Buckle Up: BEC and VEC Attacks Target Automotive Industry
Published 07/15/2024
Originally published by Abnormal Security.
Written by Mick Leach.
While every organization across every vertical is at risk of experiencing advanced email attacks, there are certain industries that, for various reasons, periodically become the go-to target for threat actors. Our research revealed that the automotive industry currently finds itself in the crosshairs of cybercriminals launching business email compromise (BEC) and vendor email compromise (VEC) attacks.
These attacks, designed to deceive employees and extract money or sensitive information, pose a significant threat to an automotive organization’s financial stability and reputation. One alarming case that highlights the severity of the issue is the $37 million loss suffered by auto parts supplier Toyota Boshoku. In this attack, fraudsters used an email scam to manipulate an employee into changing bank account information for a wire transfer.
Although BEC and VEC attacks are on the rise across the board, the data on the automotive industry is especially alarming. Here’s a closer look at what our research uncovered.
Threat Actors Rev Up BEC and VEC Attacks on the Automotive Industry
So why are organizations in the automotive industry particularly popular targets for BEC and VEC attacks? First, high-value transactions for parts and inventory are common. Second, automotive groups rely on complex supply chains and vast vendor ecosystems—providing attackers with ample third parties to impersonate and vulnerabilities to exploit.
Between September 2023 and February 2024, BEC attacks against businesses in the automotive industry increased by 70.5%. This represents 1.7 BEC attacks per week, compared to 1 attack per week during the prior six-month period. The first quarter of 2024 was particularly active, potentially indicating a trend for the rest of the year.
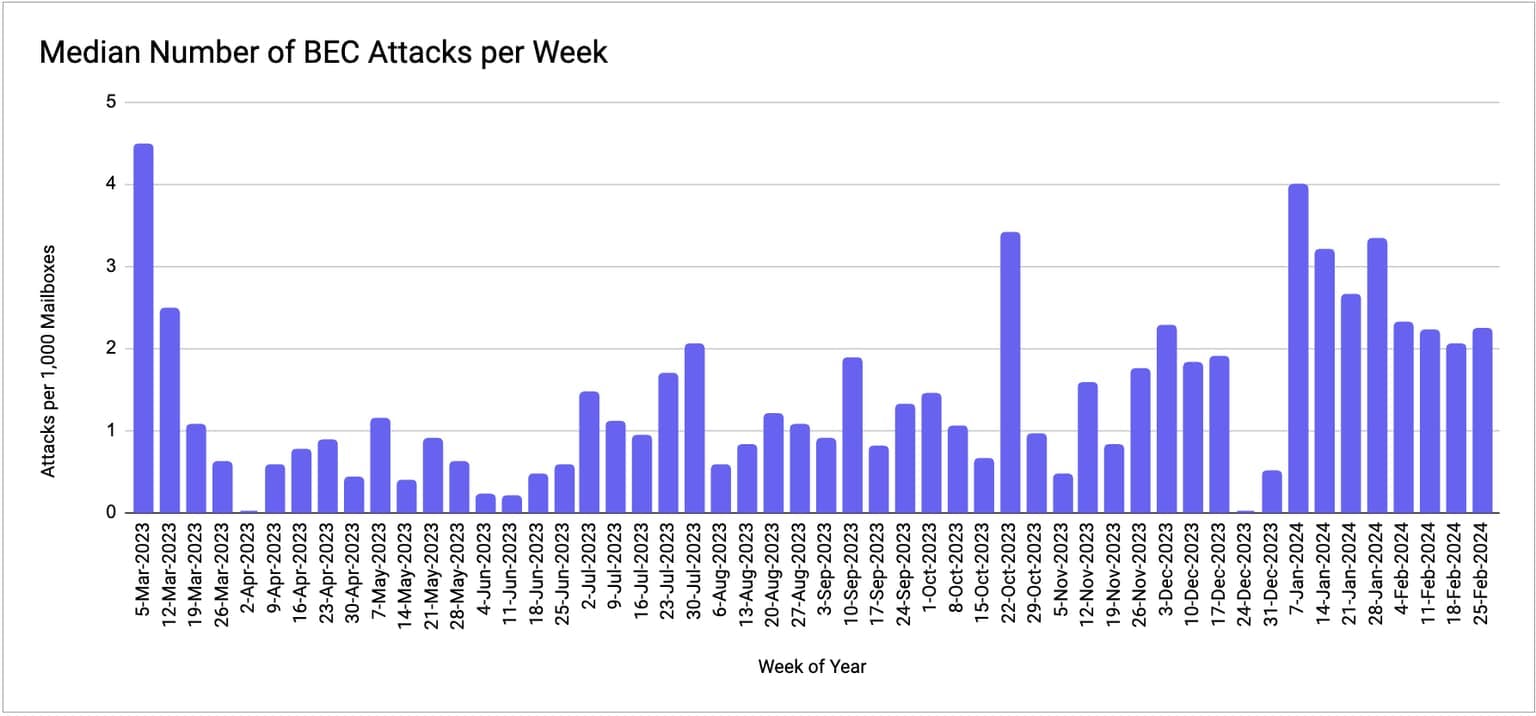
VEC attacks targeting automotive organizations were similarly elevated between September 2023 and February 2024, with 63% of Abnormal Security customers in the automotive industry experiencing at least one VEC attack. This is a higher rate than experienced by organizations in the energy/infrastructure (54%), hospitality (50%), and finance (35%) industries during the same timeframe.
The financial implications of falling victim to these attacks are substantial, with the average cost of a successful BEC attack exceeding $137,000. Adding to the challenge, these sophisticated social engineering tactics often bypass traditional security measures, leaving employees—notoriously the weakest link in the cybersecurity chain—as the last line of defense.
By impersonating colleagues or trusted vendors through spoofed email addresses or compromised accounts, threat actors trick targets into divulging sensitive information or making unauthorized financial transactions.
Looking Under the Hood of a Real Attack
In the business email compromise attack below, the threat actor posed as the president of a truck dealership and emailed the dealership’s accounts payable department. The message was designed to appear as if the impersonated president was forwarding an invoice from a professional services provider along with his approval to remit payment.
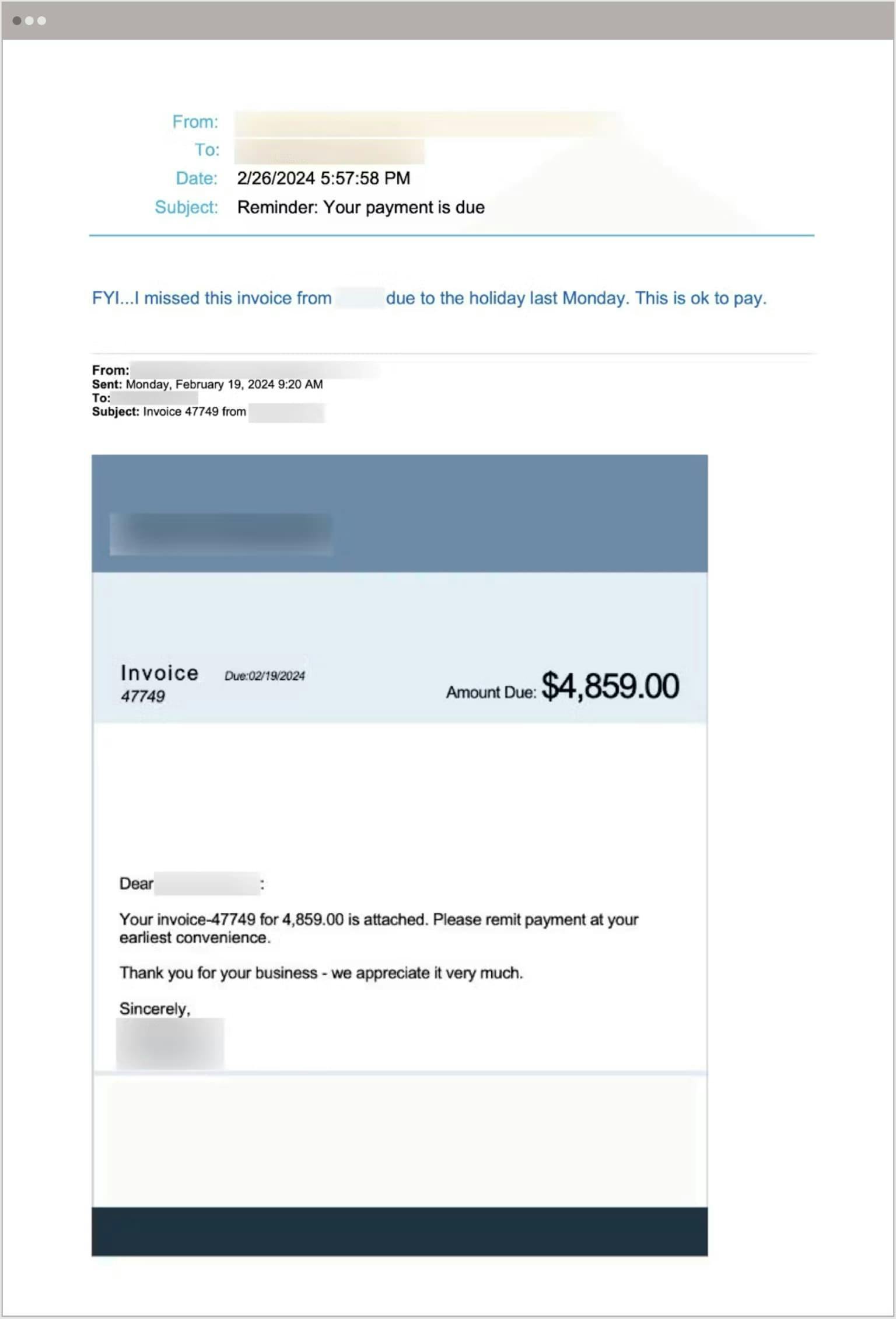
Example of email attack targeting an organization in the automotive industry
Because this attack has no obvious indicators of compromise and was sent from an established, trusted domain, it is unlikely to be flagged as malicious by a legacy email security system. Additionally, because the attacker took several steps to increase the appearance of legitimacy (e.g., changing the sender display name and email account name to that of the dealership’s president and creating a fraudulent email thread referencing a real business), the average employee would likely believe the message and the request are legitimate.
Clearly, automotive organizations need more sophisticated security to meet the evolving threat landscape head-on.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates
Related Articles:
How Attackers Are Weaponizing AI to Create a New Generation of Ransomware
Published: 03/04/2026
Core Collapse
Published: 02/26/2026






.jpeg)
.jpeg)

