Deception as a Form of Defense
Published 01/04/2022
 Written by Jordi Vilanova, Cloudtango
Written by Jordi Vilanova, Cloudtango
With thousands of breaches occurring annually, organizations must get creative when it comes to building a comprehensive and adaptive security defense plan. Detecting threats early inside any environment is critical to prevent data exfiltration and other type of damage to an organization’s infrastructure.
As such, deception is one of the most successful cybersecurity techniques you can apply today to your line of defense. Deception techniques use misleading tactics to lure attackers, from fake network environments to honeypots, the goal is to catch undesired activity and malicious actors operating undetected while collecting information to help dissect any attack.
Deception can be used in several forms and shapes; however, the most common technique will involve planting decoys across the environment to lure attackers in, forcing them to reveal their presence when they would otherwise remain undetected. Defenders can continue to monitor its activity, while unsuspecting attackers go about their business. This information will be critical to understand if any real data has been compromised, or to reinforce your current security to avoid any future data exfiltration.
There are a great many frameworks available providing deception and detection. Most of the time, these tools are called honeypots.
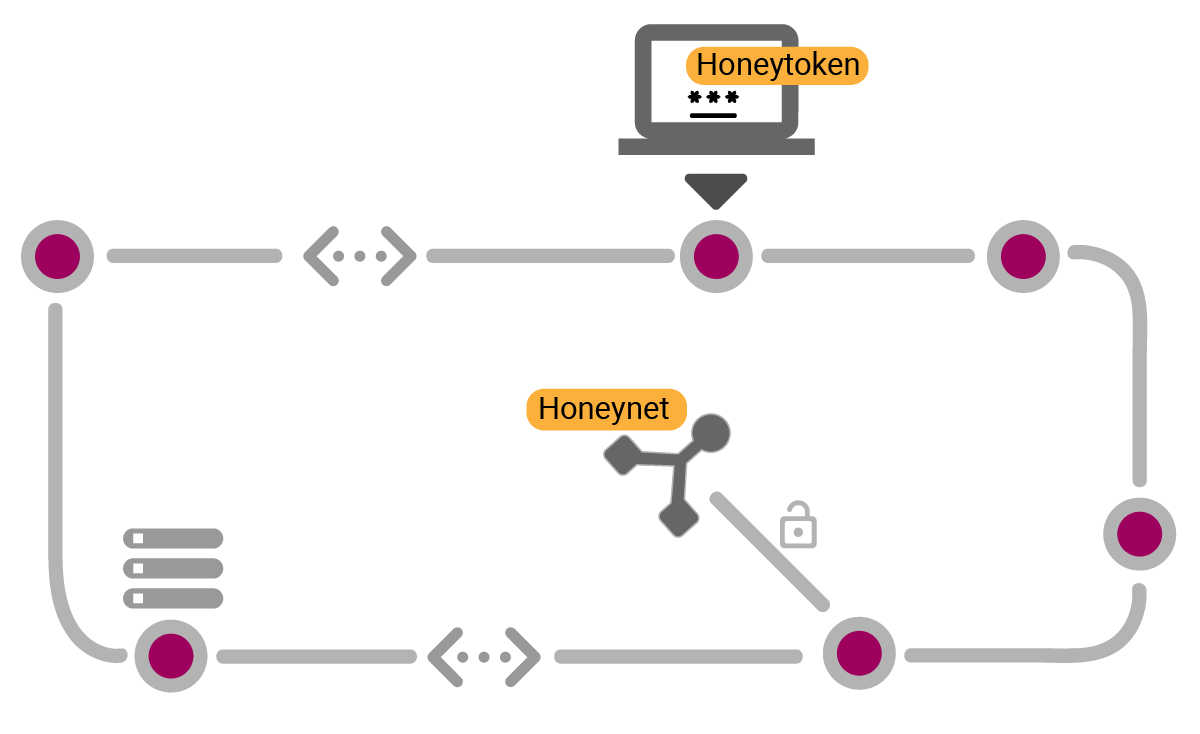
Types of Honeypots
Honeynet. A decoy network that looks like a real network.
Honeytoken. A piece of data injected as decoy objects into existing workloads.
Honeycred. Uses credentials as honeypot.
Honeyport. Sets up a specific TCP Port with no real function in the network as decoy.
Spam Trap. A fake email address used to bait spammers.
Benefits of Deception
The benefits of applying deception techniques are multiple, visibility, prevention, and reduced cost of ownership. Unlike firewalls and endpoint detection systems, deception techniques do not seek to defend a perimeter, but to uncover any illicit activity, even if it comes from within an organization. With deception you can easily factor in the human’s point of view in any attack. Modern deception is based on honeypots, but automation and AI is taking the art of deception to new levels of complexity. To implement a deception plan in an organization, one would be well advised to consult with MSPs or independent contractors as they can provide the know-how and experience required for a successful plan.
Unlock Cloud Security Insights
Subscribe to our newsletter for the latest expert trends and updates






