Living-off-the-Land Attack: PowerDrop
Published 07/27/2023
Originally published by ThreatLocker.
On June 6, 2023, Adlumin Threat Research discovered a living-off-the-land attack, PowerDrop, using a malicious PowerShell script to target the US aerospace industry.
LOTL attacks leverage powerful built-in tools to masquerade as legitimate processes. Therefore, they do not trigger any alerts. Here’s how PowerDrop was able to use this to its advantage.
PowerDrop Analysis
PowerDrop can be classified as a Remote Access Tool (RAT). This type of malicious software allows threat actors to control a computer or device from a remote location without the user's knowledge or permission.
The PowerDrop attack technique seems to be a mixture of off-the-shelf malware, better known as commonly used malware, and advanced persistent threat (APT) practices that can bypass next-generation anti-virus (NGAV) or malware detection (EDR, VDR). APTs are known to be one of the most dangerous types of attacks as they are usually state-sponsored, have a generous operating budget, and select high-value targets, like the US aerospace industry, solely for the purpose of data exfiltration. Once an APT has a foothold in an organization, they often remain there for months, slowly collecting and stealing data unbeknownst to their target.
The PowerDrop attack is initiated by a PowerShell script that then triggers Windows Management Instrumentation (WMI) to remotely execute the malicious code across multiple machines within the victim's network through a WMI event filter. WMI is commonly used by system administrators, software developers, and security analysts to manage and monitor Windows-based systems. It provides a convenient way to automate tasks, gather system information, and troubleshoot issues on many Windows computers; therefore, it is a vital component of the Windows OS.
Once the WMI commands execute, information is forwarded to the attacker's C2 Server or Command and Control Server. This information includes which computers are infected, internal IPs, hostnames, and more. Once this information is processed, attackers can clearly see the layout of the network and which computers they have control over.
Why was this able to go undetected for so long?
The goal of an APT actor is to stealthily remain in an organization's network while collecting copious amounts of data for a future agenda. In the case of PowerDrop, the hackers were able to remain undetected for an extended time for various reasons:
- PowerDrop used ICMP (ping request) to keep track of whether these machines were in an active state.
- PowerDrop has a 120-second interval for network traffic. This means the system waits 120 seconds to send traffic or request traffic from the victim's machine; this makes it harder to detect as thousands of logs flood a system per second. Therefore, the higher the wait interval, the harder malware is to detect, as it appears much less often within network logs.
- It also runs once as a single PowerShell command. Therefore, no PowerShell file (PS1) must live within the victim's machine to take effect, making detection, analysis, or dissection of the malware harder.
How to Prevent
This is not the first time we’ve seen PowerShell weaponized. In 2022, the Follina MSDT attack introduced users to a malicious web server where a payload was then issued. PowerShell continues to be the tool of choice for sophisticated attacks. How should users safeguard themselves from the tools designed to help their business?
The term Zero Trust has become an increasingly popular concept as a means of stopping modern-day attacks, as seen in the White House's Executive Order and, more recently, CISA’s #StopRamsomware Guide. Application control has been identified as a proactive measure of cybersecurity, protecting users against malicious scripts; and, more specifically, application containment tools, Ringfencing™. This is an emerging concept in the endpoint security space, as administrators are able to implement granular policies to limit certain interactions with applications and native tools like PowerShell.
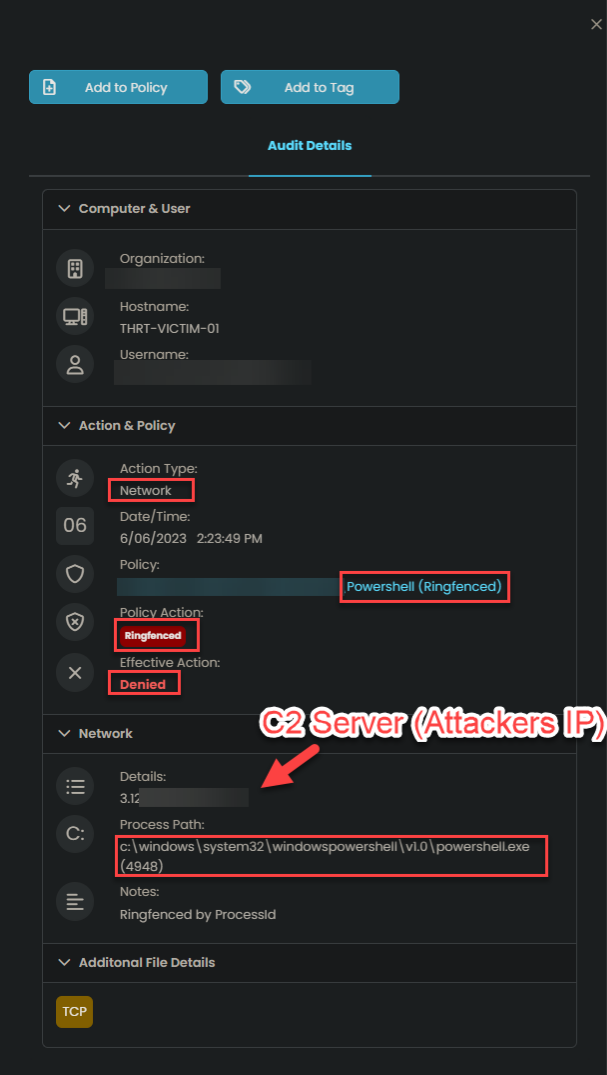
In the case of PowerDrop, application containment policies on an endpoint would have prevented PowerShell from calling out to the internet. Therefore, thwarting the attack and prohibiting the weaponization of PowerShell.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Zero Trust for Agentic Pipelines That Touch Cloud Production
Published: 02/27/2026
Core Collapse
Published: 02/26/2026
AI Security: When Authorization Outlives Intent
Published: 02/25/2026





.png)
.jpeg)
.jpeg)

