What to Do After Receiving a Phishing Attack
Published 09/06/2023
Originally published by Abnormal Security.
Written by Emily Burns.
Phishing is an increasingly common form of cyberattack that relies on social engineering tactics and malicious links to gain access to confidential data or financial accounts. In fact, over the past two years, phishing has been the most widespread email attack detected by Abnormal, comprising 70% of all advanced threats in the second half of 2022.
Moreover, the FBI's Internet Crime Complaint Center (IC3) reported that phishing was the most frequent cybercrime in 2019 and experienced a 162% rise between 2019 and 2022. In 2022, the IC3 documented over 300,000 phishing cases, five times larger than the second-most common form of cybercrime.
Although phishing is in the bottom third of all attack types in terms of losses, according to IC3, many organizations underestimate the danger it presents. It is important to note, however, that phishing is typically used as a means of gaining access to a system or network, rather than the ultimate objective itself. It’s a serious threat to both individuals and businesses, and it’s important to be aware of the risks it poses.
In this article, we will explore why phishing attacks work, provide a real-world example of a successful attack, outline how to respond effectively if you fall victim to one, and show you how to detect and block them in the future. By understanding the dangers posed by phishing attacks and following our recommendations, you will be on the way to ensuring your data remains secure.
Why Phishing Attacks Work
Phishing attacks prey on human emotions and trust. Threat actors will leverage social engineering tactics to trick users into clicking on malicious links or providing confidential information. Attackers may also use seemingly trusted identities to trick employees into clicking on phishing links. The subsequent fraudulent phishing sites are intricately crafted to look identical to real sign-in pages, making it tough for employees to discern a malicious page from a real one.
Legacy email security technologies, such as secure email gateways (SEGs), are capable of preventing basic phishing attacks that contain malicious links and/or suspicious attachments, and come from domains with known-bad reputations. However, they are unable to protect against more sophisticated phishing messages that use social engineering and email spoofing–and may not necessarily contain any attachment or link payload.
As soon as an employee engages with a phishing email, the organization is placed in a precarious position. It is therefore essential to prevent phishing emails from reaching employee inboxes, whether they are disguised as a well-known brand, an internal system, or a trusted individual. By understanding how and why these attacks work, businesses and individuals can take steps to protect themselves from falling victim.
Example of a Phishing Attack
The following phishing attempt was created by ChatGPT. Generative AI language models have the ability to easily compose a convincing phishing email with exact grammar and prompt action, making it extremely difficult for the average recipient to distinguish between a safe communication and a malicious one.
Below is an example of a ChatGPT-created email requesting invoice payment that a cyberattacker could employ in an effort to commit payment fraud.
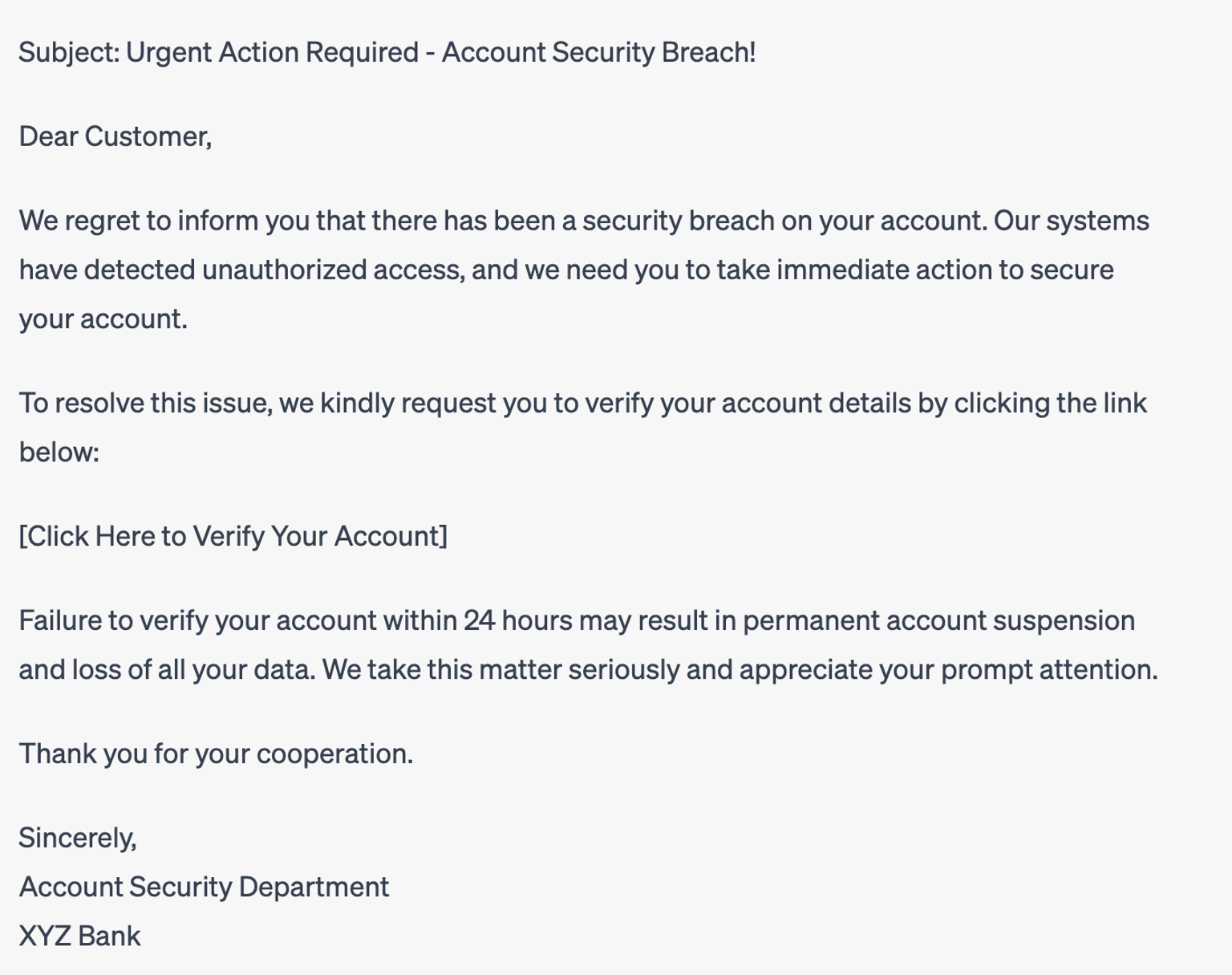
In this example, there are several red flags indicating that it may be a phishing email:
- Urgency and Fear: The email creates a sense of urgency, emphasizing an account security breach and the potential consequences if immediate action is not taken. Phishers often use fear tactics to pressure recipients into acting hastily.
- Generic Greeting: The email starts with a generic salutation like "Dear Customer" instead of addressing you by name. Legitimate organizations usually use your name in their communications.
- Suspicious Link: The email contains a link urging you to click to verify your account details. Phishing emails often include malicious links that lead to fake websites designed to steal your personal information.
- Lack of Personalization: The email doesn't include specific details about your account or any personalized information, indicating that it may be sent to a large number of recipients.
- Poor Grammar or Spelling Mistakes: Phishing emails often contain grammatical errors or typos. In this example, there are no major errors, but it's always worth being cautious if you notice such mistakes.
An Effective Phishing Response
Phishing attacks can be devastating to businesses and individuals alike. But with an effective response plan, damage can be significantly reduced. The following steps will help you combat phishing attacks before they take hold of your organization.
1. Identify
The first step is to identify the phishing attack. Most of the time attackers use emails from a legitimate source or malicious links that appear in messages. It’s important to recognize common signs of phishing attacks (or indicators of compromise) such as poor grammar, typos, generic salutations (e.g., “Dear Customer”), requests for confidential information (e.g., credit card numbers), and links leading to unknown websites with strange URLs (e.g., http://www…). By being aware of these common signs of fraudulence, you can stay one step ahead of potential scammers.
2. Contact the Source
If you receive any emails that seem out of character or contain unexpected requests for sensitive information, be sure to double-check with the sender before responding. Additionally, if you come across any links in an email that ask for personal data such as bank account numbers or usernames and passwords — don’t click on them!
3. Report
Once you have identified a potential phishing attack, it’s important to alert your IT team or cybersecurity provider straight away so they can investigate the incident further and take steps to mitigate the damage caused by the attack. This may include changing passwords and disabling access for suspicious users.
Detecting and Blocking Phishing Attacks
Being aware that malicious emails could be targeting your organization is a start, but it is not enough. To truly protect against these threats, security leaders must take action to ensure that these emails never reach employees’ inboxes in the first place. Security tools employ a fundamentally different approach to email security, leveraging AI-powered detection technology that looks out for potential threats based on context analysis and threat intelligence data; helping businesses protect against phishing scams.
As attackers change their methods and rely on social engineering to trick employees, security is more important than ever. The best way to stay safe? Stop these attacks before they reach you or your inbox.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Core Collapse
Published: 02/26/2026





.png)
.jpeg)


