DNS-Layer Security: The Ultimate Guide to What It Is and Why You Need It
Published 12/09/2021
 Originally Published by Cisco on March 10, 2020.
Originally Published by Cisco on March 10, 2020.
Written by Lorraine Bellon, Cisco.
If you’re like most people, you probably don’t pay much attention to the domain name system (DNS) or worry about investing in cloud-based DNS-layer security. After all, the hallmark of well-functioning DNS servers is their invisibility – their ability to connect users to websites or internet-enabled applications correctly and without delay. But this invisibility comes with a catch. Since most organizations don’t bother to secure the DNS layer, bad actors frequently use it to stage cyberattacks.
In today’s article, we’re taking a deep dive into the domain name system – what it is, how it works, and how investing in cloud-based DNS-layer security can help transform your network security for the better.
The Basics of DNS
Before jumping into DNS-layer security, it’s important to understand the fundamentals of the domain name system. People often refer to DNS as the, “phone book of the Internet.” That’s because every device on the Internet – from your personal computer to the servers hosting websites – has an Internet Protocol (IP) address that consists of a unique series of numbers. Connecting to another device requires knowing its associated IP address, much like connecting to another phone requires knowing its associated phone number.
If you happen to have the information off-hand, you can type an IP address directly into a browser. For example, if you know that the IP address for the Cisco Umbrella website is 67.215.70.40, you could use that address to connect directly to that website. But you’d probably find it much simpler to type in umbrella.cisco.com.
The domain name system was invented so that people wouldn’t have to remember long IP addresses. Instead, they could visit websites using human-friendly names like umbrella.cisco.com. And since there are too many websites on the Internet for a computer to store a comprehensive list of corresponding domain names and IP addresses, this task is outsourced to designated DNS servers. You probably use DNS thousands of times a day without knowing it – every time you connect to a website, open a mobile phone app, or update software, your device queries DNS servers to find the IP address associated with the domain. That’s why we often refer to DNS as the foundation of the internet.
Recursive and Authoritative DNS Servers
Research cloud-based DNS-layer security solutions and you’ll quickly find that they come in two varieties: recursive DNS security and authoritative DNS security. Understanding the difference between these two options requires knowing a bit more about how the domain name system works.
Let’s go back to our phone book analogy for a moment. Imagine you sit down at your computer and type umbrella.cisco.com into your browser. Your browser needs a copy of the phone book in order to find the corresponding IP address for that domain, so:
- Your computer connects to a recursive DNS server (sometimes called a DNS resolver). There are thousands of recursive DNS servers across the world, and most users rely on the resolvers provided by their ISP or cellular provider.
- Your computer asks the recursive DNS server, “What’s the IP address assigned to umbrella.cisco.com?”
- The recursive DNS server connects to an authoritative DNS server that holds a copy of the phone book matching the IP address of the Cisco Umbrella website with its associated domain name.
- The authoritative DNS server sends the right IP address to the recursive DNS server, which sends the information back to the computer (and browser) that requested it.
- Your computer connects to the Cisco Umbrella server using the IP address, allowing the website to load.
Whew, that was easy! Well, it was easy for the computer and DNS servers at least – this whole process usually happens so quickly that users don’t notice it happening unless something goes wrong. But plenty can go wrong – a DNS server outage will prevent users from connecting to websites, while slow DNS servers will bring website load times to a crawl. And that’s not even accounting for DNS security compromises.
Are DNS Servers Secure?
You’d think that a system which functions as the bedrock of internet connectivity would be designed with cybersecurity in mind. Unfortunately, that’s just not the case. In fact, unless you’ve invested in DNS-layer security, odds are that none of the solutions in your security stack even inspect DNS activity. In most instances, DNS packets – which normally contain IP address information – enter networks through unblocked ports without first being inspected by security protocols. Furthermore, DNS activity in a network is almost never monitored. This makes the DNS layer into the perfect blind spot for cybercriminals to exploit.
Many of today’s sophisticated attacks rely on DNS activity. Malware, ransomware, phishing, and other scams often use DNS to stage the internet infrastructure used to support each stage of their attacks. For example:
- DNS tunneling is often used to deliver payloads encoded in DNS queries and responses, exfiltrate data from compromised networks, and execute command and control attacks
- DNS beaconing is often used to establish communication with a command and control server using only DNS, which is almost always allowed in a network
These tactics, techniques, and procedures (TTPs) often play a prominent role in modern cyberattacks. Many high-profile ransomware attacks featured DNS beaconing, the supply-chain attack SUNBURST leveraged DNS tunneling during post-exploitation, and the APT group OilRig frequently uses DNS tunneling for data exfiltration. So, what can you do to secure DNS activity on your network?
How DNS-Layer Security Helps Stop Cyberattacks
Since all internet activity is enabled by DNS, something as simple as monitoring DNS requests – as well as their subsequent IP connections – can go a long way when it comes to securing your network. Ensuring you have security protocols in place to flag anomalous DNS activity can provide better accuracy and detection of malicious activity and compromised systems, improve security visibility, and enhance network protection.
If you want to go a step further, you can partner with a secure DNS vendor that will allow computers on your network to use proprietary recursive DNS servers. Your vendor will configure these servers to identify dangerous DNS activity and implement security protocols that block harmful DNS connections. Nothing stops attacks earlier than DNS-layer security. After all, DNS is the first step in making a connection on the Internet. If a dangerous connection is blocked at the DNS layer, the attack stops there.
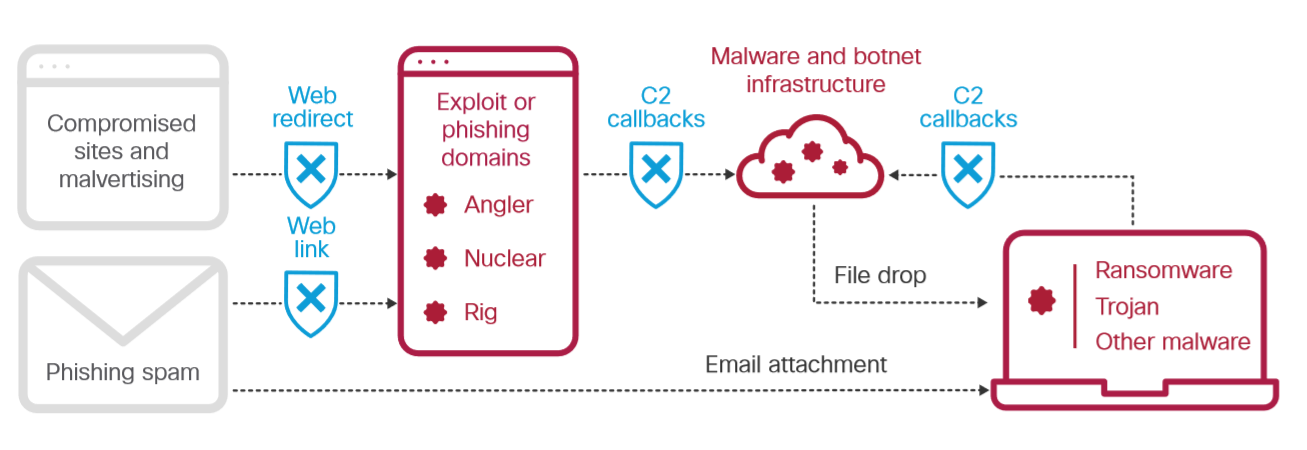
Figure 1: The blue shields show where DNS-layer security stops attacker communications.
In the figure above, you can see how DNS-layer security identifies where malicious domains and other dangerous internet infrastructures are staged. Secure DNS servers then block requests coming from these staging sites over any port or protocol, preventing both infiltration and exfiltration attempts. DNS-layer security stops malware earlier and prevents callbacks to attackers if infected machines connect to your network.
The best part is that deploying a cloud-based DNS-layer security solution can be an easy lift for IT teams. In fact, some solutions can be deployed in minutes, providing you with robust cybersecurity protection almost immediately.
This makes DNS-based security an attractive option for small businesses or for larger enterprises looking for immediate protection while they roll out a more robust cloud-based cybersecurity infrastructure.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Agentic AI Pen Testing: Speed at Scale, Certainty with Humans
Published: 01/26/2026
My Top 10 Predictions for Agentic AI in 2026
Published: 01/16/2026


.png)


.jpeg)
