these types of software tools to deliver malware to the user’s machine.
Cyble Research & Intelligence Labs (CRIL) recently identified a phishing campaign targeting Zoom application software to deliver the IcedID malware. IcedID, also known as BokBot, is a banking trojan that enables attackers to steal victims’ banking credentials. This malware primarily targets businesses and can be used to steal payment information. In addition, IcedID acts as a loader, allowing it to deliver other malware families or download additional modules.
IcedID usually spreads via spam emails with malicious Office file attachments. However, in this campaign, the attackers employed a phishing website to deliver the IcedID payload, which is not a typical distribution method for IcedID.
The TAs behind this campaign used a highly convincing phishing page that looked like a legitimate Zoom website to trick users into downloading the IcedID malware, which carries out malicious activities.
The attackers set up a phishing website that contained a download button. When users clicked on the button, they were prompted to download a Zoom installer file from the URL: hxxps[:]//explorezoom[.]com/products/app/ZoomInstallerFull[.]exe. However, the file was a disguised version of the IcedID malware. The figure below shows the Zoom phishing site.
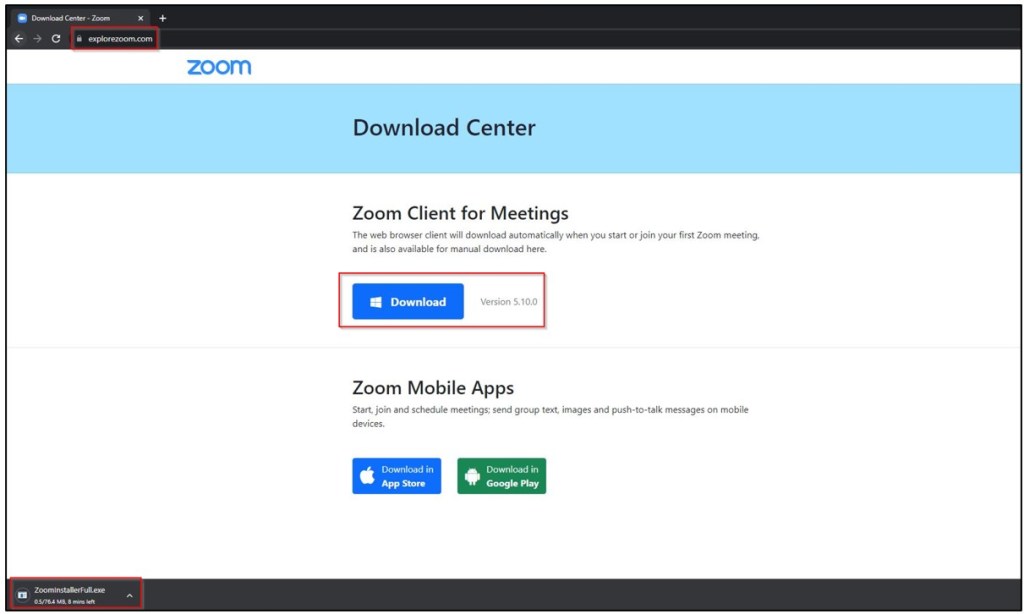
Figure 1 – Phishing page downloading malicious Zoom installer
Technical Details
Upon execution of the “ZoomInstallerFull.exe” file, it drops two binaries in the %temp% folder:
- ikm.msi
- maker.dll
The “maker.dll” is a malicious DLL file that carries out various malicious activities, while “ikm.msi” is a legitimate installer that installs the Zoom application on the user’s computer. The below figure shows the dropped binary file in the %temp% location.

Figure 2 – DLL & Installer file dropped in a temp folder
After the binary files are dropped, “ZoomInstallerFull.exe” executes “maker.dll” using rundll32.exe with the “init” parameter. To avoid suspicion, it also runs the “ikm.msi” installer, which installs the Zoom application in the %programfiles% directory, as shown below. This helps TAs conceal their true intentions and trick users into thinking they are simply installing a legitimate version of Zoom.
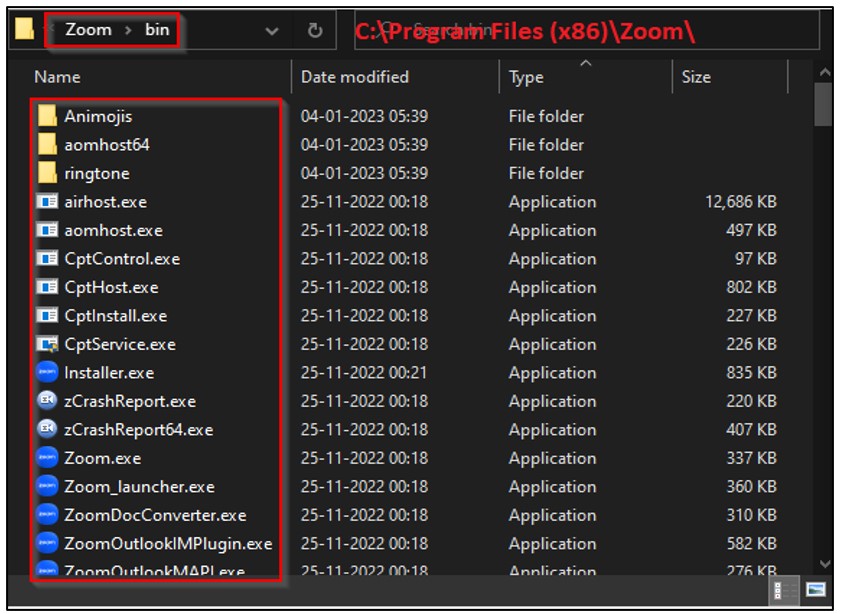
Figure 3 – Zoom application installed directory
The figure below shows the Process Tree of the malicious Zoom software installer.

Figure 4 – Process tree of Zoom installer
Analysis
The “maker.dll” is a malicious DLL file that is used to load the IcedID malware. When it is executed, it retrieves the original IcedID DLL file and loads it into the memory, as shown below.

Figure 5 - Unpacked actual IcedID payload in memory of IcedID loader
The IcedID malware, which has been loaded in memory, is a 64-bit DLL file with the following SHA256 hash: 2f3dddb9952e0268def85fbe47f253056077894ce6bd966120654324787b83be.
Additional information is shown in the figure below.

Figure 6 – Static File information
Upon execution, the malware performs a decryption operation and obtains the Command & Control (C&C) URL and the Campaign ID, as shown below.

Figure 7 – Code snippet to decrypt C&C URL and Campaign ID
Then, the malware uses various Windows API functions, such as GetTickCount64(), ZwQuerySystemInformation(), RtlGetVersion(), GetComputerNameExW(), GetUserNameW(), GetAdaptersInfo(), LookupAccountNameW() and CPUID, to gather system information from the victim’s machine, which it then converts into numerical data.
The code snippet shown in the figure below demonstrates how the malware extracts system details.

Figure 8 – Code snippet to extract the victim’s system information
C&C Communication
Finally, the malware assigns an ID to the converted numbers and sends them to the C&C server as a “Cookie”, as shown in the figure below.

Figure 9 – Exfiltrated data
The table below provides a description of the IDs that are used in the “Cookie” by the malware.
| Name | Description |
| __gads | Campaign ID, a response flag from the server, the value of GetTickCount64(), and system information gathered using ZwQuerySystemInformation() function. |
| _gat | Windows version information obtained using the RtlGetVersion() function. |
| _ga | Processor information obtained using the CPUID function. |
| _u | Computer name obtained using GetComputerNameExW(), the username obtained using GetUserNameW(), and information about whether the victim’s machine is running in a virtual environment. |
| __io | SID (Security IDentifier) value obtained using LookupAccountNameW(). |
| _gid | Adapter information for the local computer obtained using GetAdaptersInfo() function. |
The malware connects to the C&C server using the code snippet shown in the figure below.

Figure 10 – Code snippet used to connect the C&C server
If the malware can successfully connect to the C&C server, it can drop an additional malware file in the %programdata% directory. The code snippet shown in the image below demonstrates how the downloaded file is written to the %programdata% location.

Figure 11 – Code to write downloaded malware file from C&C
At the time of analysis, the Command-and-Control (C&C) server was not functioning, and the end payload responsible for performing banking trojan activity could not be analyzed.
Conclusion
IcedID is a highly advanced, long-lasting malware that has affected users worldwide. It has frequently been distributed as a subsequent payload by various well-known threats such as Emotet, TrickBot, and Hancitor. IcedID is usually spread through spam emails containing malicious Office file attachments.
The threat actor utilized a phishing site in this specific campaign to deliver the IcedID payload. Threat actors are constantly adapting their techniques to evade detection by cybersecurity measures. Cyble Research & Intelligence Labs is continuously monitoring the activity of IcedID and other malware and will keep our readers updated.
Our Recommendations
- Avoid downloading pirated software from warez/torrent websites. The “Hack Tool” present on sites such as YouTube, torrent sites, etc., contains such malware.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices.
- Use a reputed anti-virus and internet security software package on your connected devices, including PC, laptop, and mobile.
- Refrain from opening untrusted links and email attachments without first verifying their authenticity.
- Educate employees on protecting themselves from threats like phishing/untrusted URLs.
- Block URLs that could be used to spread the malware, e.g., Torrent/Warez.
- Monitor the beacon on the network level to block data exfiltration by malware or TAs.
MITRE ATT&CK® Techniques
| Tactic | Technique ID | Technique Name |
| Execution | T1204 T1059 | User Execution Command and Scripting Interpreter |
| Defense Evasion | T1218 T1027 T1497 | Rundll32 Obfuscated Files or Information Virtualization/Sandbox Evasion |
| Discovery | T1082 T1518 T1083 T1087 | System Information Discovery Security Software Discovery File and Directory Discovery Account Discovery |
| Command and Control | T1071 T1095 | Application Layer Protocol Non-Application Layer Protocol |
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 9108e1d22d74bc5397b8886edc4f0a84b8906436a648ef8a86f30cf7e08978dd | Sha256 | ZoomInstallerFull.exe |
| 3c9cd4cf008ed70df41cc270c77055f6edac139ec7ec2a9c3de1b21c1a294ca7 | Sha256 | Maker.dll (IcedID loader) |
| 2f3dddb9952e0268def85fbe47f253056077894ce6bd966120654324787b83be | Sha256 | IcedID payload |
| hxxps[:]//explorezoom[.]com/products/app/ZoomInstallerFull[.]exe | URL | Zoom download link contains IcedID loader DLL |
| Trbiriumpa[.]com | Domain | C&C |
| 143.198.92.88 | IP | C&C |
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026


.png)
.jpeg)


