3 Ways Cybercriminals are Targeting Your Email
Published 09/20/2023
Original published by Abnormal Security.
Written by Mike Britton.
It wasn't long ago that the world was much simpler when it came to protecting our employees and their email use. We all had a data center. Most of our employees spent their days working in an office. While SaaS has been around for quite some time, the ability to access it from anywhere, anytime, and from any device, was limited.
Fast forward to today, and an overwhelming majority of companies are using a hosted email solution like Microsoft 365 or Google Workspace. Many have a majority of their employees working remotely. And the proliferation of SaaS seems to just pick up pace every year.
Unfortunately, email is still a very insecure form of communication and collaboration for critical business functions like paying invoices or sharing sensitive information. Cybercriminals are well aware of this, and they leverage email attacks to a high degree of success.
Just like email marketing, attackers can send out millions of emails for pennies. And they only require a fraction of their targets to fall for the attack to earn thousands or even millions of dollars. Sadly, there's next to no risk involved for cybercriminals to launch these types of attacks—and they’re getting more advanced every single day. Here are a few new ways that they’re reaching your users.
1. Increasingly Sophisticated Inbound Attacks
Inbound email attacks are only getting more sophisticated, and it’s definitely not fake CEOs asking for gift cards anymore. Cybercriminals are using many of the tools we are all familiar with for their nefarious purposes. For example:
- ChatGPT can help cybercriminals write high-quality emails that better fool employees.
- Grammarly eliminates many grammar mistakes and misspellings that would tip off email recipients of possible scam messages.
- LinkedIn is used to target new employees unfamiliar with your security protocols or more effectively impersonate team members.
- And if you're a public company, bad guys are also looking at your SEC filings, 8-Ks, and press releases to better understand your organization.
The bad guys are watching and are quick to act. In my previous role as a CISO for a large bank, when we employed a new executive, , our team would start seeing attacks impersonating that new executive almost immediately..
Let's look at a real-world example.
Example Attack: Aging Report Theft in Italian
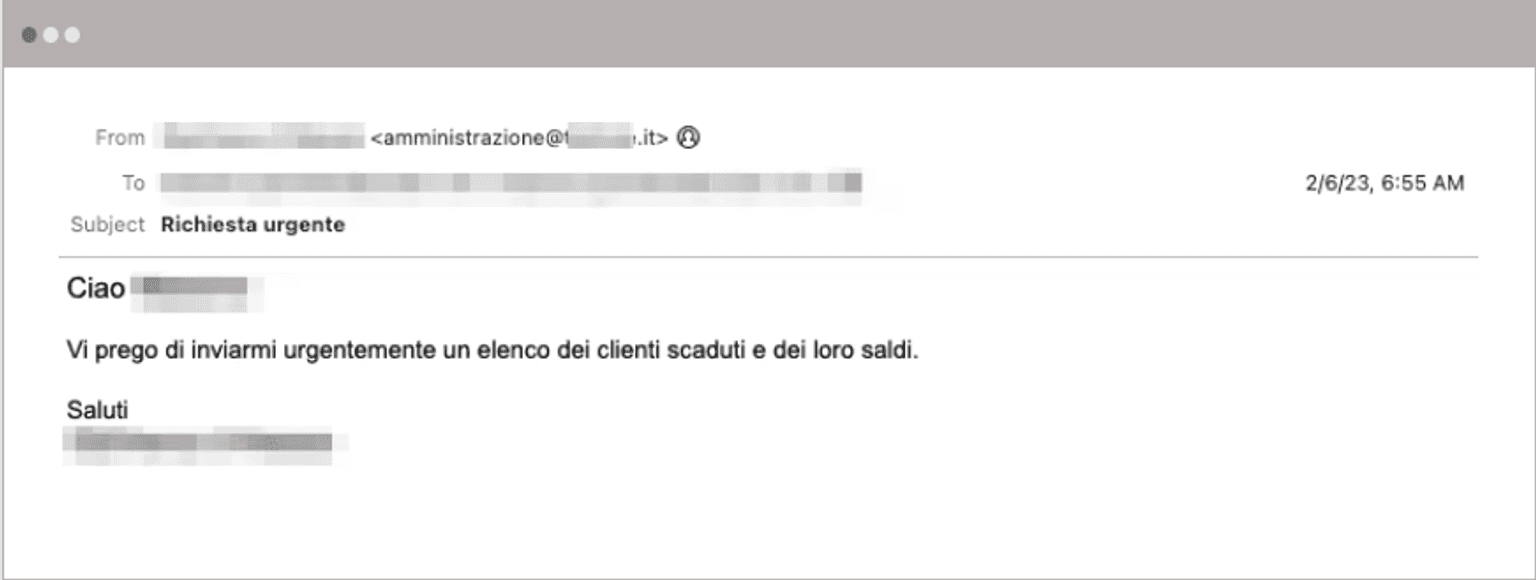
In this attack, we have an impersonated company executive that's requesting a list of all customers' outstanding payments, including their overdue balances. The email is written in Italian, which has a better chance of blending in with other business communications.
In this situation, without raising any red flags, the email was sent from a likely compromised email account at a company unrelated to the target company and the sender's name. The display name is spoofed to match the name of the impersonated employee. Because this attack is text-based without any other indicators of compromise, there's very little for a secure email gateway to use to determine its malicious intent.
What happens if the victim falls for this spoofed email and sends that information? Well, the attacker now has a list of other customers and other people that they can attack. Not only that, attackers can leverage social engineering to understand exactly how much is owed and what the overdue balances are, adding additional credibility and trust of the sender to the new victim.
2. Increased Targeting and Impersonation of Your Vendors
The second way things are getting more difficult is that criminals are turning away from impersonating your executives. Instead, they're impersonating your vendors or even third-party solutions used within your organization.
For instance, they may spoof a ServiceNow ticket, a Jira ticket, or a Zoom update. These cybercriminals know what technologies are used within your organization. They understand that those solutions usually spit out a lot of emails as the back and forth either password resets or updates. And they're cleverly mimicking those so that they look like legitimate emails a user might be expecting on this attack.
Here’s another real-world example—this time of a vendor looking for payment.
Example Attack: Compromised Vendor with Hijacked Thread
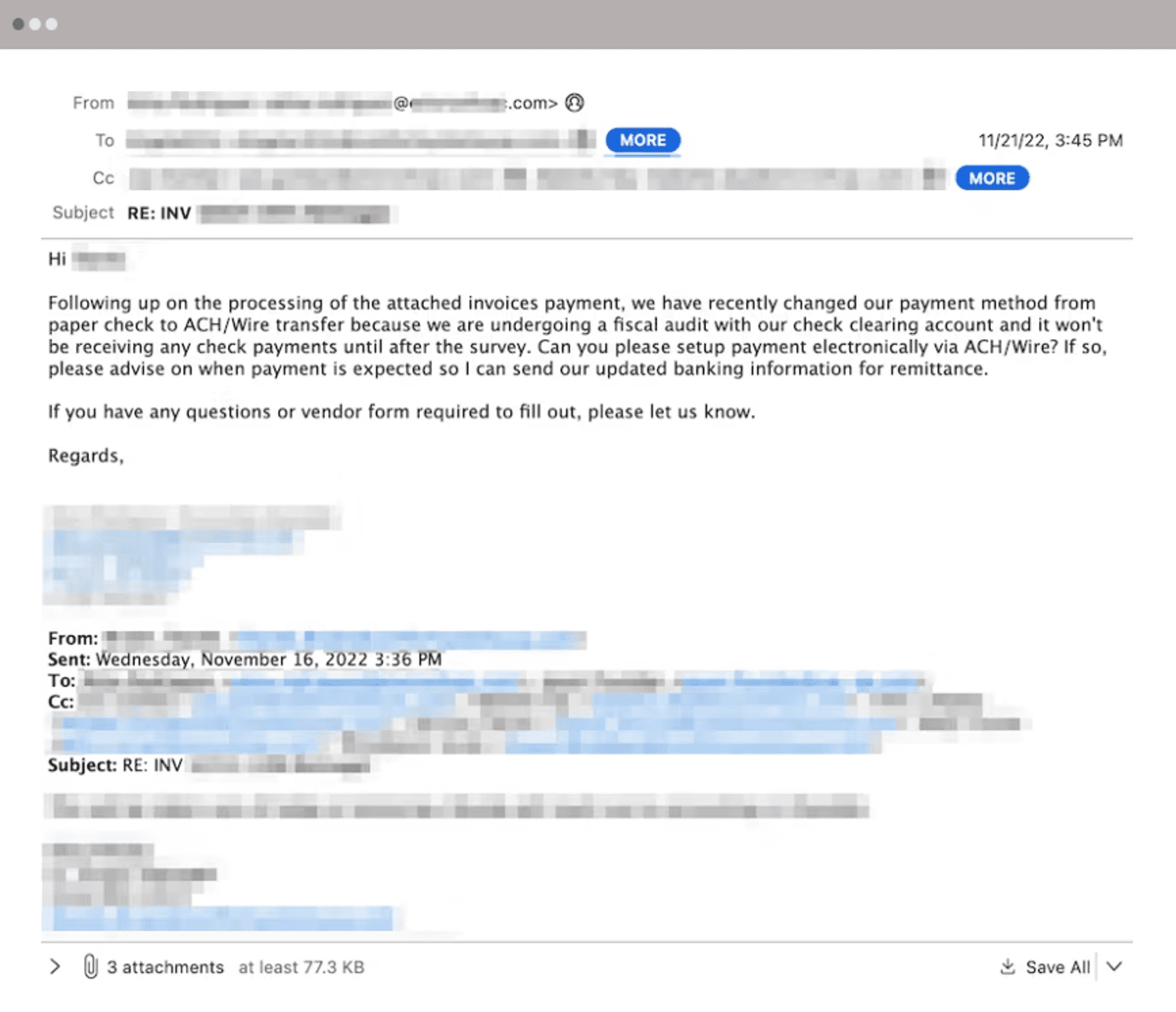
The initial email impersonated the head of finance of one of the targeted company’s external distribution partners. The message asked the recipient to provide a list of unpaid invoices owed to the partner. The message also indicated that the partner's existing bank information should be disregarded due to an audit investigation of the account. The email also provided an incentive of a 5% discount if they could pay by the end of the day. The email address displayed as the origin of the message appeared to be a compromised external account not affiliated with the impersonated partner.
However, the reply address was sent to an account setup on a provider that provides freely available encrypted email services to hide all the attack targets. Once again, the attacker BCC'd all of their recipients instead of including them on the normal "to" field. Because this is a text-based account without any indicators of compromise, there are little things that a secure email gateway could do to determine the malicious intent. Because this email was sent from a legitimate account without a history of abuse, there are no direct signals indicating that the email's origin is malicious.
It's not uncommon to see a vendor compromised. The bad guy goes in, and they look through the sent folder. They find emails, they find threads, and they figure out who their targets should be. Then they cut and paste that email message. They create a lookalike domain. They paste it in there, and they send it back to the original recipients.
3. Use of Third-Party Applications and Integrations
And unfortunately, it's not just basic inbound email either anymore. Bad guys are very much omnichannel and they’re finding new ways into your email infrastructure. Recently, we’ve seen a focus on third-party applications whereby attackers will use social engineering to convince a user to install what appears to be a legitimate application, but that actually provides them with near-instant data about what is happening within the inbox.
Here’s a real-world example.
Example Attack: Access Compromise through Third-Party App API
In February 2020, attackers installed an Azure application that had email access into the M365 tenant at News Corp—the parent company of The Wall Street Journal and the New York Post. Once installed into the environment, the application had no noticeable side effects. As a result, the application shipped logs of searches and emails to the attacker’s server on a nightly basis, providing information to them for nearly two years before it was detected.
It’s common for large organizations to have hundreds or thousands of third-party apps integrated into their Google or Microsoft ecosystem. And these applications can be easy targets for attackers, who love them because they don’t have to break into your email account or spoof anyone.
How to Stop Modern Email Attacks
Although these are serious and real-world examples, the news isn’t all doom and gloom. The reality of it is email is still that common denominator. Every organization, whether you are big or small, uses email. That's how we communicate with our vendors, our customers, and our coworkers. We can't eliminate email as a channel, but we can do something to stop these modern email attacks.
When we discuss modern email attacks, we need to think of cloud email security as going beyond the message itself. We need to take a holistic approach to cloud email security to stop both the inbound email attacks that infiltrate through the front door and the third-party application attacks that enter through side doors in our email infrastructure.
Doing so requires a new solution that understands the people, vendors, and applications in your ecosystem and can baseline normal behavior to detect anomalous activity. Traditional ways of detecting attacks by looking for known bad signatures no longer work—it’s time to understand known good instead.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
The Visibility Gap in Autonomous AI Agents
Published: 02/24/2026
OpenClaw Threat Model: MAESTRO Framework Analysis
Published: 02/20/2026
Token Sprawl in the Age of AI
Published: 02/18/2026





.png)



