How Global Conflicts Influenced Cyber Attack Behaviors
Published 02/16/2023
Originally published by Sysdig.
Written by Michael Clark, Sysdig.
The conflict between Russia and Ukraine includes a cyberwarfare component with government-supported threat actors and civilian hacktivists taking sides.
The goals of disrupting IT infrastructure and utilities have led to a 4-fold increase in DDoS attacks between 4Q21 and 1Q22. Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub. The threat actors hit anyone they perceive as sympathizing with their opponent, and any unsecured infrastructure is targeted for leverage in scaling the attacks.
Most of the time, Sysdig TRT finds financial gain is the primary motivation for attacks in the cloud and on containerized workloads. However, motives such as espionage and political or military objectives also play a role.
Cryptomining is the most common approach on the financial gain front, followed by Distributed Denial of Service (DDoS). It is easy to understand why cryptomining is so popular, due to the ease of turning compromised assets into profit and the relatively low risk to the attacker. As seen with adversaries like TeamTNT, it costs the attacker relatively little to establish infrastructure to run attacks and set up the cryptomining operations. Meanwhile, the victim of the attack may end up losing hundreds of thousands of dollars in stolen infrastructure costs.
This article is part of the 2022 Sysdig Cloud-Native: Threat report.
Russia-Ukraine Conflict
The Russo-Ukrainian war began in 2014, but escalated substantially with the armed Russian invasion on February 24, 2022.
Various hacktivist and cybercriminal organizations quickly started to align themselves with the various conflict participants. For example, Anonymous announced support for Ukraine while Killnet backed Russia. The Ukrainian government also facilitated communication with allied cybergroups through a Telegram channel in order to provide targeting information.
DDoS Attacks on the Rise
From January through July 2022, the Sysdig TRT global honeynet system captured numerous breaches through multiple attack vectors. The incoming attacks are categorized as DDoS, Cryptomining, or something else based on the type of malware leveraged, noted TTPs, and other context. DDoS agents are often added to botnets, which attackers use in their DDoS-as-a-Service operation. Threat actors can make money by renting out their botnet to other parties. Other types of malware, such as reverse shells, were discarded for the purposes of this comparison.
When comparing the attack types between Q4 of 2021 and Q1 of 2022, there is a clear shift away from cryptomining and toward DDoS activity.
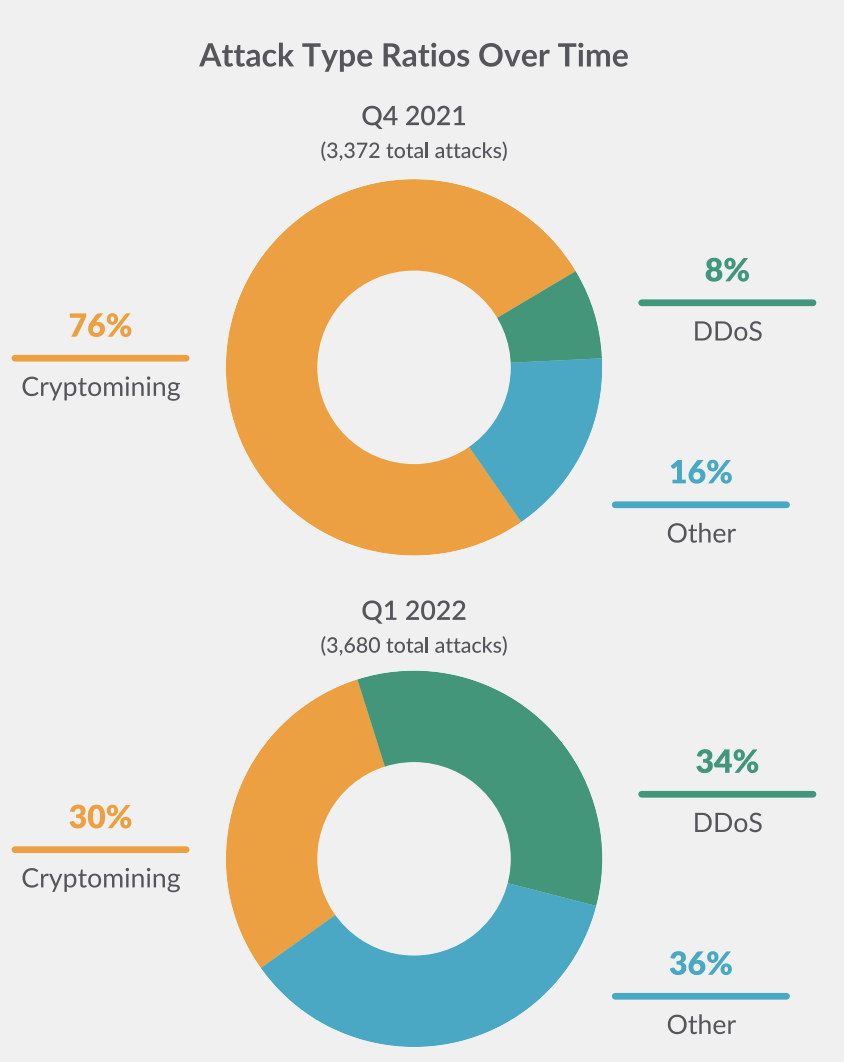
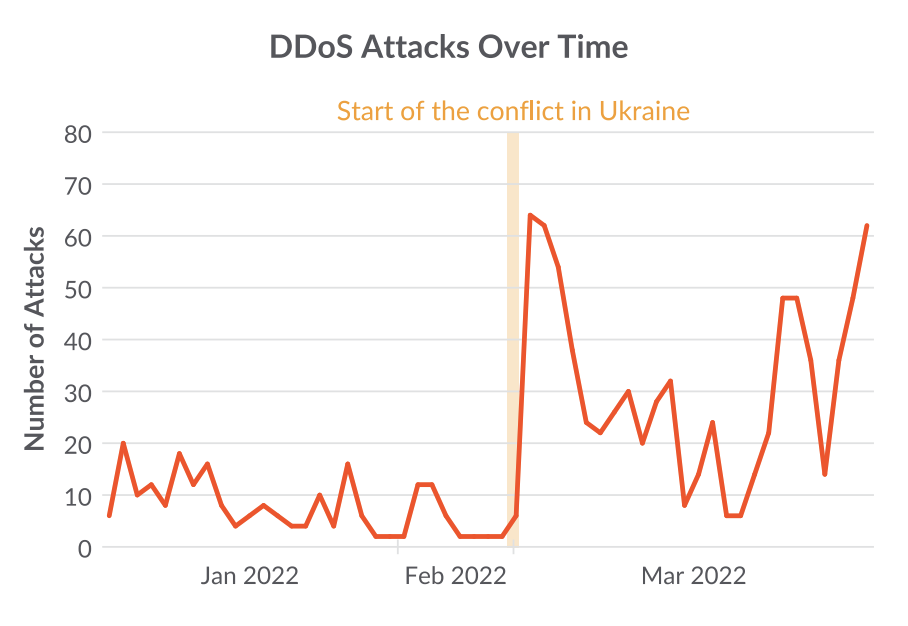
Sysdig TRT data also showed a large overall increase in the amount of DDoS malware being installed throughout the honeynet around the time of the conflict escalation.
In order to conduct successful DDoS campaigns in response to a specific political event, cybercriminal groups need to rapidly scale up their botnets infrastructure. The most common use of the botnet involves taking down websites for the duration of the attack. These DDoS attacks may result in civil, social, or economic damage depending on what is targeted and the attacker’s goal.
For example, at the start of the conflict, pro-Russian DDoS attacks were able to disrupt access to Ukrainian financial institutions.
DDoS Malware Installs
Cloud Hosted Websites Targeted
One of the pro-Russian hacktivist groups, called Killnet, launched a number of DDoS attacks on NATO countries. These included, but are not limited to, websites in Italy, Poland, Estonia, Ukraine, and the United States. Because many sites are now hosted in the cloud, DDoS protections are more common, but they are not yet ubiquitous and can sometimes be bypassed by skilled adversaries.
Much of Killnet’s coordination for these attacks was conducted via the messaging service Telegram. Members of the channel were provided with scripts to run the attack and a list of targets. During Killnet’s attack, they used a variety of DDoS methods, including the traditional SYN-Flood, where TCP SYN packets are sent in large numbers causing the target machine to try to open connections and waste resources. However, this approach is often successfully mitigated by CSPs. IP Stressing services, aka DDoS-as-a-Service, were also leveraged. While these attacks were not sophisticated, they were successful in causing outages at sites owned by the Italian government and the United States Congress.
To bypass CSP protections, Killnet also used Layer 7 attacks, which involve targeting the application directly. For example, sending large amounts of legitimate requests to the web server can end up causing a service outage as the application runs out of resources. The data sent is randomized and originates from different sources, making it difficult for typical mitigating controls, such as WAFs, to defend against the attack.
A combination of protections is the best way to counter this type of activity, including ensuring ample bandwidth, creating a wealth of resources on the systems being attacked, dropping traffic before it reaches the site, and modifying a WAF to handle as much of the attack as possible.
Hacktivist Enablement via Malicious Container Images
New technologies like containers were used in this conflict to quickly crowdsource participation in attacks. Container images are set up with all the tools an attacker would need to join a malicious campaign within minutes with very little prior knowledge required.
In a hacktivist movement, coordination of the masses is critical. Containers pre-loaded with DDoS software make it easy for hacktivist leaders to quickly enable their volunteers. Sysdig TRT analyzed the data collected from hundreds of thousands of images gathered from Docker Hub, looking for attributes and IoCs that can be connected to the Russia-Ukraine conflict.
The two factions are using different methods and approaches to deploying these container images. Russia is keeping secret as much information as possible, while Ukraine and its allies are trying to share the information publicly to reach more and more people, thus enhancing their capabilities.
“Over 150,000 volunteers have joined anti-Russian DDoS campaigns using container images from Docker Hub.”
The following table shows the most-downloaded Docker Hub images that have been used to perform DDoS attacks against Russian and Belarusian websites:
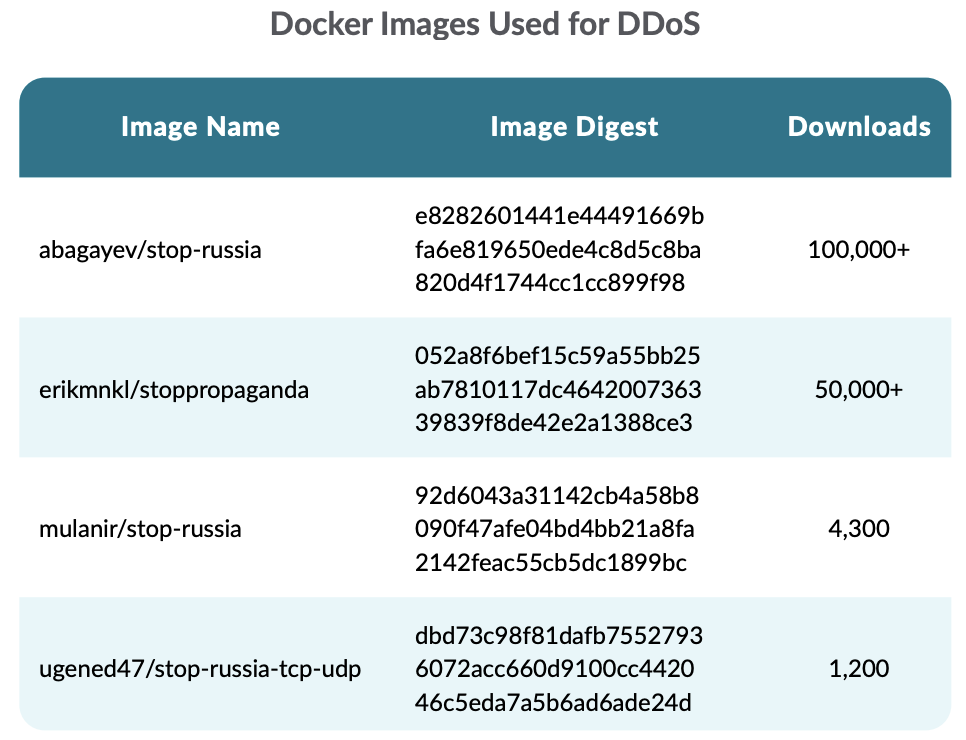
abagayev/stop-russia uses an HTTP benchmarking tool called bombardier to generate a high load of HTTP requests against the targets. By default, the image provides a list of targets for the tool.
erikmnkl/stoppropaganda provides different options for the usage, as shown in its Github repository. It can also be run on Kubernetes and Android. They recommend using the “IT ARMY of Ukraine” Telegram channel as the primary source of the target websites.
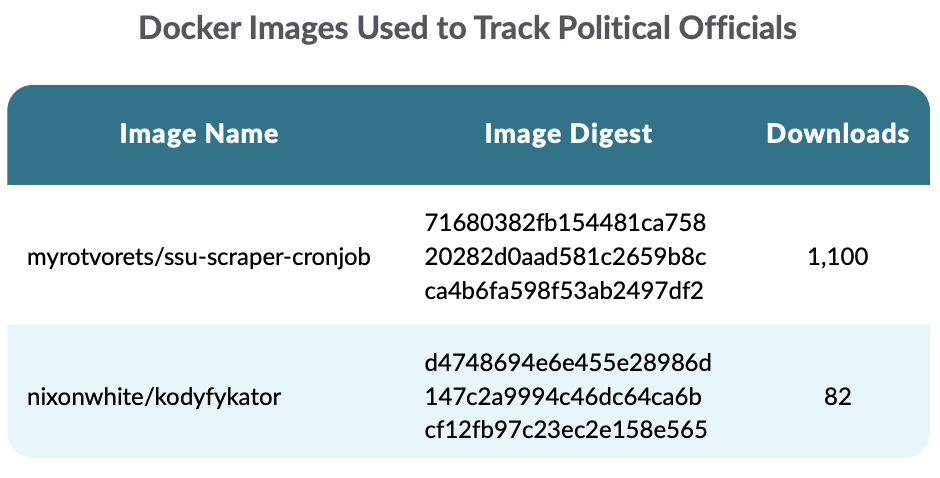
Moreover, other images were found to be related to the war. Specifically, the following images have been used, respectively, to scrape the list of persons wanted by the Security Service of Ukraine.
Despite the temporary geopolitical shift in motivations, the primary, persistent goal Sysdig TRT observes across attackers is still financial gain. This likely won’t change any time soon due to the clear advantages of cryptojacking. It is very lucrative, due to the scalability of the cloud, and poses a very low risk for the threat actors.
Conclusion
2022 saw major events around the world, especially the conflict between Russia and Ukraine.
This war did not contain itself to the physical realm, but involved significant cyber warfare. Both governments and militaries were heavily involved in conducting these operations, but the civilian populace around the world joined as well. Whether it was patriotism, a desire to support the side politically identified with, or wanting to play a role in a large, publicized event, a significant number of people tried to contribute. One way this played out was in the shift from cryptomining malware installations on honeypots to DDoS agents, which were used to attack the other side’s web infrastructure.
Over time, this trend seems to have reversed as the initial fervor has subsided.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates






