Microsoft 365 and Azure AD: Addressing Misconfigurations and Access Risks
Published 11/30/2023
Originally published by Reco.
Written by Gal Nakash.
In this blog post, we'll explore a real-world use case involving a SaaS Threat Detection module and its revelation of a common threat within Office 365: disabled users retaining access to sensitive company data.
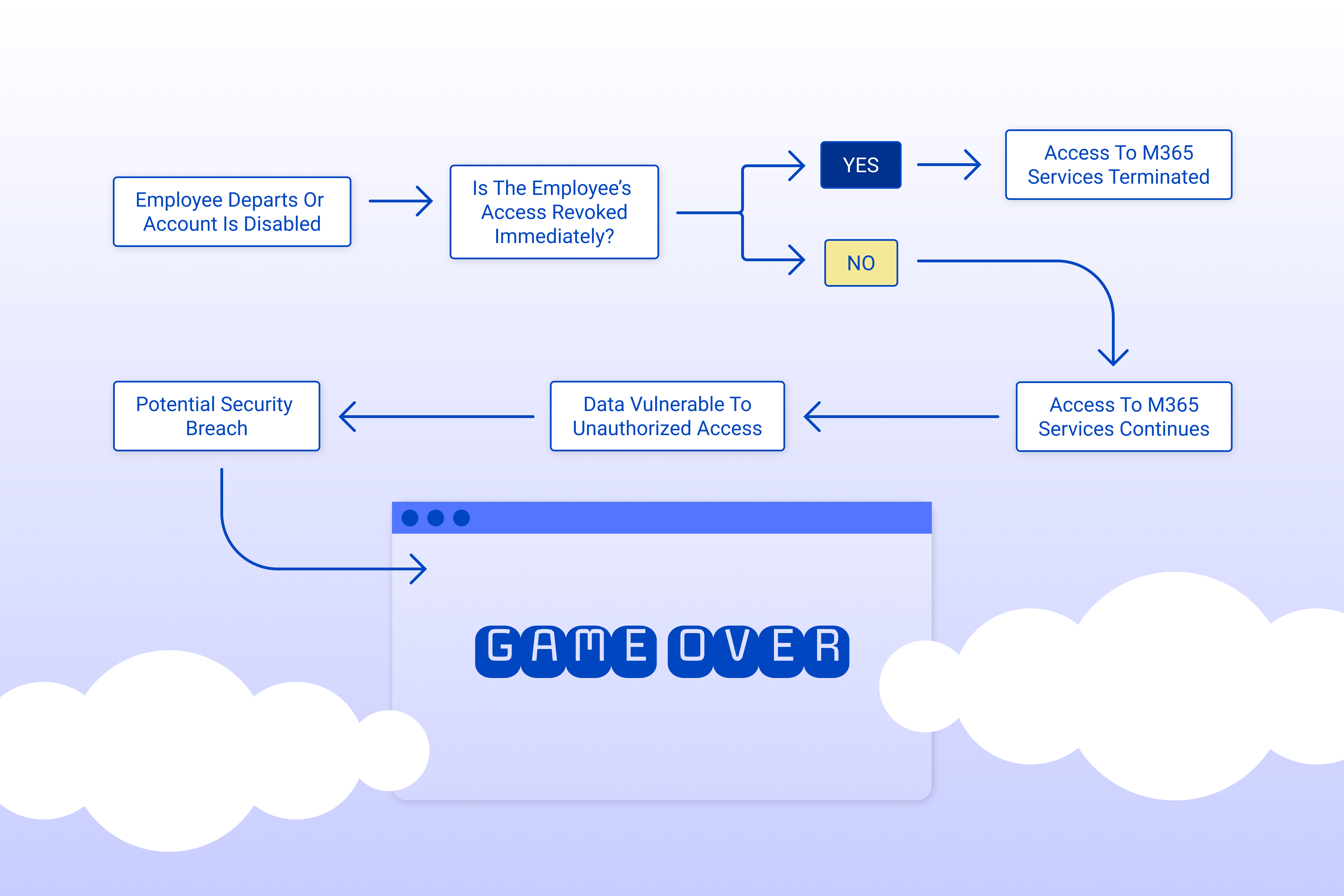
Disabled users can continue to access M365 services until their access tokens expire
When an employee departs from your organization or their account is disabled, it's easy to assume that their access to M365 services, like SharePoint and OneDrive, is immediately terminated. However, the reality is quite different. Disabled users can continue to access these services until their access tokens expire, leaving your data vulnerable to unauthorized access and potential security breaches.
What is an access token?
Access tokens, often referred to as session tokens in the context of web services like Microsoft 365 (M365), are crucial components in digital identity and access management. They function as digital keys, allowing users to access services and resources after successful authentication. When users log in, the system authenticates their credentials and issues an access token. This token contains the user's identity, privileges, and other session information, enabling the user to interact with the service without needing to re-enter credentials for each action or request.
Access tokens have a predefined expiration time, a critical design aspect. This expiration time is set to balance security and convenience. A shorter lifespan for the token means higher security, as it reduces the window of opportunity for unauthorized access if the token is compromised. However, it also requires users to re-authenticate more frequently, which can impact user experience. In the case of M365, these tokens ensure that users can smoothly access various services like SharePoint and OneDrive. Still, they also pose a security risk if not managed correctly, mainly when dealing with disabled accounts.
.jpg)
Are M365 and Azure AD customers at risk?
The short answer is yes. As long as these access tokens remain valid, even a disabled user can access M365 services, putting your organization's data at risk. So, the question is, what can you do to mitigate this risk?
Steps to fix default misconfigurations
To address the issue of disabled users retaining access, it's crucial to take proactive steps to ensure that inactive users are disabled after a predetermined period of time:
- Sign in to the Microsoft 365 Admin Center as a global or SharePoint admin, ensuring you have the necessary Office 365 administrator permissions within your organization.
- In the left pane of the admin center, select SharePoint under Admin centers. If you are directed to the classic SharePoint admin center, choose "Try it now" to access the new SharePoint admin center.
- In the new SharePoint admin center, navigate to "Policies" and select "Access control."
- Choose "Idle session sign-out" and enable "Sign out inactive users automatically."
- Select when you want to sign out users and specify how much notice you want to provide before signing them out. Ensure these settings align with your organization's security policies and operational needs.
- Finally, select "Save" to apply the configured settings.
- Ensure related policies are in place and receive prioritized alerts on configuration drift.
Security risks in the Microsoft identity
This scenario highlights a significant security gap in Microsoft's identity management system. Access tokens should be invalidated immediately upon account disablement to enhance security further.
For those devices that remain unmanaged, consider utilizing session conditional access policies and other compensating controls to reduce the impact of token theft:
Reducing the lifetime of the session increases the number of times a user is forced to re-authenticate but minimizes the length of time session token is viable.
Reducing the viable time of a token forces threat actors to increase the frequency of token theft attempts which in turn provides defenders with additional chances at detection.
Implement Conditional Access App Control in Microsoft Defender for Cloud Apps for users connecting from unmanaged devices.
In addressing the inherent security risks within Microsoft's identity management system, it's instructive to consider insights from Microsoft's own experts. As highlighted in their article 'Token tactics: How to prevent, detect, and respond to cloud token theft', organizations can significantly reduce the risk of token theft by ensuring full visibility of user authentication processes. This includes employing device-based conditional access policies and compliance tools like Intune to manage device security. For unmanaged devices, strategies such as reducing session token lifetimes and implementing Conditional Access App Control can be crucial in mitigating the impact of token theft. Furthermore, deploying phishing-resistant MFA solutions, especially for users with significant privileges, adds another layer of security. This approach, tailored to the organization's specific risk profile, underscores the importance of vigilance and proactive measures in protecting against unauthorized access and data breaches".
Takeaways
In conclusion, disabled users retaining access to SaaS applications such as M365 services is a genuine security concern that needs attention. By implementing the suggested recommendations to disable user access immediately and addressing idle session sign-out settings, you can improve your organization's security posture.
Addressing SaaS misconfigurations and improving identity management systems are essential steps to protect your sensitive data and ensure that an employee's departure or the disabling of an account does not lead to unauthorized data access or security breaches. It's a shared responsibility between organizations and service providers to keep M365 data safe in today's digital landscape.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
Securing the Modern Cloud: 5 Best Practices for Protecting Multi-Cloud Workloads
Published: 03/02/2026
Why DNS TXT Records Deserve Governance in Security Programs
Published: 02/02/2026
Your Cloud May Be Secure, But Are Your Backups? Lessons From The EY Incident
Published: 01/12/2026








.jpeg)
